Embed presentation
Download to read offline
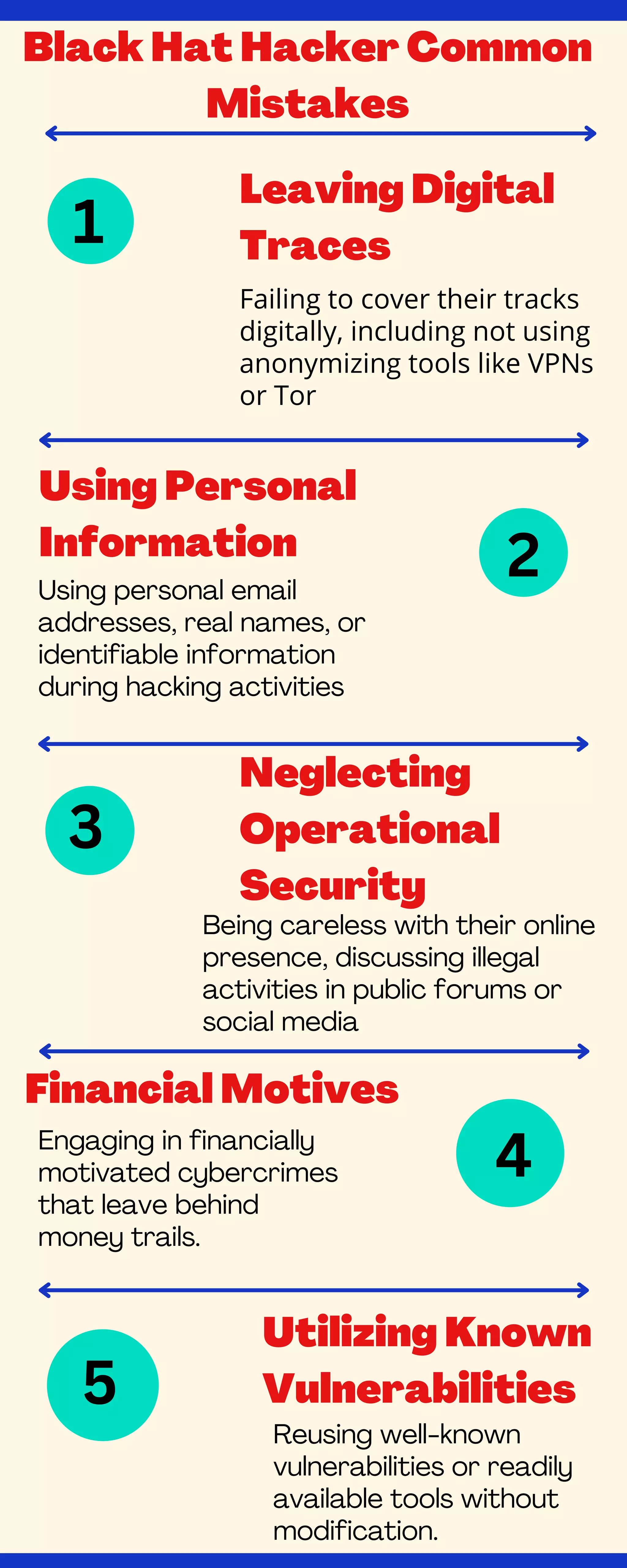
The document outlines common mistakes made by black hat hackers, emphasizing their failure to use anonymizing tools, leaving digital traces, and neglecting operational security. It highlights financial motives behind cybercrimes and the careless use of identifiable personal information during illegal activities. Additionally, it notes the dangers of reusing known vulnerabilities and available tools without modification.
