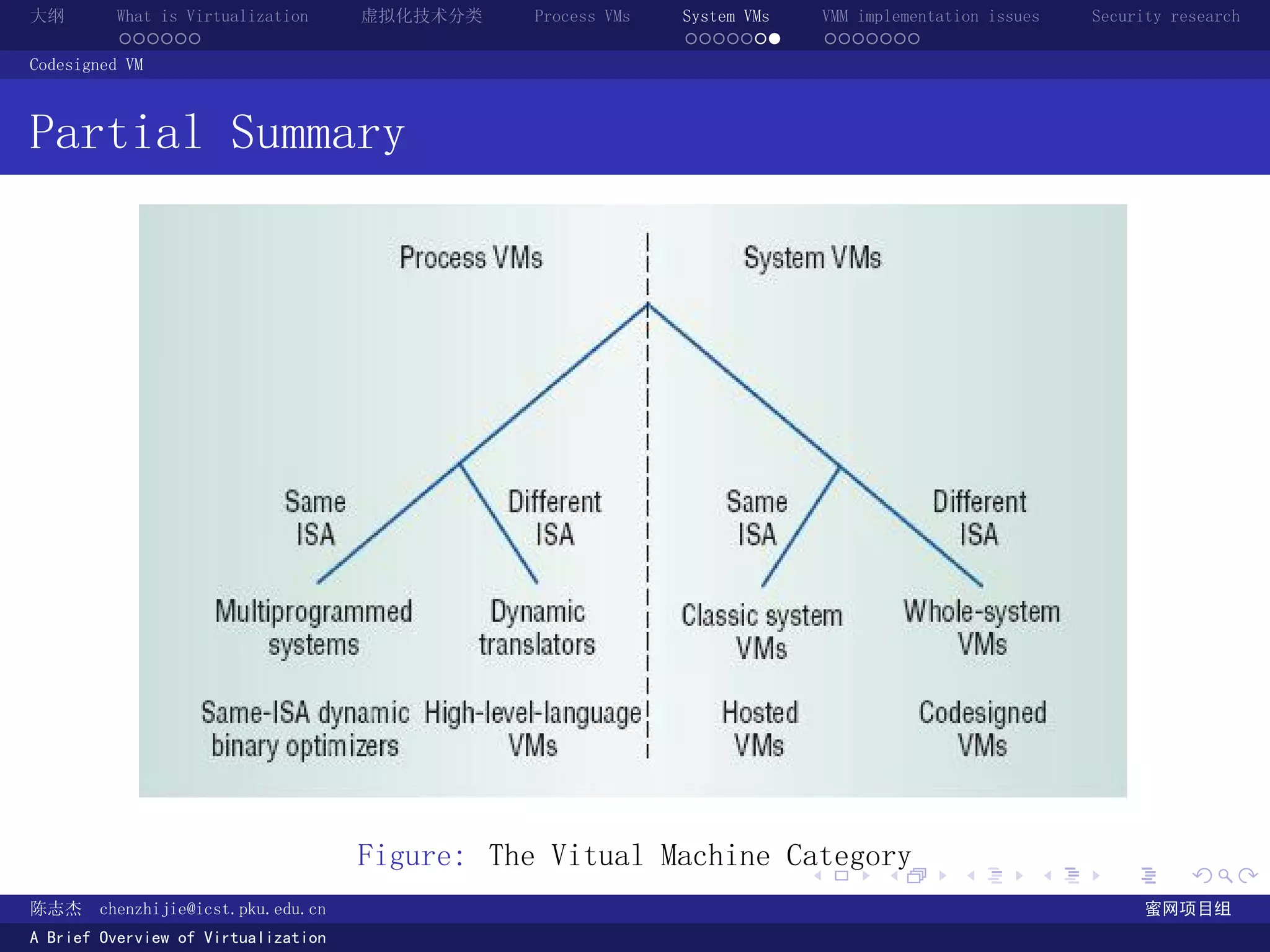
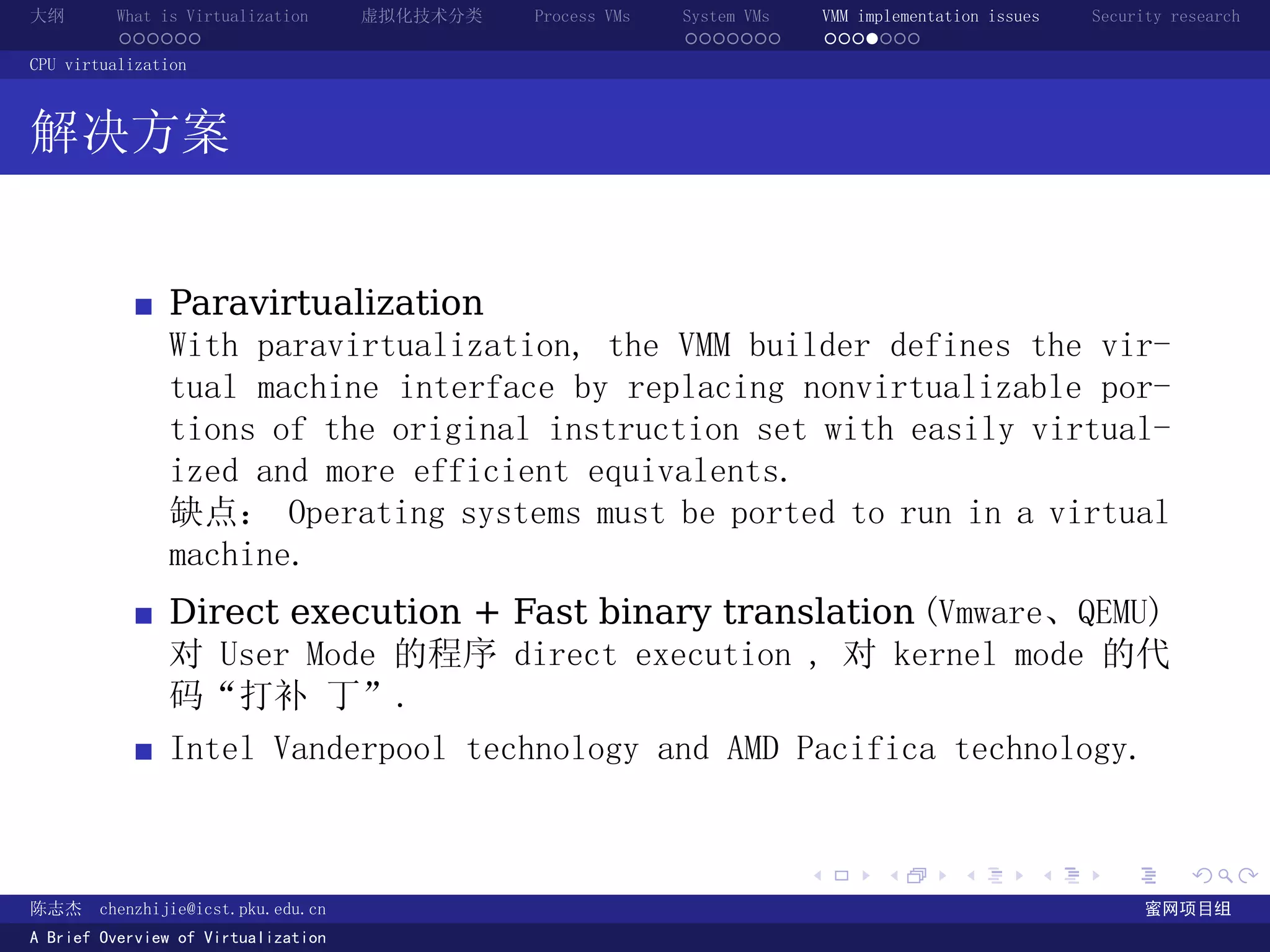
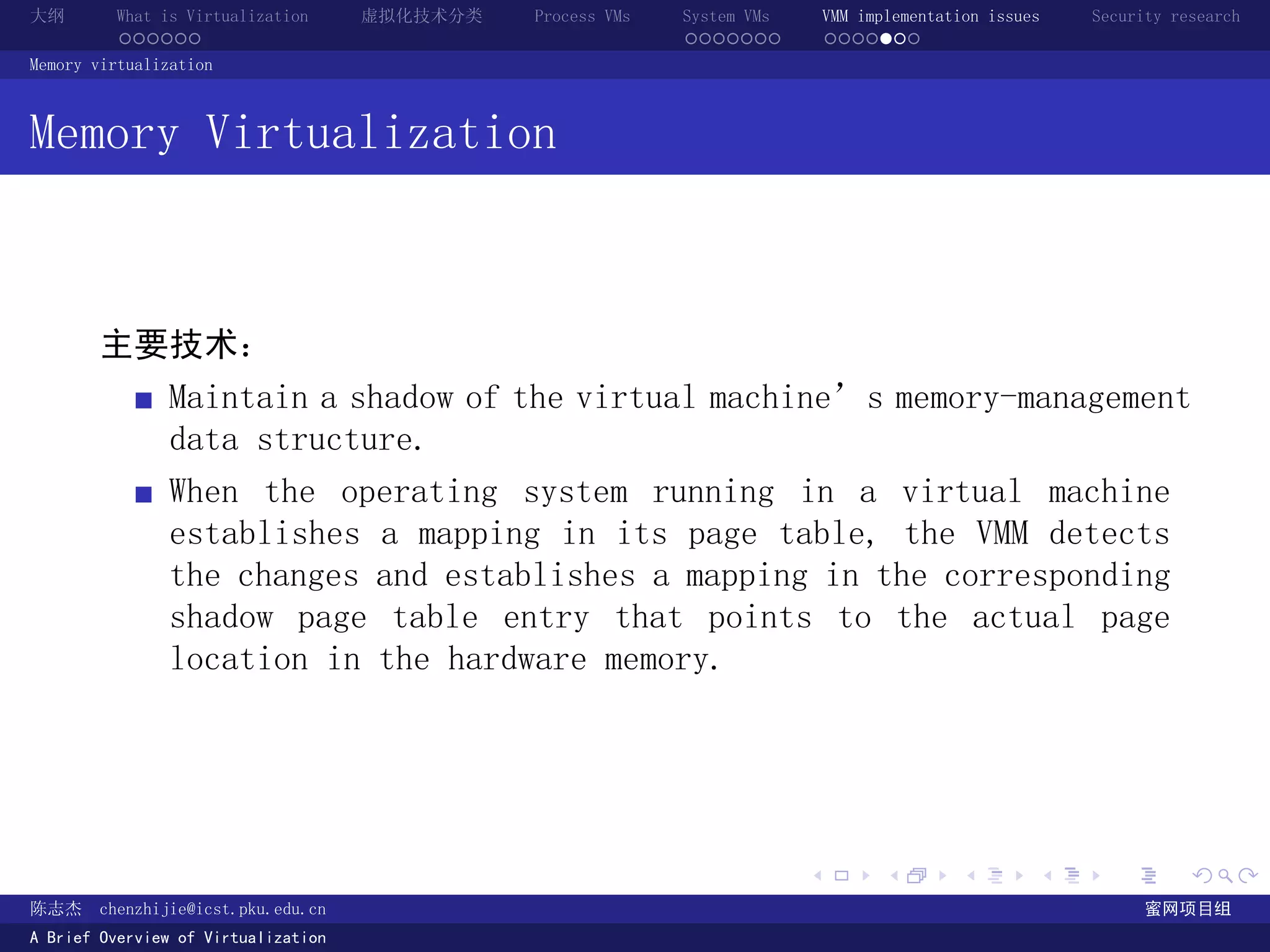
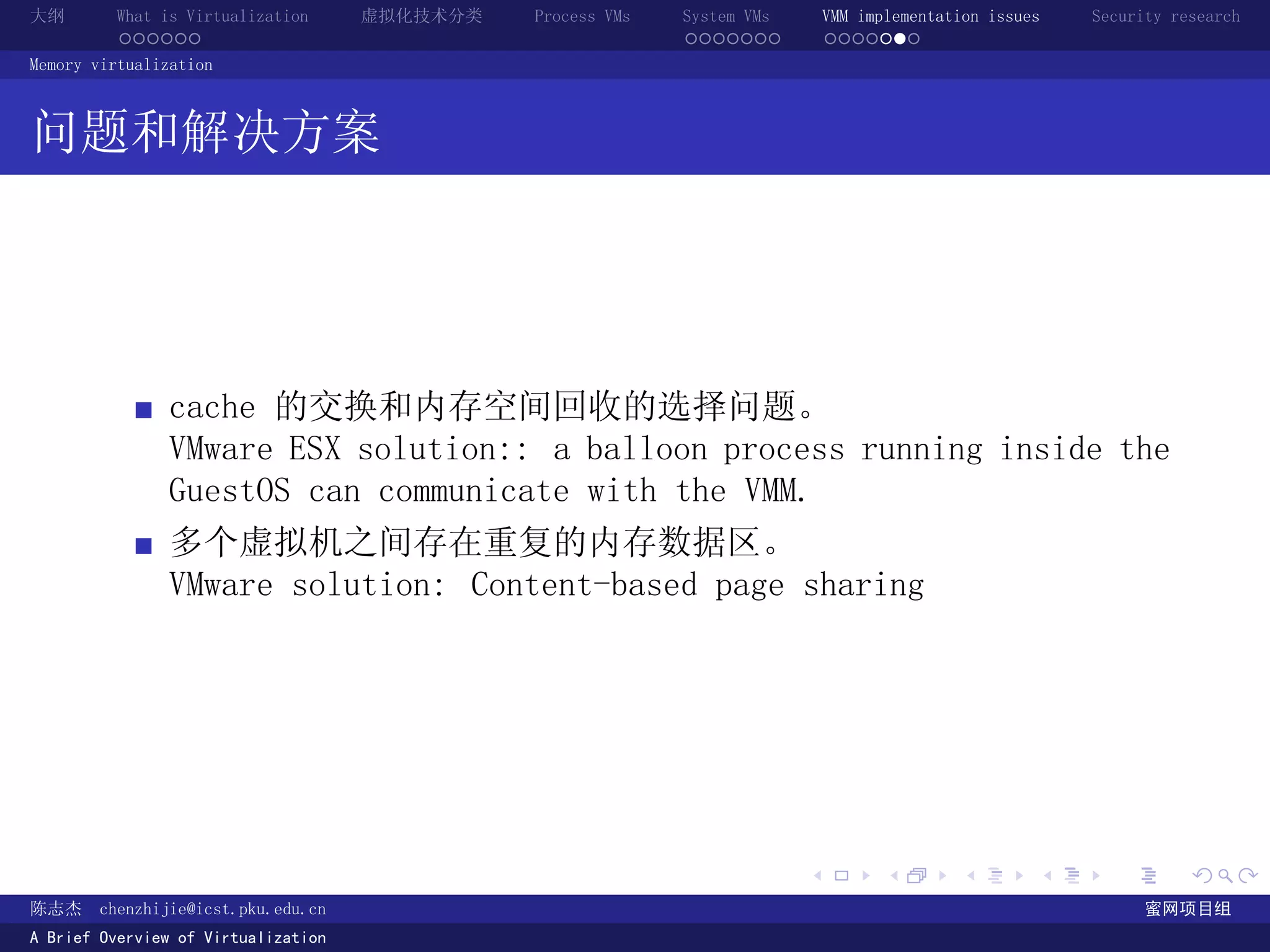
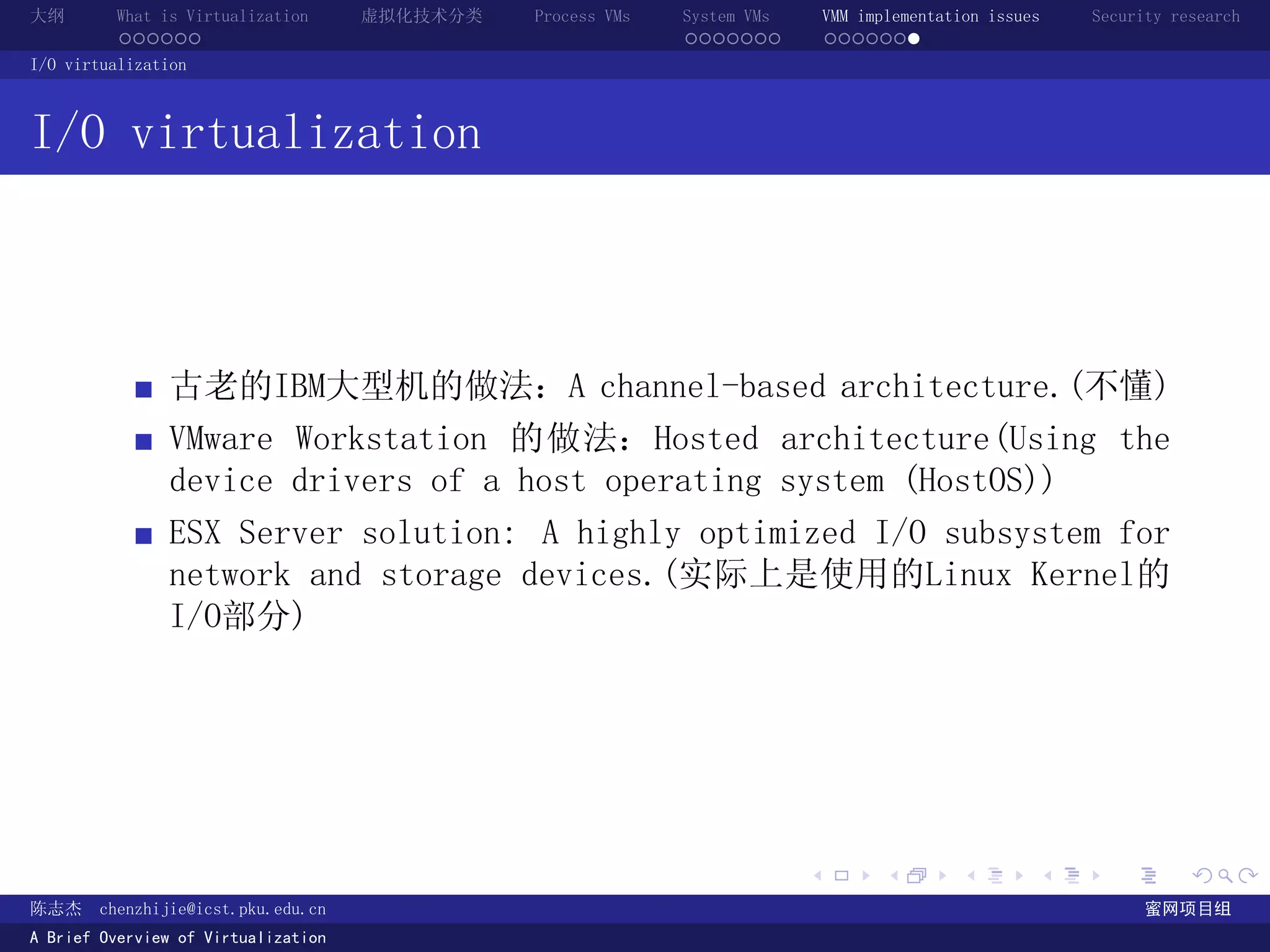
The document provides an overview of virtualization technology, including definitions of virtualization, classifications of virtualization techniques, and discussions of process VMs, system VMs, and virtual machine monitor implementation issues and security research. It defines virtualization as making one computer system appear to be another system and discusses how virtualization provides abstraction through defined interfaces between layers.
![大纲 What is Virtualization 虚拟化技术分类 Process VMs System VMs VMM implementation issues Security research
...... ....... .......
Defination
What is Virtualization ?
To virtualize means to take something of one form and make
it appear to be another form.[1]
To make a computer appear to be multiple computers or a
different computer entirely.
To making many computers appear to be a single computer.
(Server Aggregation/Grid Computing)
我们这里讨论的虚拟化指的是前者。
不过目前的趋势是合二为一,即将一些分离的计算资源抽象成统
一的资源库, 然后再由 Virtual Machine Infrastructure 统一
调度,分配给多个虚拟的机器。
. . . . . .
陈志杰 chenzhijie@icst.pku.edu.cn 蜜网项目组
A Brief Overview of Virtualization](https://image.slidesharecdn.com/vmintroslidesv0-2-090915034854-phpapp02/75/A-Brief-Overview-of-Virtualization-4-2048.jpg)

![大纲 What is Virtualization 虚拟化技术分类 Process VMs System VMs VMM implementation issues Security research
...... ....... .......
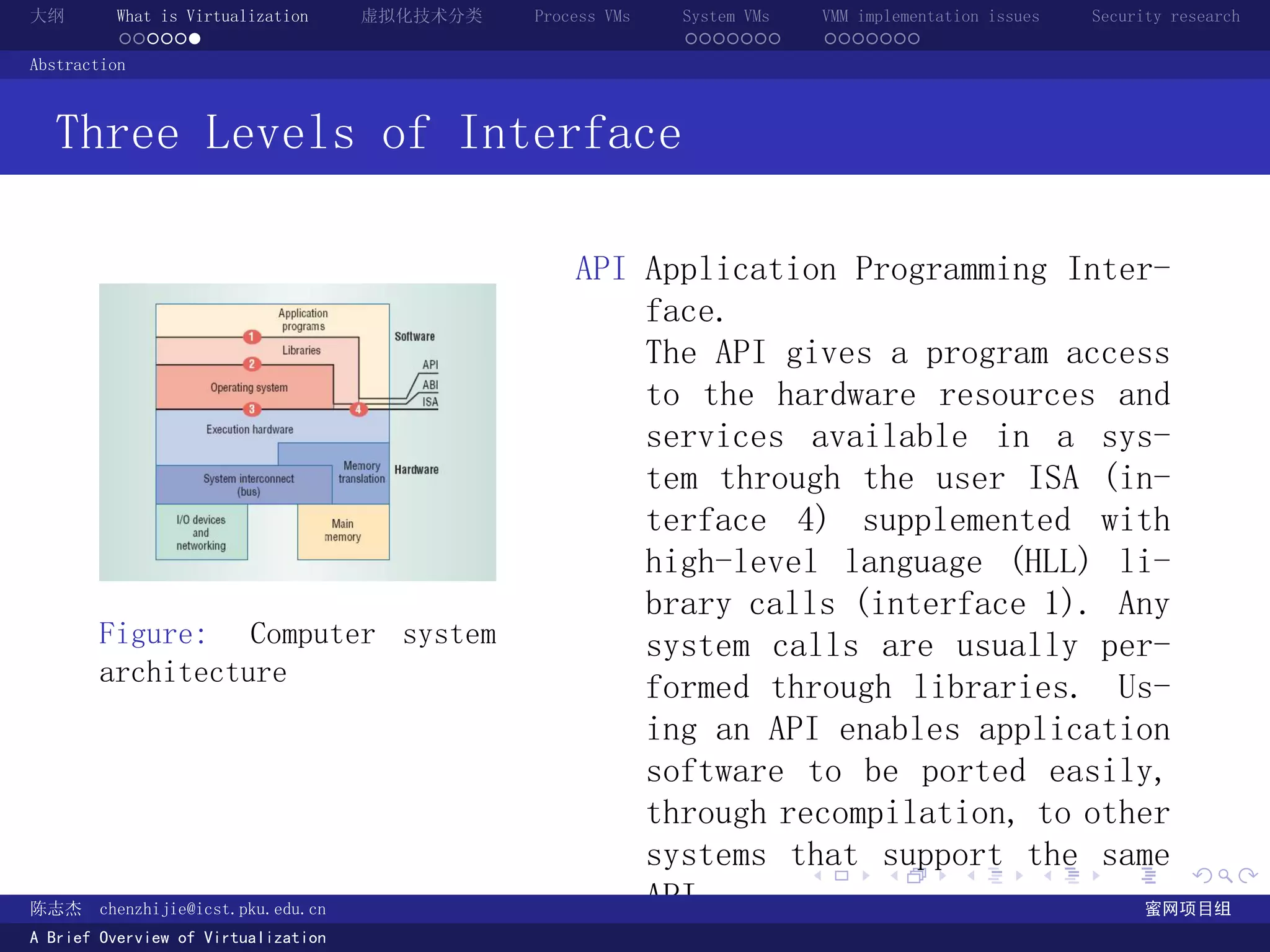
Abstraction
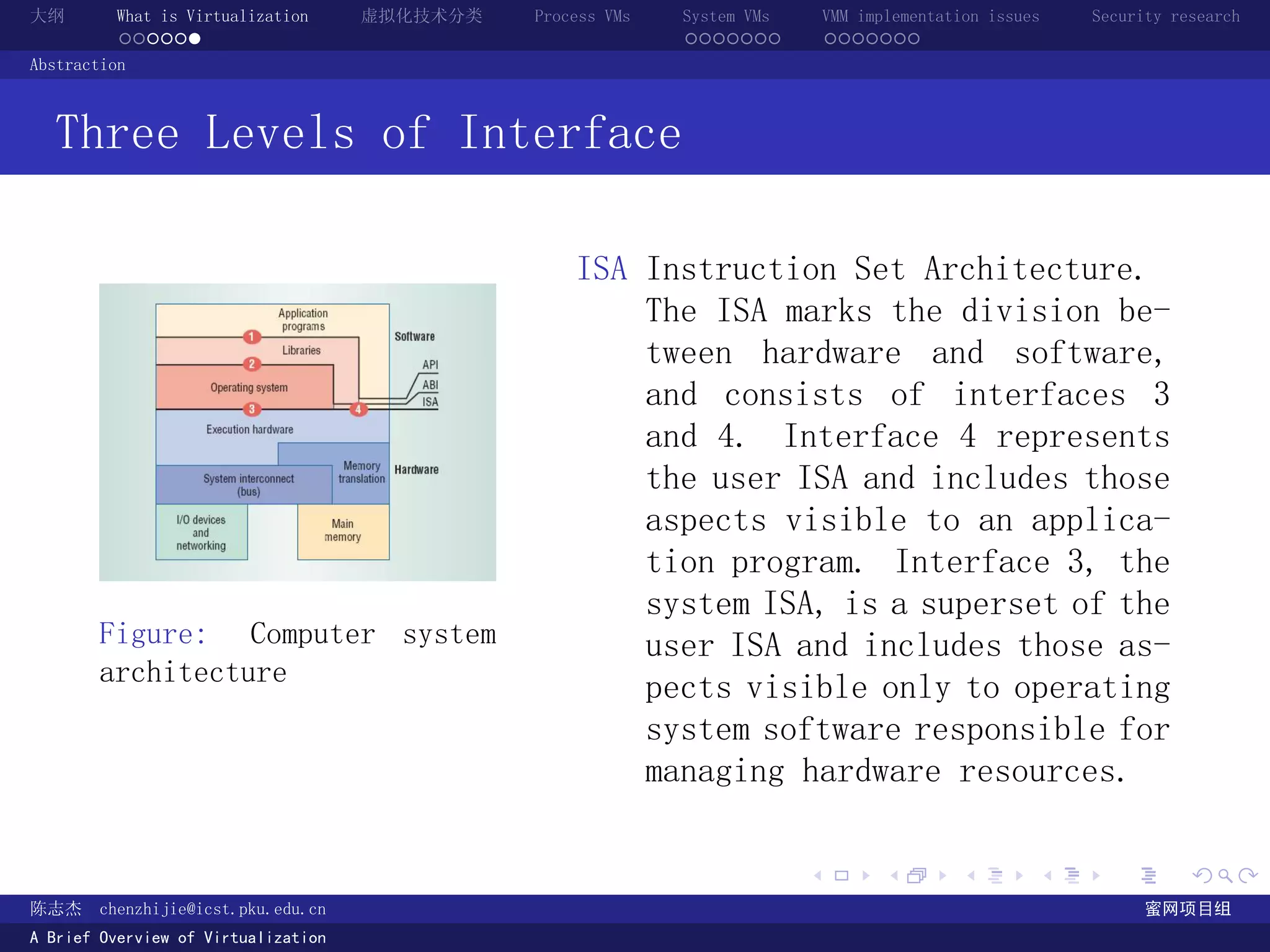
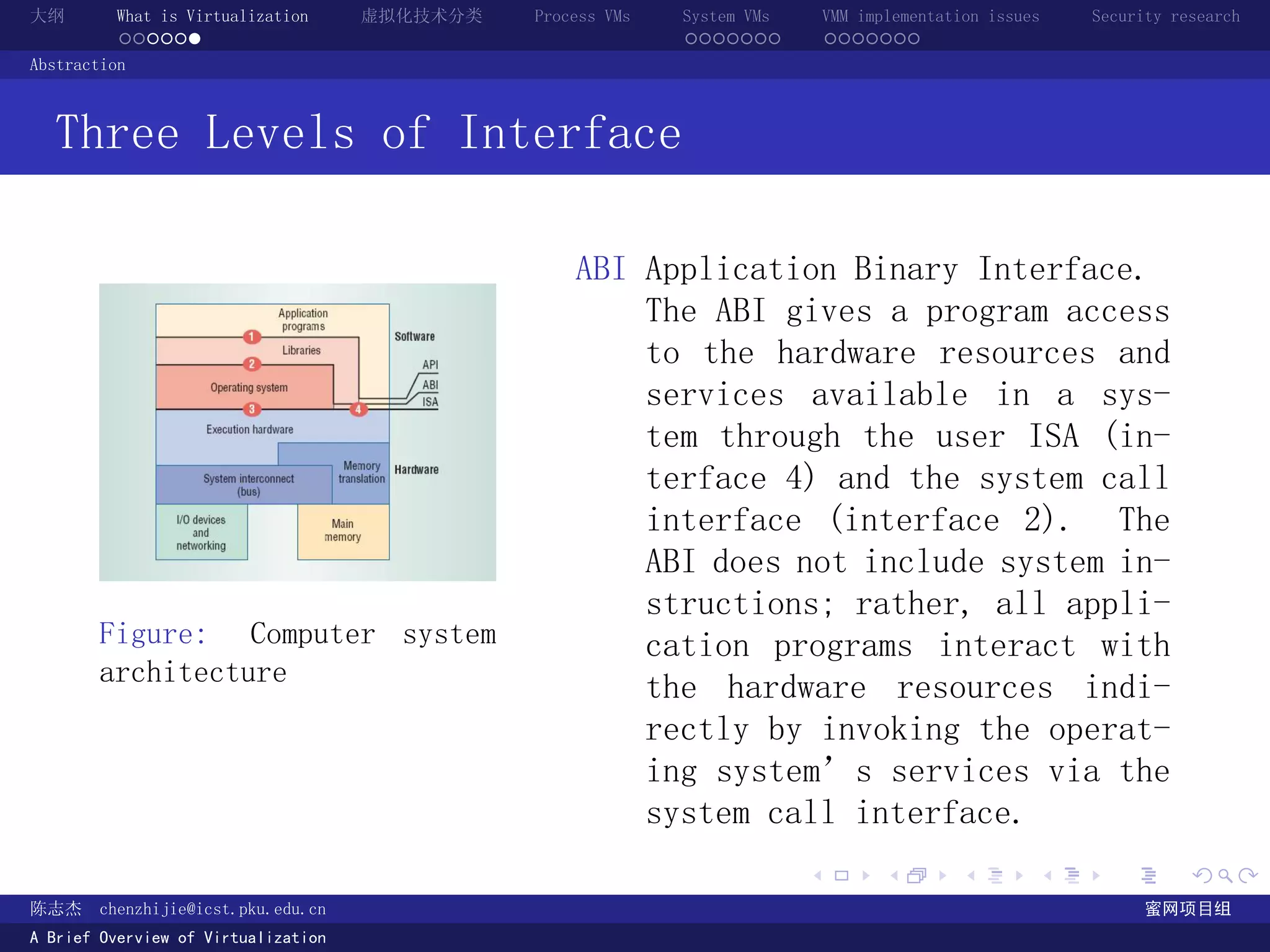
计算机系统的三层 Interface [2]
ISA Instruction
Set Architec-
ture.
ABI Application
Binary Inter-
face.
API Application
Programming
Interface.
Figure: Computer system architecture
. . . . . .
陈志杰 chenzhijie@icst.pku.edu.cn 蜜网项目组
A Brief Overview of Virtualization](https://image.slidesharecdn.com/vmintroslidesv0-2-090915034854-phpapp02/75/A-Brief-Overview-of-Virtualization-7-2048.jpg)



![大纲 What is Virtualization 虚拟化技术分类 Process VMs System VMs VMM implementation issues Security research
...... ....... .......
参考文献
[1] M. Tim Jones
Virtual Linux –An overview of virtualization methods, architectures, and
implementations [EB/OL].
IBM DeveloperWorks.
http://www.ibm.com/developerworks/library/l-linuxvirt/ .
[2] James E.Smith and Ravi Nair
The Architecture of Virtual Machines [J]
Computer, May 2005 IEEE.
[3] Mendel Rosenblum and Tal Garfinkel
Virtual Machine Monitors: Current Technology and Future Trends [J].
Computer, May 2005 IEEE.
[4] Fabrice Bellard
QEMU, a Fast and Portable Dynamic Translator.
2005 USENIX Annual Technical Conference.
. . . . . .
陈志杰 chenzhijie@icst.pku.edu.cn 蜜网项目组
A Brief Overview of Virtualization](https://image.slidesharecdn.com/vmintroslidesv0-2-090915034854-phpapp02/75/A-Brief-Overview-of-Virtualization-37-2048.jpg)