Embed presentation
Download to read offline

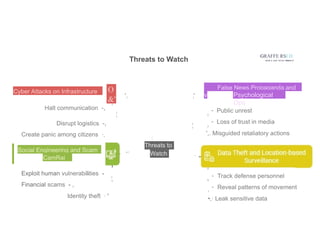
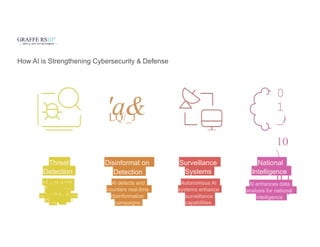
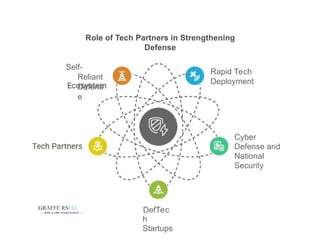
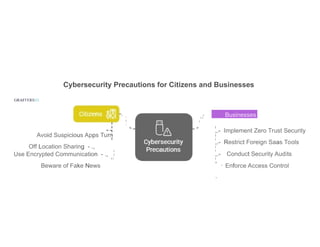

Explore how AI and emerging technologies are transforming cybersecurity and reshaping national security in 2025. This guide covers advancements in threat detection, automated response systems, predictive analytics, and AI-driven defense strategies that help governments and organizations protect against increasingly sophisticated cyber threats and ensure data integrity.




