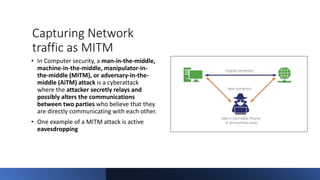
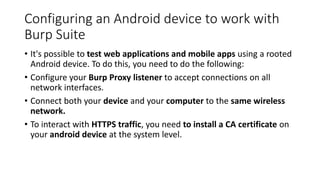
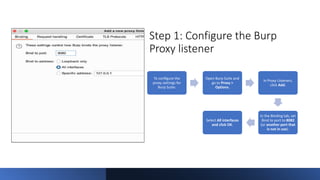
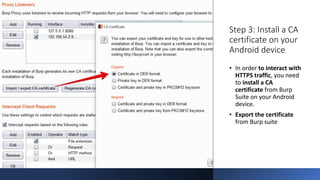
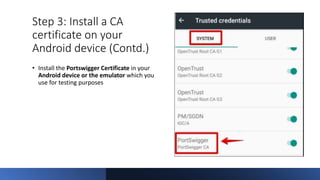
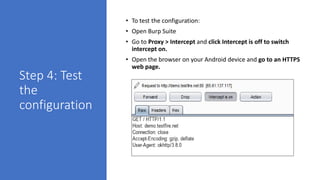
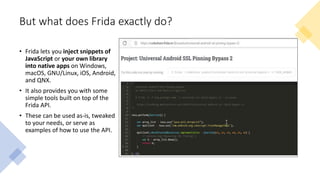
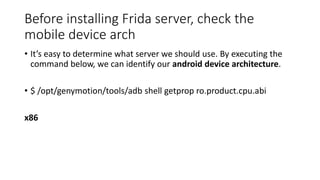
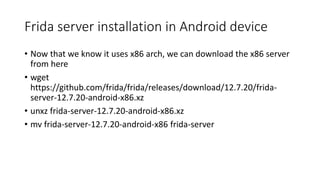
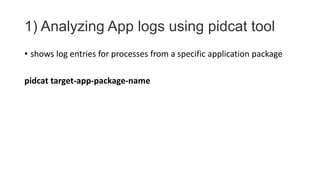
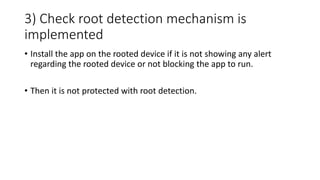
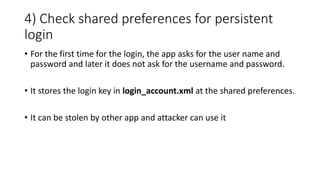
The document provides a comprehensive agenda for an Android hacking session focusing on network analysis and dynamic analysis using Burp Suite, including configuration steps for intercepting HTTPS traffic. It details various security tests and recommendations to mitigate vulnerabilities, such as effectively managing sessions, preventing clickjacking, and ensuring secure communications. The document offers practical guidance on using Frida for bypassing SSL pinning and emphasizes the importance of secure coding practices throughout app development.