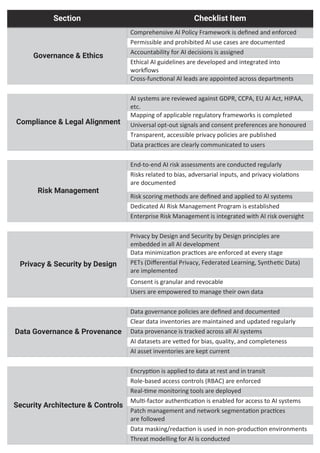
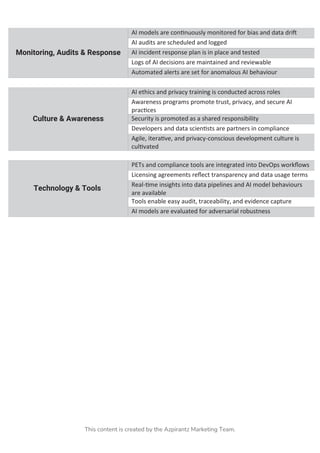
The AI GRC Implementation Checklist is your go-to guide to embed trust, accountability, and security into your AI initiatives. From governance and privacy to risk management and compliance, this end-to-end checklist helps ensure your AI systems are responsible, resilient, and regulation-ready.
Ethics
Legal Alignment
Privacy and Security
Data Governance
Monitoring and Response
Download the checklist now and benchmark your AI program!