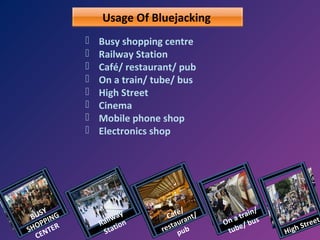
This document discusses bluejacking, which is sending unsolicited messages to Bluetooth-enabled devices. It provides an example of a man named Ajack who sent a message saying "Buy Ericsson!" to a Nokia phone he discovered with Bluetooth. It then explains how to enable Bluetooth and send messages to other devices. It discusses software tools for bluejacking and possible locations to find targets. It covers related concepts like bluesnarfing and ethics around bluejacking. Controls are suggested like turning Bluetooth off when not in use. While it could be used to advertise, it is also an offense under law.
![Presented By
A. Mercy
S. Asvitha
(II B.Sc.[CS])](https://image.slidesharecdn.com/bluejacking-mercy-140304000332-phpapp02/75/Blue-jacking-mercy-1-2048.jpg)