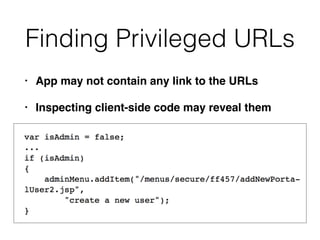
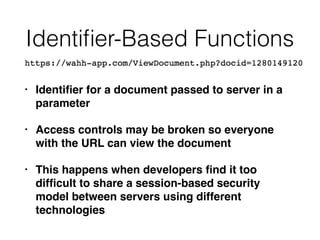
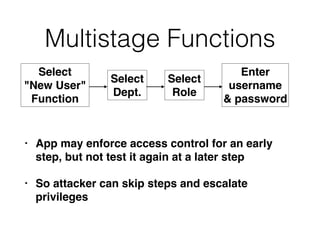
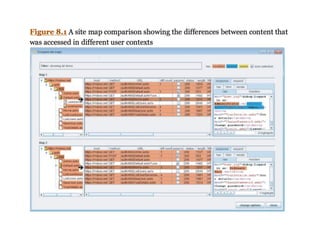
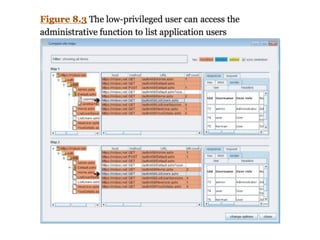
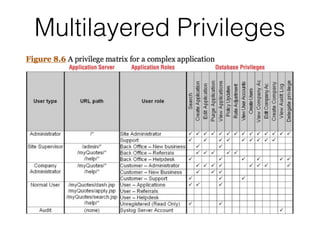
This document discusses common vulnerabilities in access controls for web applications and best practices for securing them. It covers different types of privilege escalation like vertical, horizontal, and context-dependent escalation. It also discusses vulnerabilities like unprotected functionality that can be accessed without authentication, identifier-based functions where access is based on predictable IDs, and multistage functions where access is not re-validated at each step. The document provides recommendations for testing access controls and securing them through measures like centralizing control checks and restricting access based on sessions rather than request parameters.