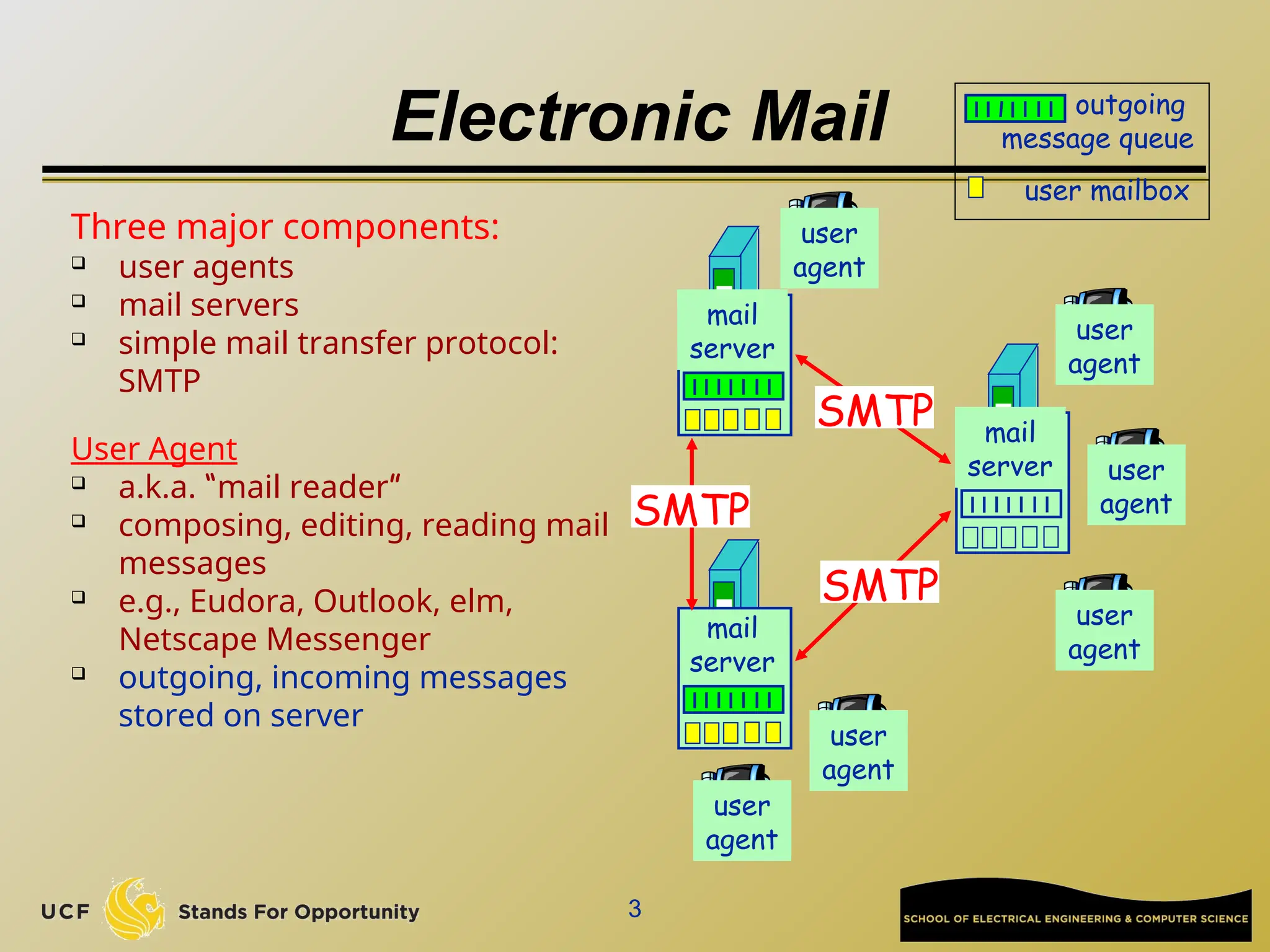
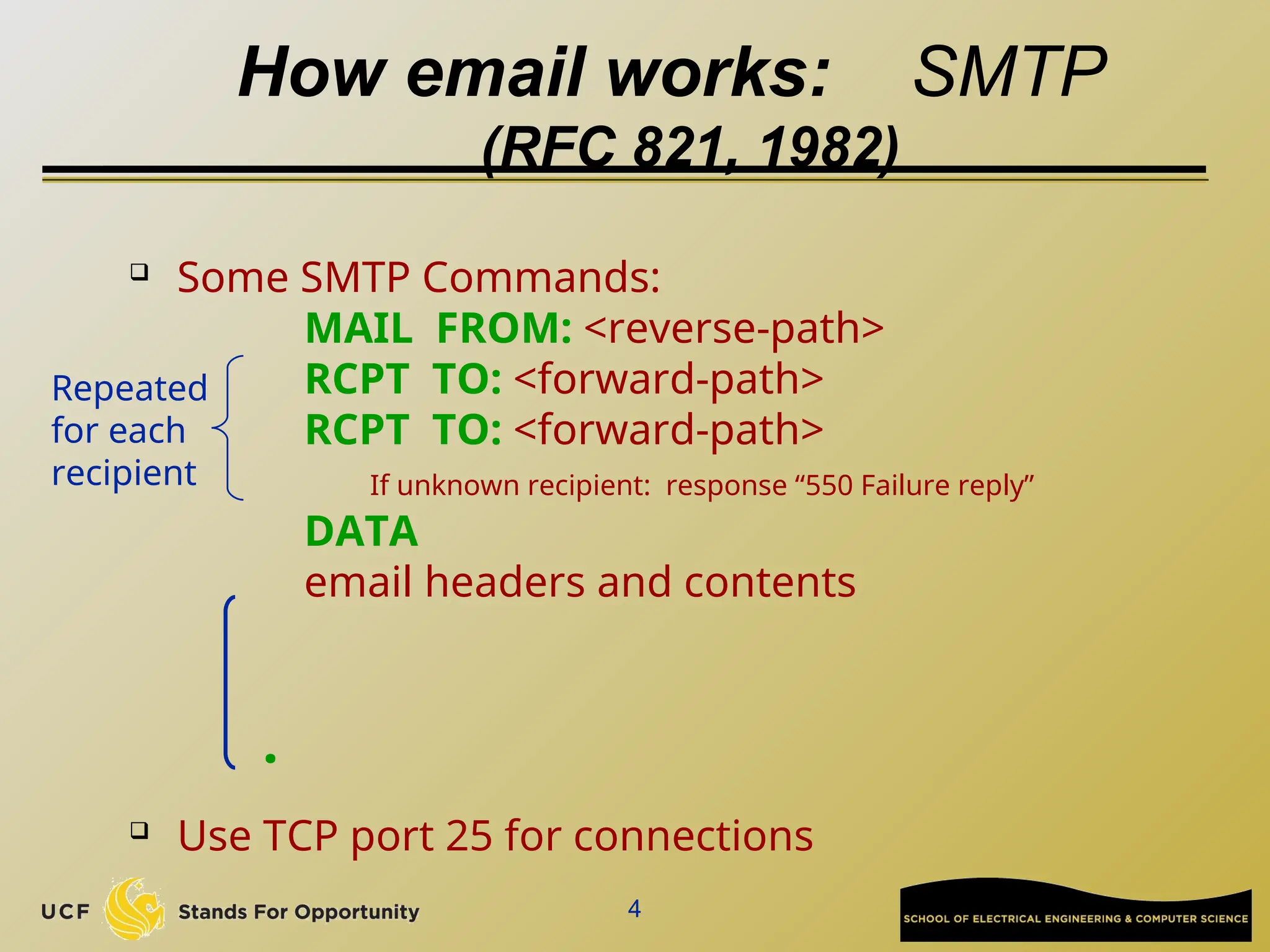
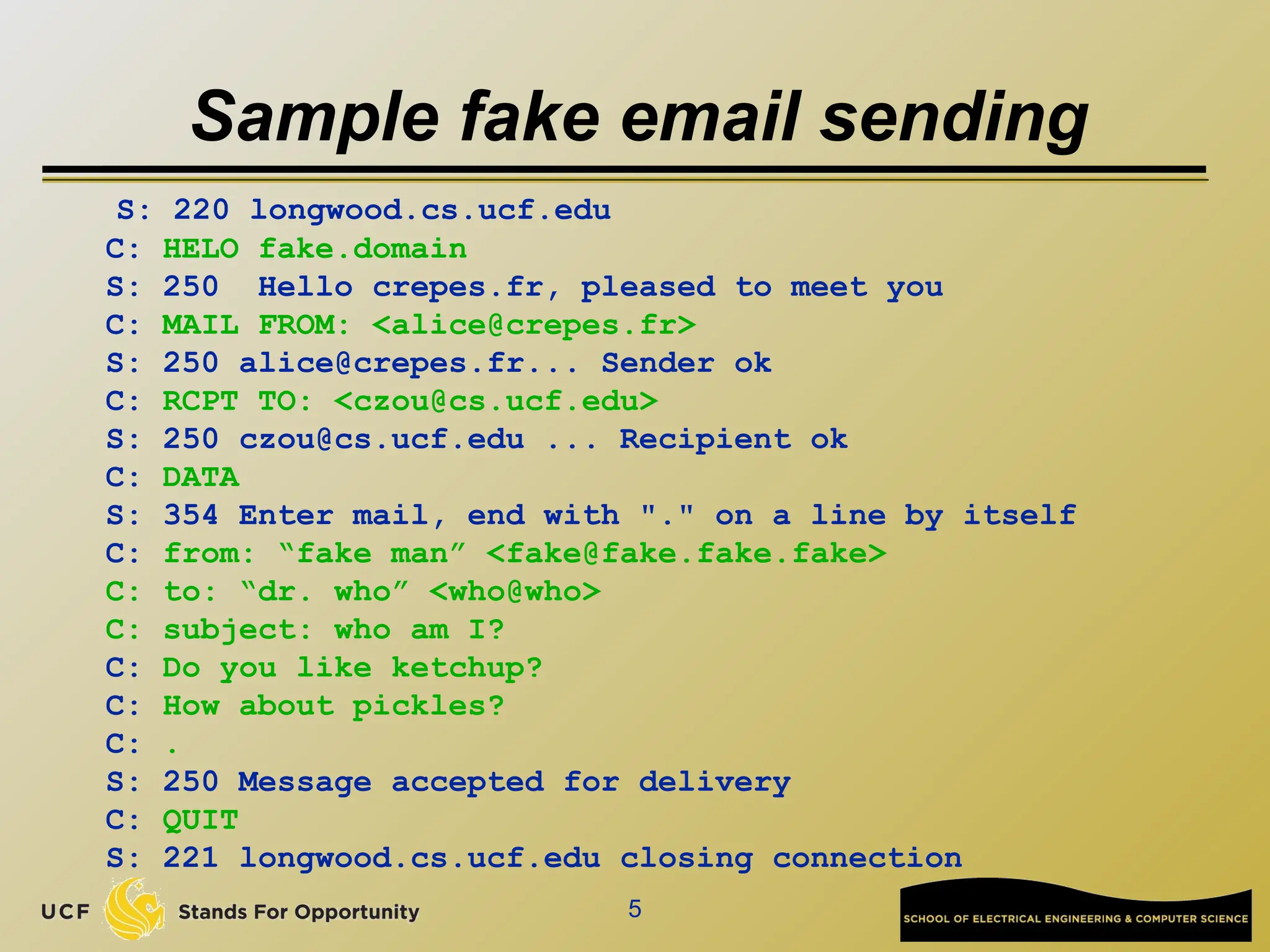
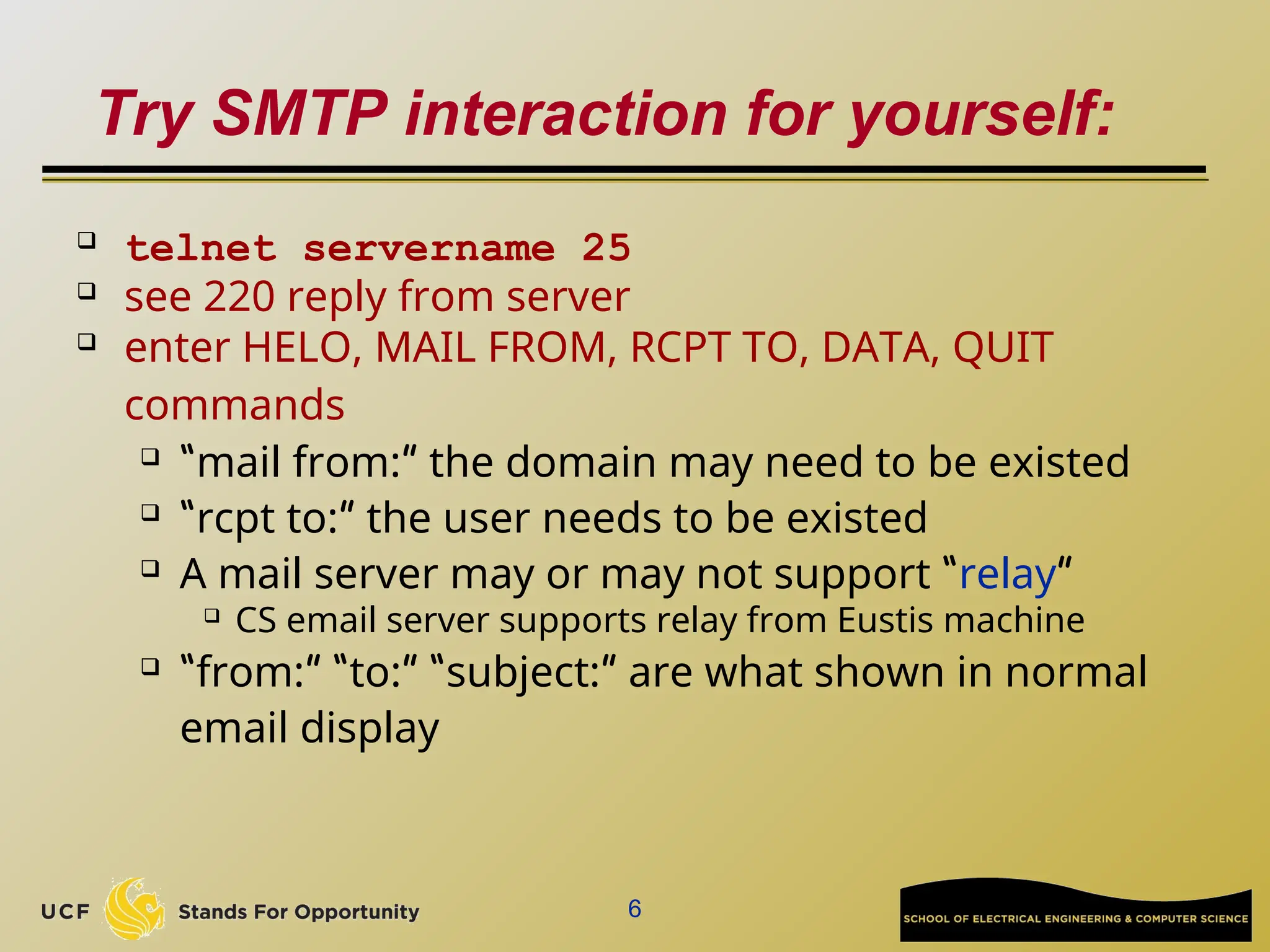
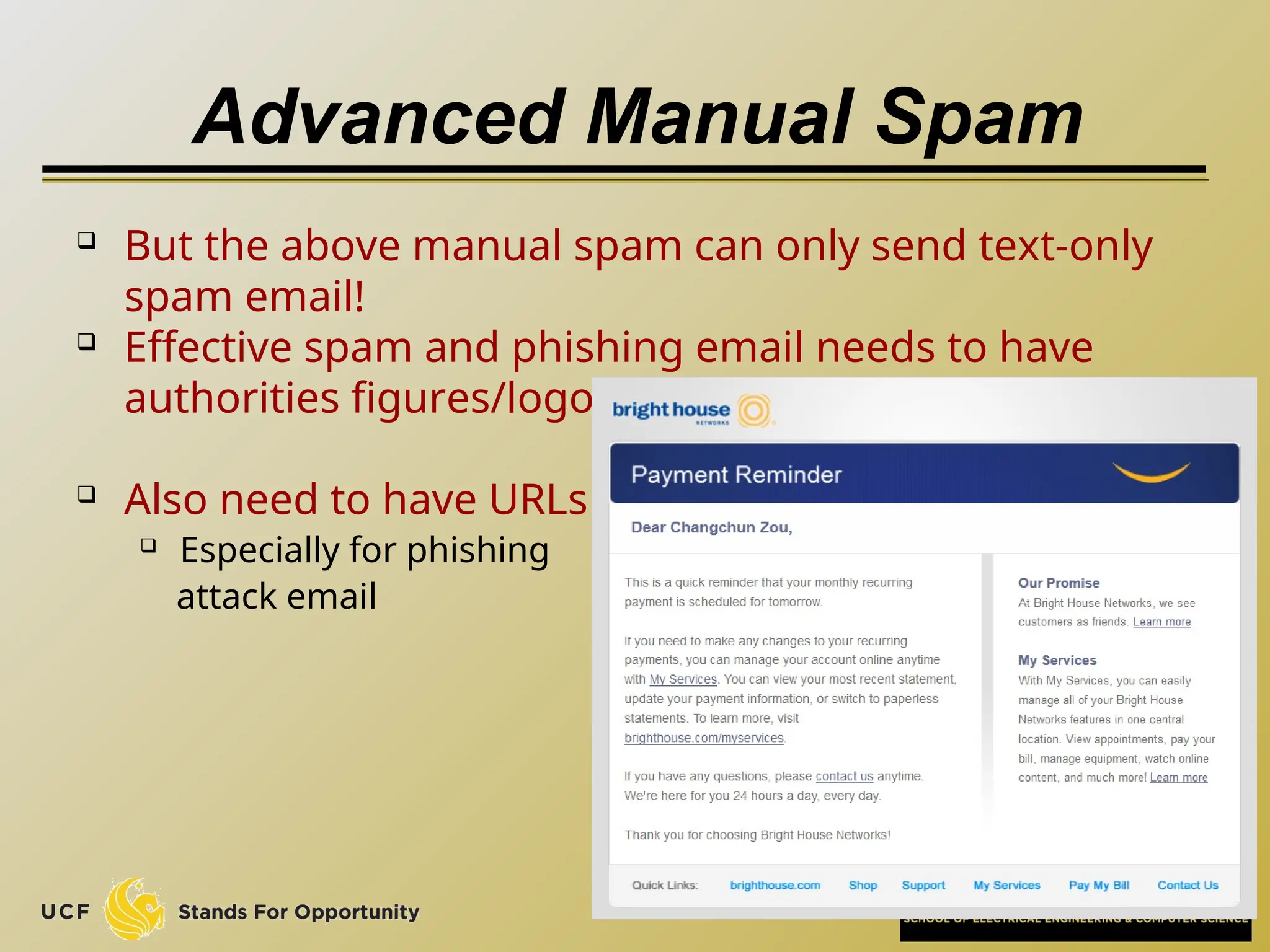
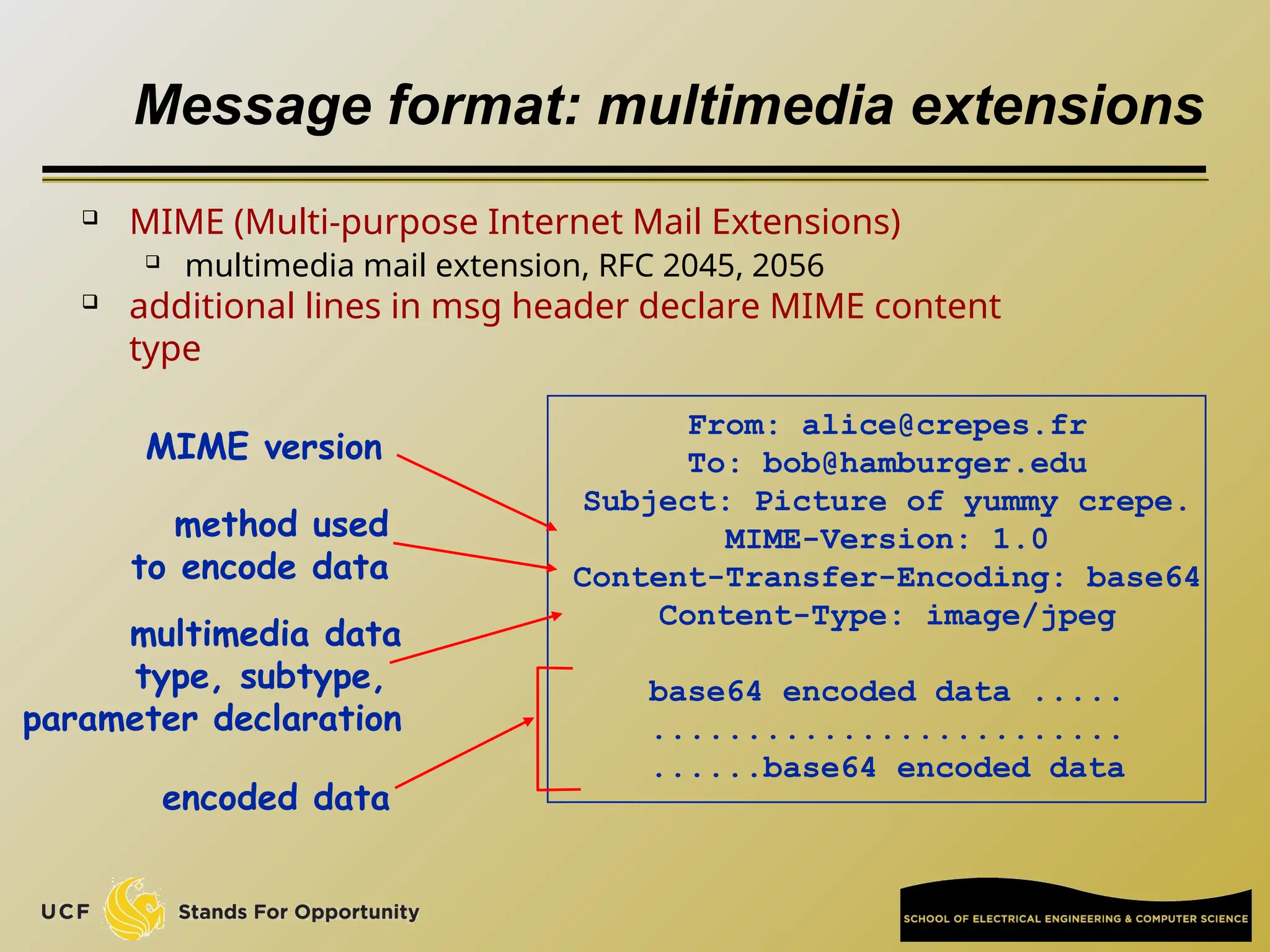
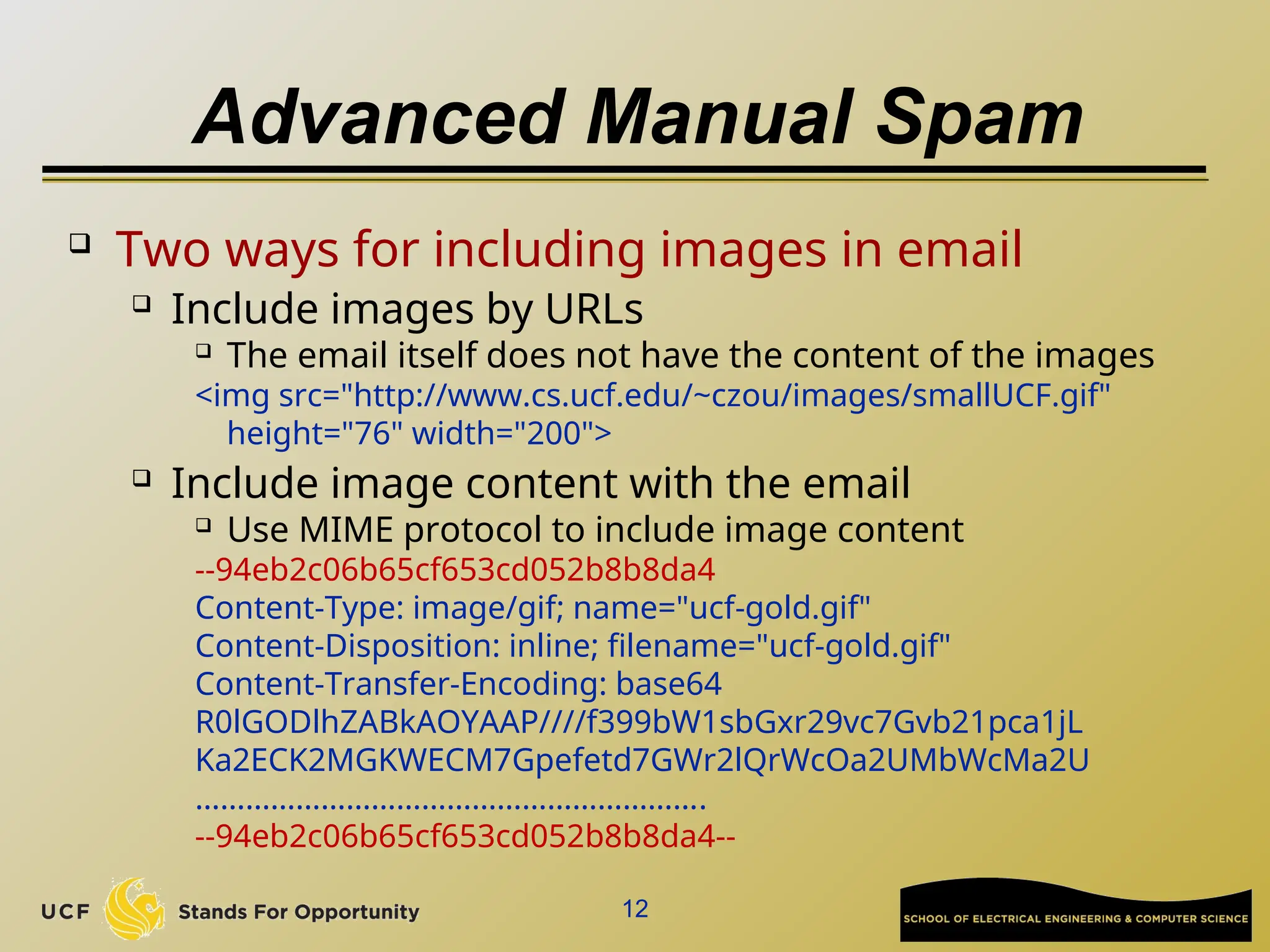
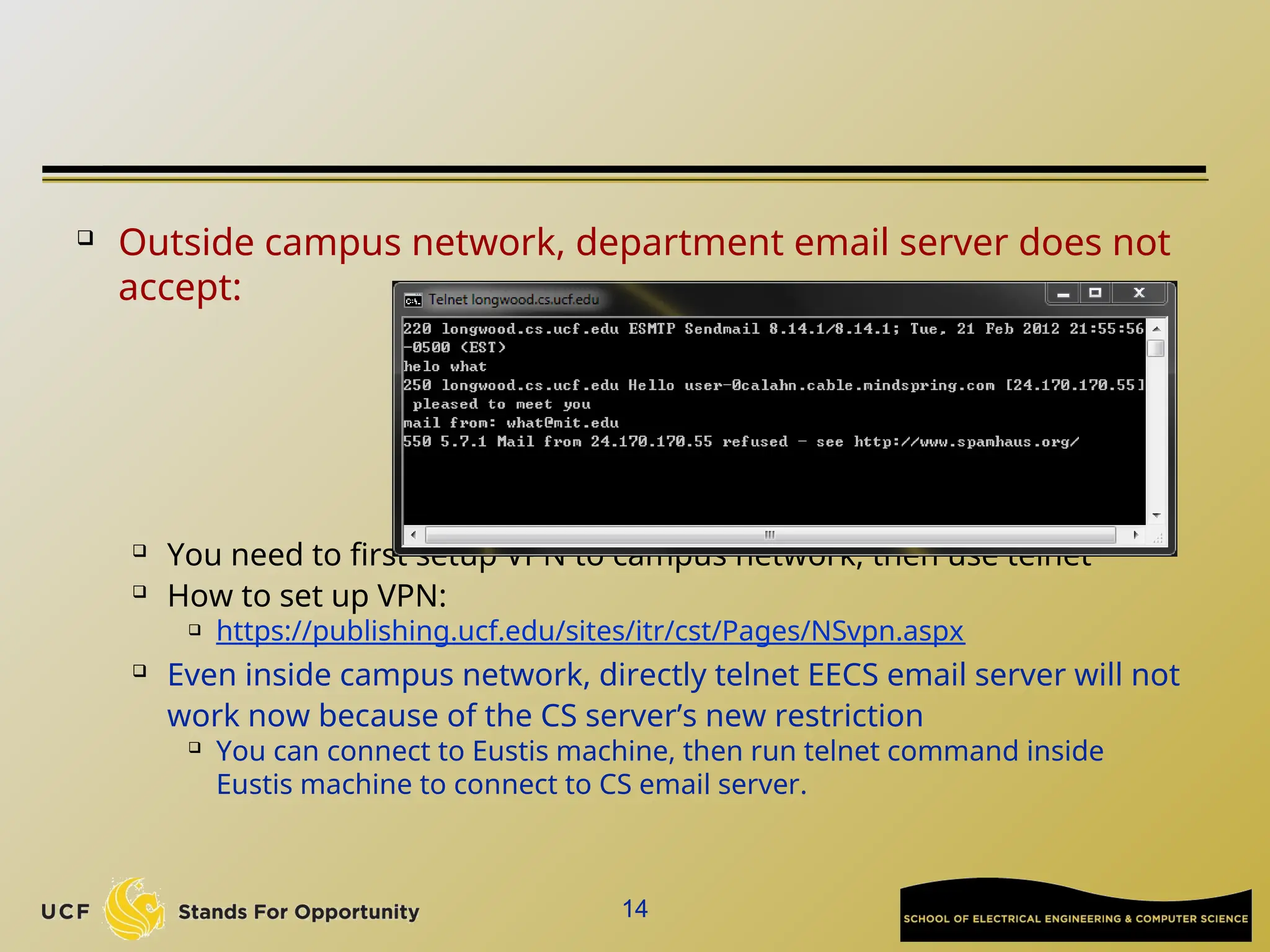
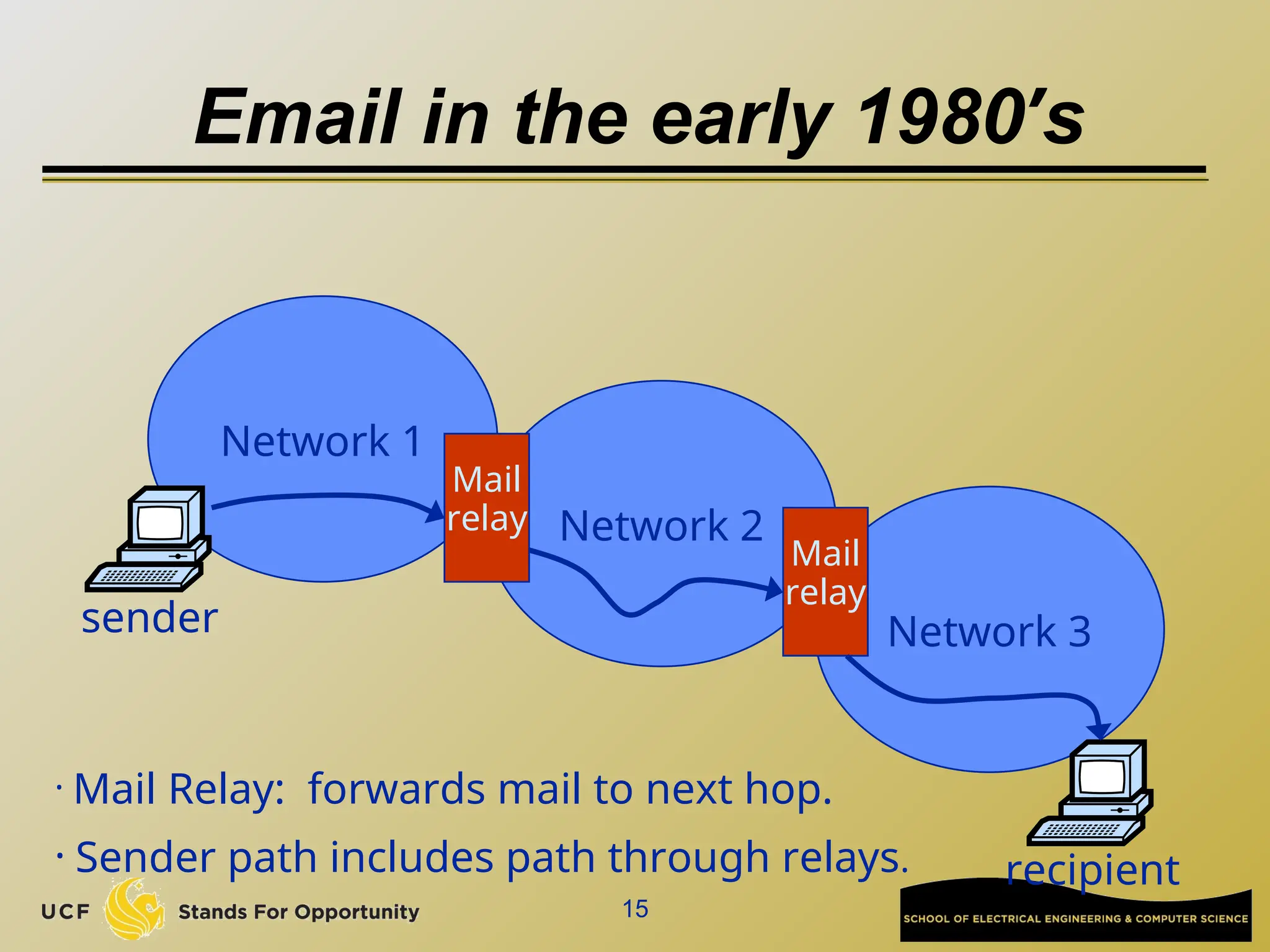
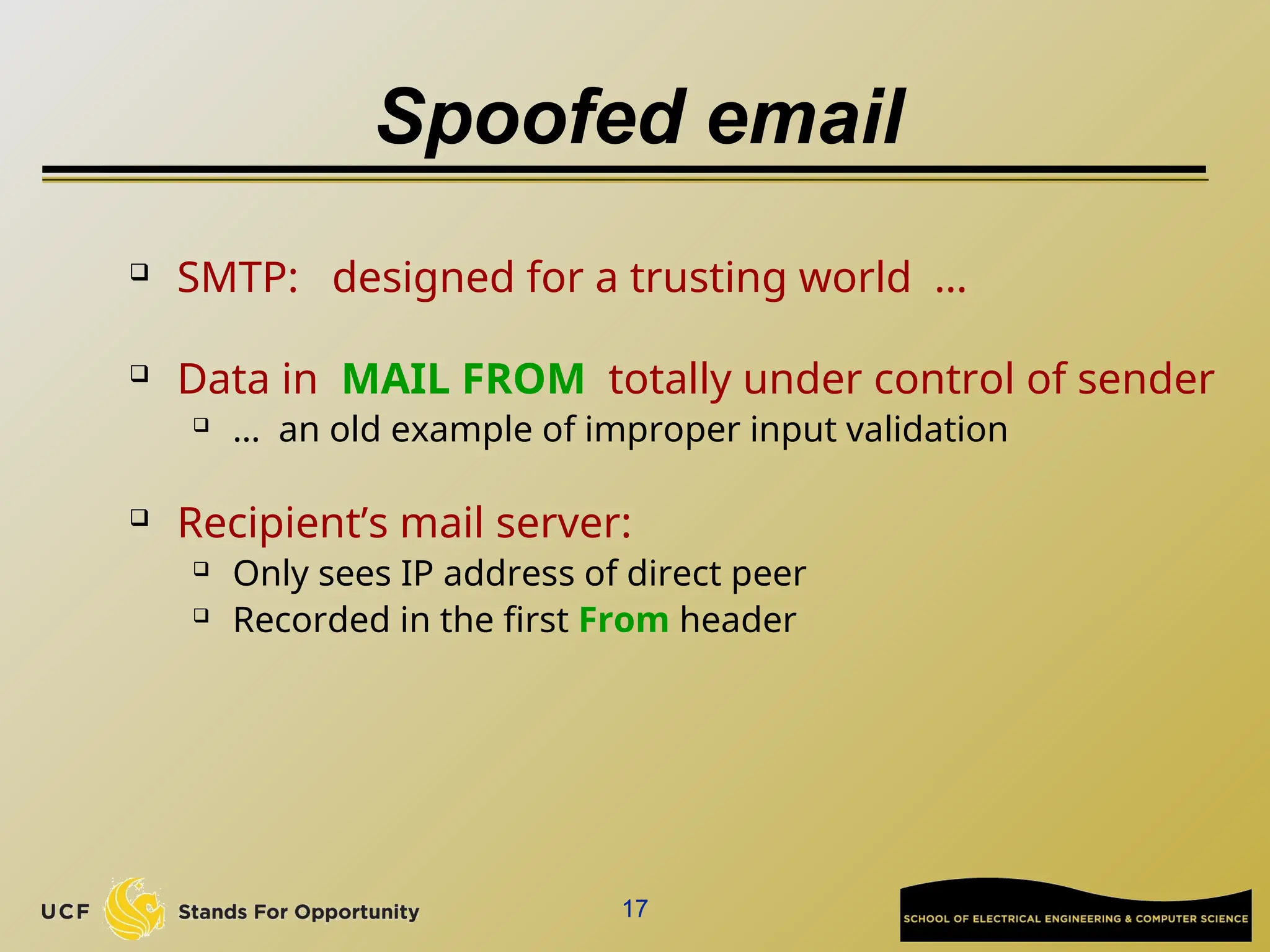
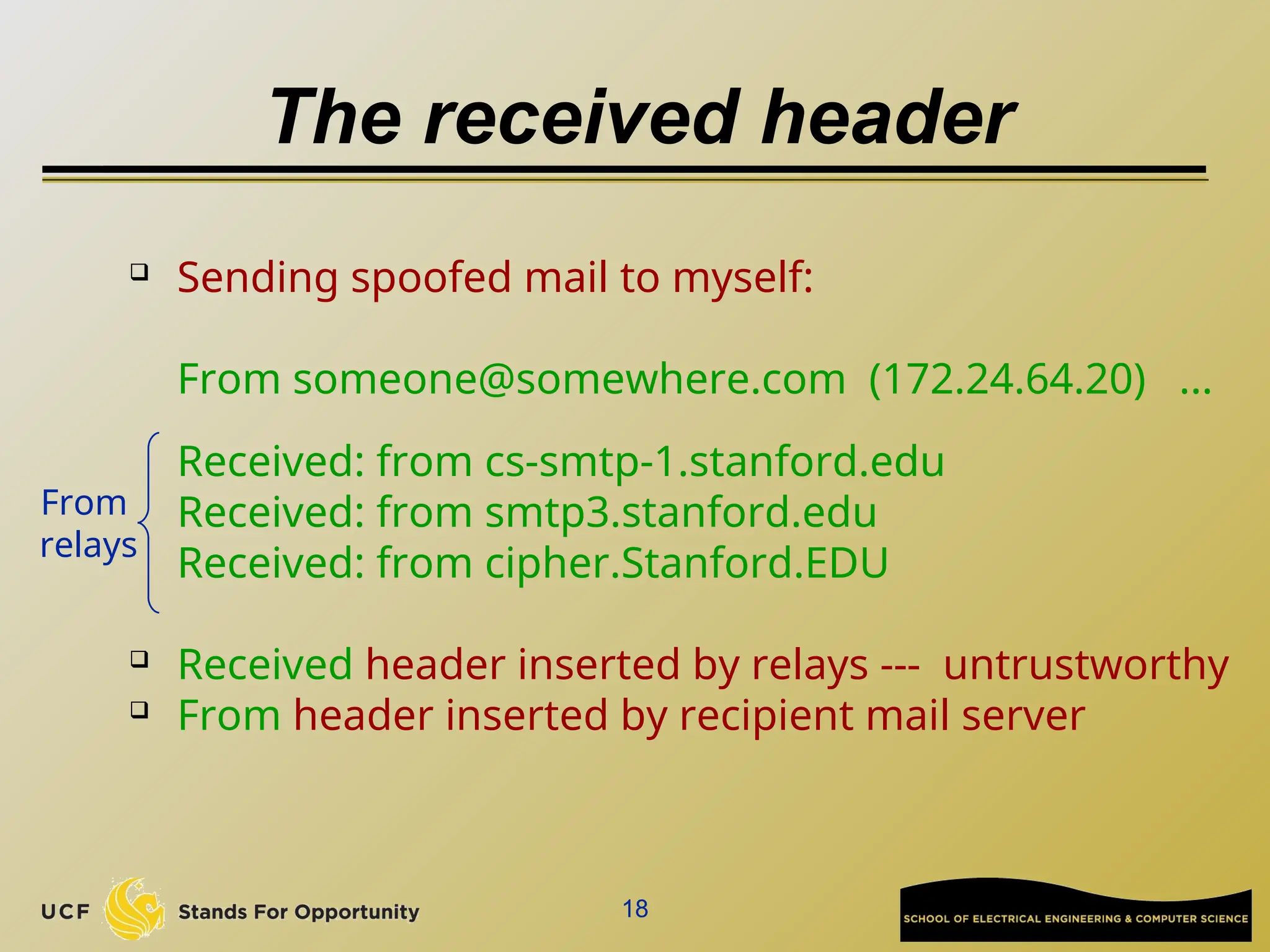
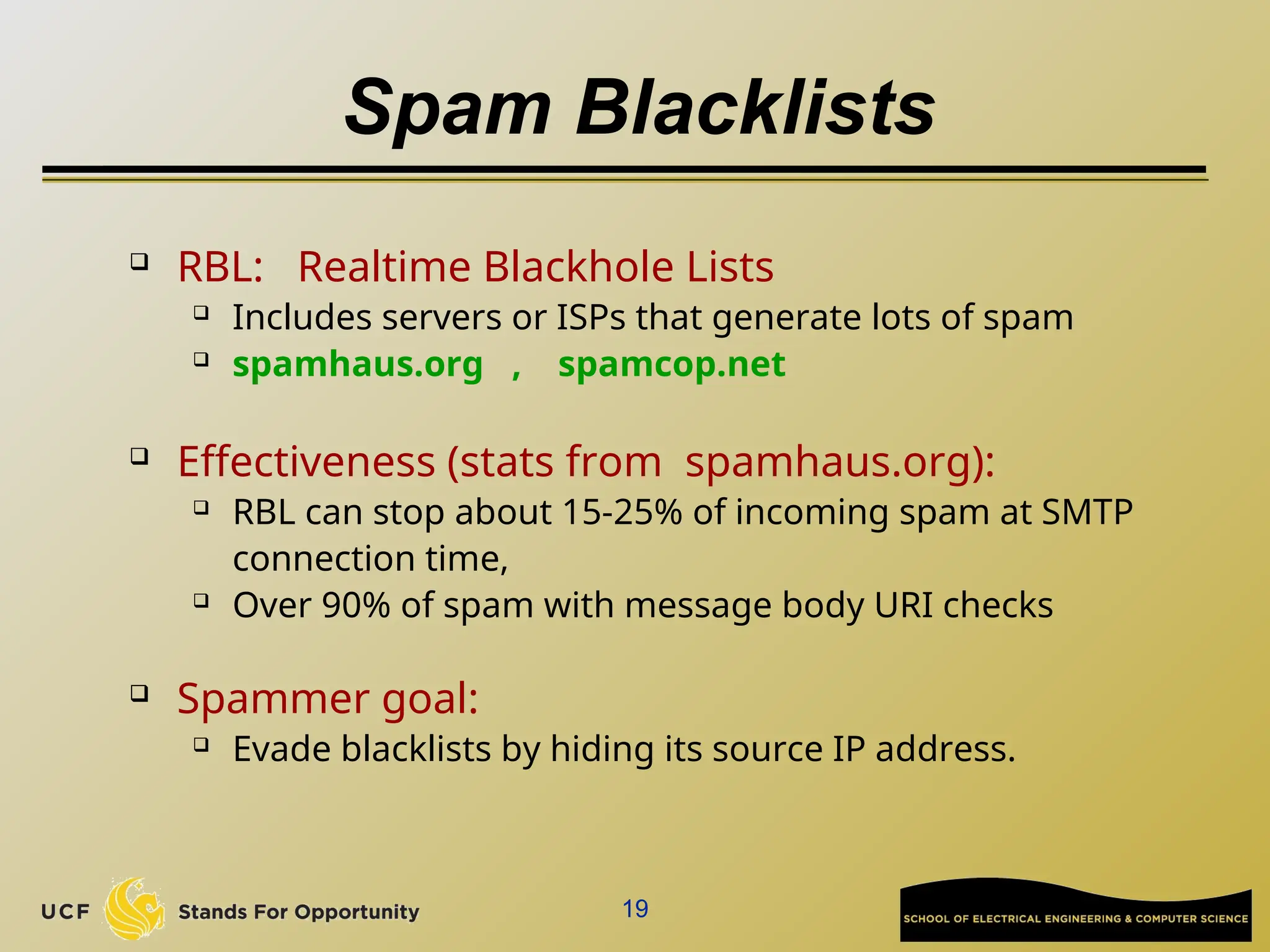
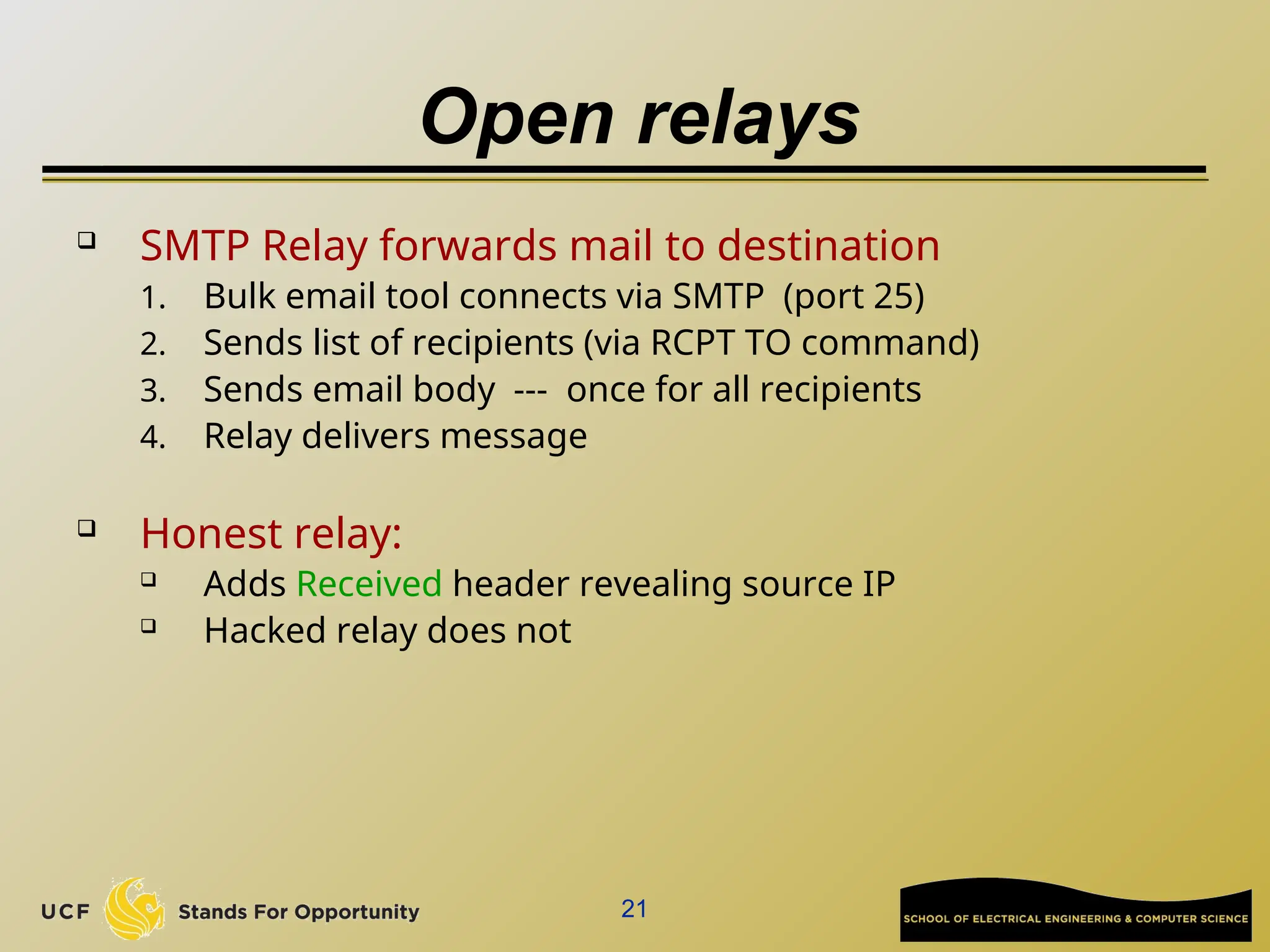
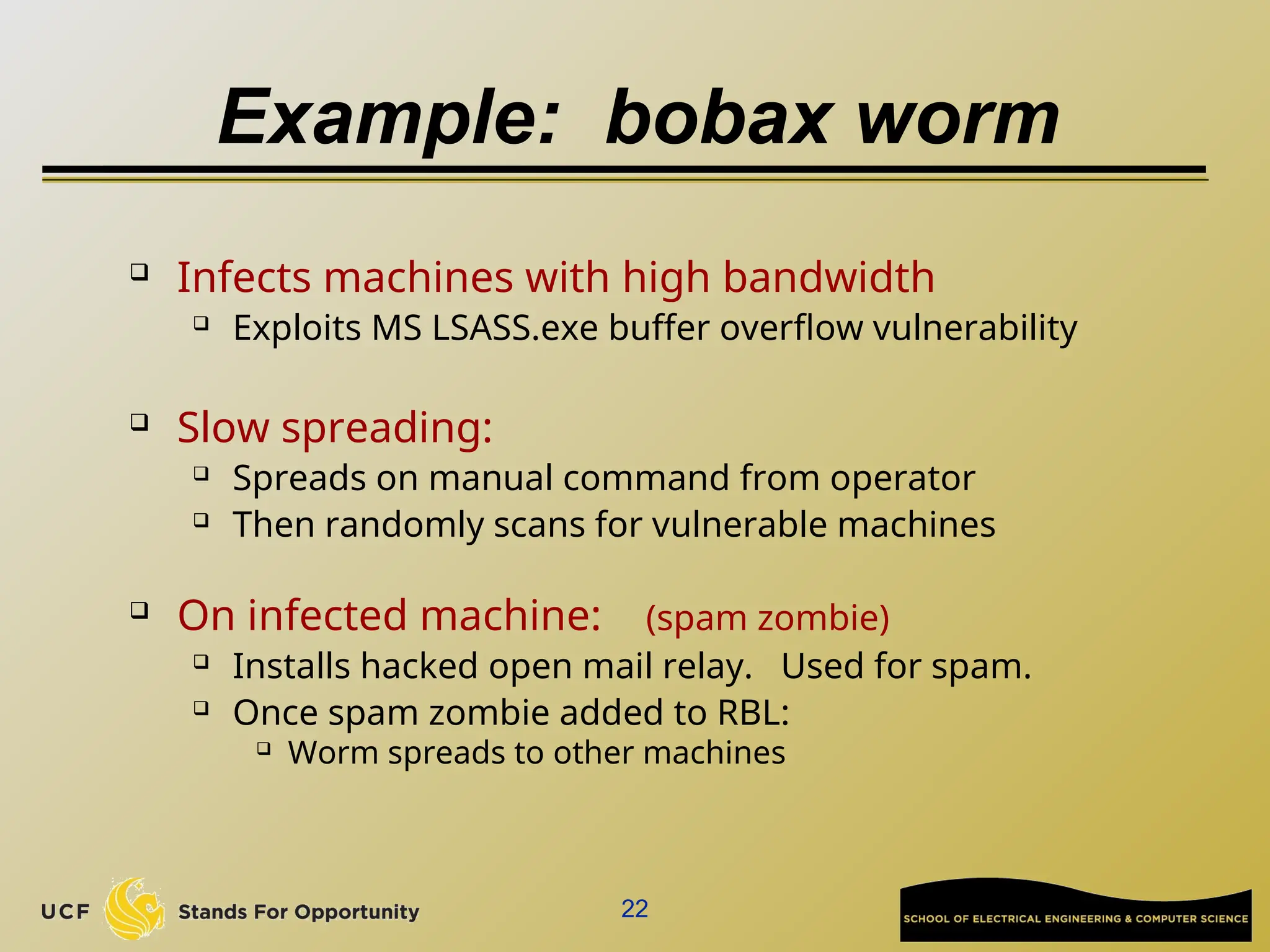
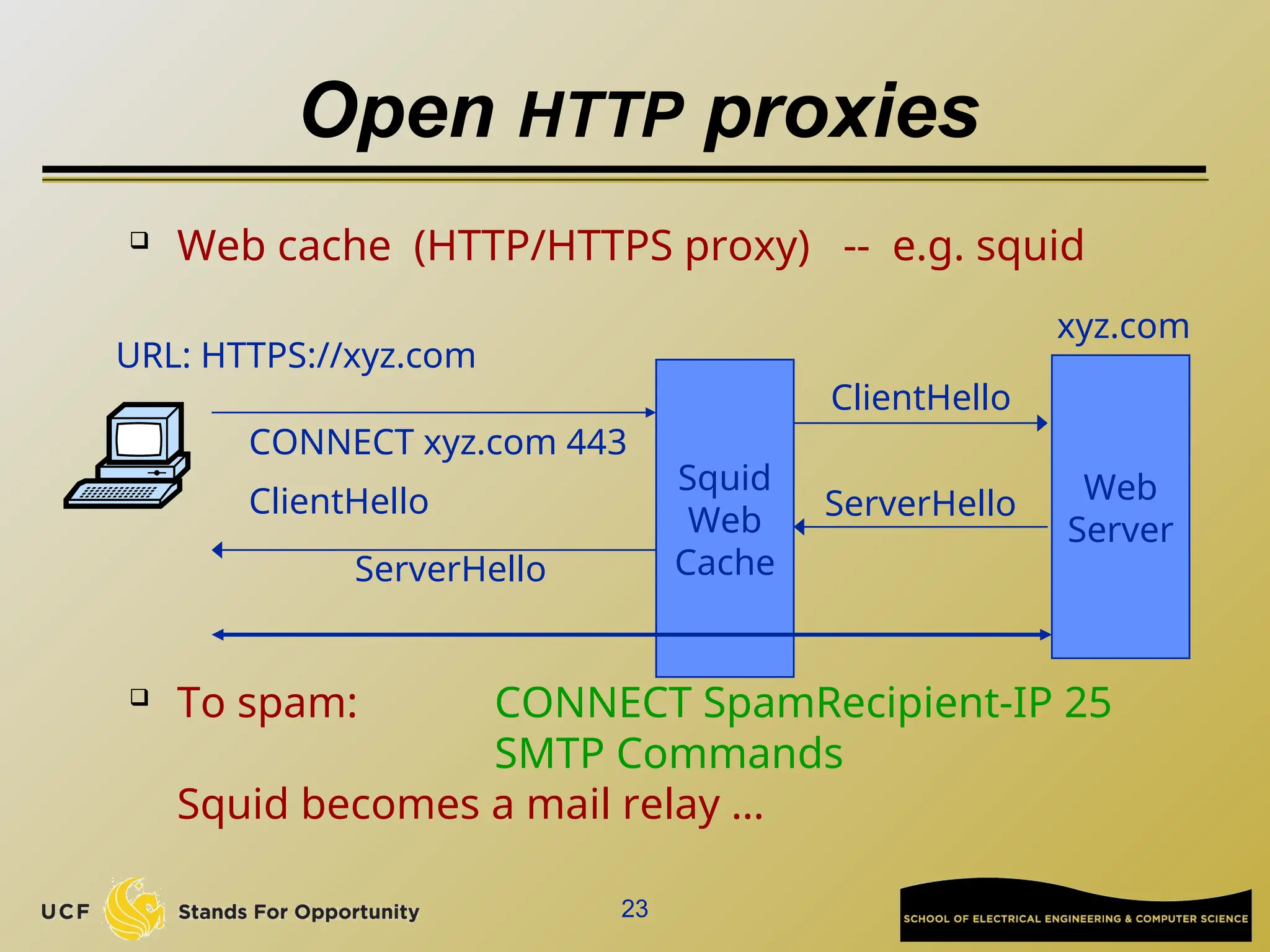
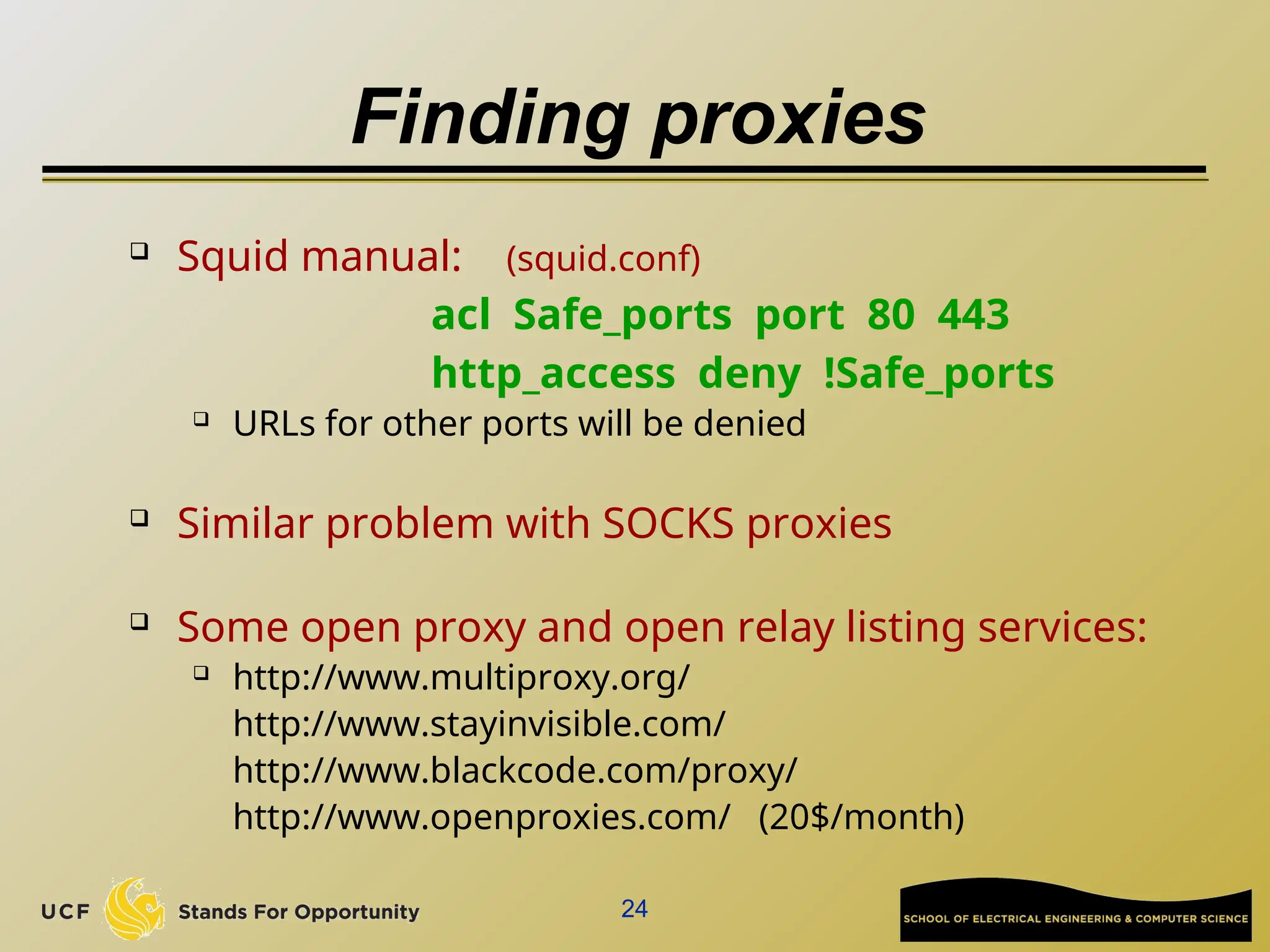
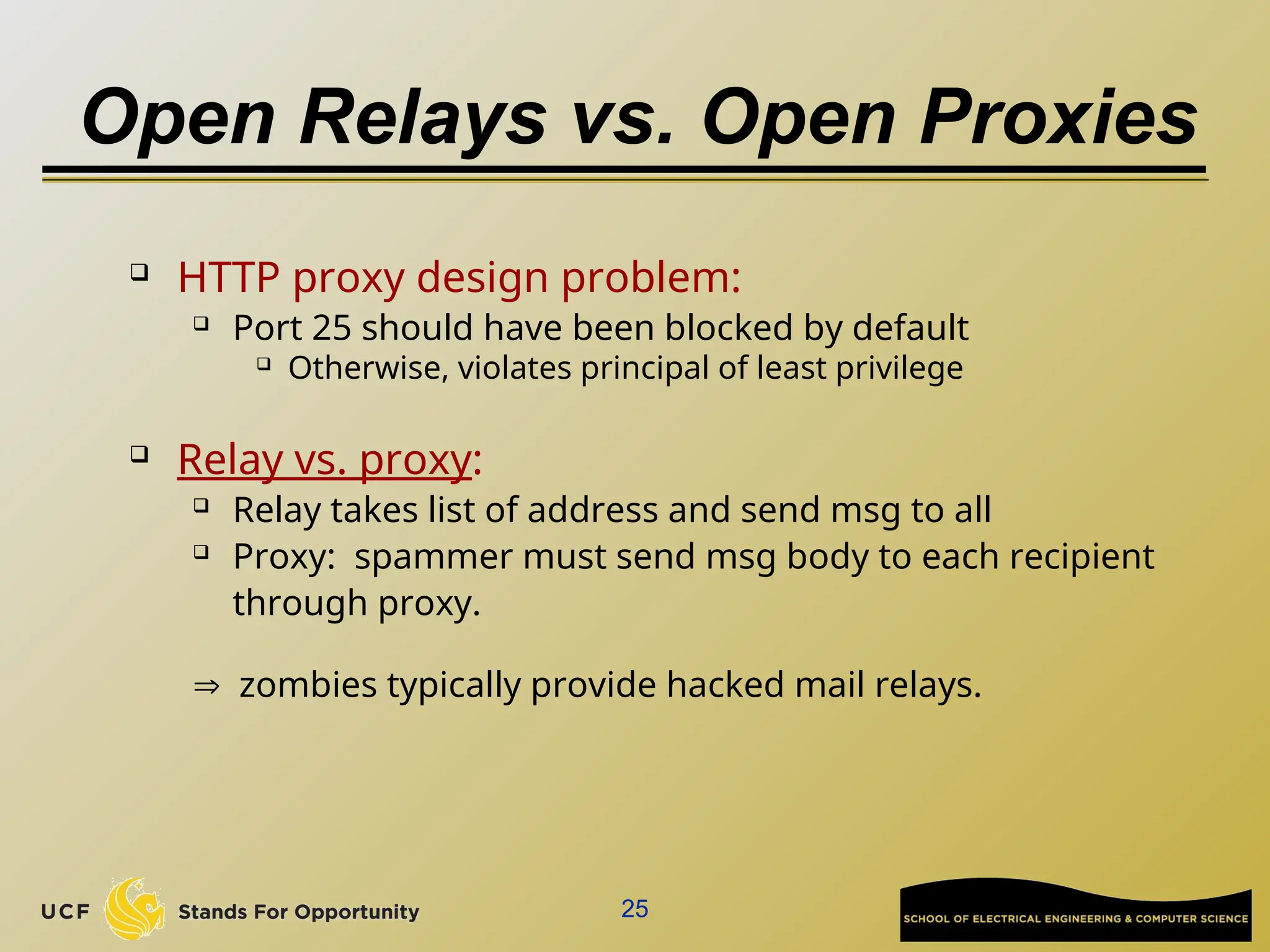
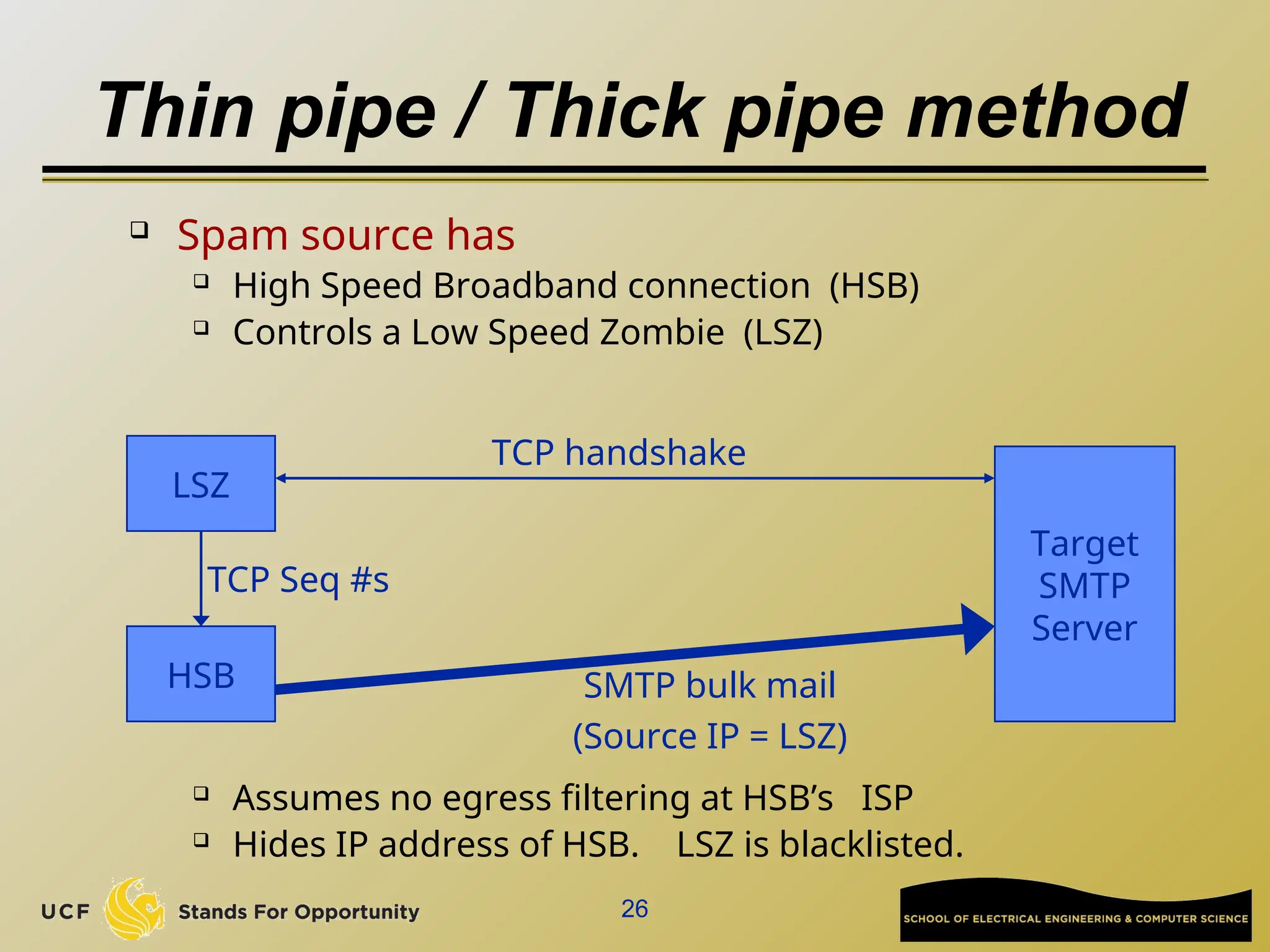
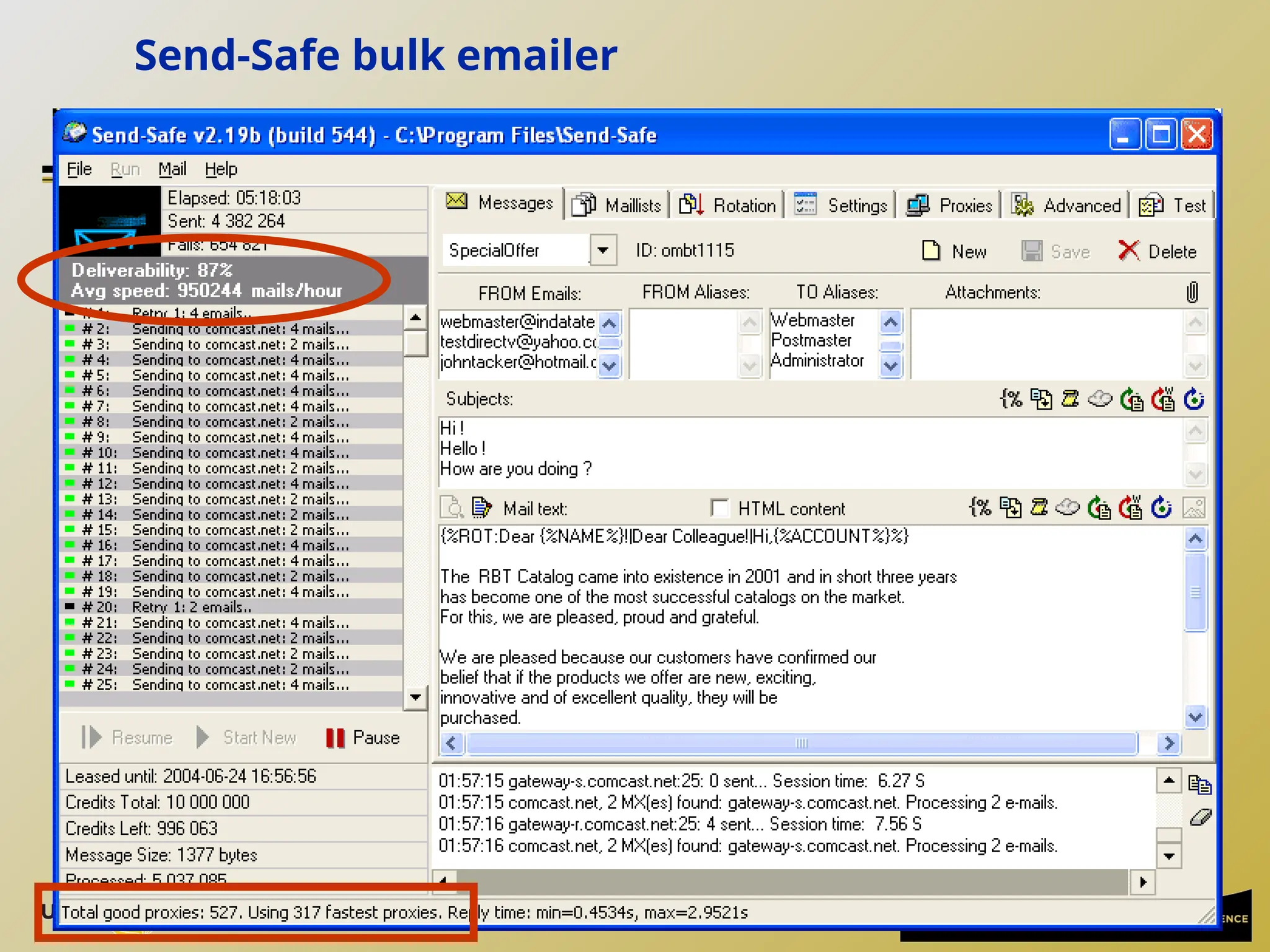
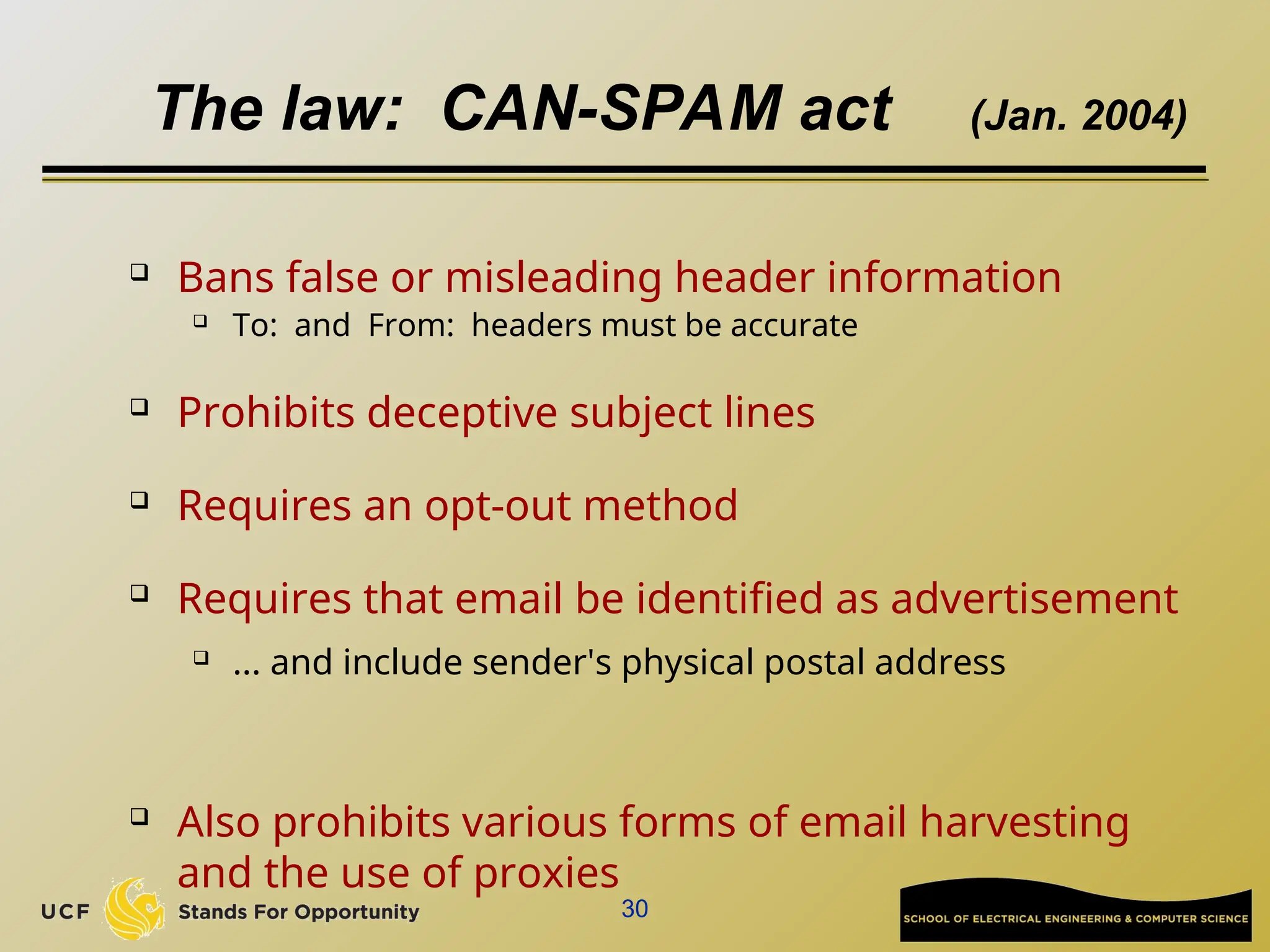
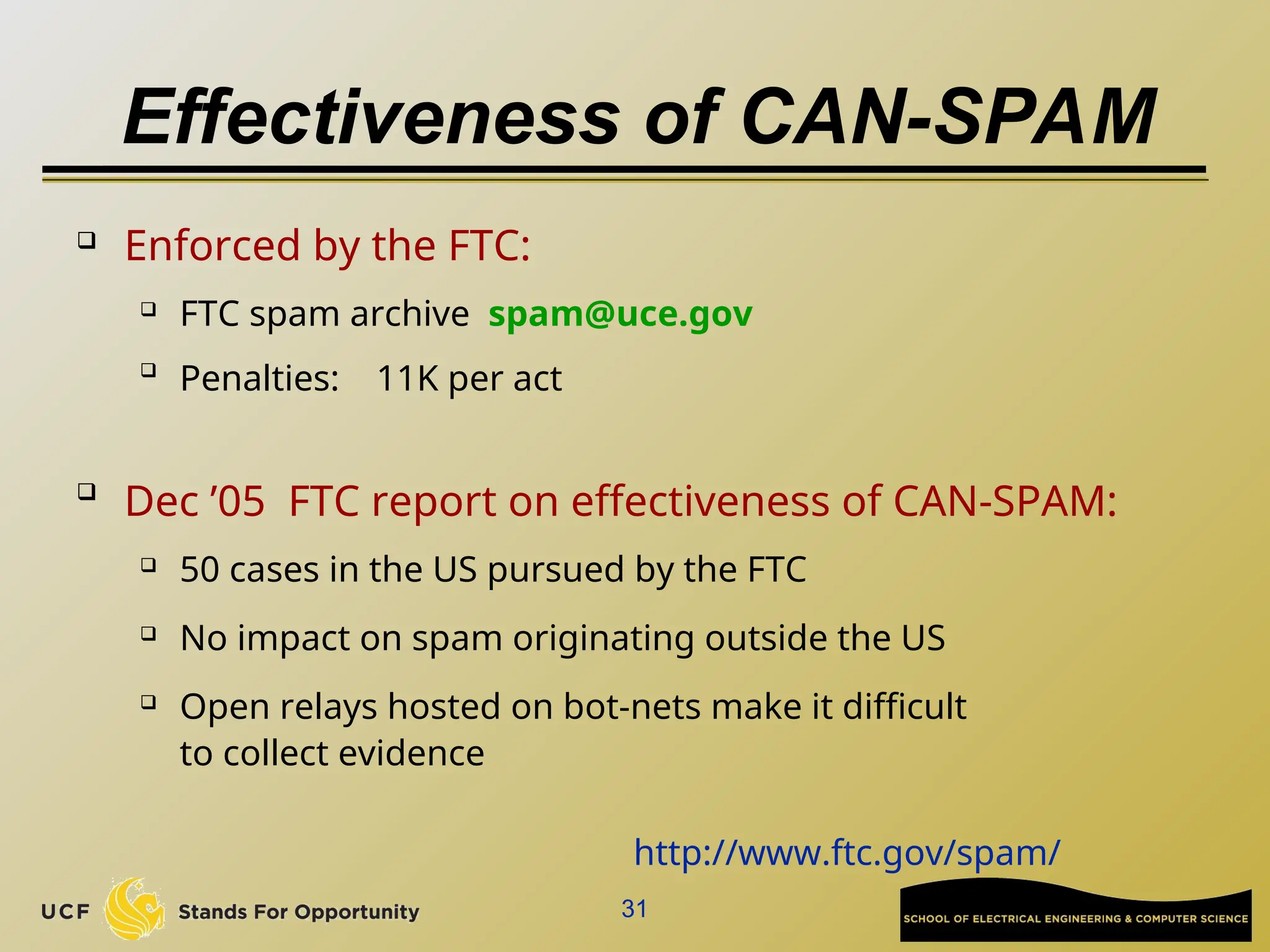
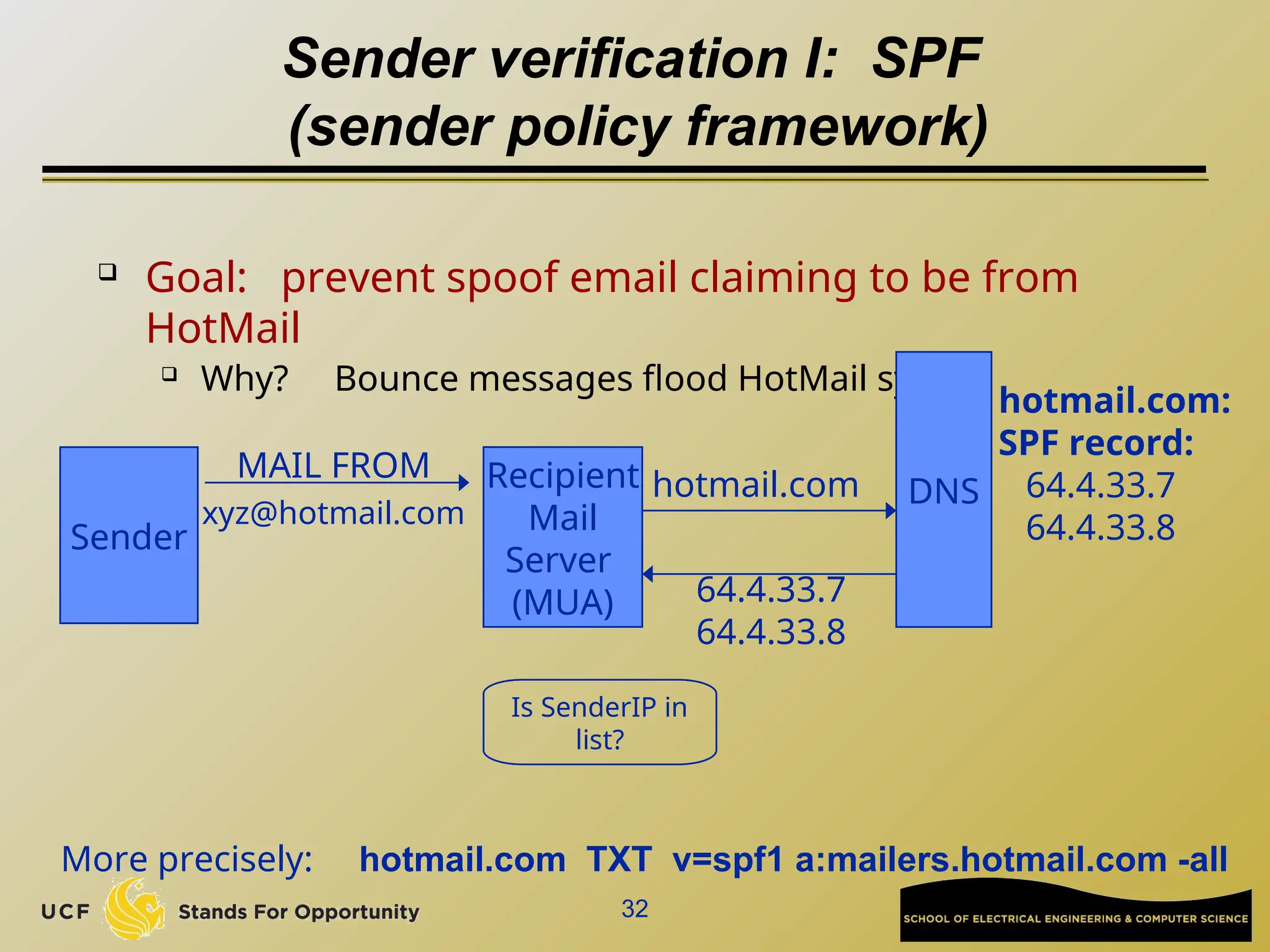
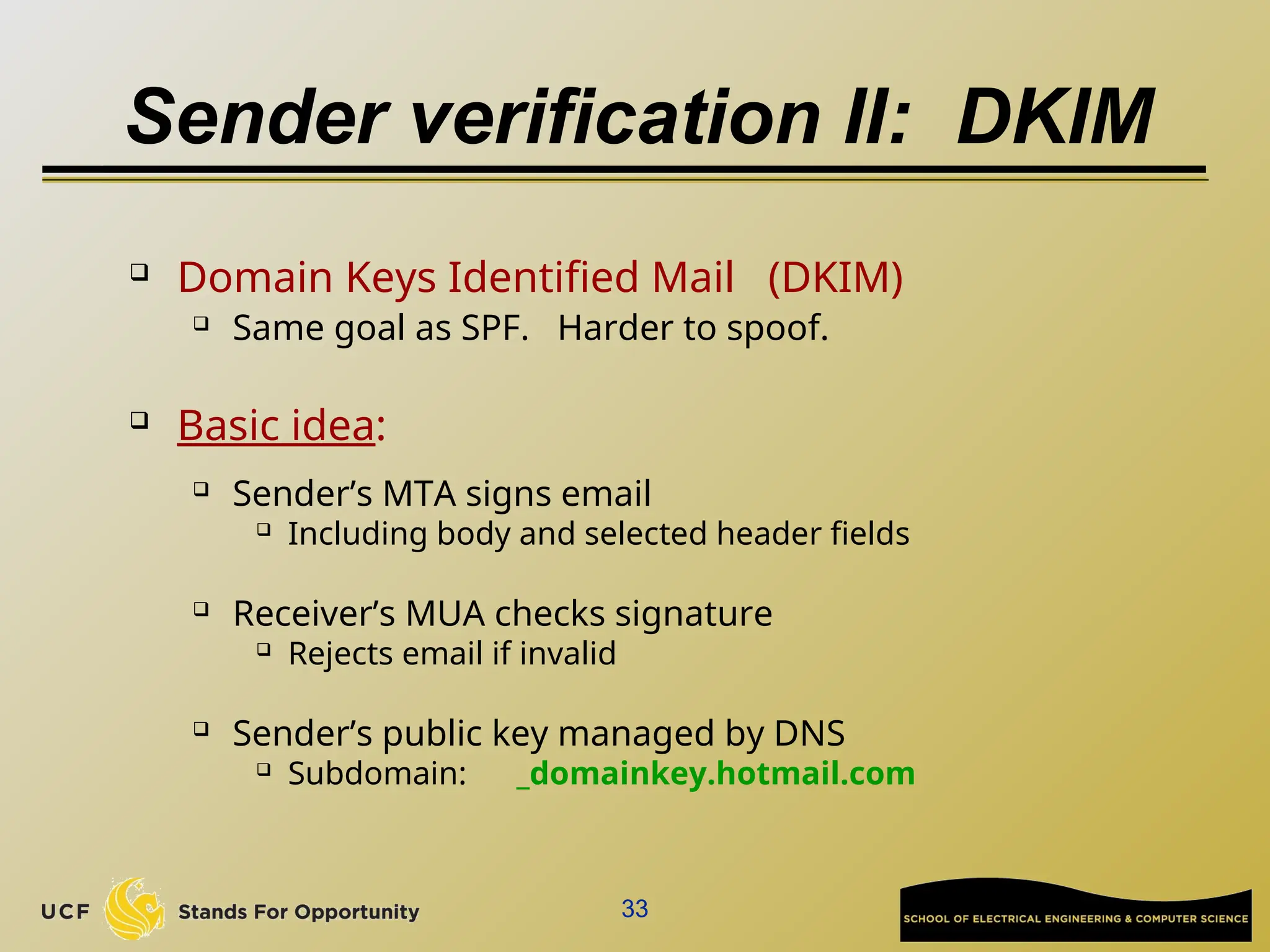
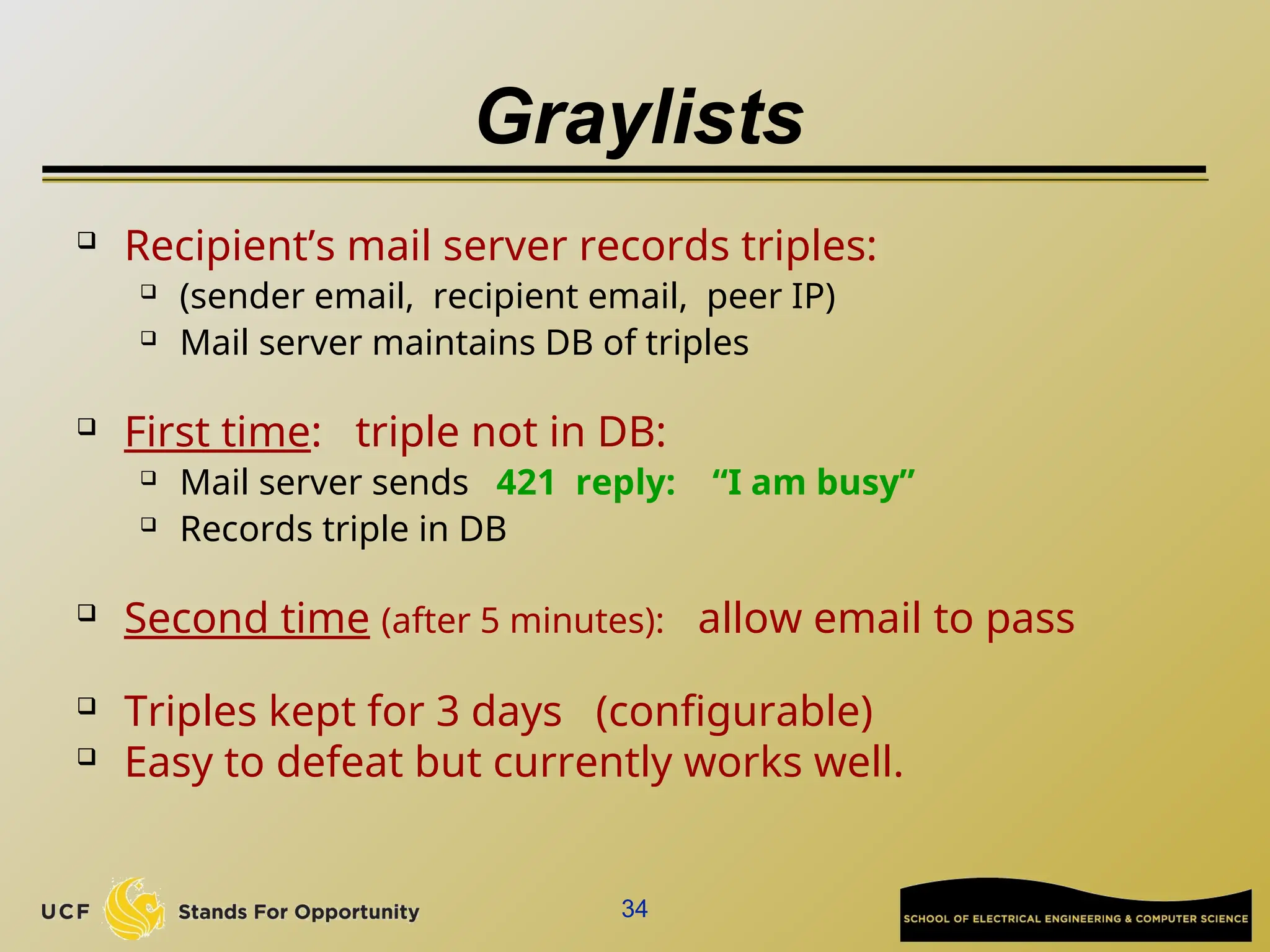
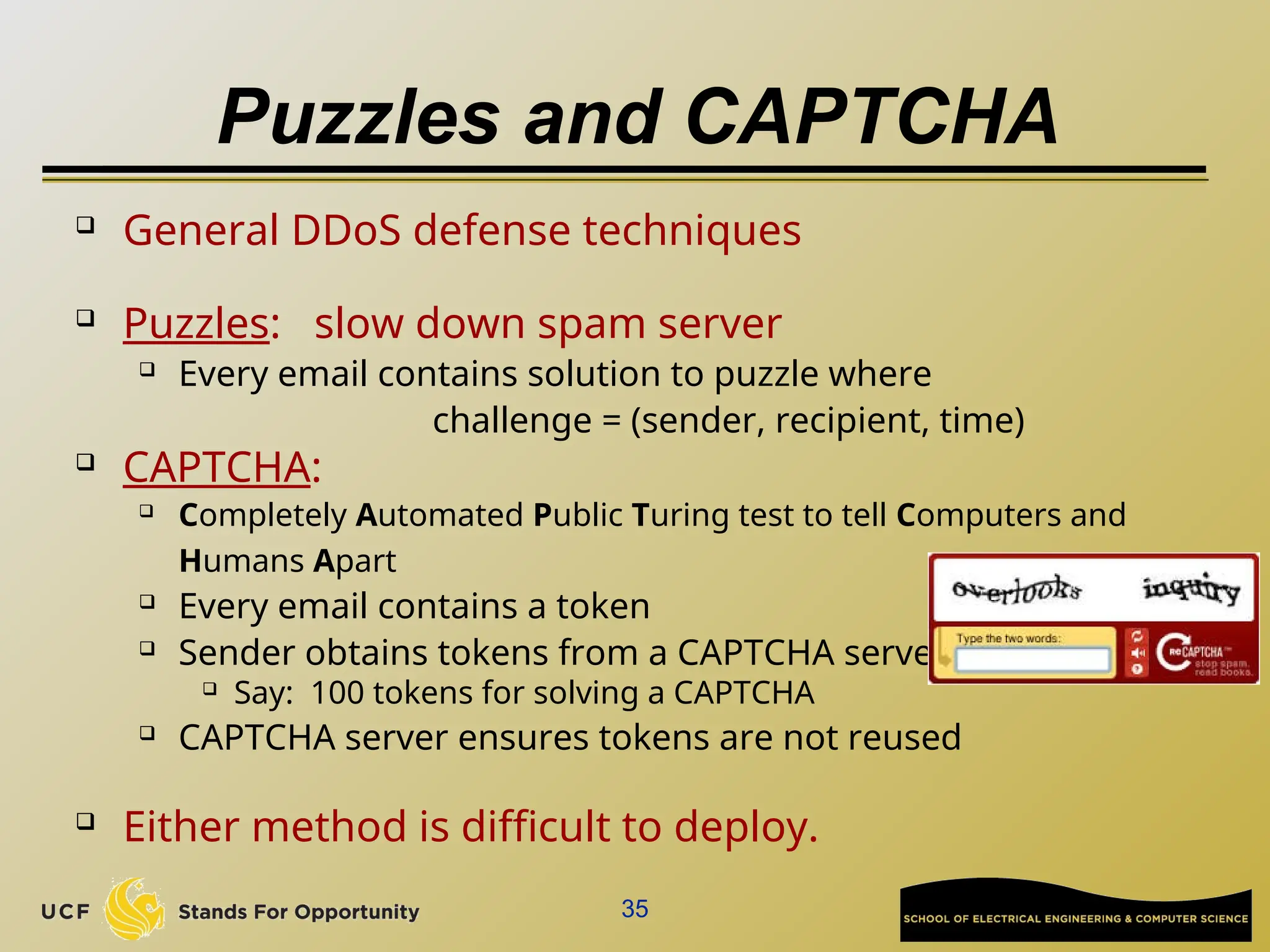
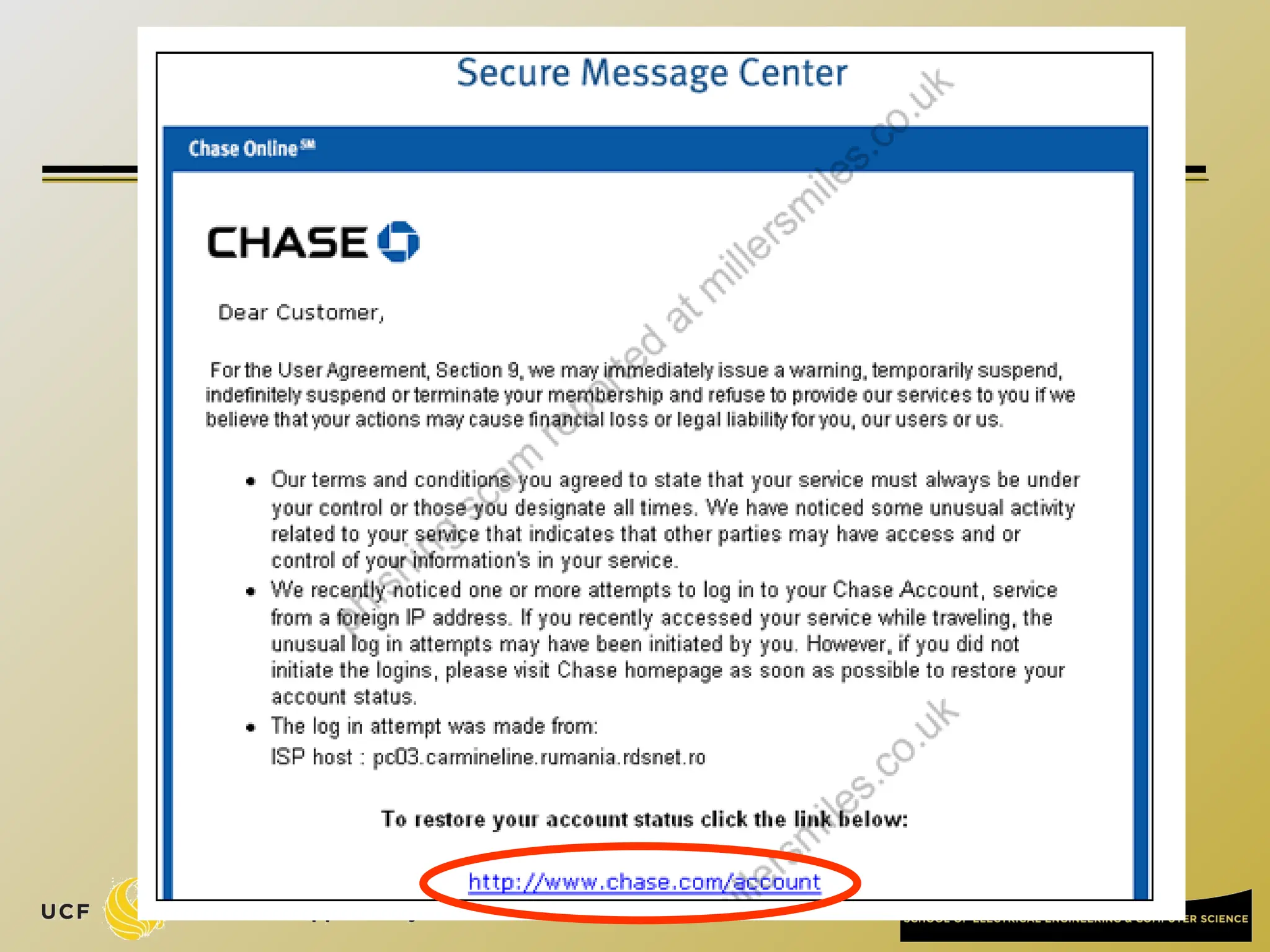
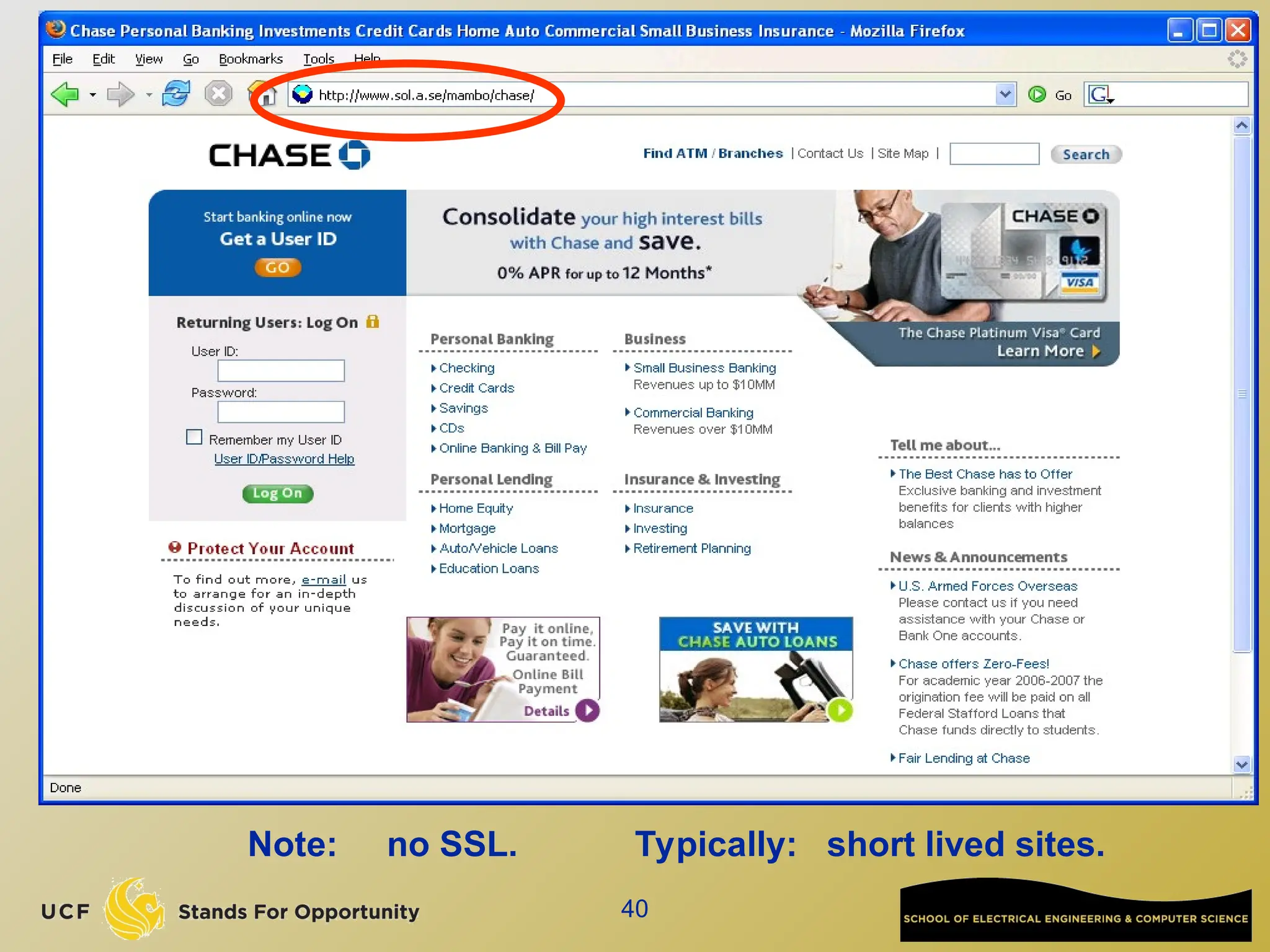
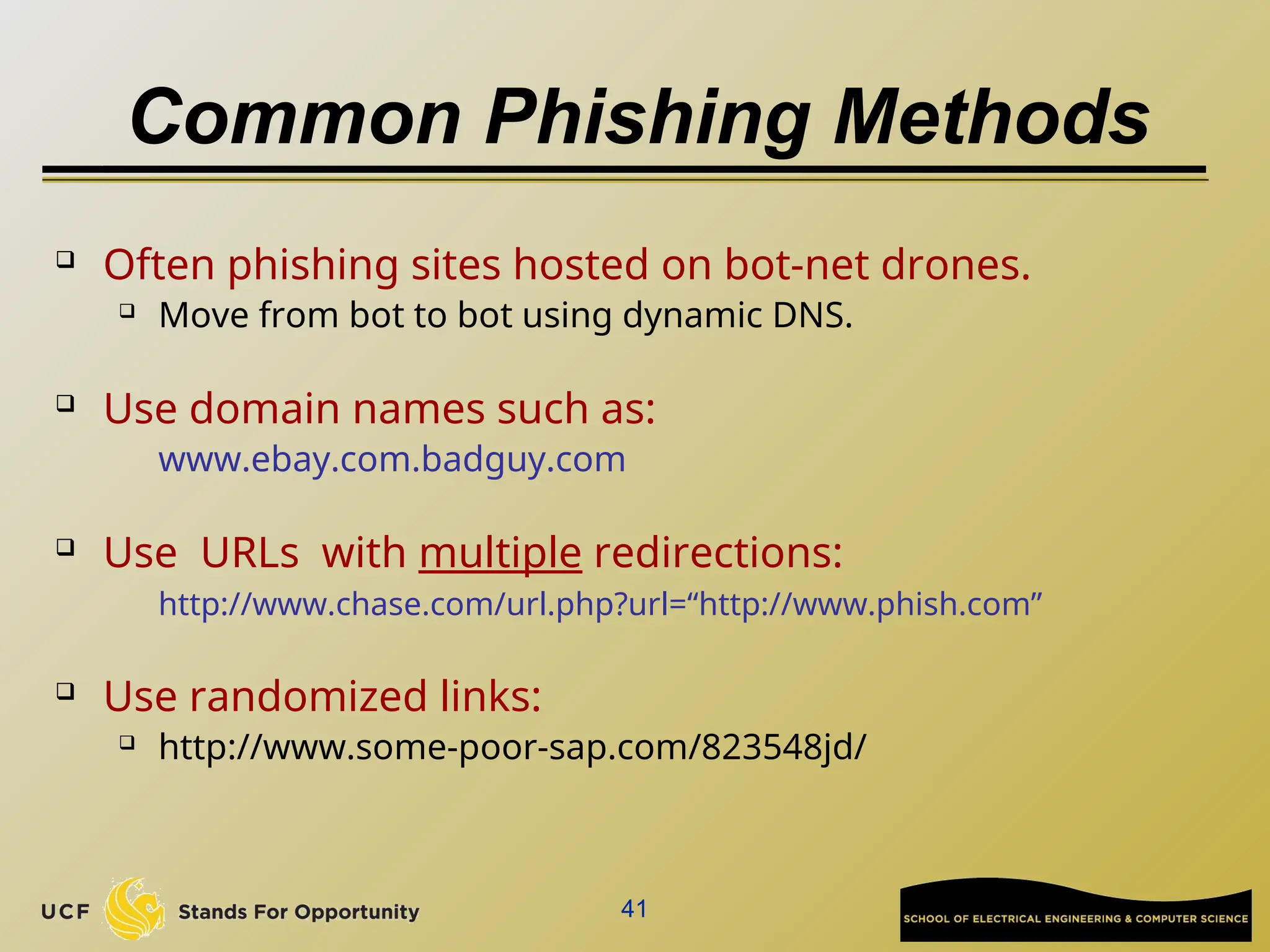
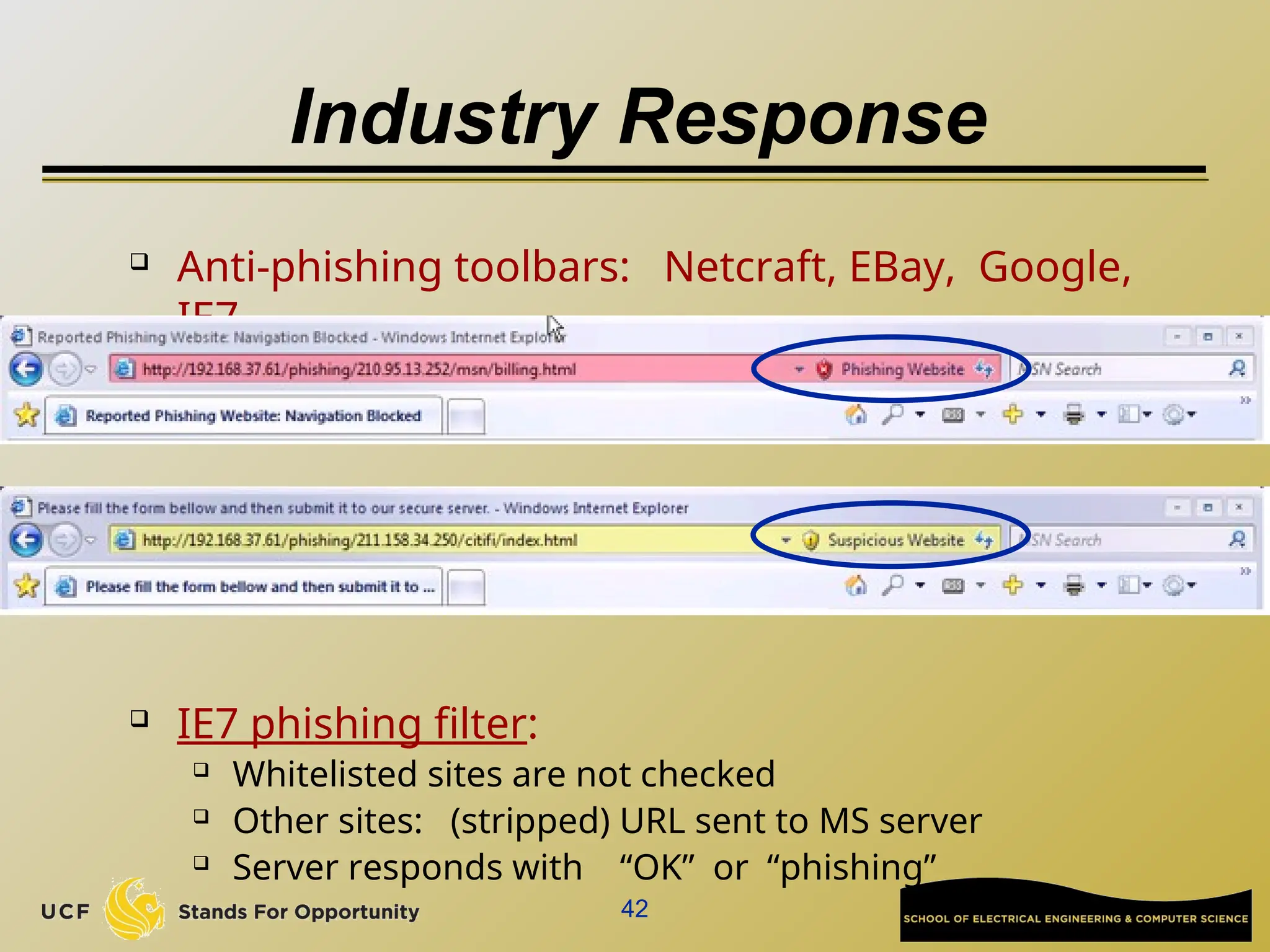
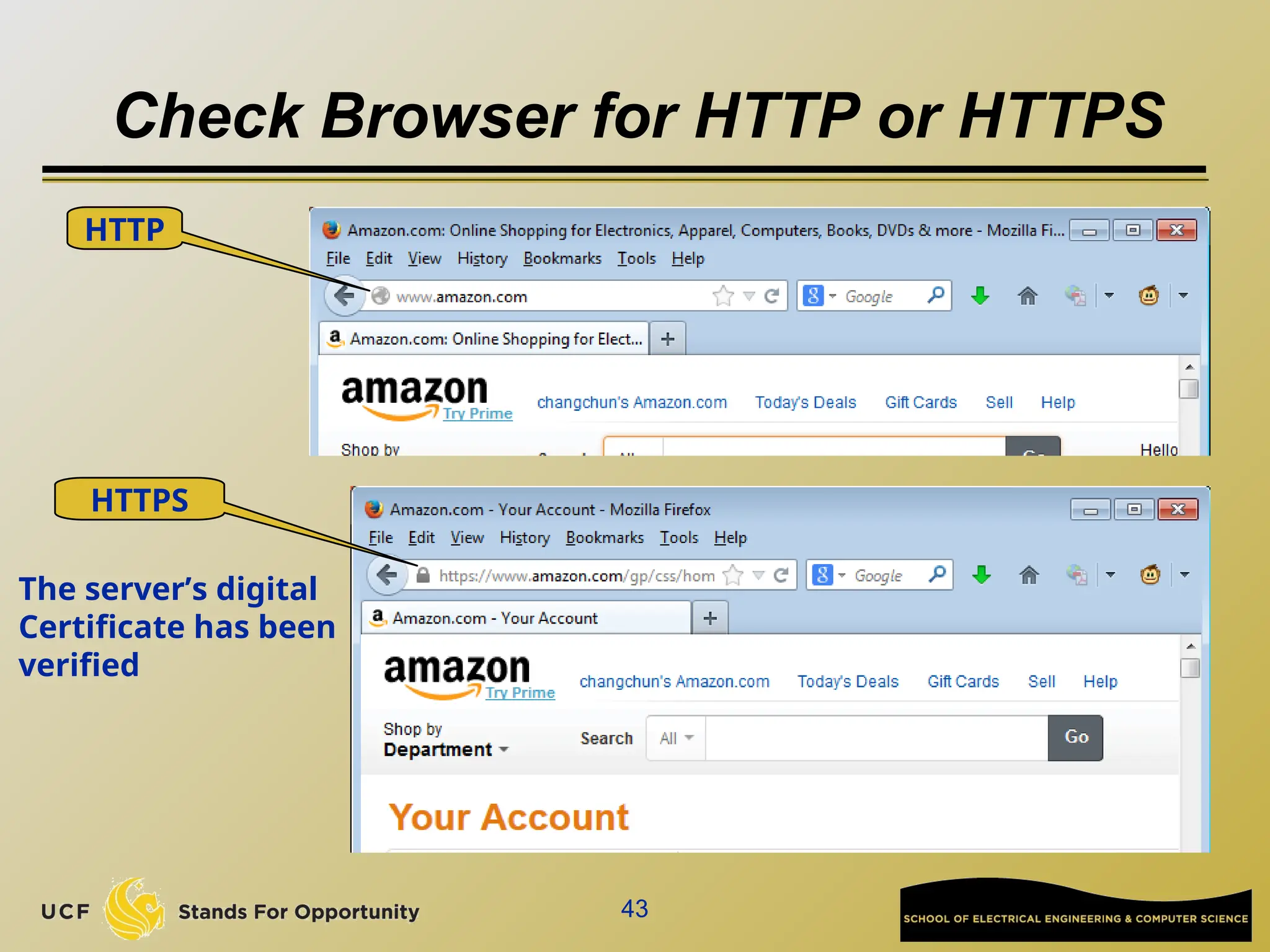
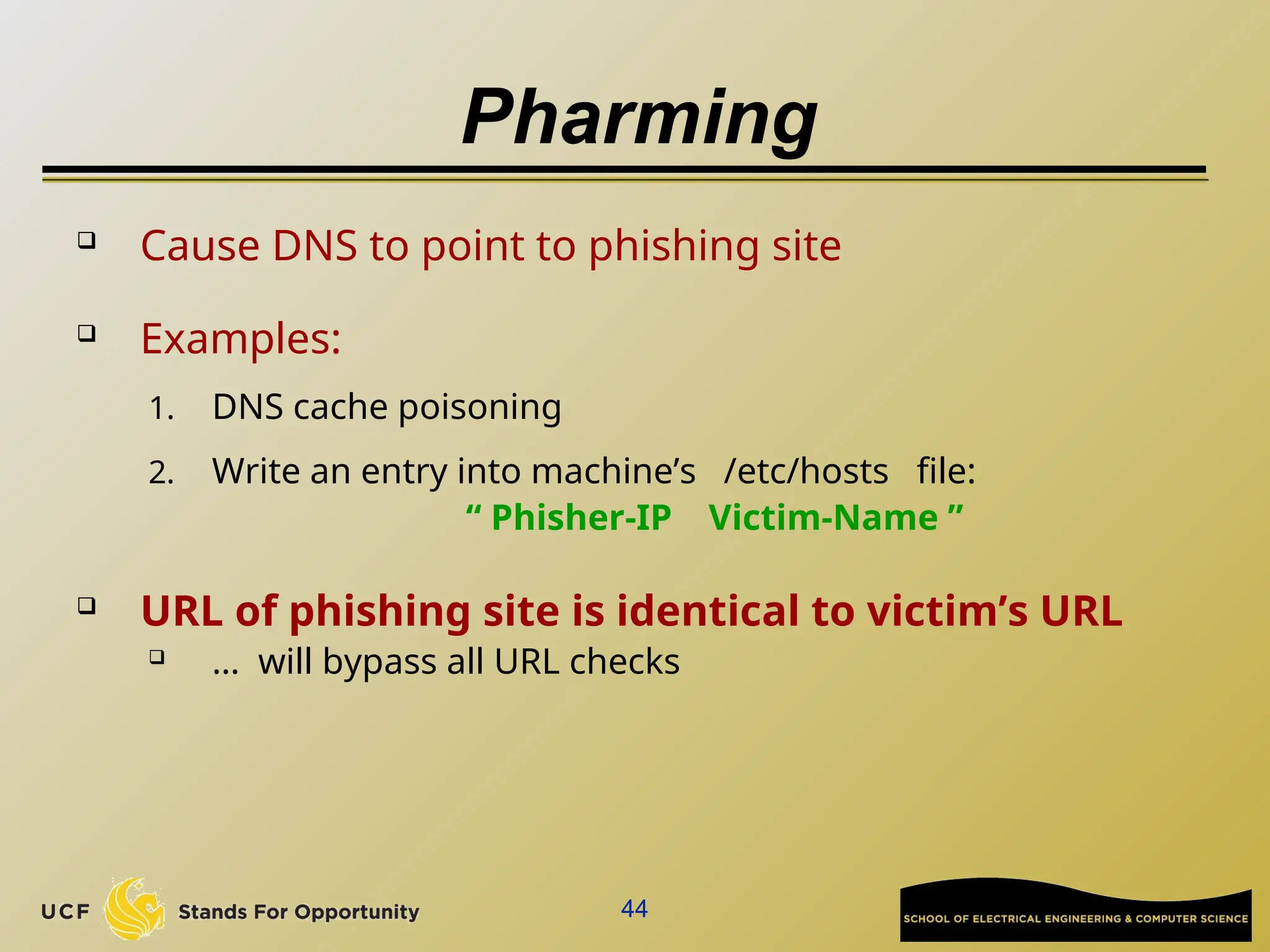
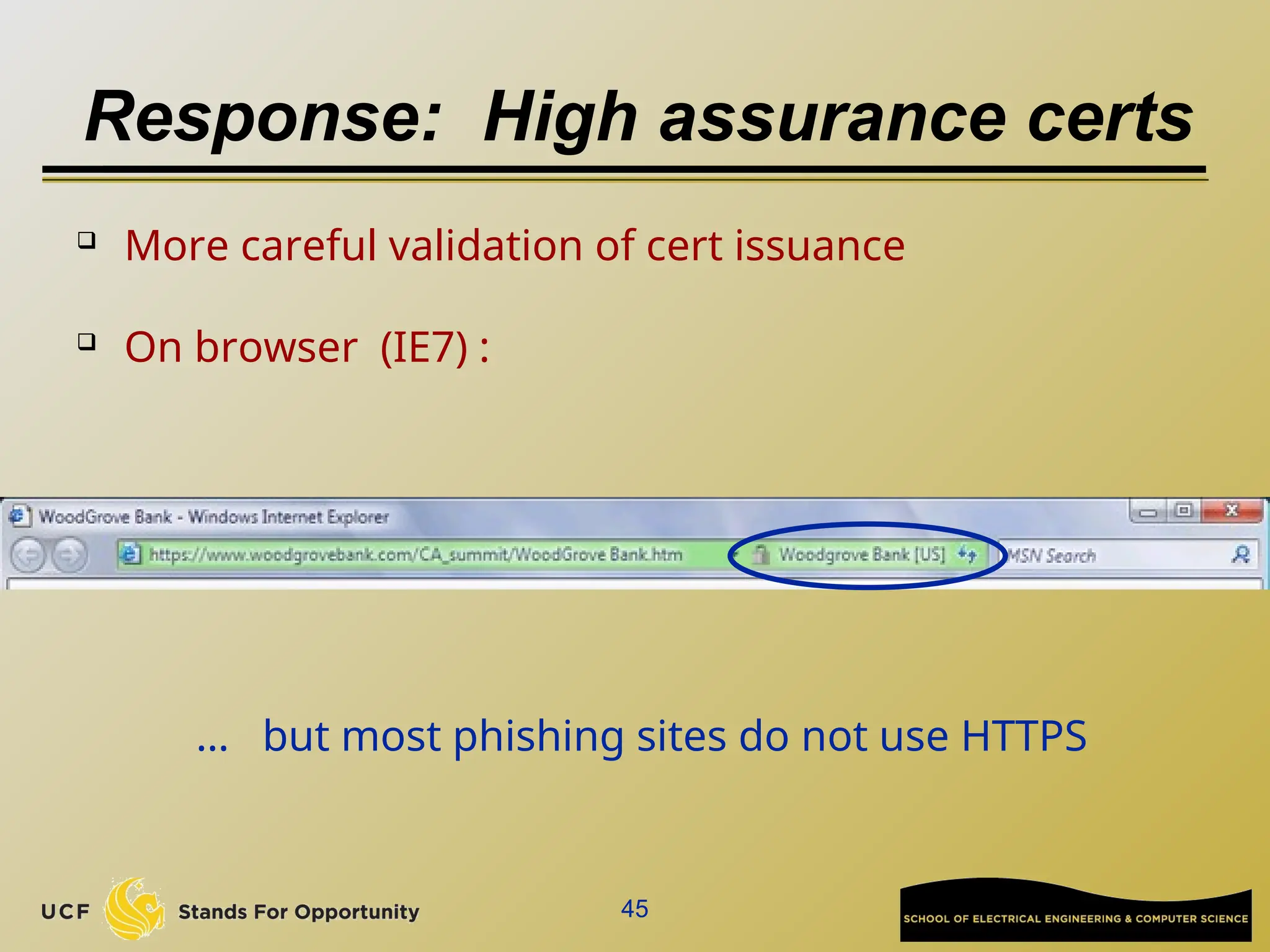
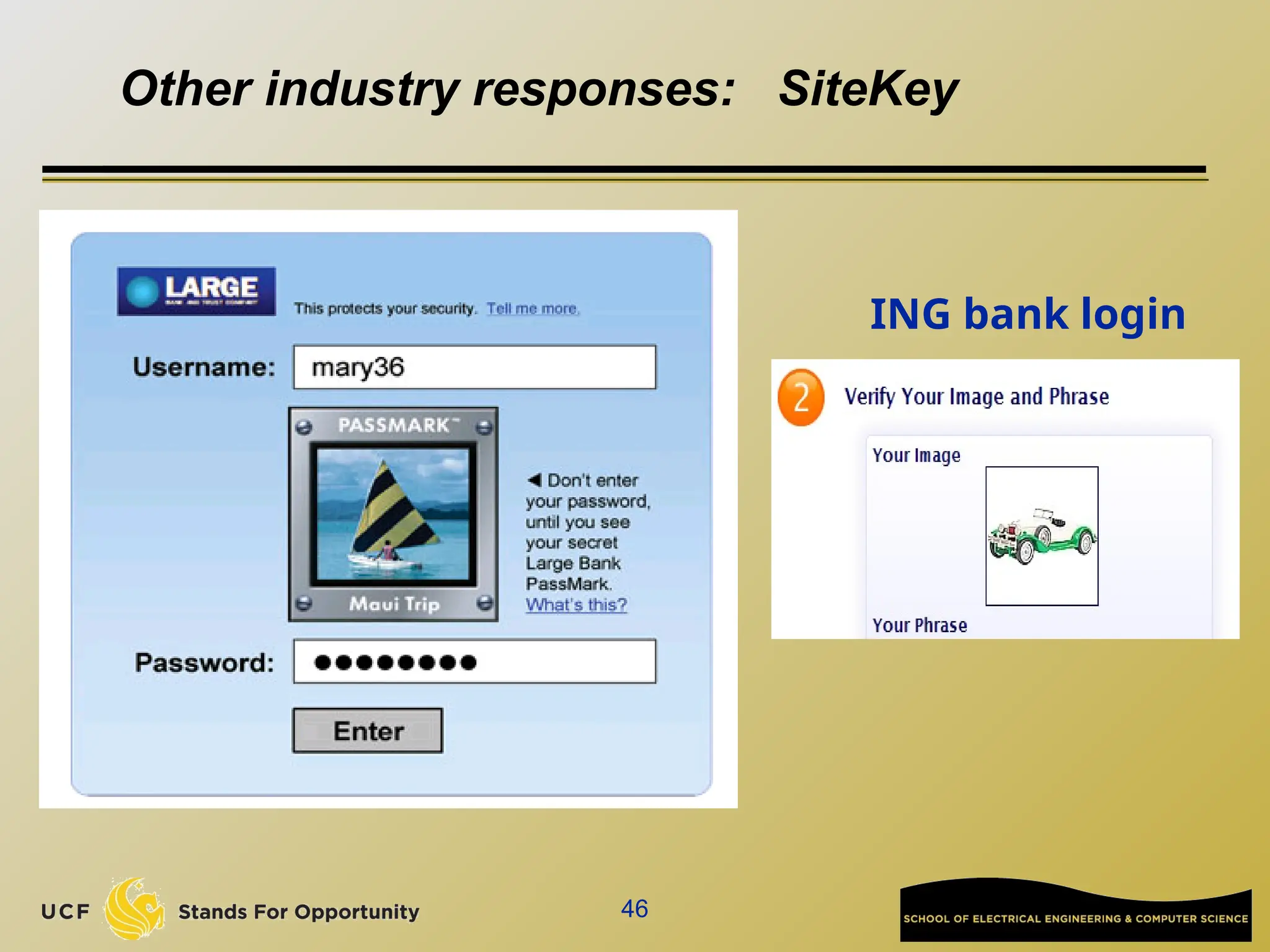
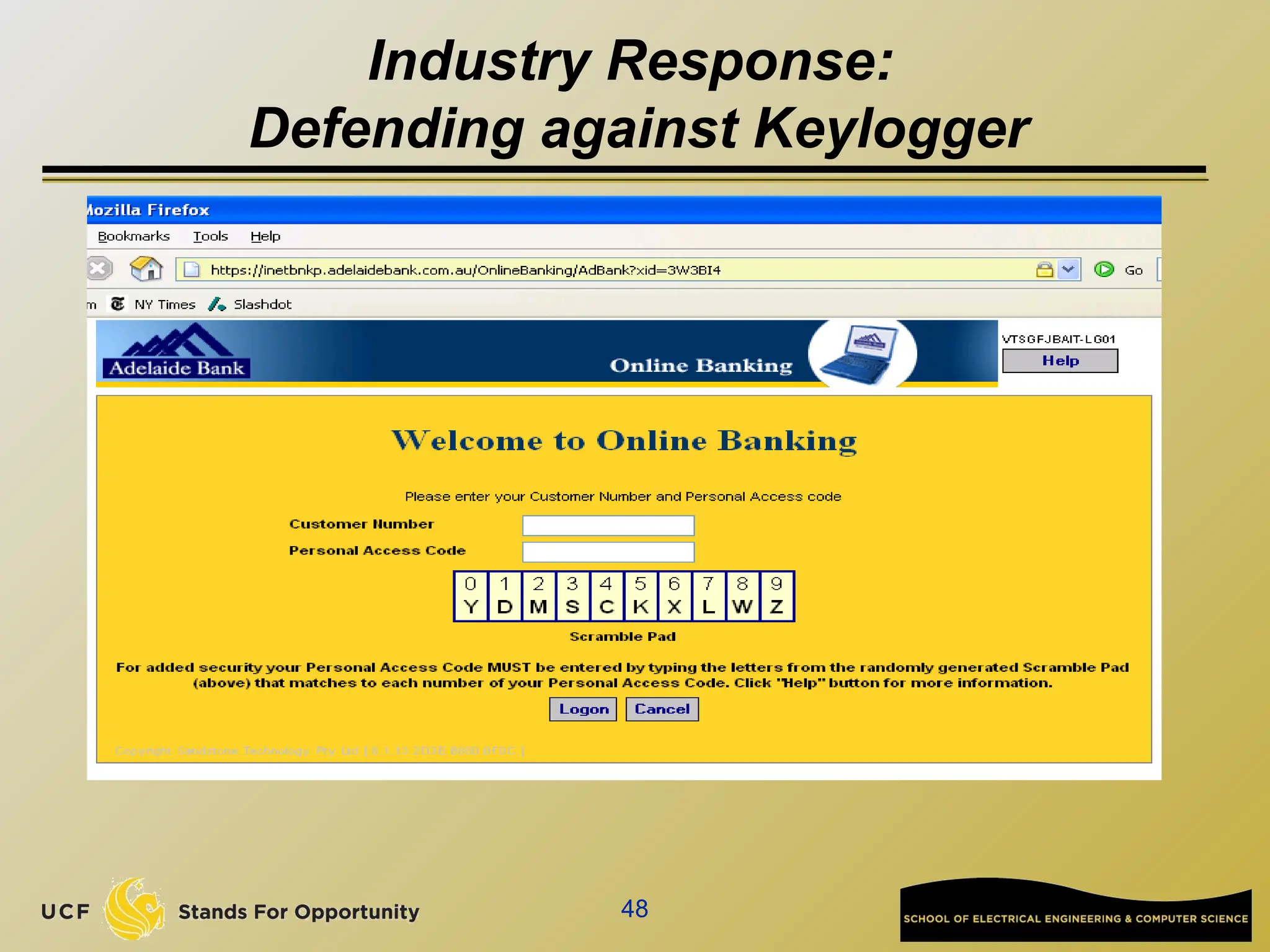
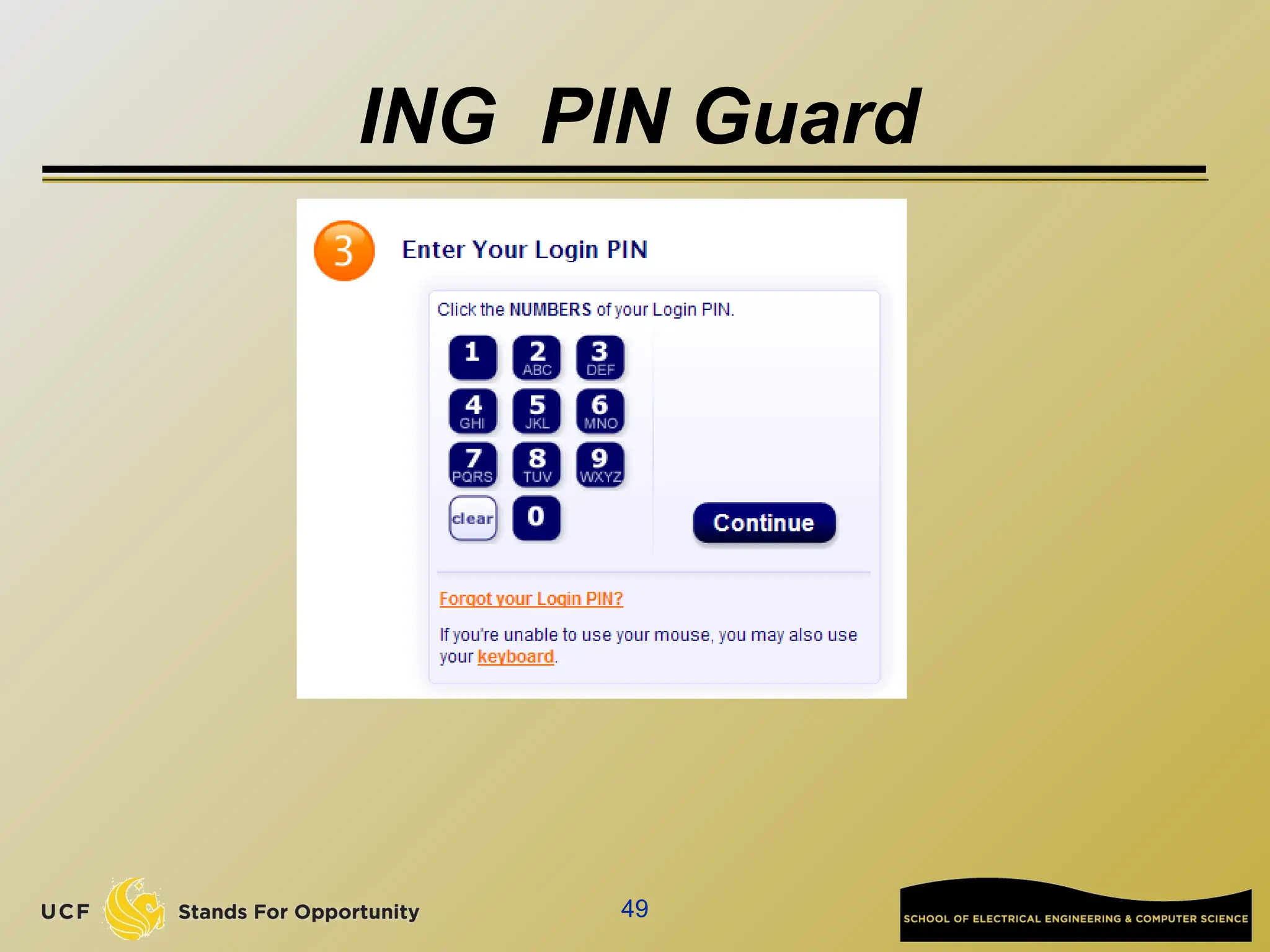
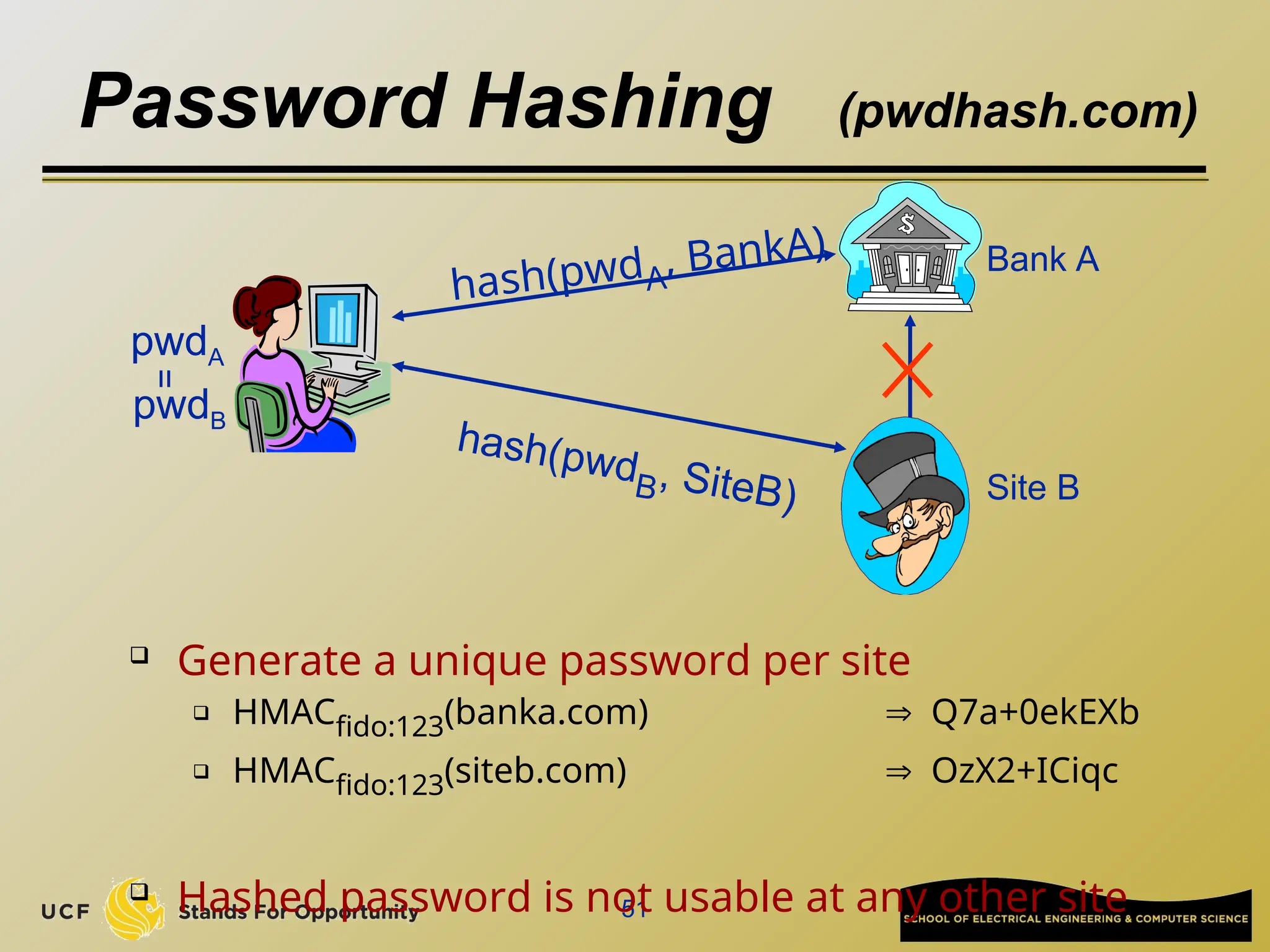
The document discusses the operation and vulnerabilities of email systems, highlighting the SMTP protocol, spam and phishing techniques, and various email security measures like SPF and DKIM. It also covers the evolution of email relays, the impact of spam regulations such as the CAN-SPAM Act, and the role of spam filters like SpamAssassin in identifying unwanted emails. Additionally, it addresses phishing methods and responses from the industry to combat such risks.