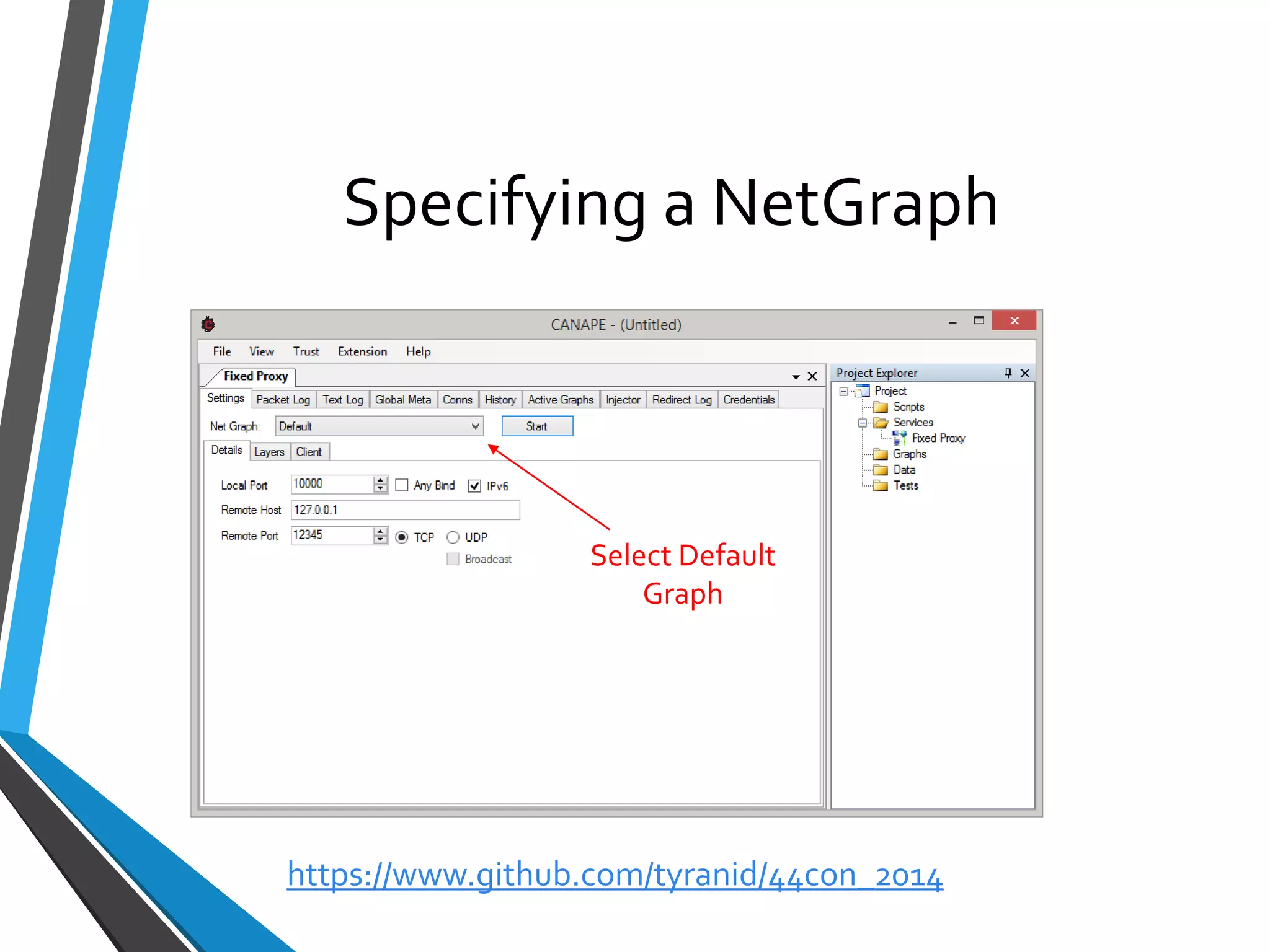
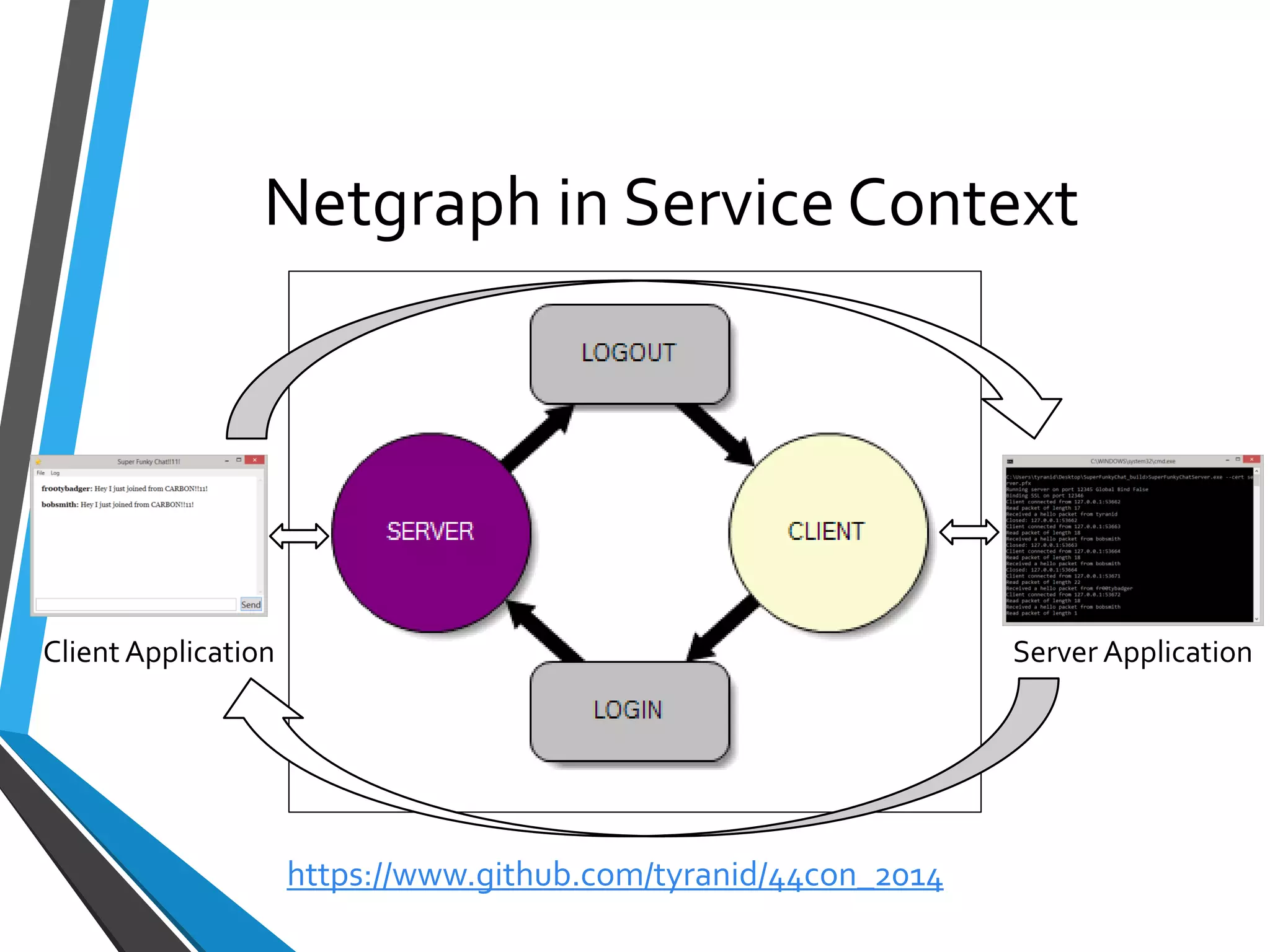
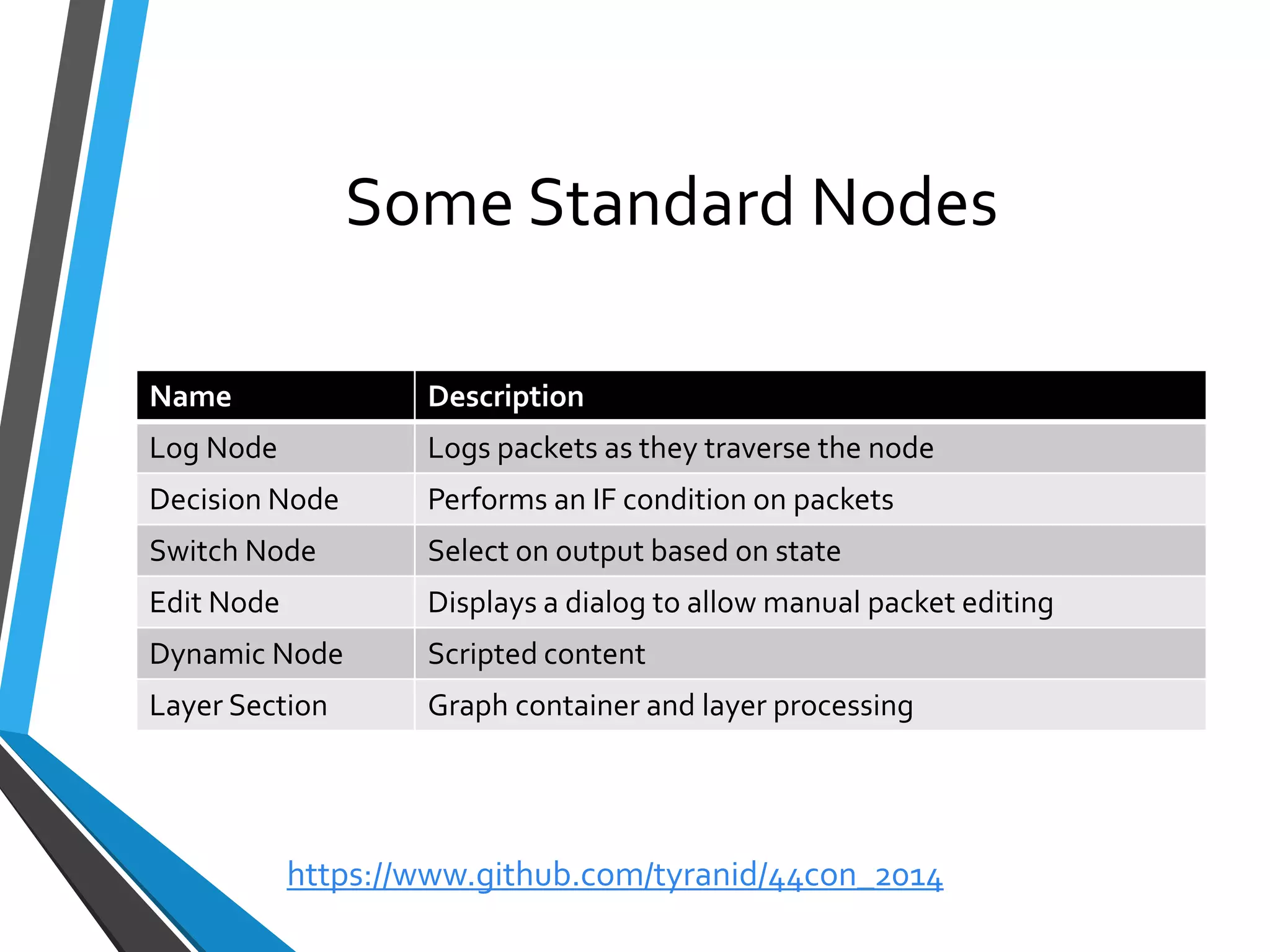
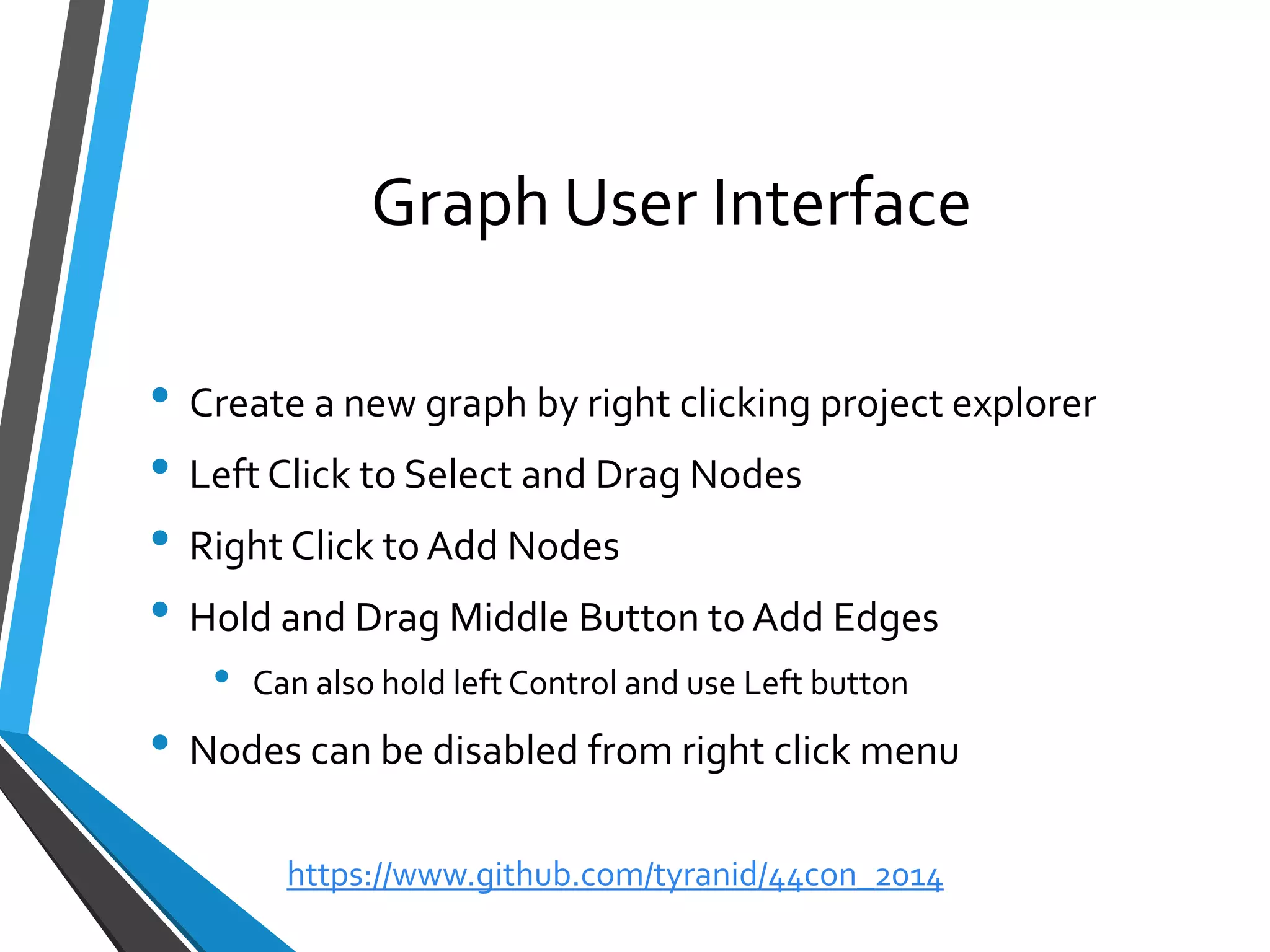
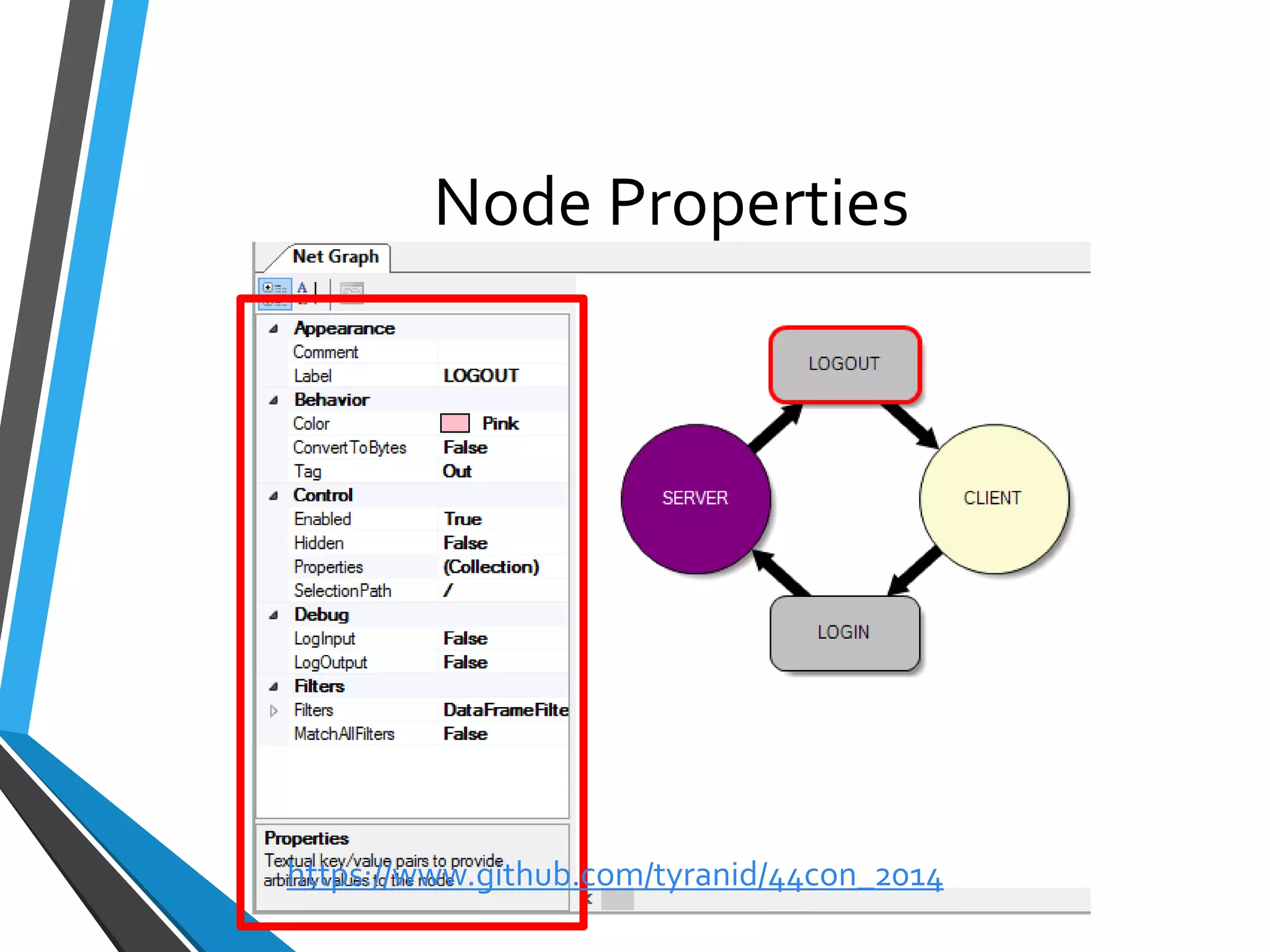
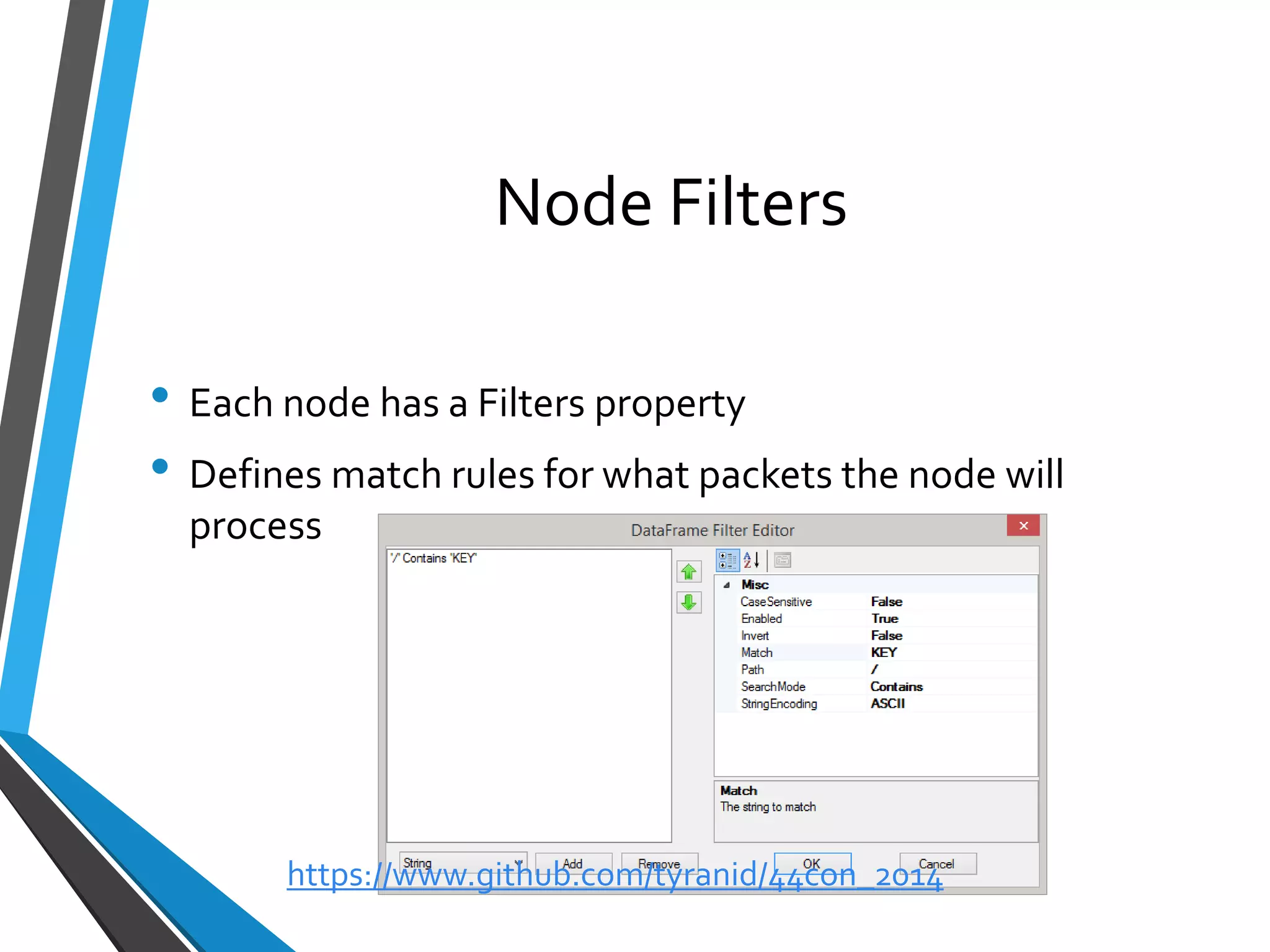
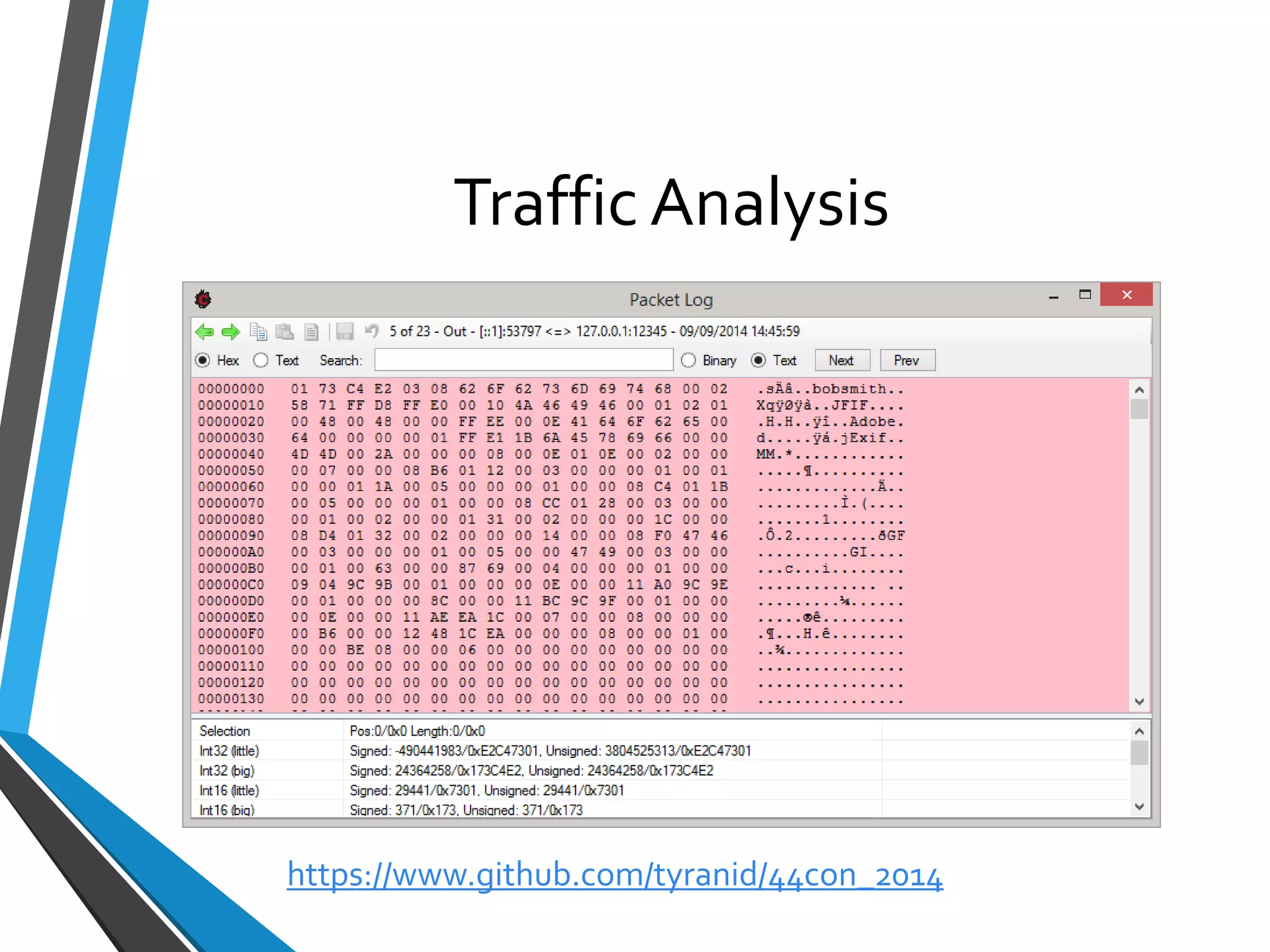
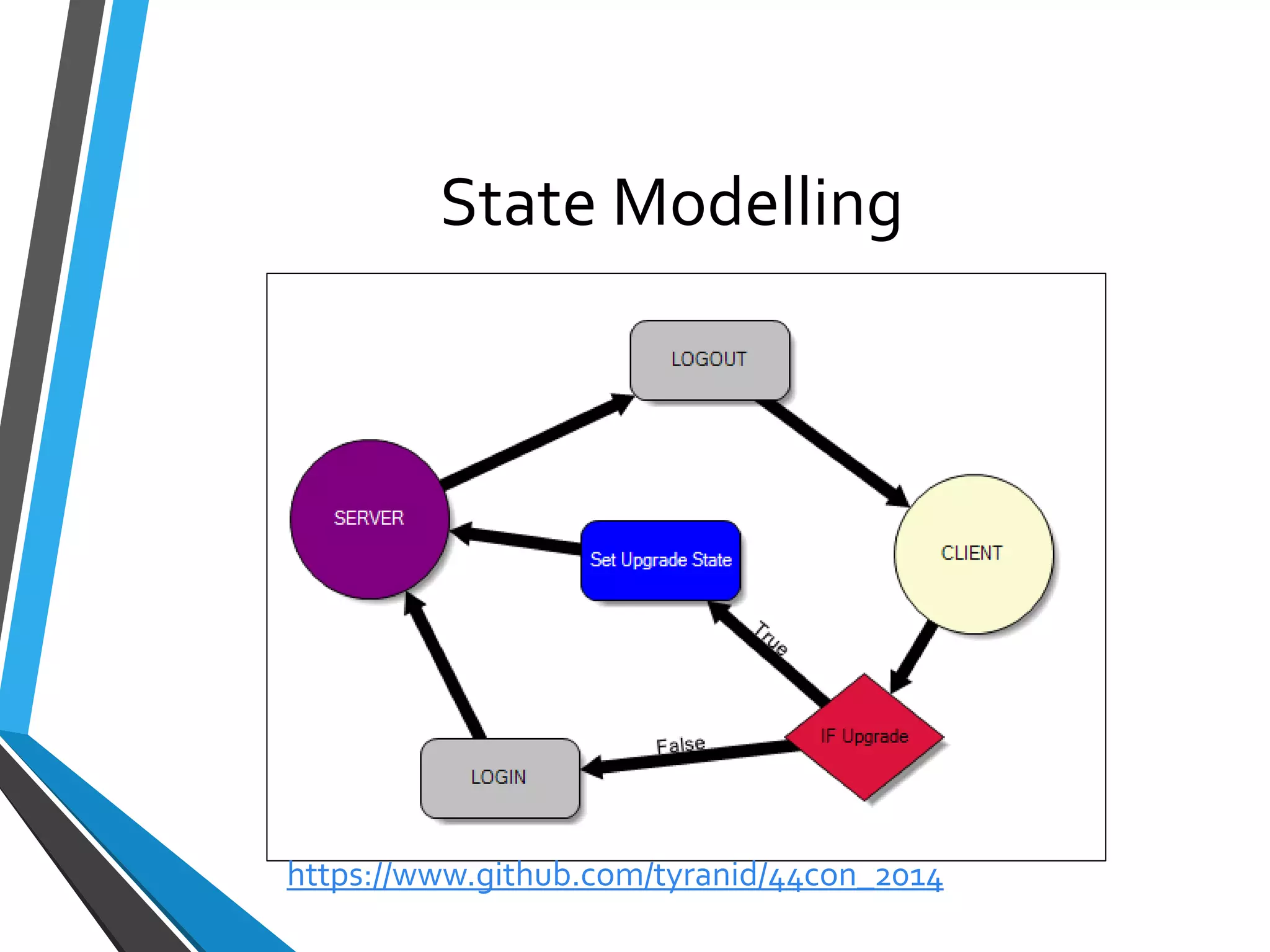
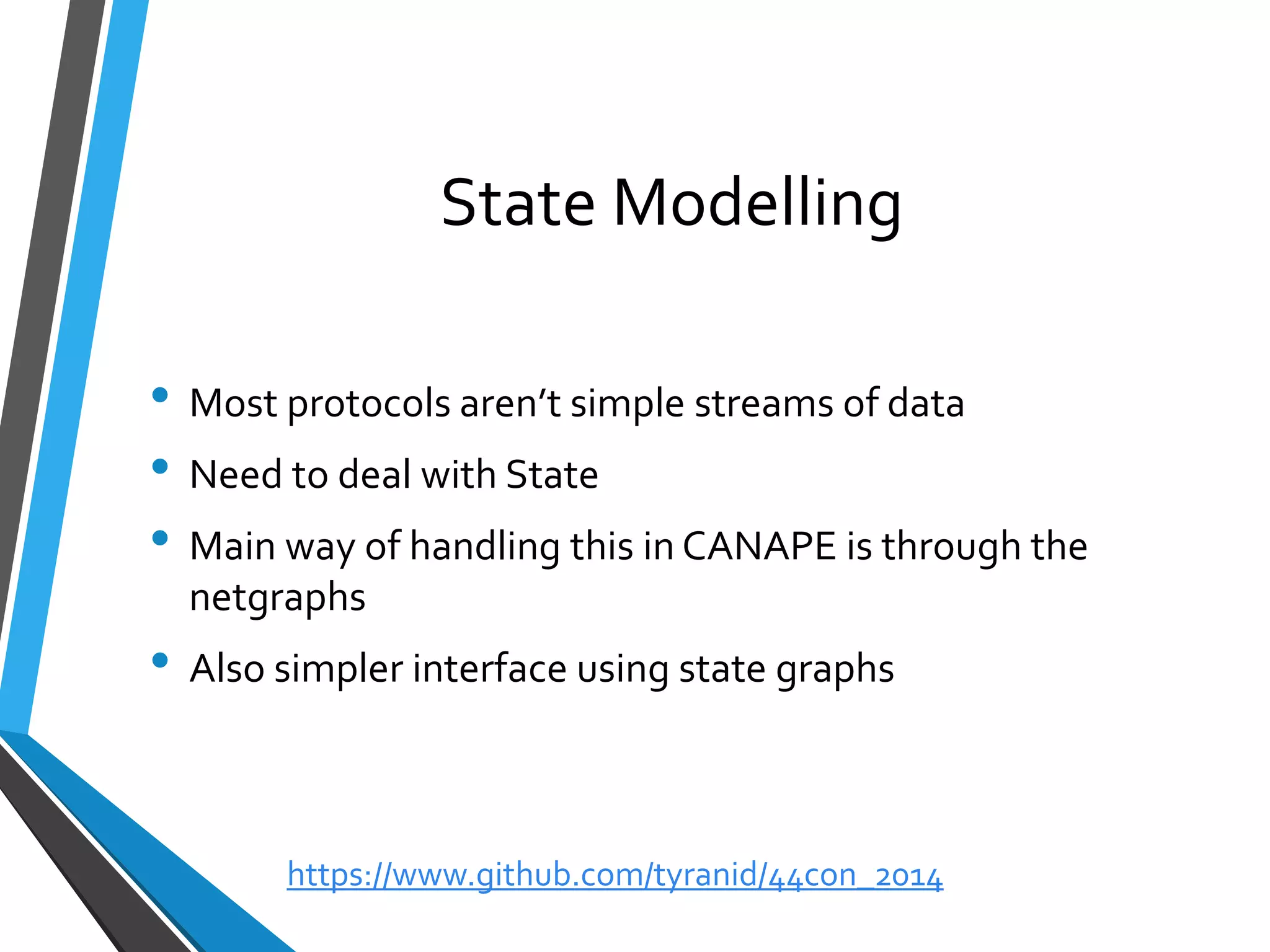
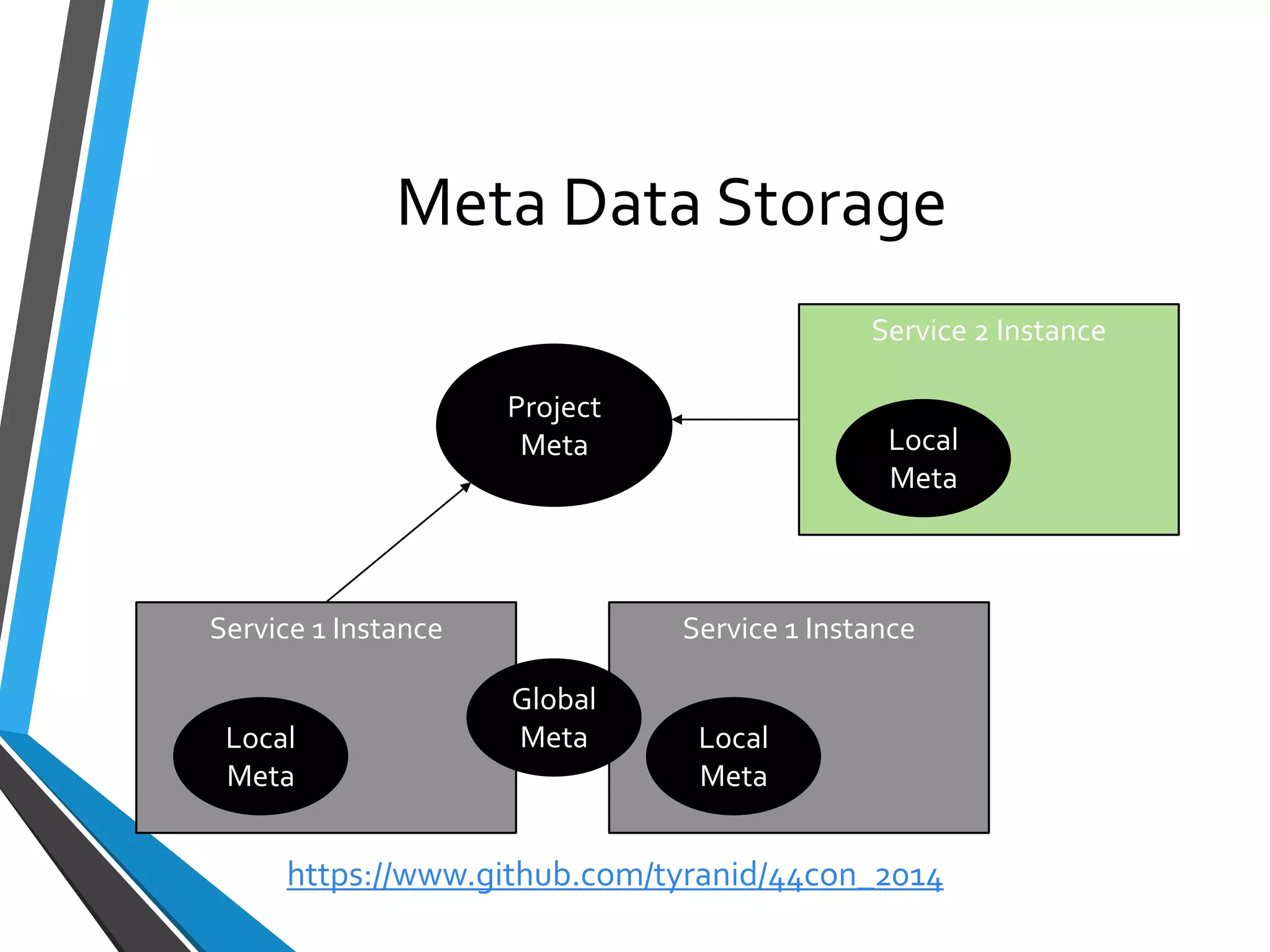
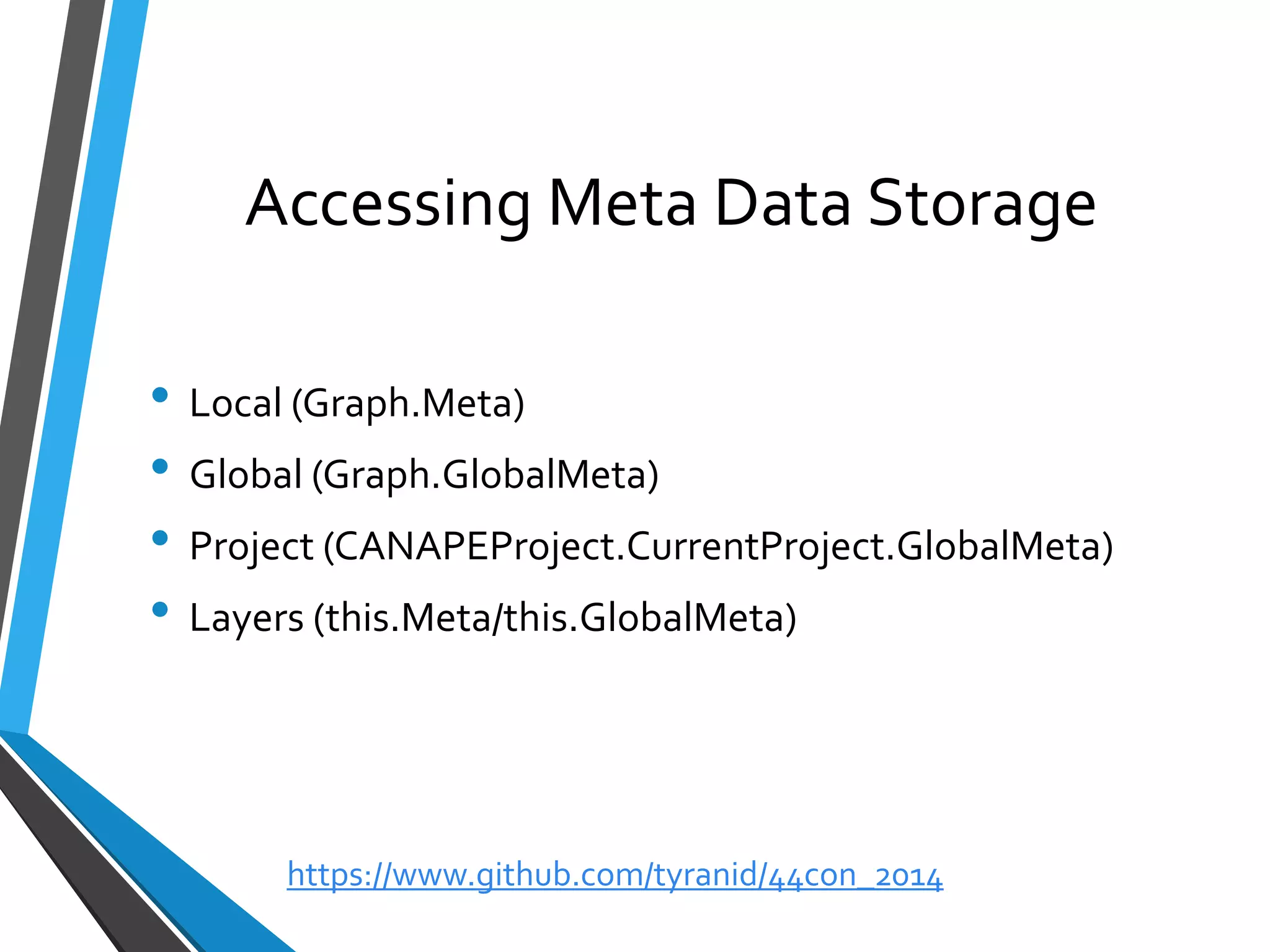
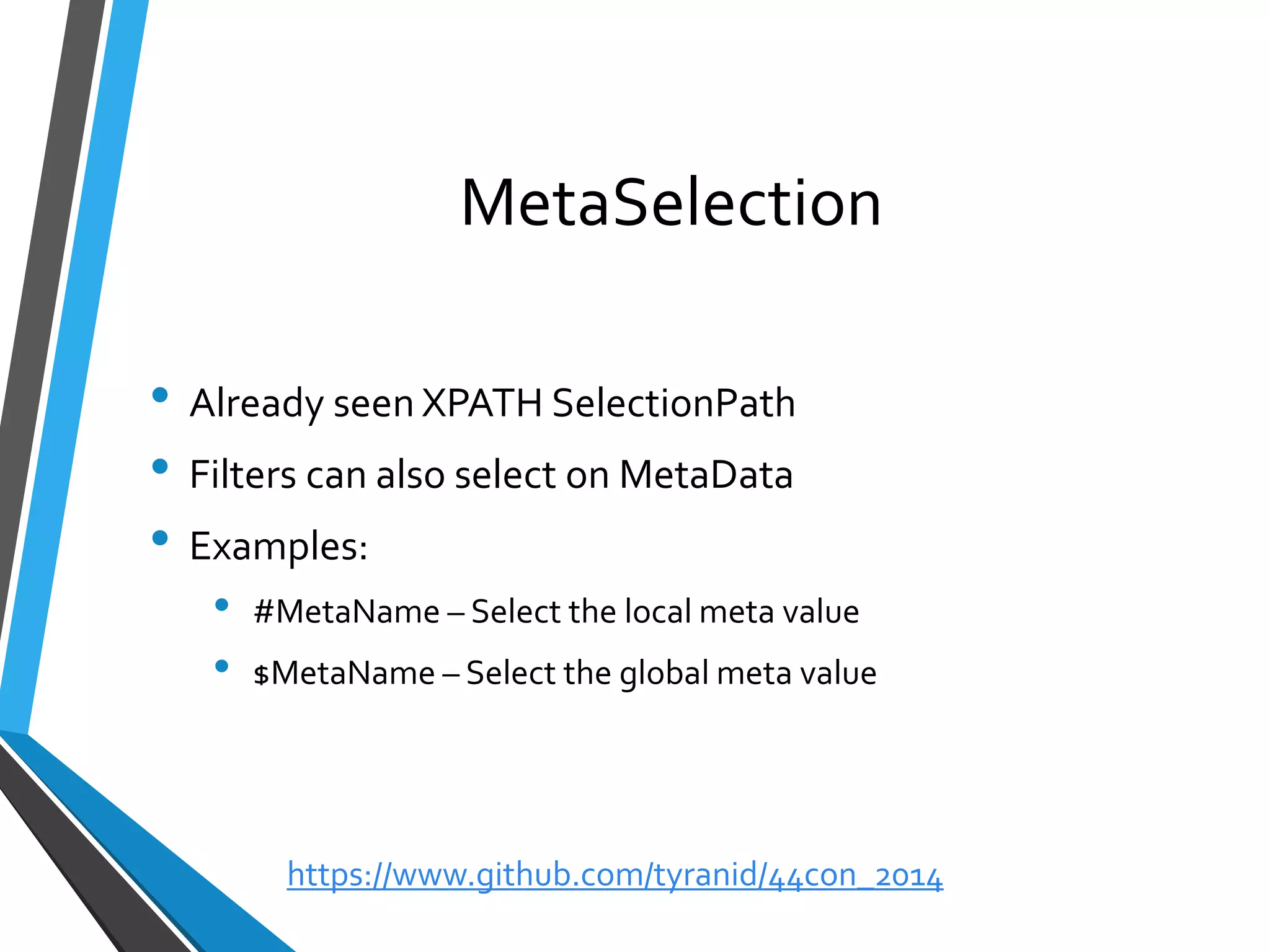
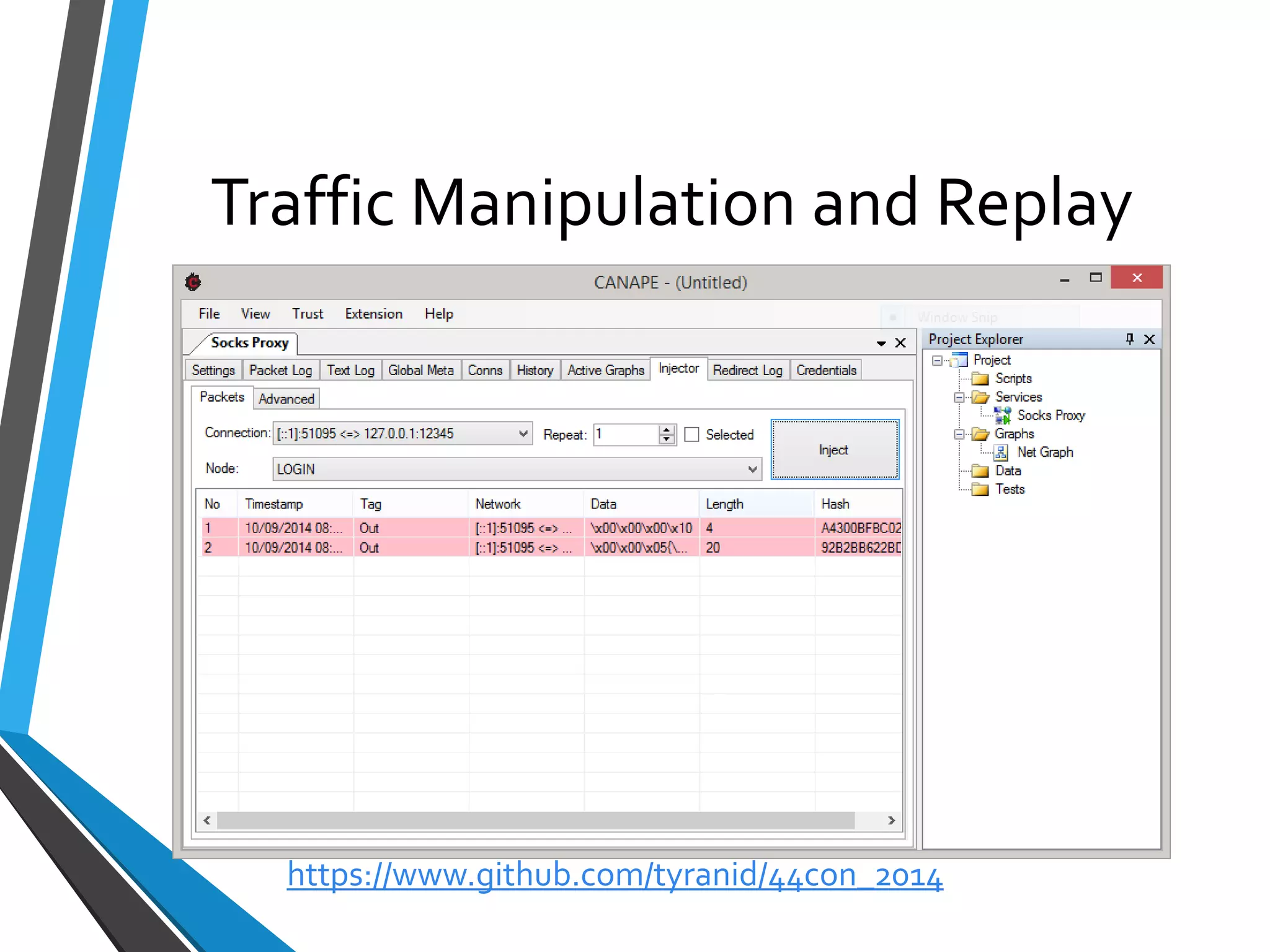
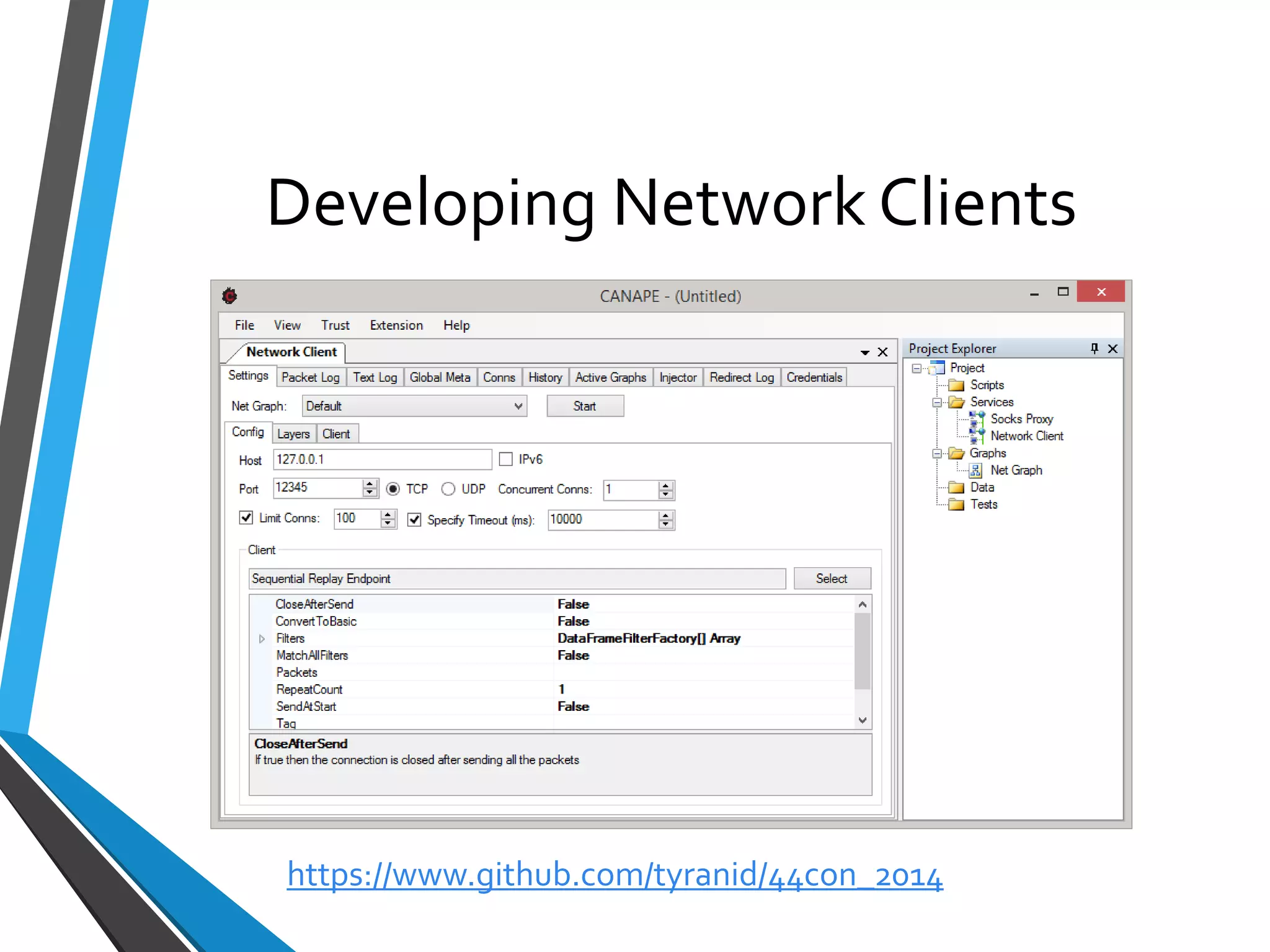
The document is a comprehensive guide on using Canape, an open-source tool for analyzing and manipulating binary network protocols. It covers various aspects including traffic proxying, data capturing, protocol modeling, and developing network clients. The guide also includes workshops to demonstrate practical applications of Canape in capturing, logging, and manipulating traffic.