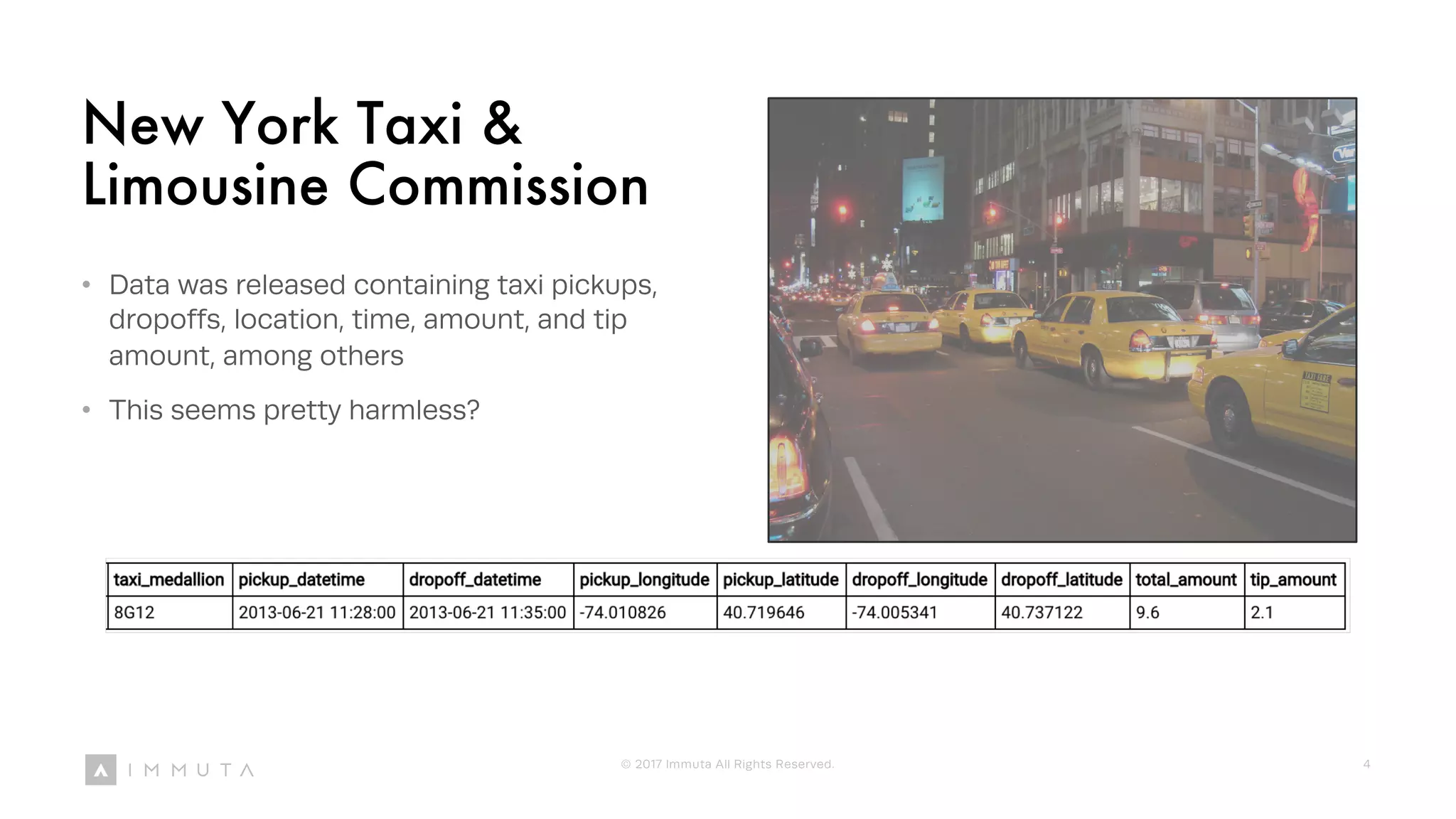
The document discusses the challenges of maintaining privacy in the context of machine learning, emphasizing that data can be either useful or anonymous, but never both. It highlights the risks of 'link attacks' where seemingly innocuous data can be used to identify individuals, and outlines regulatory responses like the GDPR and the California Consumer Privacy Act. The author argues for adopting data agility and privacy-preserving techniques to address privacy concerns in data usage, particularly as machine learning evolves.
















![The End of Privacy
[as we know it]?
• Rise of technology and data science
has killed privacy as we know it
• Instead of focusing on how and
when our data is gathered...
• Privacy should now be
how our data is being used.
© 2017 Immuta All Rights Reserved. 25](https://image.slidesharecdn.com/canprivacyexistwithmachinelearning-181023191114/75/Can-Privacy-Exist-With-Machine-Learning-25-2048.jpg)


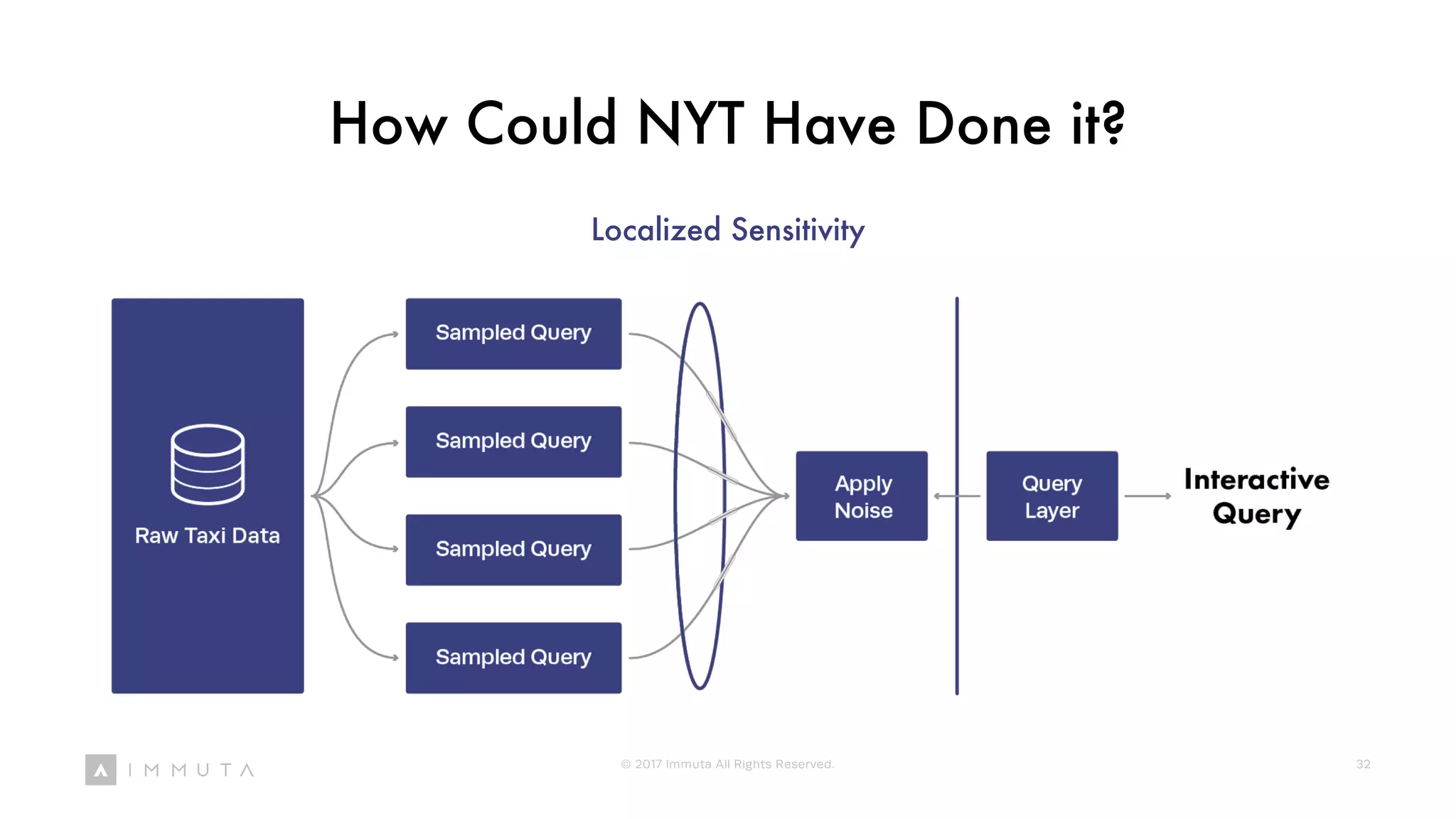
![This is Differential Privacy
• I protected your privacy by providing plausible deniability
• But I can also understand the percentage of people that hide spending from their
spouse because I understand the probability of you selecting a 3
• Differential Privacy is restricted to only statistical queries and adds the appropriate
amount of noise based on the sensitivity of the question
• ‘Differential privacy formalizes the idea that a "private" computation should not reveal
whether any one person participated in the input or not, much less what their data are.’
- [Frank McSherry] (https://github.com/frankmcsherry/blog/blob/master/posts/2016-02-03.md)
© 2017 Immuta All Rights Reserved. 31](https://image.slidesharecdn.com/canprivacyexistwithmachinelearning-181023191114/75/Can-Privacy-Exist-With-Machine-Learning-31-2048.jpg)