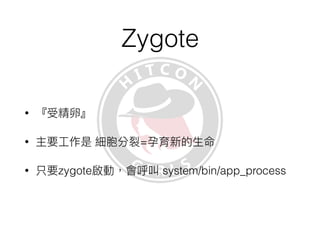
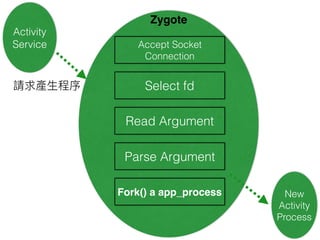
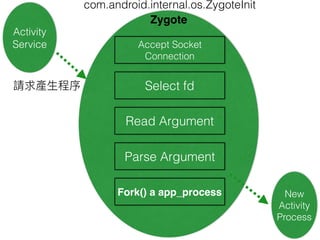
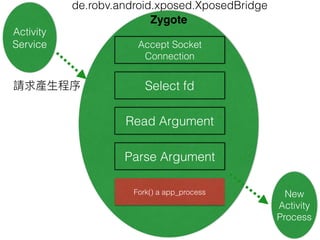
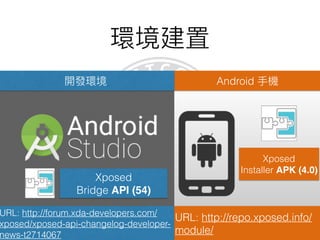
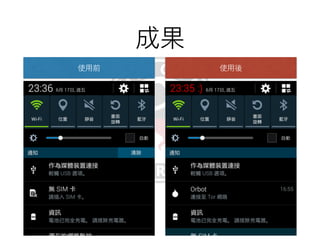
This document discusses the Xposed Framework, which allows modifying and hooking into system level Android apps. It covers how the Zygote process works in Android to launch new processes, and how Xposed hooks into this by intercepting calls to the ZygoteInit class. It then provides an overview of how to create an Xposed module to hook into and modify another app, using the System Clock app as an example.
![Android Hook -
Xposed Framework
[Android Penetration Testing] Elven
2016/06](https://image.slidesharecdn.com/androidhookxposedframewrok-160817131828/75/Android-Hook-Xposed-Framework-Elven-Liu-1-2048.jpg)
![Who am I?
• Elven Liu
•
•
•
•
• HITCON GIRLS [Android Penetration Testing]
• liuelven@gmail.com
• www.linkedin.com/in/liu-elven](https://image.slidesharecdn.com/androidhookxposedframewrok-160817131828/85/Android-Hook-Xposed-Framework-Elven-Liu-2-320.jpg)