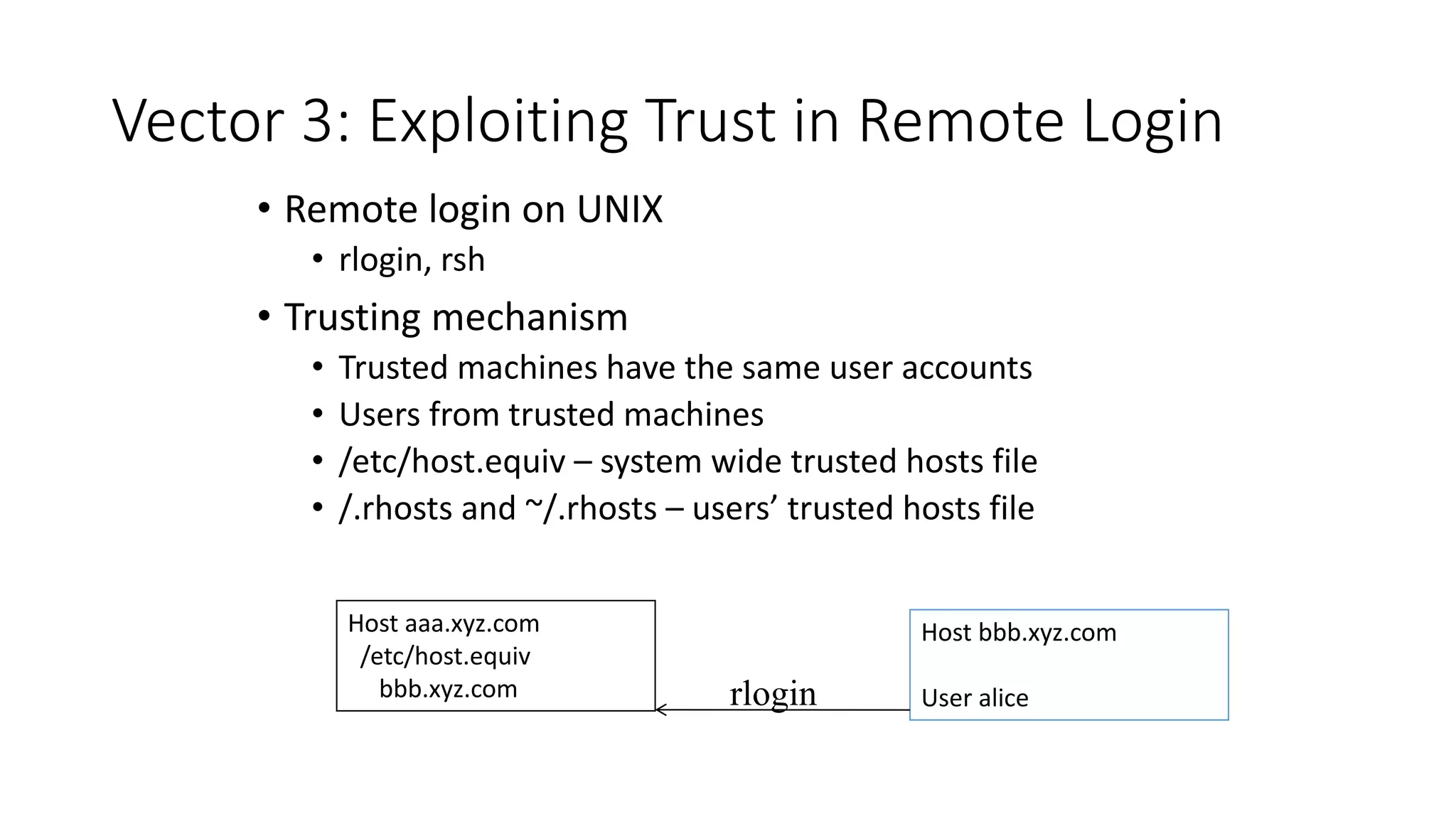
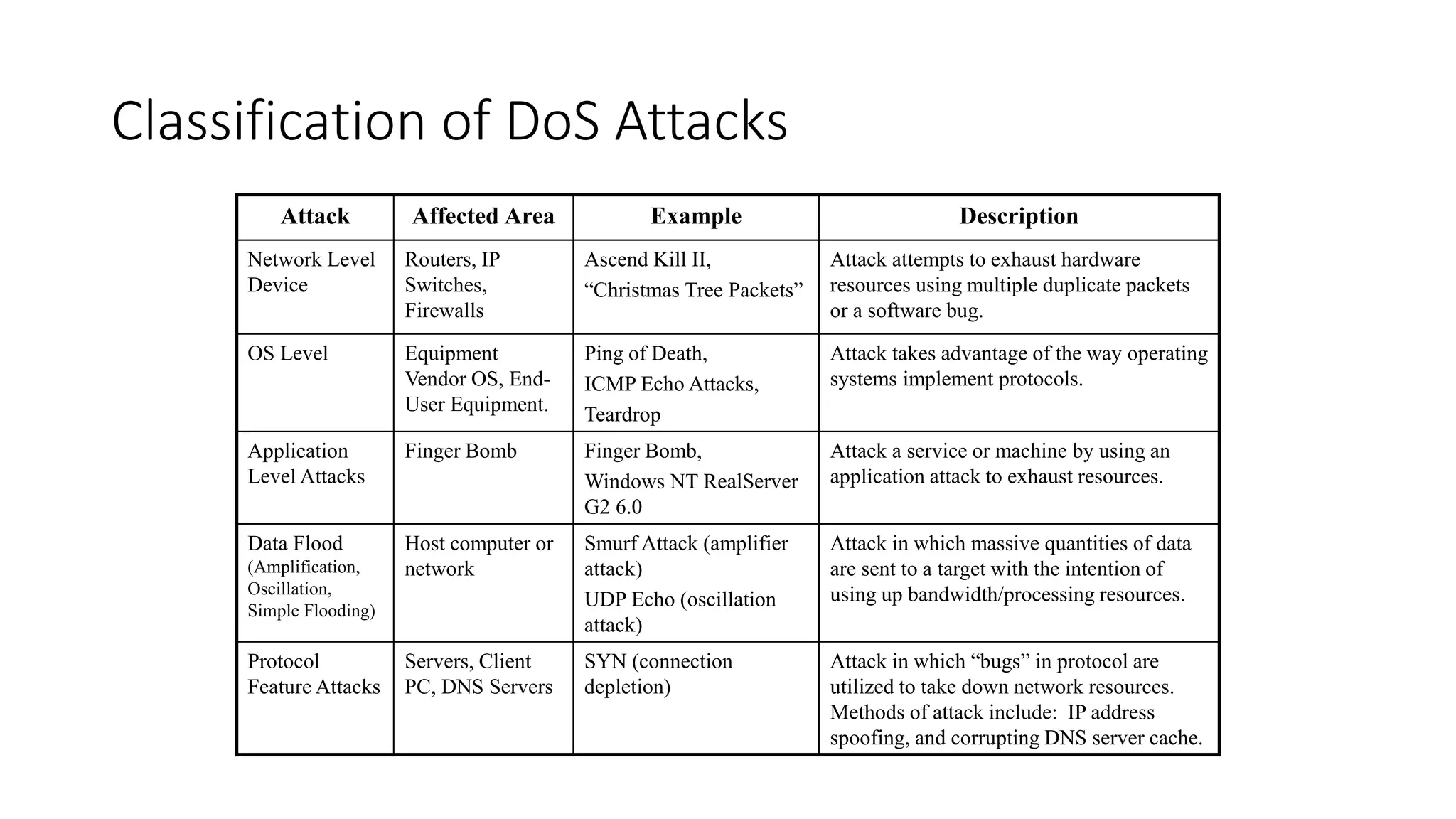
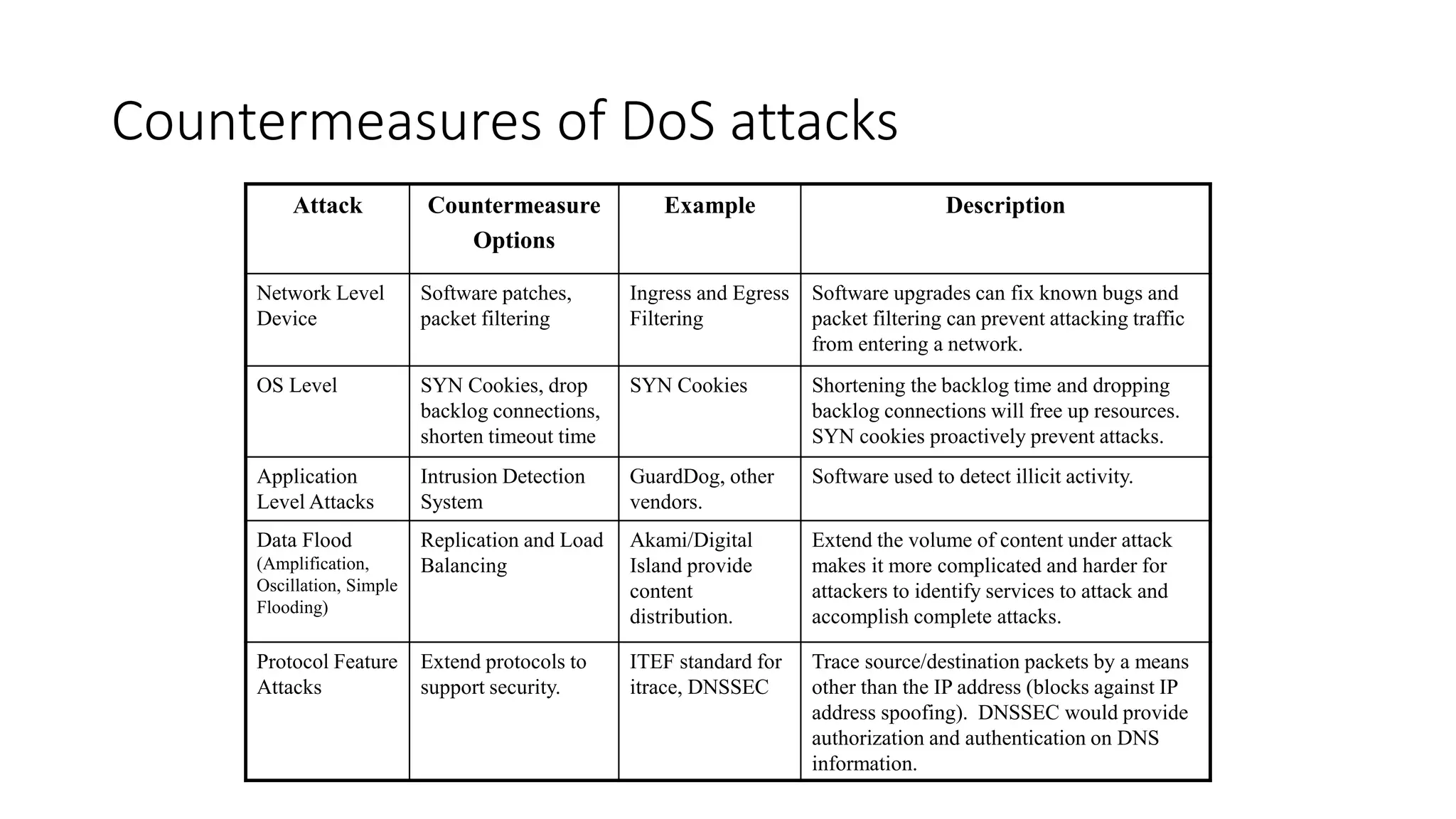
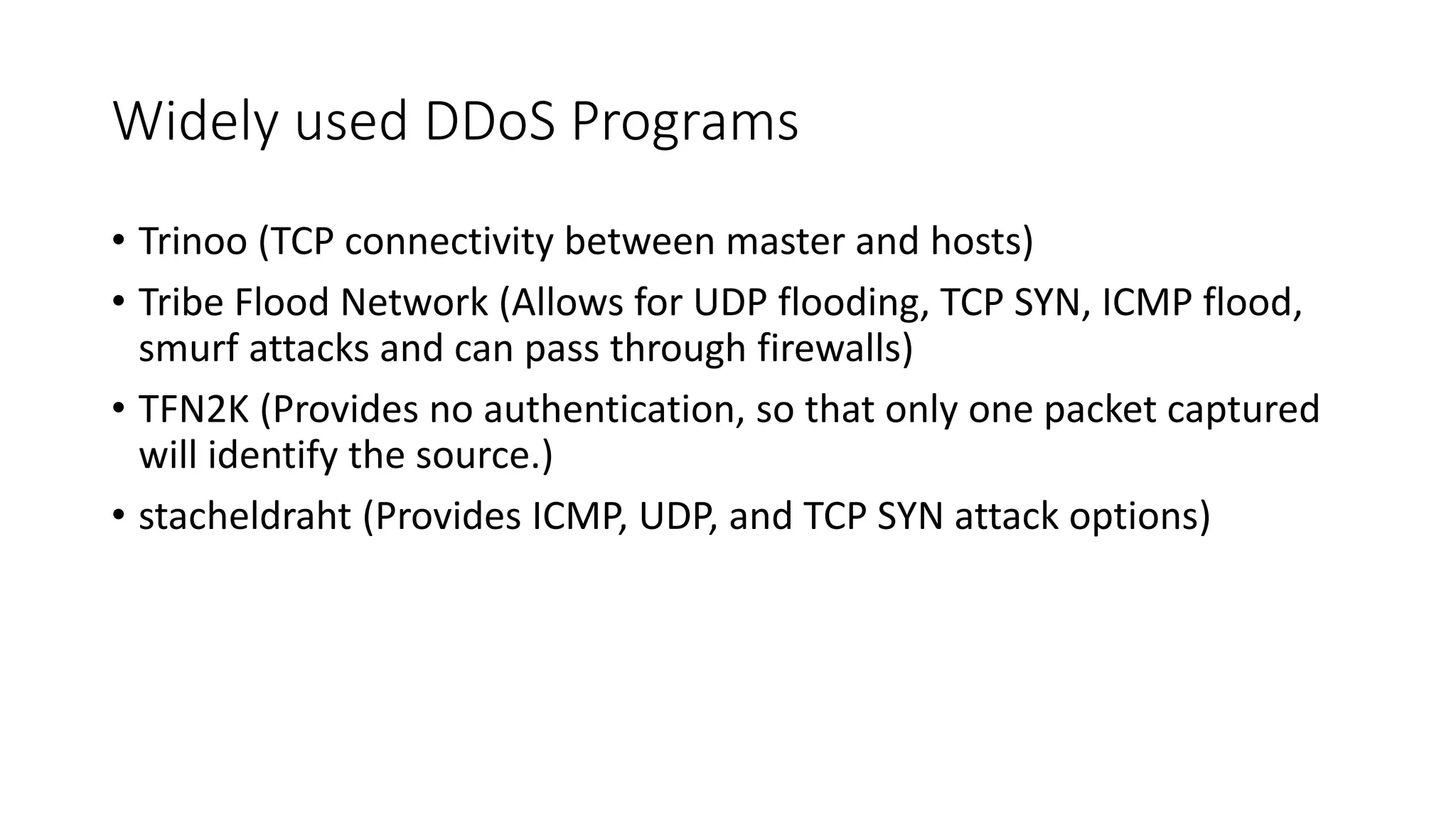
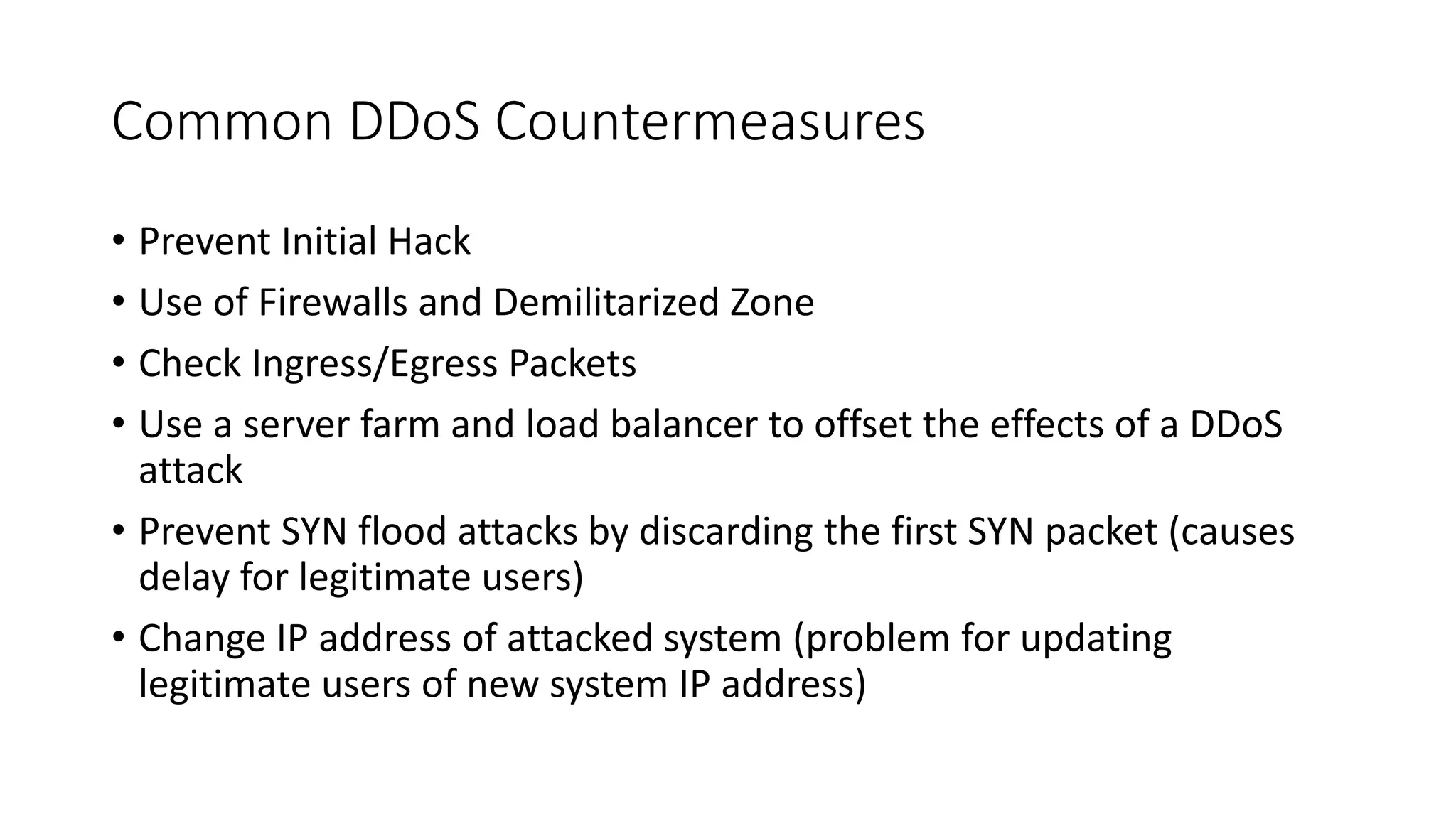
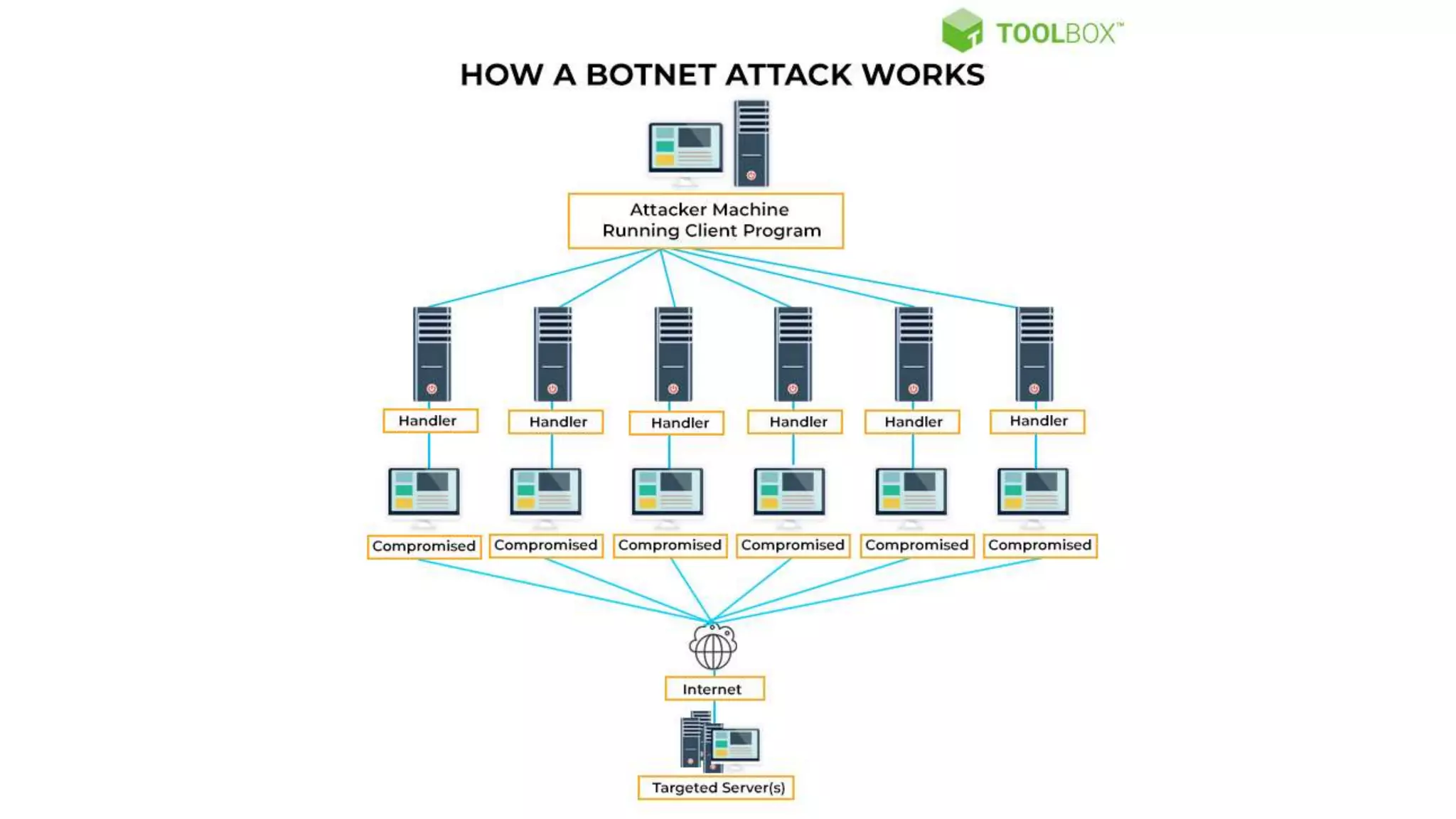
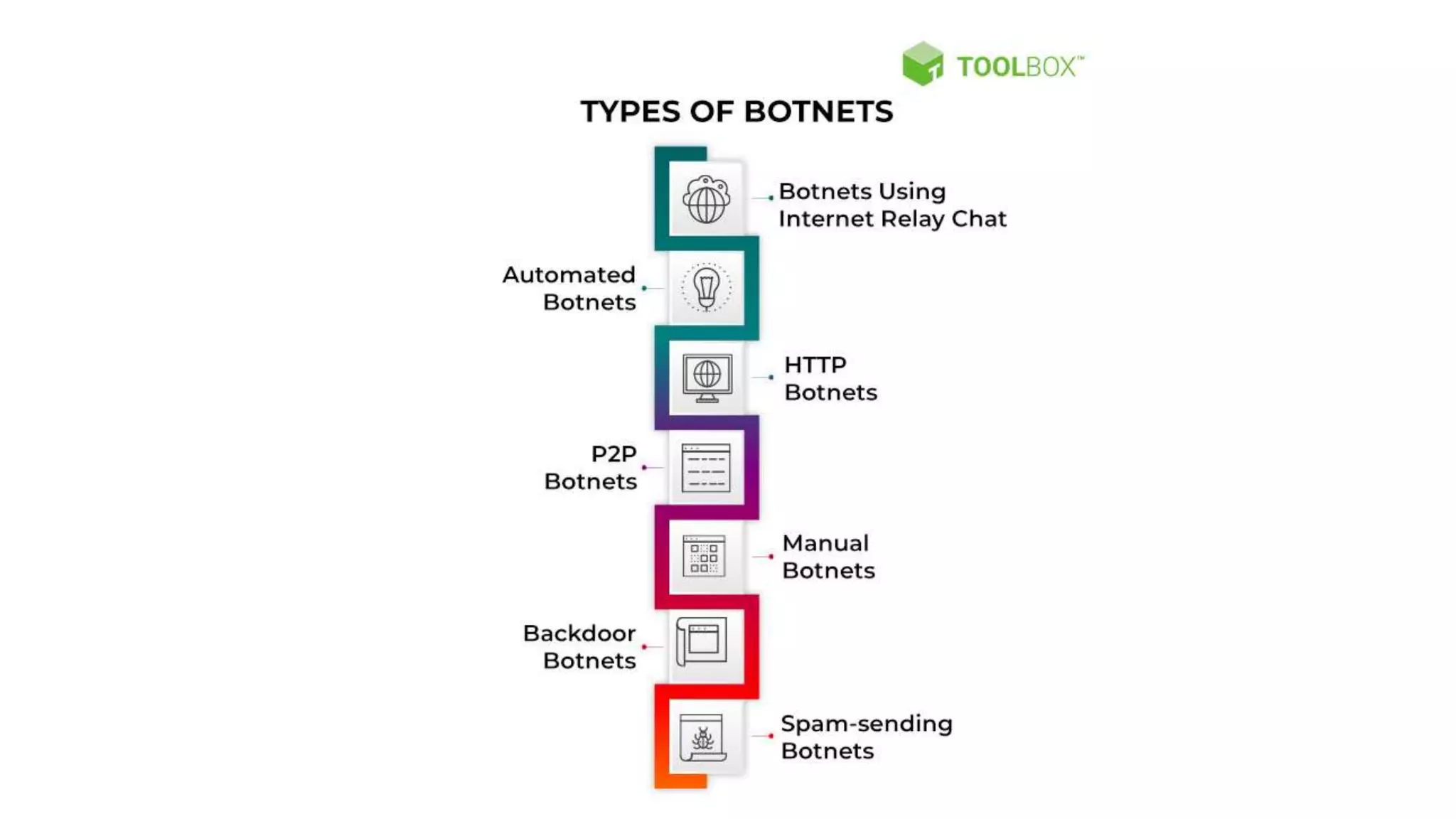
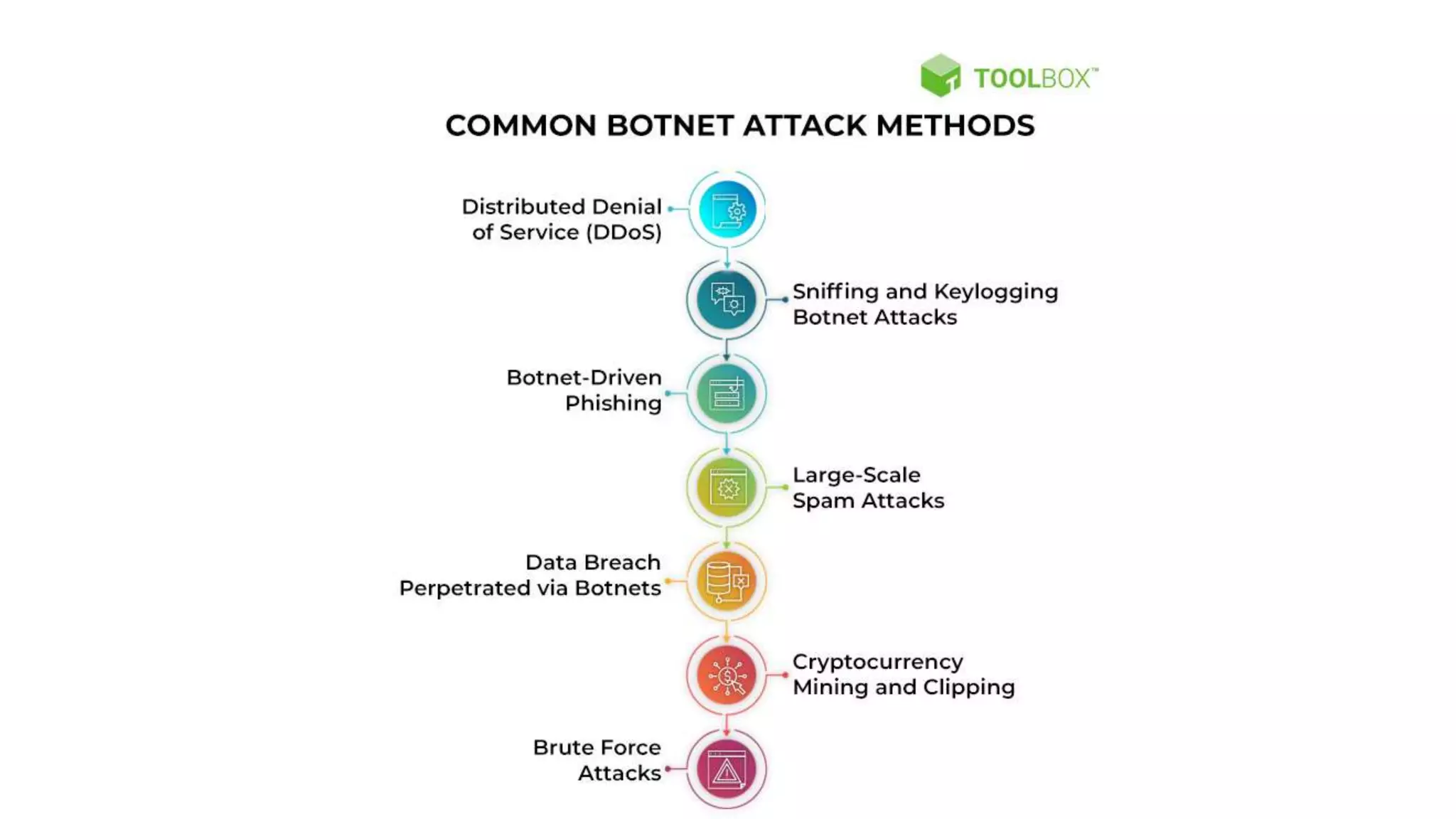
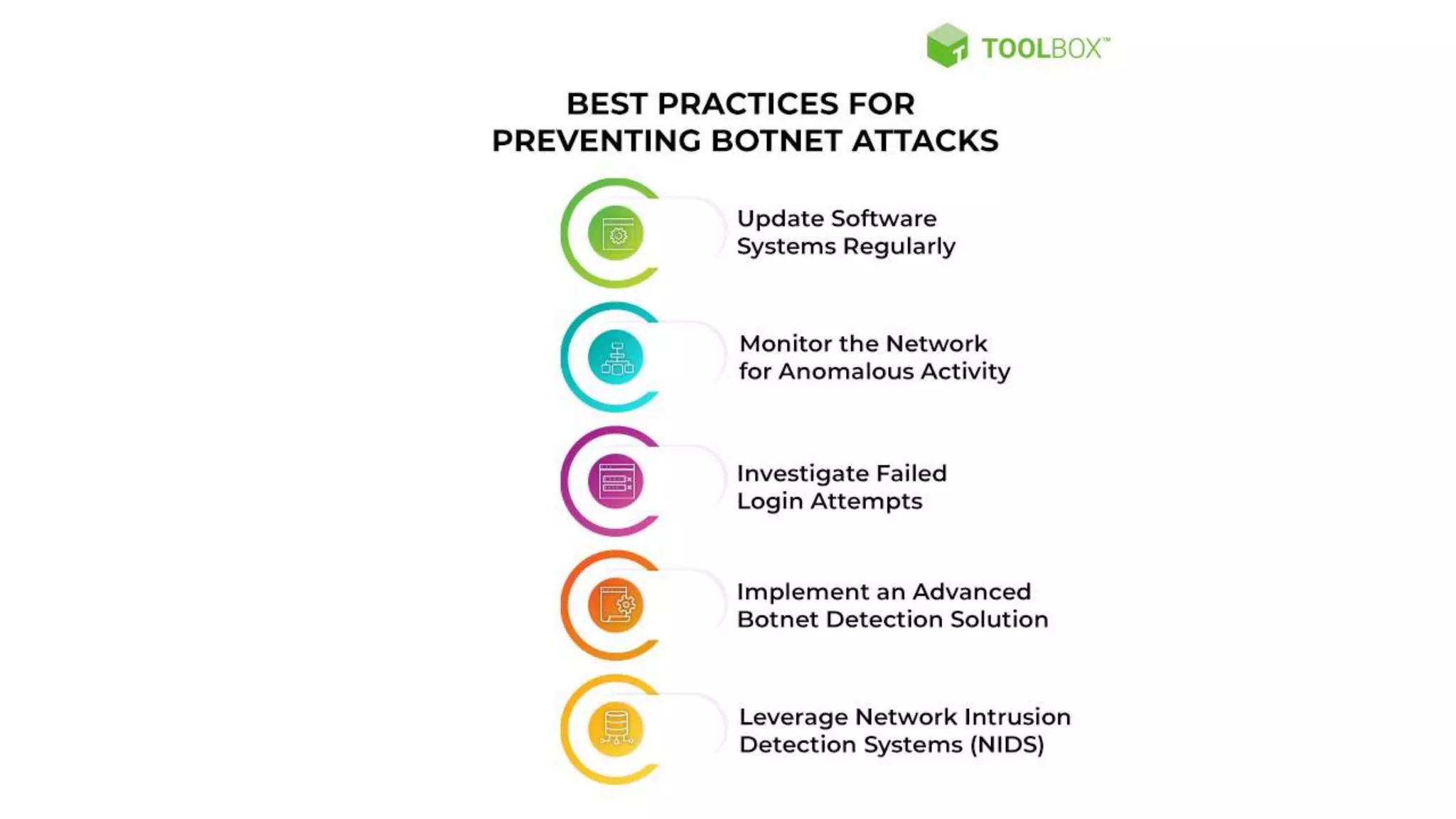
The document discusses various types of malware attacks including DDoS attacks, botnets, and mitigations. It provides definitions and examples of different malware types such as viruses, worms, Trojan horses, rootkits, logic bombs, and ransomware. It also discusses how botnets are used to launch DDoS attacks and describes common DDoS attack countermeasures such as preventing initial hacks, using firewalls, and changing targeted IP addresses.