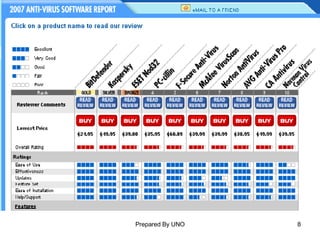
The document discusses network security and computer viruses. It defines network security and lists common types of computer viruses such as macro viruses, worms, and Trojan horses. It provides preventive actions against viruses like using antivirus software and security patches. Examples of antivirus software are also given along with their criteria. The document also defines disaster recovery plans and lists common network security threats such as malicious threats from spoofing, scanning and eavesdropping.