Embed presentation
Download to read offline
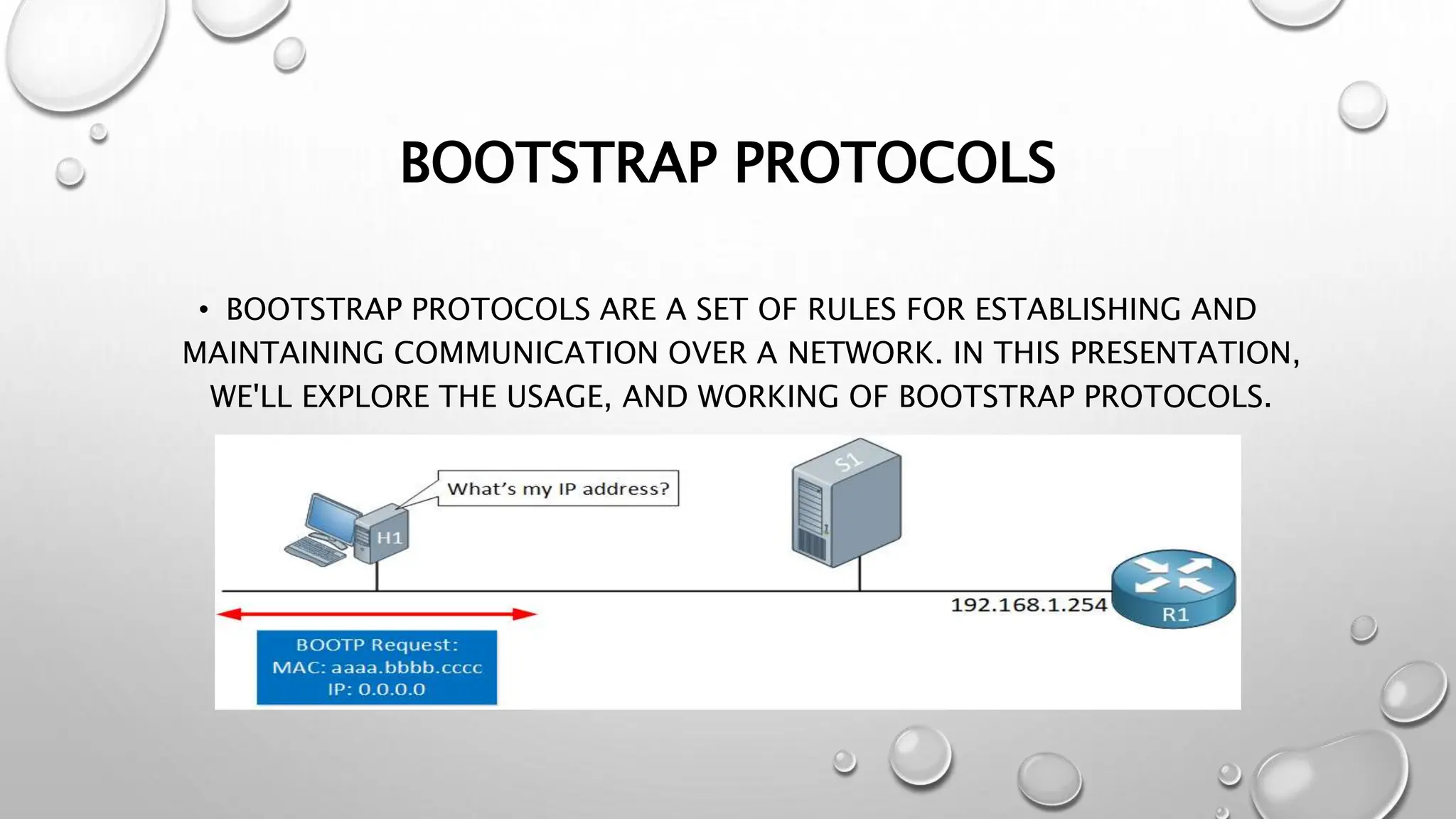


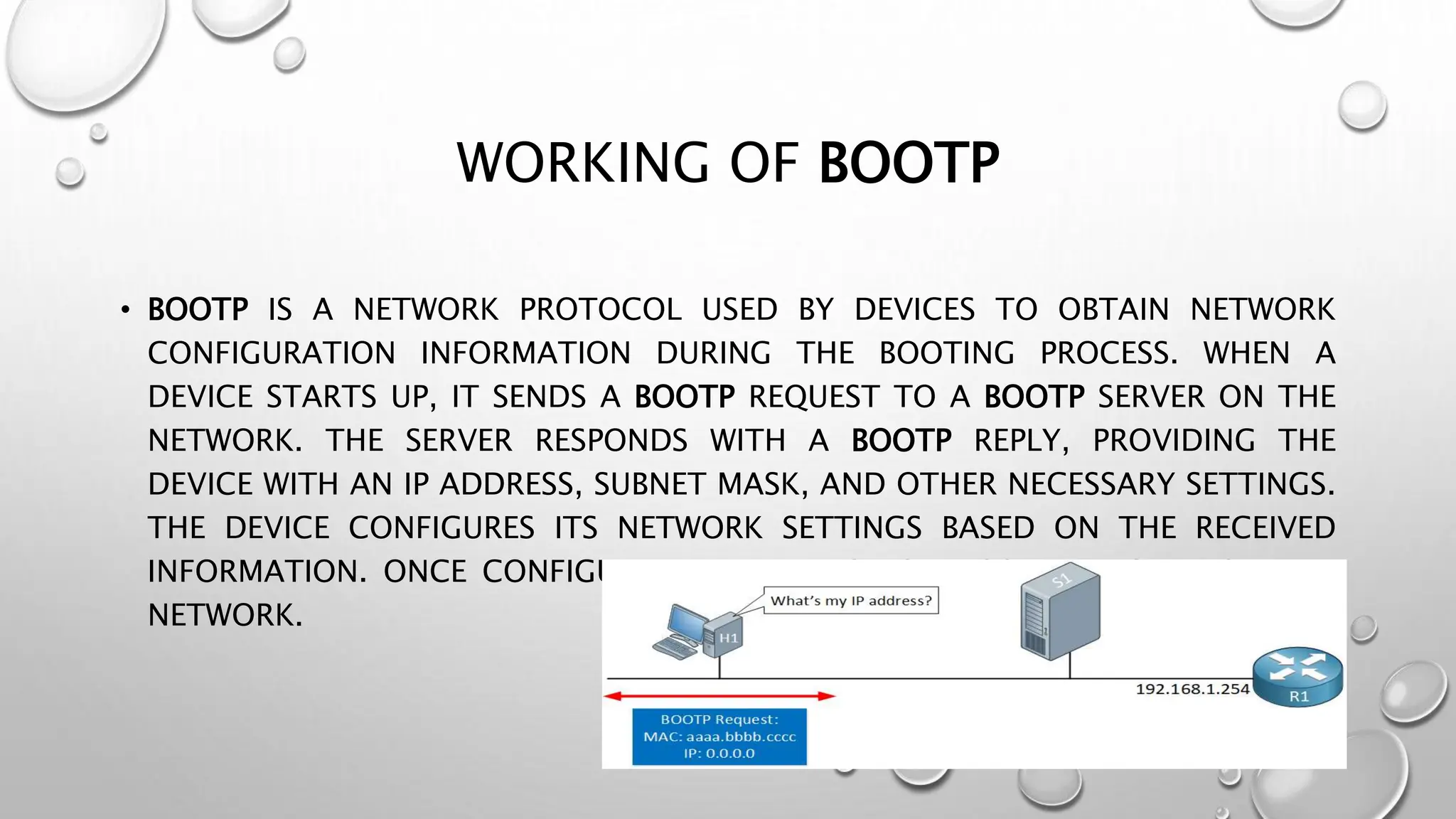
Bootstrap protocols are rules for network communication that allow devices to dynamically obtain IP addresses and configuration details. The Bootstrap Protocol (BOOTP) specifically facilitates this process during device startup by enabling network settings to be retrieved from a server. Additionally, these protocols can enforce security policies like MAC address filtering.



