More Related Content
PDF
20200422 AWS Black Belt Online Seminar Amazon Elastic Container Service (Amaz... PDF
20190130 AWS Black Belt Online Seminar AWS Identity and Access Management (AW... PDF
AWS Black Belt Online Seminar 2016 AWS CloudFormation PDF
202106 AWS Black Belt Online Seminar 小売現場のデータを素早くビジネス に活用するAWSデータ基盤 PDF
20190326 AWS Black Belt Online Seminar Amazon CloudWatch PDF
20201118 AWS Black Belt Online Seminar 形で考えるサーバーレス設計 サーバーレスユースケースパターン解説 PDF
AWS Black Belt Online Seminar 2017 AWS Elastic Beanstalk PDF
20191002 AWS Black Belt Online Seminar Amazon EC2 Auto Scaling and AWS Auto S... What's hot
PDF
AWS Black Belt Online Seminar AWS Key Management Service (KMS) PDF
20190521 AWS Black Belt Online Seminar Amazon Simple Email Service (Amazon SES) PDF
20191029 AWS Black Belt Online Seminar Elastic Load Balancing (ELB) PDF
20190522 AWS Black Belt Online Seminar AWS Step Functions PDF
20210119 AWS Black Belt Online Seminar AWS CloudTrail PDF
20190514 AWS Black Belt Online Seminar Amazon API Gateway PDF
PDF
AWS Black Belt Online Seminar 2018 Amazon DynamoDB Advanced Design Pattern PDF
AWS Black Belt Online Seminar 2017 AWS Storage Gateway PDF
20200303 AWS Black Belt Online Seminar AWS Cloud Development Kit (CDK) PDF
20190226 AWS Black Belt Online Seminar Amazon WorkSpaces PDF
202205 AWS Black Belt Online Seminar Amazon VPC IP Address Manager (IPAM) PDF
20210526 AWS Expert Online マルチアカウント管理の基本 PDF
202110 AWS Black Belt Online Seminar AWS Site-to-Site VPN PDF
AWS Black Belt Online Seminar 2017 Amazon ElastiCache PDF
20190220 AWS Black Belt Online Seminar Amazon S3 / Glacier PDF
AWS Black Belt Online Seminar 2017 Amazon Kinesis PDF
20190814 AWS Black Belt Online Seminar AWS Serverless Application Model PDF
PDF
20191016 AWS Black Belt Online Seminar Amazon Route 53 Resolver Similar to AWS CLIでAssumeRole
PDF
Developers.IO 2018 ビジネスを阻害しない!AWS アカウントの管理 PDF
AWS Black Belt Techシリーズ AWS IAM PDF
AWS Black Belt Techシリーズ AWS IAM PPTX
PenTesterが知っている危ないAWS環境の共通点 PDF
AWS Black Belt Techシリーズ AWS Management Console PDF
20191125 Container Security PPTX
PDF
IAM & Consolidated Billing -ほぼ週刊AWSマイスターシリーズ第4回 PDF
20120201 aws meister-reloaded-iam-and-billing-public PDF
20200722 AWS Black Belt Online Seminar AWSアカウント シングルサインオンの設計と運用 PDF
20190129 AWS Black Belt Online Seminar AWS Identity and Access Management (AW... PDF
[AWSマイスターシリーズ]Identity and Access Management (IAM) PDF
AWS Well-Architected Tool 活用術セミナー セキュリティ編 PDF
JAWS-UG CLI #27 LT ActiveDirectoryのユーザとパスワードでManagement Consoleにログインする PDF
PDF
JAWS DAYS 2018 Community-based Security PDF
SecurityJAWS AWS Security Services Update 20200214 PDF
More from Tetsunori Nishizawa
PDF
はじめてのAWS設計でやりがちな失敗パターンまとめ PDF
Amazon WorkSpaces導入からはじめるスケーラブルなオフィス運営と、業務システムのクラウド移行 PDF
インフラエンジニアのためのAWSサービスを利用したログ分析はじめの一歩 PDF
クラウド移行を終えてからが本番〜AWSの使いこなし術〜 PDF
オープンなクラウドの世界でエンジニアが楽しいと思うことを仕事にする方法 PDF
Amazon s3へのデータ転送における課題とその対処法を一挙紹介 PDF
EC2+RDSを基本から #cmdevio2017 PDF
AWS CLIでAssumeRole
- 1.
- 2.
- 3.
- 4.
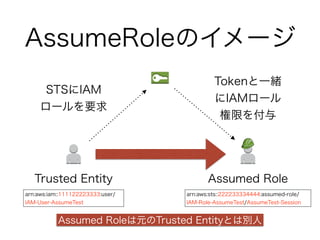
Temporary Security Credentialの種類
種別説明 権限
GetSessionToken 自身の権限で一時認証
自身の権限と同じ
クロスアカウント不可
MFA利用可
GetFederationToken 信頼ユーザで一時認証
自身の権限内で規定
クロスアカウント不可
MFA利用不可
AssumeRole IAMロールとマッピング
IAMロールで規定
クロスアカウント可
MFA利用可
(参考)http://docs.aws.amazon.com/ja_jp/STS/latest/UsingSTS/Welcome.html#AccessingSTS
- 5.
- 6.
- 7.
- 8.
- 9.
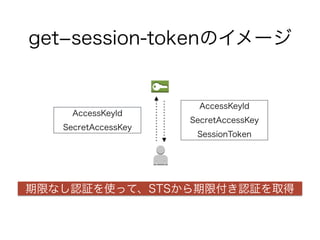
AWS CLIでGetSessionToken
(コマンド)
$ awssts get-session-token
(結果)
{
"Credentials": {
"SecretAccessKey": "yyyyyyyy",
"SessionToken": "zzzzzzzzzzzz",
"Expiration": "2015-05-25T19:00:00Z",
"AccessKeyId": "xxxx"
}
}
※KeyやTokenは実際にはもっと長い
- 10.
- 11.
- 12.
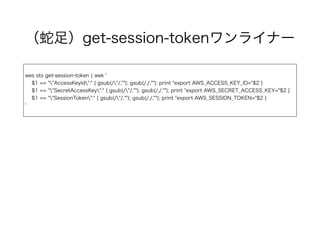
(蛇足)期限付き認証ワンライナー
aws sts get-session-token¦ awk '
$1 == ""AccessKeyId":" { gsub(/"/,""); gsub(/,/,""); print "export AWS_ACCESS_KEY_ID="$2 }
$1 == ""SecretAccessKey":" { gsub(/"/,""); gsub(/,/,""); print "export AWS_SECRET_ACCESS_KEY="$2 }
$1 == ""SessionToken":" { gsub(/"/,""); gsub(/,/,""); print "export AWS_SESSION_TOKEN="$2 }
'
- 13.
- 14.
- 15.
- 16.
- 17.
- 18.
- 19.
- 20.
- 21.
- 22.
- 23.
- 24.
- 25.
- 26.
- 27.
Principal設定例
"Principal": {"AWS": "111122223333"}
"Principal":{"AWS": "arn:aws:iam::111122223333:root"}
"Principal": {"AWS": "arn:aws:iam::111122223333:user/iam-user"}
"Principal": {"AWS": "arn:aws:iam::111122223333:role/iam-role"}
"Principal": {"Service": "ec2.amazonaws.com"}
"Principal": {"Federated": "www.amazon.com"}
(参考)http://docs.aws.amazon.com/ja_jp/IAM/latest/UserGuide/AccessPolicyLanguage_ElementDescriptions.html#Principal
- 28.
- 29.
- 30.
- 31.
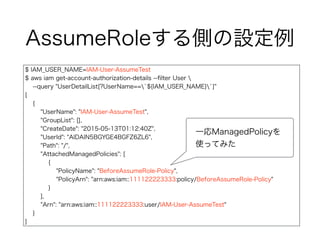
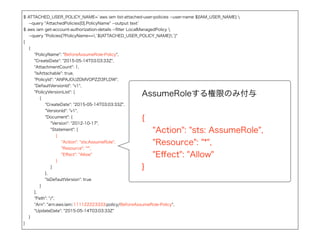
AssumeRoleする側の設定例
$ IAM_USER_NAME=IAM-User-AssumeTest
$ awsiam get-account-authorization-details --filter User
--query "UserDetailList[?UserName==`${IAM_USER_NAME}`]"
[
{
"UserName": "IAM-User-AssumeTest",
"GroupList": [],
"CreateDate": "2015-05-13T01:12:40Z",
"UserId": "AIDAIN5BGYGE4BGFZ6ZL6",
"Path": "/",
"AttachedManagedPolicies": [
{
"PolicyName": "BeforeAssumeRole-Policy",
"PolicyArn": "arn:aws:iam::111122223333:policy/BeforeAssumeRole-Policy"
}
],
"Arn": "arn:aws:iam::111122223333:user/IAM-User-AssumeTest"
}
]
一応ManagedPolicyを
使ってみた
- 32.
$ ATTACHED_USER_POLICY_NAME=`aws iamlist-attached-user-policies --user-name ${IAM_USER_NAME}
--query "AttachedPolicies[0].PolicyName" --output text`
$ aws iam get-account-authorization-details --filter LocalManagedPolicy
--query "Policies[?PolicyName==`${ATTACHED_USER_POLICY_NAME}`]"
[
{
"PolicyName": "BeforeAssumeRole-Policy",
"CreateDate": "2015-05-14T03:03:33Z",
"AttachmentCount": 1,
"IsAttachable": true,
"PolicyId": "ANPAJOUZGMVOPZZI3FLDW",
"DefaultVersionId": "v1",
"PolicyVersionList": [
{
"CreateDate": "2015-05-14T03:03:33Z",
"VersionId": "v1",
"Document": {
"Version": "2012-10-17",
"Statement": [
{
"Action": "sts:AssumeRole",
"Resource": "arn:aws:iam::222233334444:role/IAM-Role-AssumeTest",
"Effect": "Allow"
}
]
},
"IsDefaultVersion": true
}
],
"Path": "/",
"Arn": "arn:aws:iam::111122223333:policy/BeforeAssumeRole-Policy",
"UpdateDate": "2015-05-14T03:03:33Z"
}
]
AssumeRoleする権限のみ付与
{
"Action": "sts: AssumeRole",
"Resource": "arn:aws:iam::222233334444:role/
IAM-Role-AssumeTest",
"Effect": "Allow"
}
- 33.
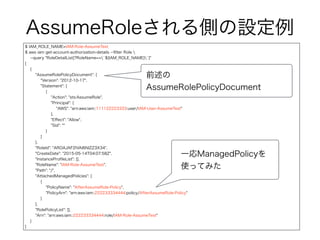
AssumeRoleされる側の設定例
$ IAM_ROLE_NAME=IAM-Role-AssumeTest
$ awsiam get-account-authorization-details --filter Role
--query "RoleDetailList[?RoleName==`${IAM_ROLE_NAME}`]"
[
{
"AssumeRolePolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Action": "sts:AssumeRole",
"Principal": {
"AWS": "arn:aws:iam::111122223333:user/IAM-User-AssumeTest"
},
"Effect": "Allow",
"Sid": ""
}
]
},
"RoleId": "AROAJAF2IVAI6NIZZ3X34",
"CreateDate": "2015-05-14T04:07:58Z",
"InstanceProfileList": [],
"RoleName": "IAM-Role-AssumeTest",
"Path": "/",
"AttachedManagedPolicies": [
{
"PolicyName": "AfterAssumeRole-Policy",
"PolicyArn": "arn:aws:iam::222233334444:policy/AfterAssumeRole-Policy"
}
],
"RolePolicyList": [],
"Arn": "arn:aws:iam::222233334444:role/IAM-Role-AssumeTest"
}
]
前述の
AssumeRolePolicyDocument
一応ManagedPolicyを
使ってみた
- 34.
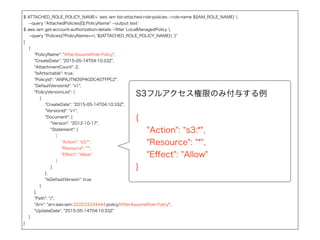
$ ATTACHED_ROLE_POLICY_NAME=`aws iamlist-attached-role-policies --role-name ${IAM_ROLE_NAME}
--query "AttachedPolicies[0].PolicyName" --output text`
$ aws iam get-account-authorization-details --filter LocalManagedPolicy
--query "Policies[?PolicyName==`${ATTACHED_ROLE_POLICY_NAME}`]"
[
{
"PolicyName": "AfterAssumeRole-Policy",
"CreateDate": "2015-05-14T04:10:33Z",
"AttachmentCount": 2,
"IsAttachable": true,
"PolicyId": "ANPAJTNO5P4GDC4GTFPC2",
"DefaultVersionId": "v1",
"PolicyVersionList": [
{
"CreateDate": "2015-05-14T04:10:33Z",
"VersionId": "v1",
"Document": {
"Version": "2012-10-17",
"Statement": [
{
"Action": "s3:*",
"Resource": "*",
"Effect": "Allow"
}
]
},
"IsDefaultVersion": true
}
],
"Path": "/",
"Arn": "arn:aws:iam::222233334444:policy/AfterAssumeRole-Policy",
"UpdateDate": "2015-05-14T04:10:33Z"
}
]
S3フルアクセス権限のみ付与する例
{
"Action": "s3:*",
"Resource": "*",
"Effect": "Allow"
}
- 35.
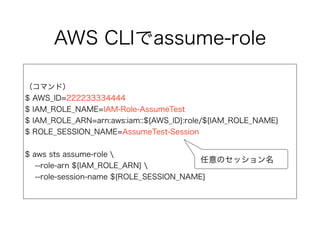
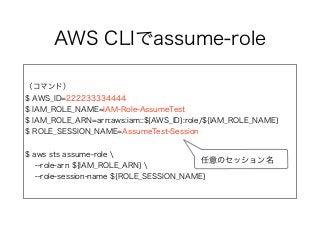
AWS CLIでassume-role
(コマンド)
$ AWS_ID=222233334444
$IAM_ROLE_NAME=IAM-Role-AssumeTest
$ IAM_ROLE_ARN=arn:aws:iam::${AWS_ID}:role/${IAM_ROLE_NAME}
$ ROLE_SESSION_NAME=AssumeTest-Session
$ aws sts assume-role
--role-arn ${IAM_ROLE_ARN}
--role-session-name ${ROLE_SESSION_NAME}
任意のセッション名
- 36.
- 37.
- 38.
- 39.
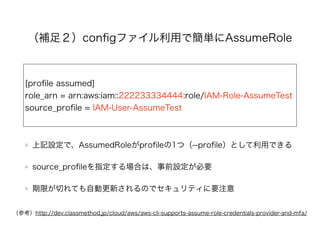
(補足2)configファイル利用で
簡単にAssumeRole
[profile assumed]
role_arn =arn:aws:iam::222233334444:role/IAM-Role-AssumeTest
source_profile = IAM-User-AssumeTest
上記設定で、Assumed Roleがprofileの1つ(--profile)として利用できる
source_profileを指定する場合は、事前設定が必要
期限が切れても自動更新されるのでセキュリティに要注意
(参考)http://dev.classmethod.jp/cloud/aws/aws-cli-supports-assume-role-credentials-provider-and-mfa/
- 40.
- 41.
- 42.
- 43.
- 44.







![期限付き認証の使い方
取得した期限付き認証を使いたい人に渡す
環境変数で指定
export AWS_ACCESS_KEY_ID=xxxx
export AWS_SECRET_ACCESS_KEY=yyyyyyyy
export AWS_SESSION_TOKEN=zzzzzzzzzzzz
configファイルで指定も可能
[profile temp-profile]
aws_access_key_id=xxxx
aws_secret_access_key=yyyyyyyy
aws_session_token=zzzzzzzzzzzz
※credentialに記載の場合は"profile"は不要
(参考)http://docs.aws.amazon.com/ja_jp/cli/latest/userguide/cli-chap-getting-started.html](https://image.slidesharecdn.com/awscliassumerole-150517151026-lva1-app6892/85/AWS-CLI-AssumeRole-11-320.jpg)












![AssumeRolePolicyDocumentの設定例
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::111122223333:user/IAM-User-AssumeTest"
},
"Action": "sts:AssumeRole"
}
]
}
ExternalId(ユニークなキー)やMFA必須も設定可能
"Condition": {
"StringEquals": {
"sts:ExternalId": "TestExternalId"
},
"Bool": {
"aws:MultiFactorAuthPresent": true
}
}](https://image.slidesharecdn.com/awscliassumerole-150517151026-lva1-app6892/85/AWS-CLI-AssumeRole-30-320.jpg)
![AssumeRoleする側の設定例
$ IAM_USER_NAME=IAM-User-AssumeTest
$ aws iam get-account-authorization-details --filter User
--query "UserDetailList[?UserName==`${IAM_USER_NAME}`]"
[
{
"UserName": "IAM-User-AssumeTest",
"GroupList": [],
"CreateDate": "2015-05-13T01:12:40Z",
"UserId": "AIDAIN5BGYGE4BGFZ6ZL6",
"Path": "/",
"AttachedManagedPolicies": [
{
"PolicyName": "BeforeAssumeRole-Policy",
"PolicyArn": "arn:aws:iam::111122223333:policy/BeforeAssumeRole-Policy"
}
],
"Arn": "arn:aws:iam::111122223333:user/IAM-User-AssumeTest"
}
]
一応ManagedPolicyを
使ってみた](https://image.slidesharecdn.com/awscliassumerole-150517151026-lva1-app6892/85/AWS-CLI-AssumeRole-31-320.jpg)
![$ ATTACHED_USER_POLICY_NAME=`aws iam list-attached-user-policies --user-name ${IAM_USER_NAME}
--query "AttachedPolicies[0].PolicyName" --output text`
$ aws iam get-account-authorization-details --filter LocalManagedPolicy
--query "Policies[?PolicyName==`${ATTACHED_USER_POLICY_NAME}`]"
[
{
"PolicyName": "BeforeAssumeRole-Policy",
"CreateDate": "2015-05-14T03:03:33Z",
"AttachmentCount": 1,
"IsAttachable": true,
"PolicyId": "ANPAJOUZGMVOPZZI3FLDW",
"DefaultVersionId": "v1",
"PolicyVersionList": [
{
"CreateDate": "2015-05-14T03:03:33Z",
"VersionId": "v1",
"Document": {
"Version": "2012-10-17",
"Statement": [
{
"Action": "sts:AssumeRole",
"Resource": "arn:aws:iam::222233334444:role/IAM-Role-AssumeTest",
"Effect": "Allow"
}
]
},
"IsDefaultVersion": true
}
],
"Path": "/",
"Arn": "arn:aws:iam::111122223333:policy/BeforeAssumeRole-Policy",
"UpdateDate": "2015-05-14T03:03:33Z"
}
]
AssumeRoleする権限のみ付与
{
"Action": "sts: AssumeRole",
"Resource": "arn:aws:iam::222233334444:role/
IAM-Role-AssumeTest",
"Effect": "Allow"
}](https://image.slidesharecdn.com/awscliassumerole-150517151026-lva1-app6892/85/AWS-CLI-AssumeRole-32-320.jpg)
![AssumeRoleされる側の設定例
$ IAM_ROLE_NAME=IAM-Role-AssumeTest
$ aws iam get-account-authorization-details --filter Role
--query "RoleDetailList[?RoleName==`${IAM_ROLE_NAME}`]"
[
{
"AssumeRolePolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Action": "sts:AssumeRole",
"Principal": {
"AWS": "arn:aws:iam::111122223333:user/IAM-User-AssumeTest"
},
"Effect": "Allow",
"Sid": ""
}
]
},
"RoleId": "AROAJAF2IVAI6NIZZ3X34",
"CreateDate": "2015-05-14T04:07:58Z",
"InstanceProfileList": [],
"RoleName": "IAM-Role-AssumeTest",
"Path": "/",
"AttachedManagedPolicies": [
{
"PolicyName": "AfterAssumeRole-Policy",
"PolicyArn": "arn:aws:iam::222233334444:policy/AfterAssumeRole-Policy"
}
],
"RolePolicyList": [],
"Arn": "arn:aws:iam::222233334444:role/IAM-Role-AssumeTest"
}
]
前述の
AssumeRolePolicyDocument
一応ManagedPolicyを
使ってみた](https://image.slidesharecdn.com/awscliassumerole-150517151026-lva1-app6892/85/AWS-CLI-AssumeRole-33-320.jpg)
![$ ATTACHED_ROLE_POLICY_NAME=`aws iam list-attached-role-policies --role-name ${IAM_ROLE_NAME}
--query "AttachedPolicies[0].PolicyName" --output text`
$ aws iam get-account-authorization-details --filter LocalManagedPolicy
--query "Policies[?PolicyName==`${ATTACHED_ROLE_POLICY_NAME}`]"
[
{
"PolicyName": "AfterAssumeRole-Policy",
"CreateDate": "2015-05-14T04:10:33Z",
"AttachmentCount": 2,
"IsAttachable": true,
"PolicyId": "ANPAJTNO5P4GDC4GTFPC2",
"DefaultVersionId": "v1",
"PolicyVersionList": [
{
"CreateDate": "2015-05-14T04:10:33Z",
"VersionId": "v1",
"Document": {
"Version": "2012-10-17",
"Statement": [
{
"Action": "s3:*",
"Resource": "*",
"Effect": "Allow"
}
]
},
"IsDefaultVersion": true
}
],
"Path": "/",
"Arn": "arn:aws:iam::222233334444:policy/AfterAssumeRole-Policy",
"UpdateDate": "2015-05-14T04:10:33Z"
}
]
S3フルアクセス権限のみ付与する例
{
"Action": "s3:*",
"Resource": "*",
"Effect": "Allow"
}](https://image.slidesharecdn.com/awscliassumerole-150517151026-lva1-app6892/85/AWS-CLI-AssumeRole-34-320.jpg)



![(補足2)configファイル利用で
簡単にAssumeRole
[profile assumed]
role_arn = arn:aws:iam::222233334444:role/IAM-Role-AssumeTest
source_profile = IAM-User-AssumeTest
上記設定で、Assumed Roleがprofileの1つ(--profile)として利用できる
source_profileを指定する場合は、事前設定が必要
期限が切れても自動更新されるのでセキュリティに要注意
(参考)http://dev.classmethod.jp/cloud/aws/aws-cli-supports-assume-role-credentials-provider-and-mfa/](https://image.slidesharecdn.com/awscliassumerole-150517151026-lva1-app6892/85/AWS-CLI-AssumeRole-39-320.jpg)




