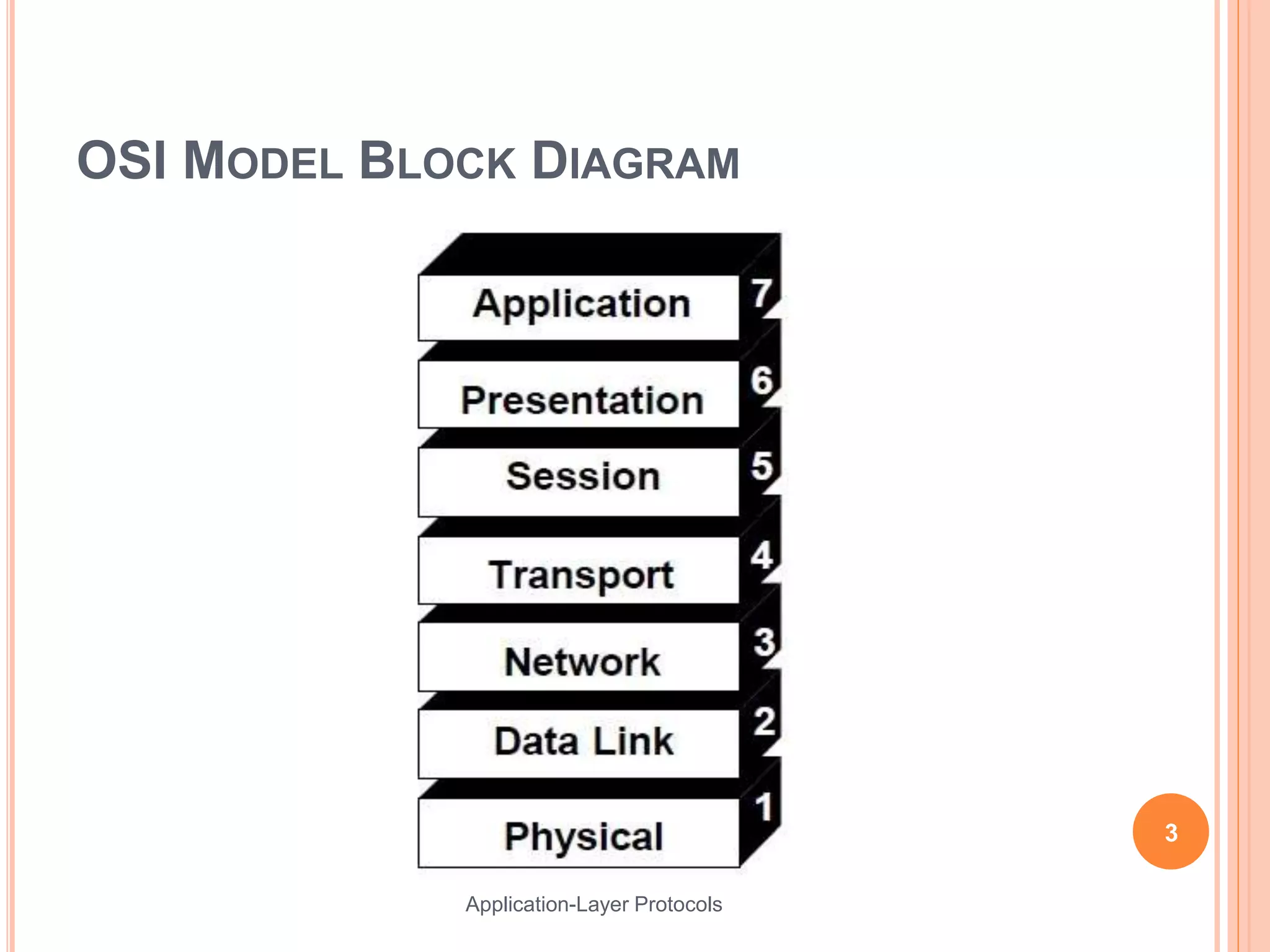
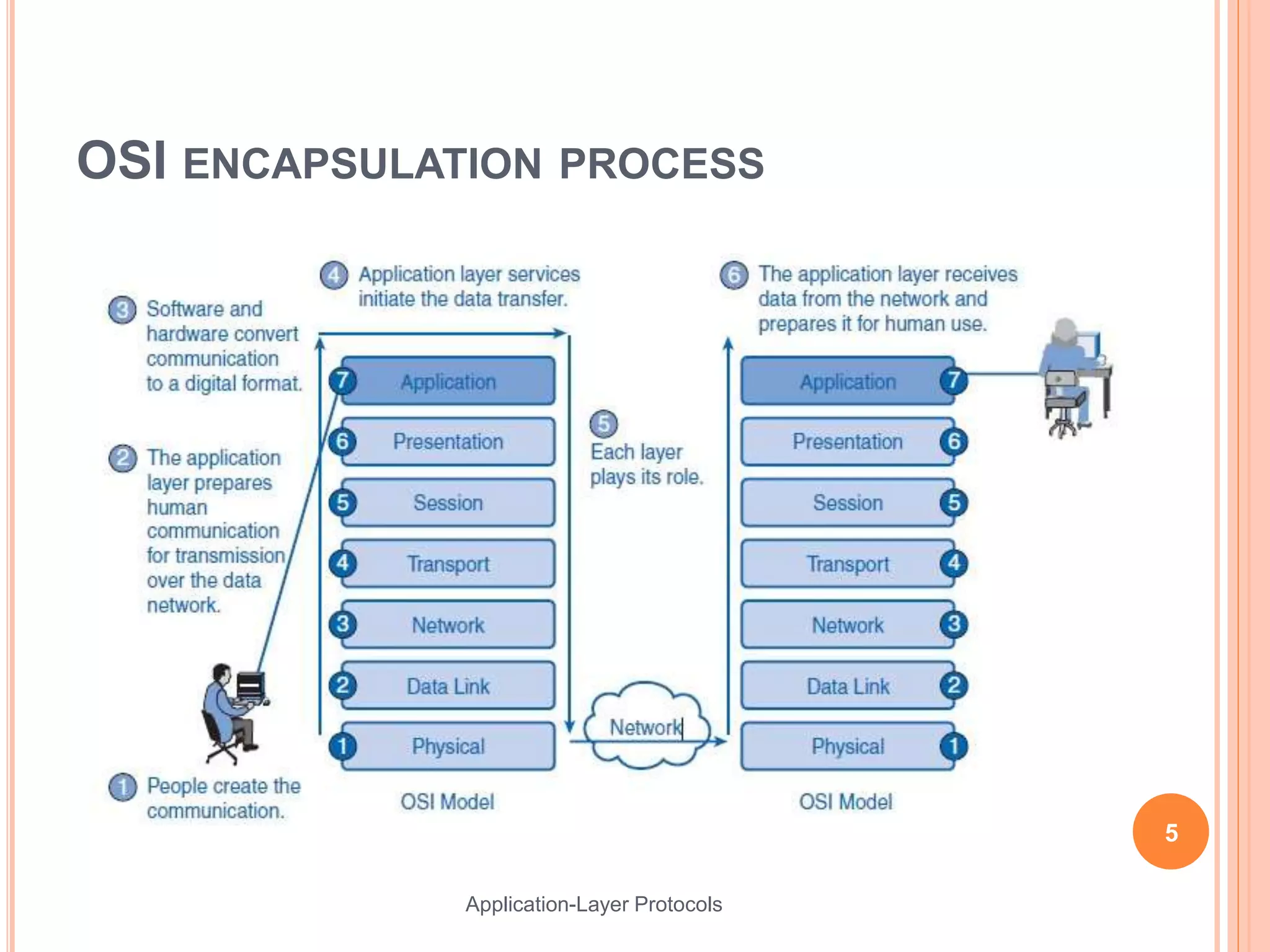
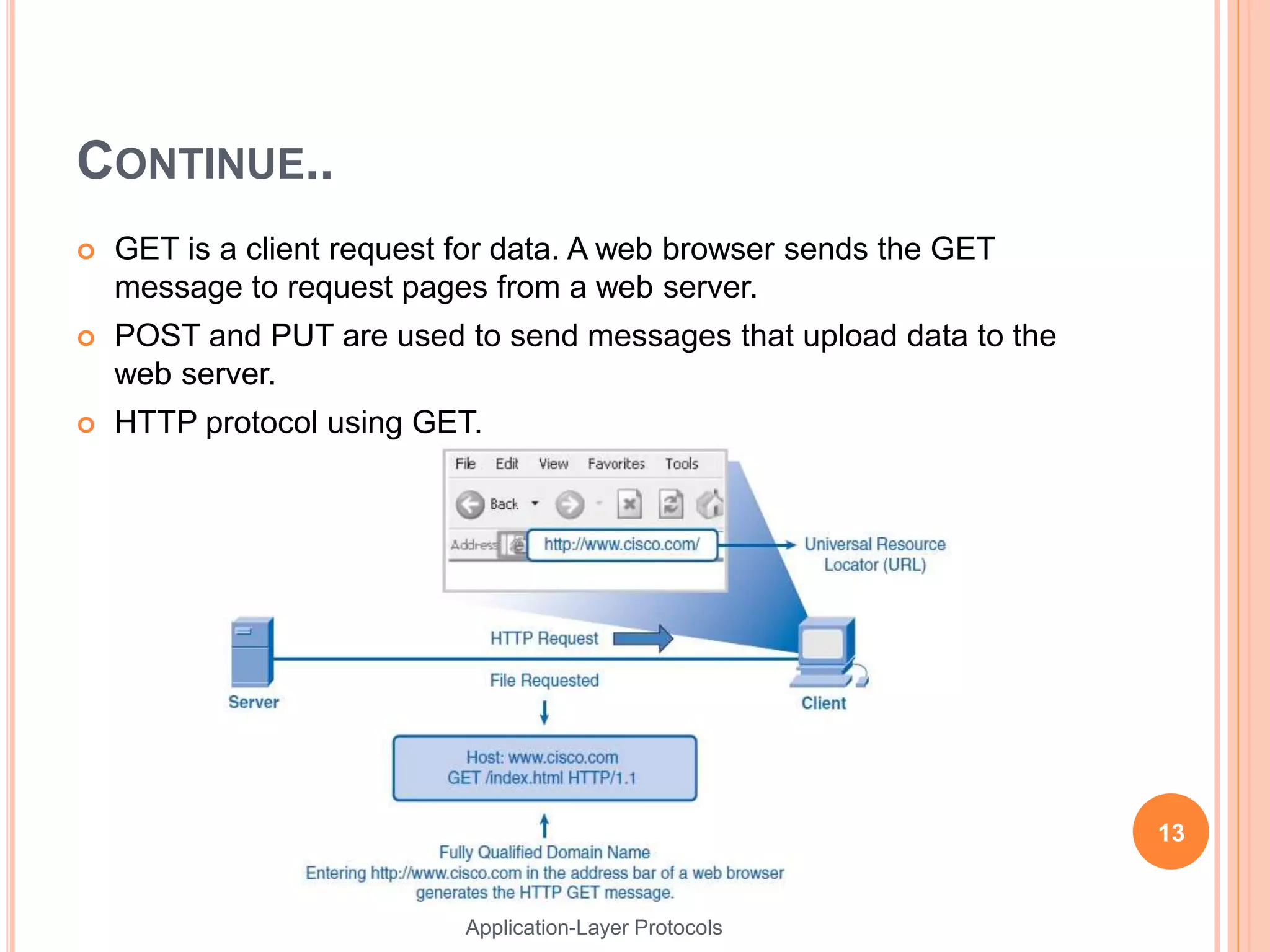
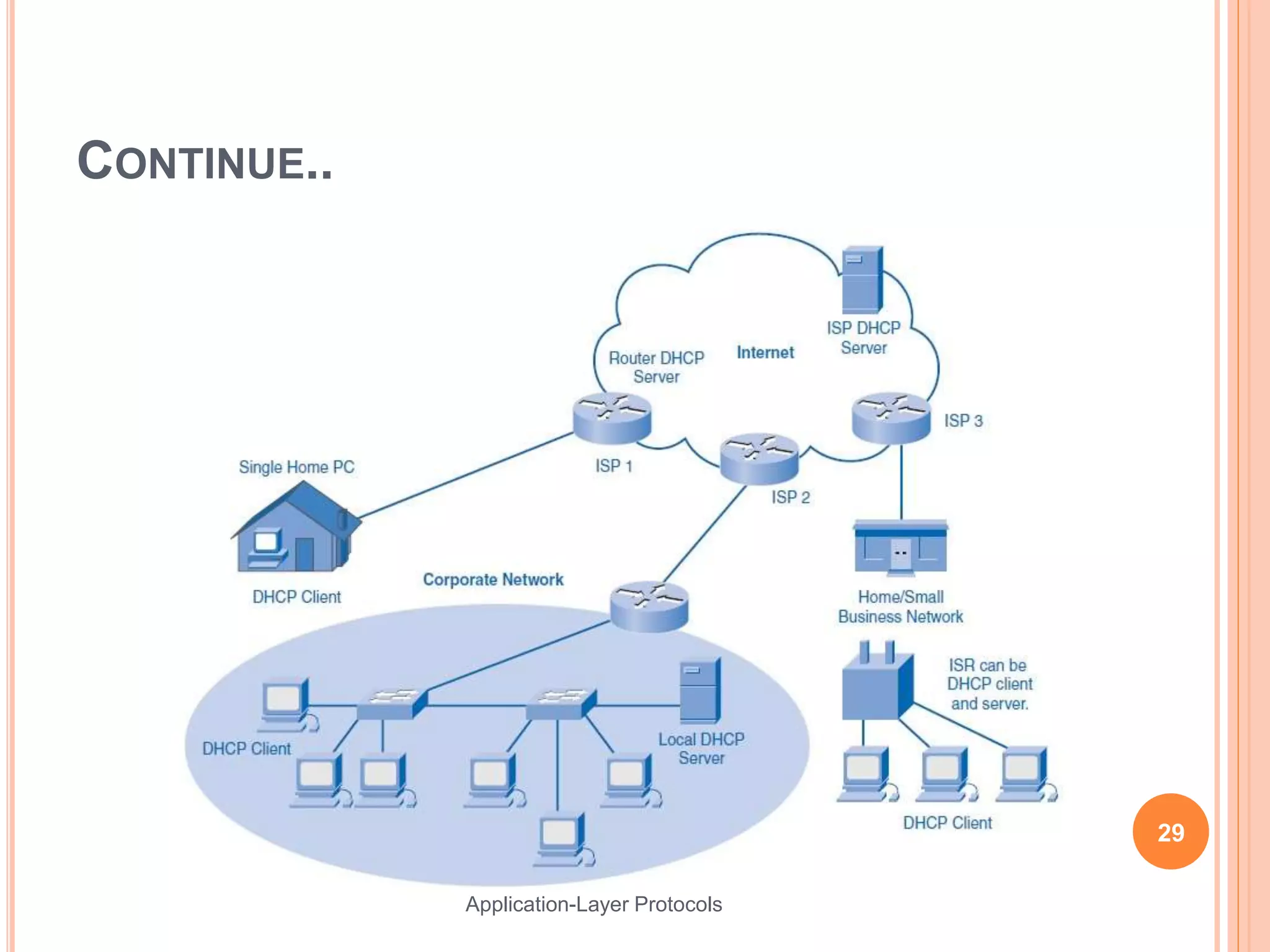
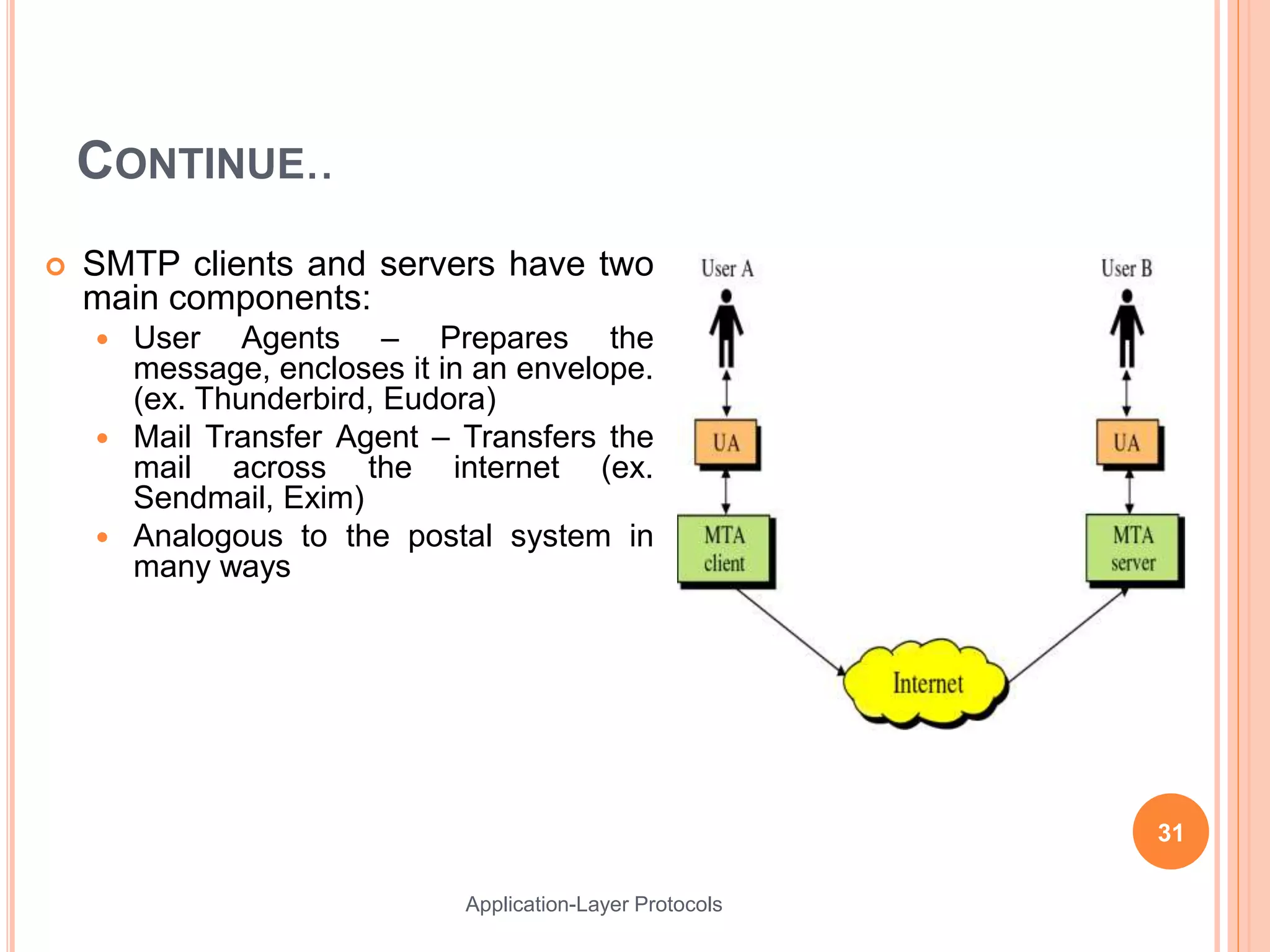
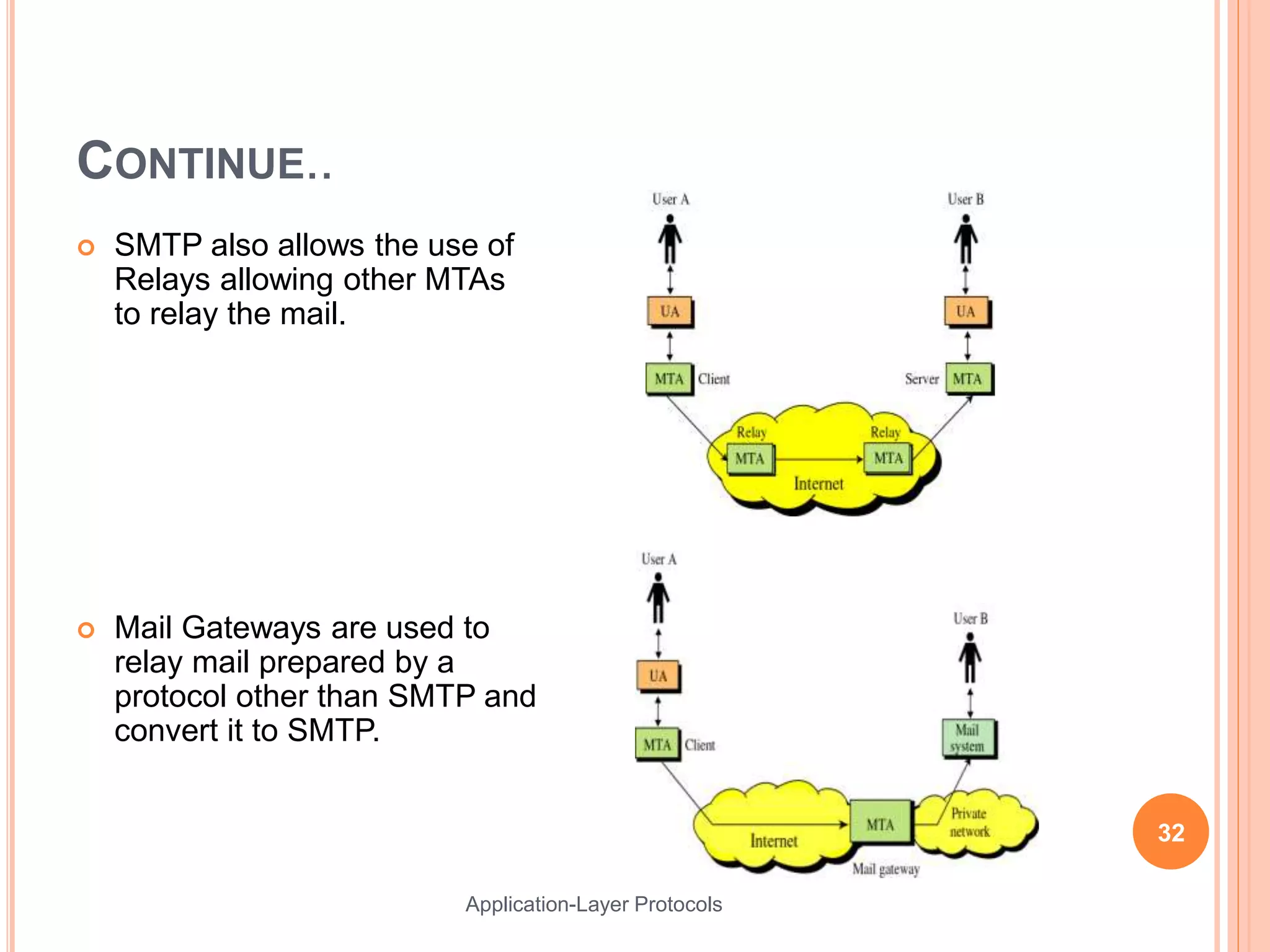
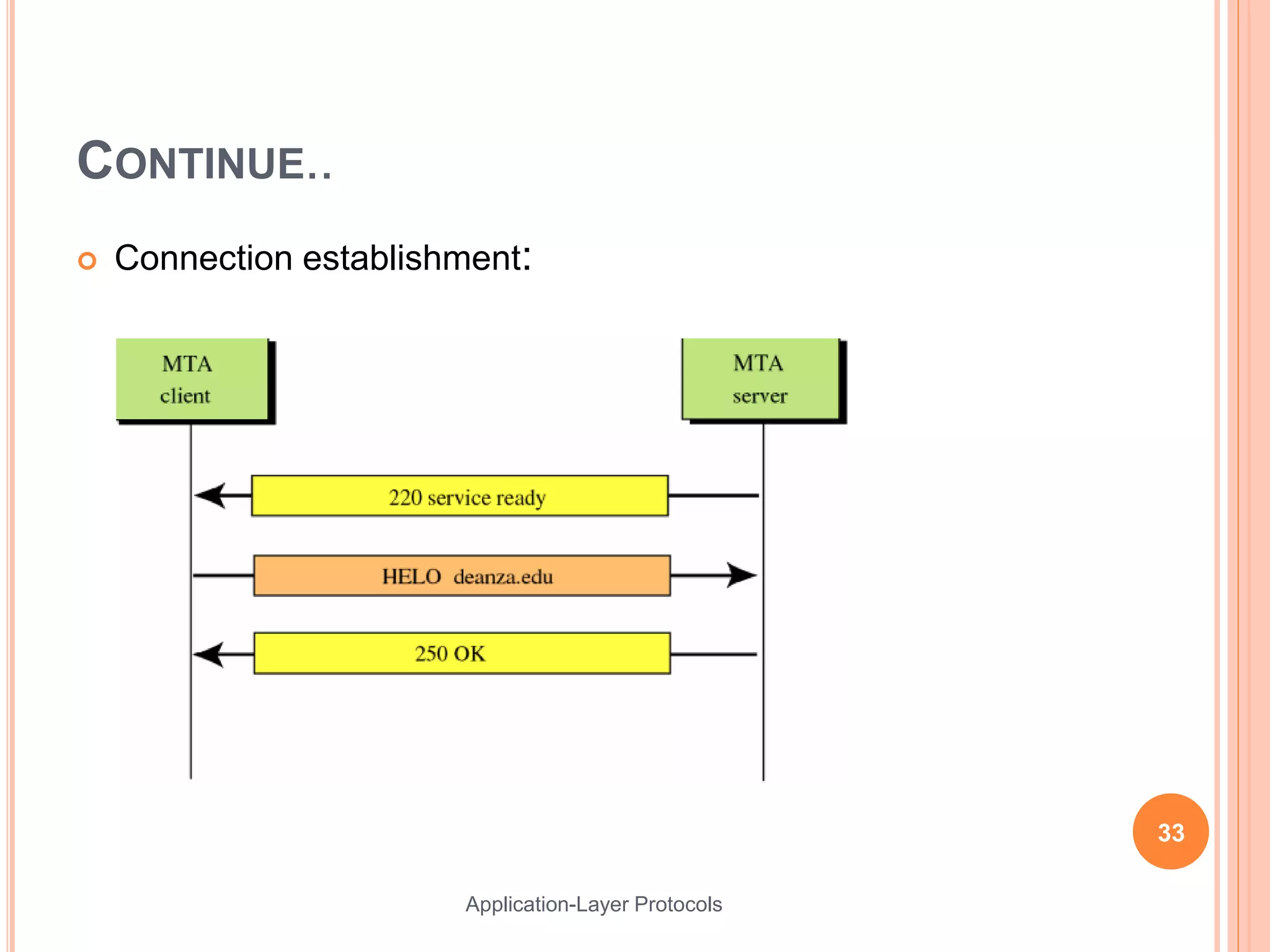
This document discusses various application layer protocols. It begins with an agenda that lists OSI models, encapsulation processes, application protocol design, and specific protocols including HTTP, DNS, FTP, Telnet, DHCP, and SMTP. For each protocol, it provides details on how the protocol functions, message formats, and roles of clients and servers. The document is intended to describe key application layer protocols and their basic operations.