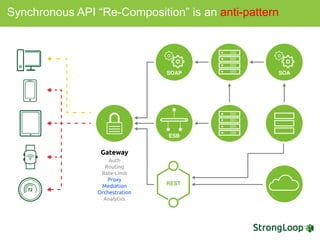
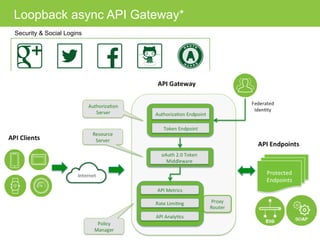
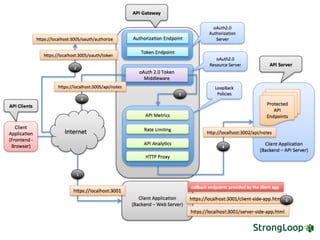
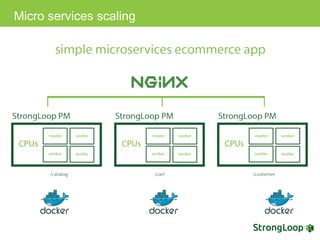
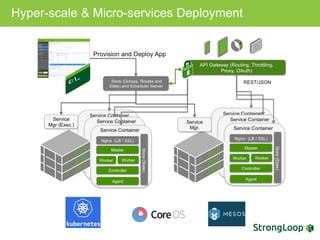
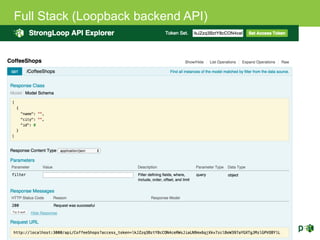
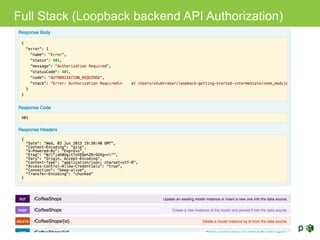
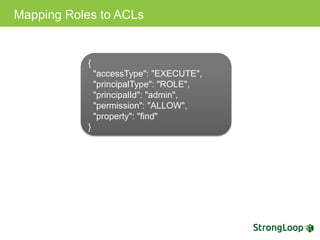
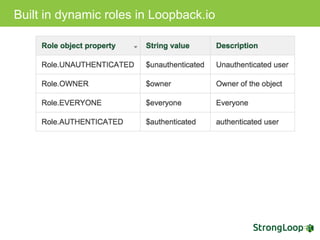
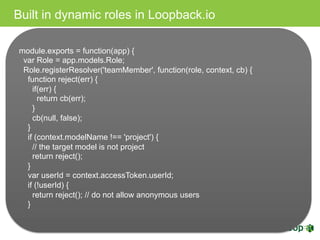
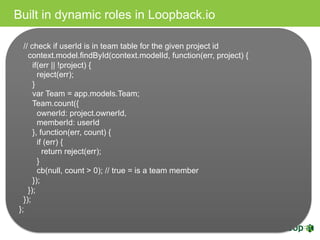
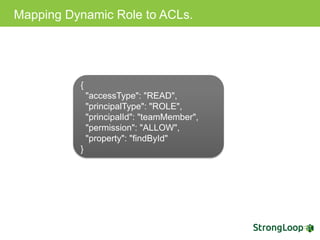
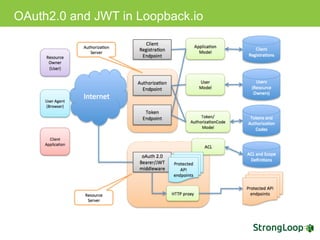
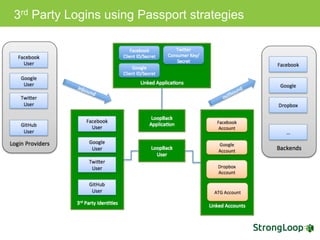
The document discusses various topics related to implementing authentication and authorization in LoopBack applications. It covers setting up SSL, configuring OAuth2, adding third-party login support using Passport strategies, defining roles and ACLs, and deploying LoopBack apps for microservices and hyper-scale.





![Static Roles in Loopback.io
User.create([
{username: 'John', email: 'john@doe.com', password: 'opensesame'},
{username: 'Jane', email: 'jane@doe.com', password: 'opensesame'},
{username: 'Bob', email: 'bob@projects.com', password: 'opensesame'}
], function(err, users) {
if (err) return cb(err);
//create the admin role
Role.create({
name: 'admin'
}, function(err, role) {
if (err) cb(err);
//make bob an admin
role.principals.create({
principalType: RoleMapping.USER,
principalId: users[2].id
}, function(err, principal) {
cb(err);
});
});
});](https://image.slidesharecdn.com/authenticatingandsecuringnode-150603200041-lva1-app6891/85/Authenticating-and-Securing-Node-js-APIs-8-320.jpg)
![Configuration – OAuth2.0 in Loopback.io
var oauth2 = require('loopback-component-oauth2');
var options = {
dataSource: app.dataSources.db, // Data source for oAuth2 metadata
persistence
loginPage: '/login', // The login page URL
loginPath: '/login' // The login form processing URL
};
oauth2.oAuth2Provider(
app, // The app instance
options // The options
);
oauth2.authenticate(['/protected', '/api', '/me'],
{session: false, scope: 'email'})](https://image.slidesharecdn.com/authenticatingandsecuringnode-150603200041-lva1-app6891/85/Authenticating-and-Securing-Node-js-APIs-16-320.jpg)

![Config – Facebook Authentication in Loopback.io
{
"facebook-login": {
"provider": "facebook",
"module": "passport-facebook",
"clientID": "{facebook-client-id-1}",
"clientSecret": "{facebook-client-secret-1}",
"callbackURL": "http://localhost:3000/auth/facebook
/callback",
"authPath": "/auth/facebook",
"callbackPath": "/auth/facebook/callback",
"successRedirect": "/auth/account",
"scope": ["email"]
}](https://image.slidesharecdn.com/authenticatingandsecuringnode-150603200041-lva1-app6891/85/Authenticating-and-Securing-Node-js-APIs-20-320.jpg)
![Config – Google Authentication in Loopback.io
{
"google-link": {
"provider": "google",
"module": "passport-google-oauth",
"strategy": "OAuth2Strategy",
"clientID": "{google-client-id-2}",
"clientSecret": "{google-client-secret-2}",
"callbackURL": "http://localhost:3000/link/google/
callback",
"authPath": "/link/google",
"callbackPath": "/link/google/callback",
"successRedirect": "/link/account",
"scope": ["email", "profile"],
"link": true
}](https://image.slidesharecdn.com/authenticatingandsecuringnode-150603200041-lva1-app6891/85/Authenticating-and-Securing-Node-js-APIs-21-320.jpg)
![Config – MS AD Authentication in Loopback.io
{
"ms-ad": {
"provider": "ms-ad",
"authScheme":"ldap",
"module": "passport-ldapauth",
"authPath": "/auth/msad",
"successRedirect": "/auth/account",
"failureRedirect": "/msad",
"failureFlash": true,
"session": true,
"LdapAttributeForLogin": "mail",
"LdapAttributeForUsername": "mail",
"LdapAttributeForMail": "mail",
"server":{
"url": "ldap://ldap.example.org:389/dc=example,dc=org",
"bindDn": "bindUsername",
"bindCredentials": "bindPassword",
"searchBase": "ou=people,dc=example,dc=org",
"searchAttributes": ["cn", "mail", "uid", "givenname"],
"searchFilter": "(&(objectcategory=person)(objectclass=user)(|(s
amaccountname={{username}})(mail={{username}})))"
}
}](https://image.slidesharecdn.com/authenticatingandsecuringnode-150603200041-lva1-app6891/85/Authenticating-and-Securing-Node-js-APIs-22-320.jpg)

![Application Level using Passport configurator
// Initialize passport
passportConfigurator.init();
// Set up related models
passportConfigurator.setupModels({
userModel: app.models.user,
userIdentityModel: app.models.userIdentity,
userCredentialModel: app.models.userCredential
});
// Configure passport strategies for third party auth providers
for(var s in config) {
var c = config[s];
c.session = c.session !== false;
passportConfigurator.configureProvider(s, c);
}](https://image.slidesharecdn.com/authenticatingandsecuringnode-150603200041-lva1-app6891/85/Authenticating-and-Securing-Node-js-APIs-24-320.jpg)