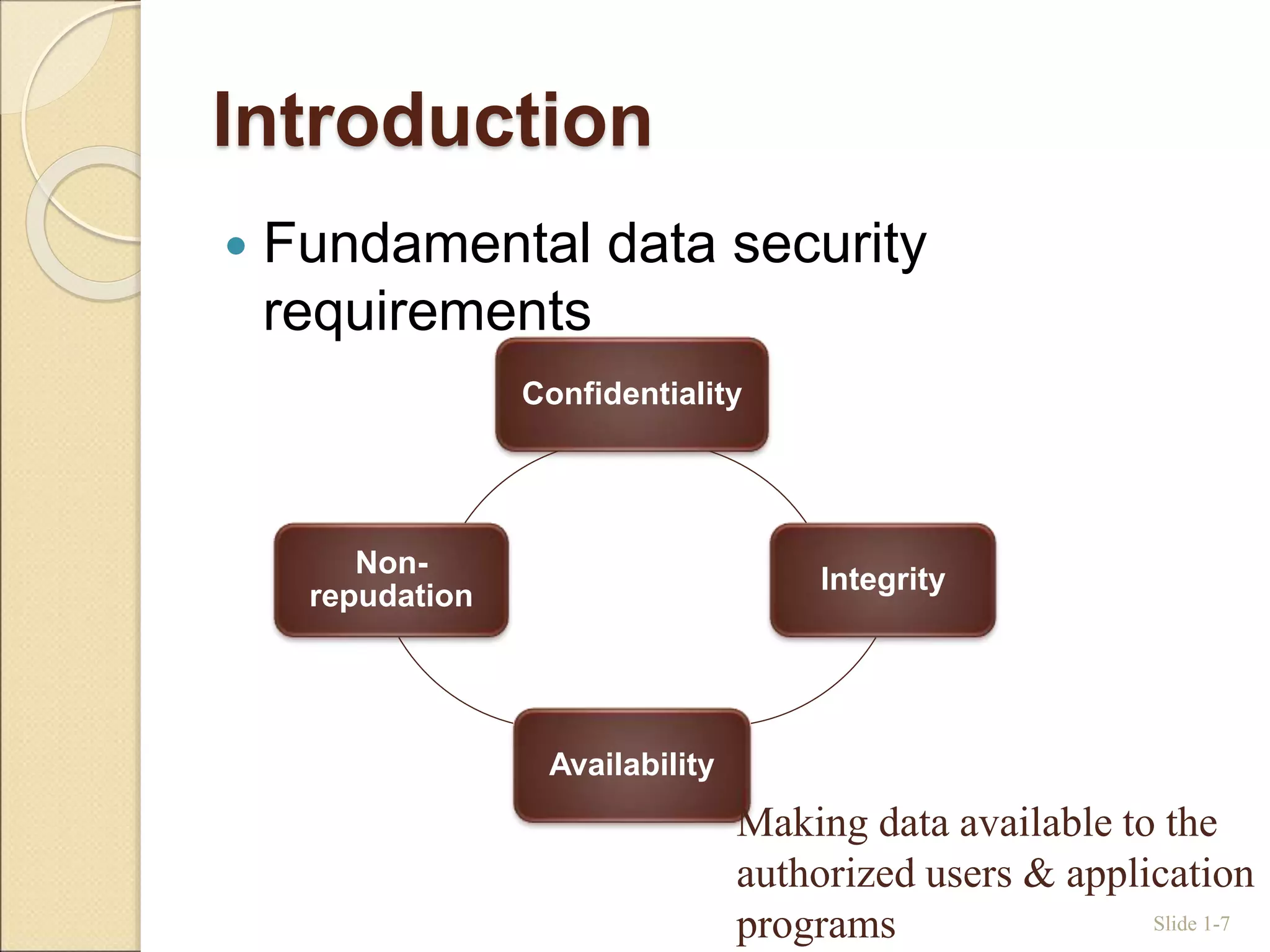
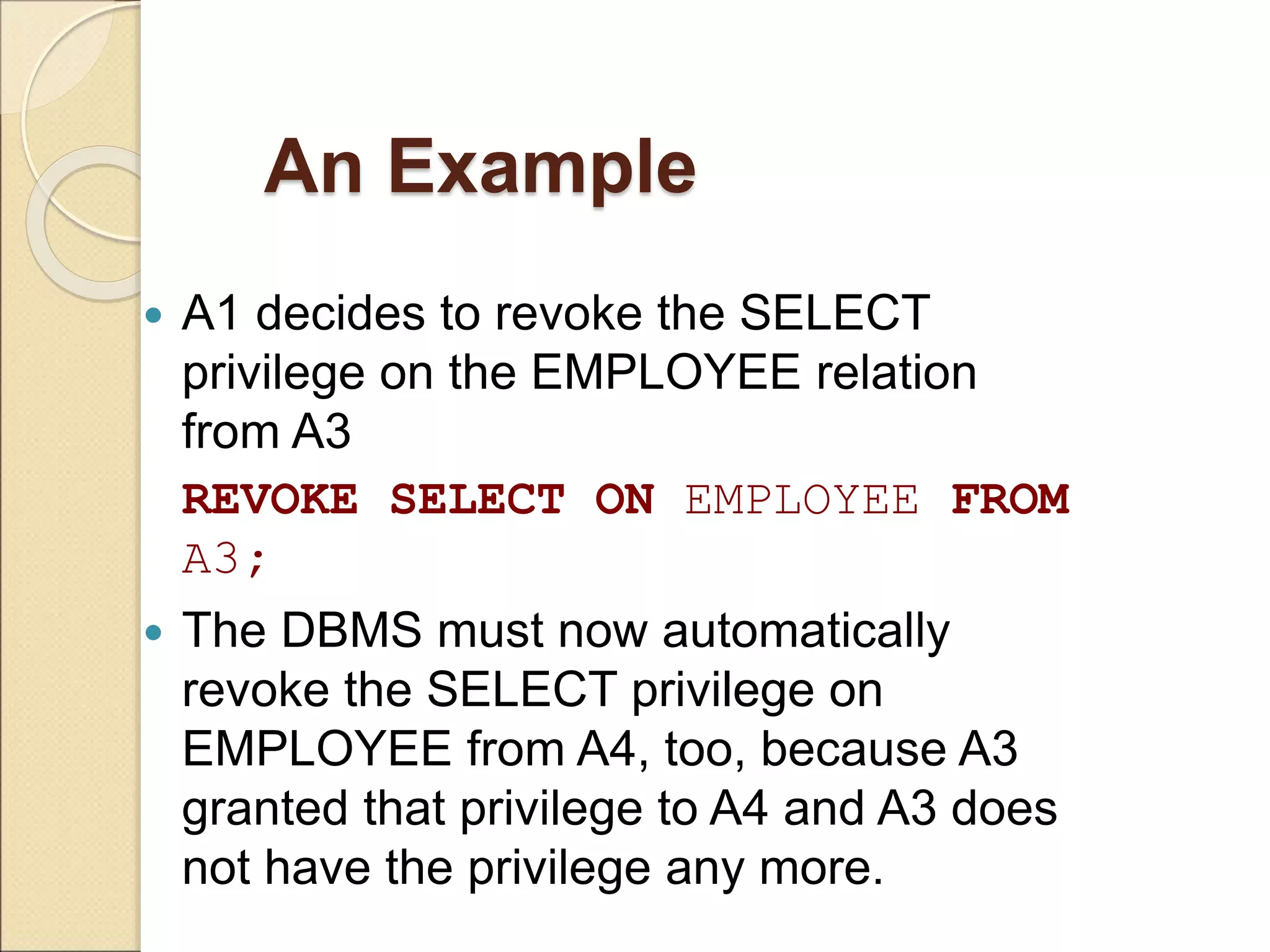
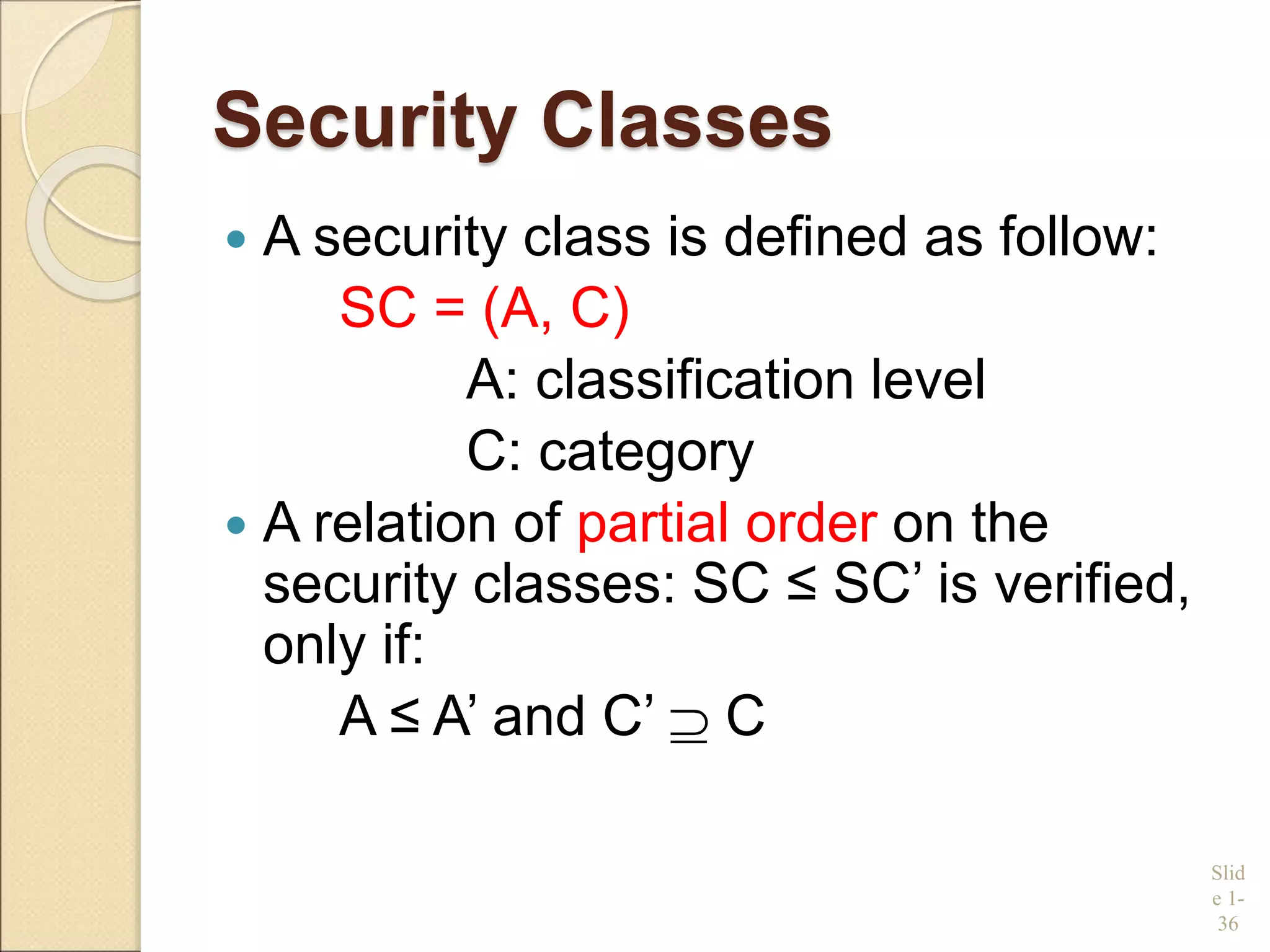
This document discusses database security. It introduces common threats to databases like loss of confidentiality, integrity and availability. The key database security requirements are then outlined as confidentiality, integrity, availability and non-repudiation. Two main types of access control are described - discretionary access control (DAC) using privileges and mandatory access control (MAC) using security classifications. The role of the database administrator to implement access controls is also discussed.