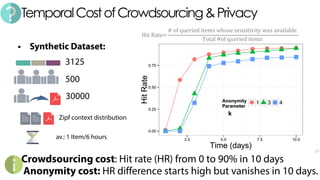
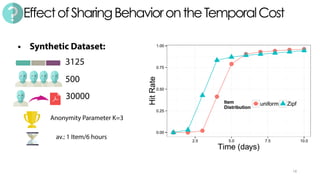
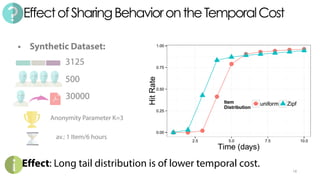
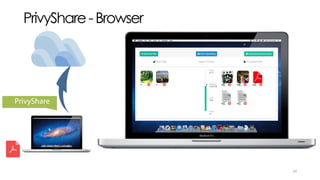
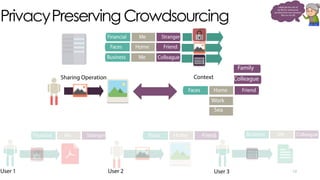
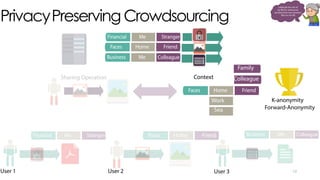
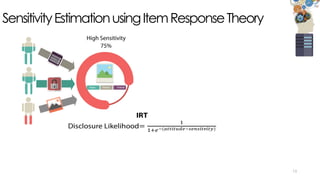
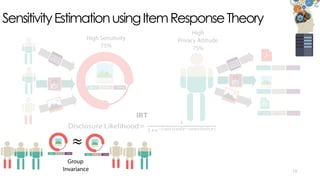
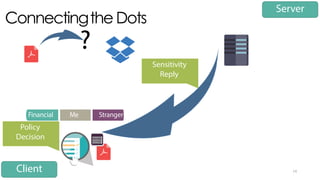
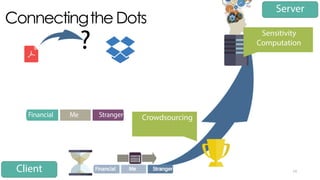
The document discusses C3P, a context-aware crowdsourced privacy solution for enhancing cloud data protection. It highlights the 60% increase in corporate data shared to the cloud in 2015, with 20% of those files containing protected information, and emphasizes the need for fine-grained data sensitivity assessment rather than brute encryption. It proposes a private crowdsourcing mechanism for estimating data sensitivity based on context and user input to improve privacy management.










































![IRTModelsFitPrivacy-AwareCloudSharing?
• Ex: With which privacy level would you
share a project presentation with a friend?
• Standardized Infit Statistic:
• (x-axis values should lie in [-2,2])
16
81
96
Dichotomous case
Sensitivity
Infit t-statistic
A dot
represents a
context](https://image.slidesharecdn.com/onlineversion-160710210747/85/C3P-Context-Aware-Crowdsourced-Cloud-Privacy-at-PETS-2014-52-320.jpg)
![IRTModelsFitPrivacy-AwareCloudSharing?
• Ex: With which privacy level would you
share a project presentation with a friend?
• Standardized Infit Statistic:
• (x-axis values should lie in [-2,2])
16
81
96
Dichotomous case
Sensitivity
Infit t-statistic
A dot
represents a
context](https://image.slidesharecdn.com/onlineversion-160710210747/85/C3P-Context-Aware-Crowdsourced-Cloud-Privacy-at-PETS-2014-53-320.jpg)
![IRTModelsFitPrivacy-AwareCloudSharing?
• Ex: With which privacy level would you
share a project presentation with a friend?
• Standardized Infit Statistic:
• (x-axis values should lie in [-2,2])
16
81
96
Polytomous case
Infit t-statistic
Sensitivity
Dichotomous case
Sensitivity
Infit t-statistic
A dot
represents a
context](https://image.slidesharecdn.com/onlineversion-160710210747/85/C3P-Context-Aware-Crowdsourced-Cloud-Privacy-at-PETS-2014-54-320.jpg)
![IRTModelsFitPrivacy-AwareCloudSharing?
• Ex: With which privacy level would you
share a project presentation with a friend?
• Standardized Infit Statistic:
• (x-axis values should lie in [-2,2])
16
81
96
Polytomous case
Infit t-statistic
Sensitivity
Dichotomous case
Sensitivity
Infit t-statistic
A dot
represents a
context](https://image.slidesharecdn.com/onlineversion-160710210747/85/C3P-Context-Aware-Crowdsourced-Cloud-Privacy-at-PETS-2014-55-320.jpg)
![IRTModelsFitPrivacy-AwareCloudSharing?
• Ex: With which privacy level would you
share a project presentation with a friend?
• Standardized Infit Statistic:
• (x-axis values should lie in [-2,2])
16
81
96
Yes!
Polytomous case
Infit t-statistic
Sensitivity
Dichotomous case
Sensitivity
Infit t-statistic
A dot
represents a
context](https://image.slidesharecdn.com/onlineversion-160710210747/85/C3P-Context-Aware-Crowdsourced-Cloud-Privacy-at-PETS-2014-56-320.jpg)