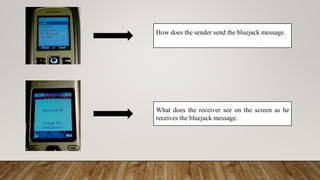
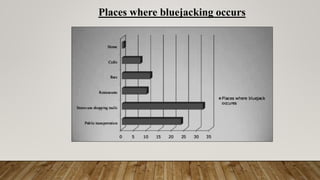
Bluejacking involves sending unsolicited messages to Bluetooth-enabled devices like mobile phones using Bluetooth technology. It allows sending business cards or other information anonymously within Bluetooth's limited range. While sometimes used to share contact information, it can also be used to annoy users or enable further attacks by exploiting vulnerabilities. The document discusses the OBEX protocol used, different bluejacking tools and techniques, potential attacks like bluesnarfing, and security measures to prevent unauthorized access.