Embed presentation
Download as PDF, PPTX








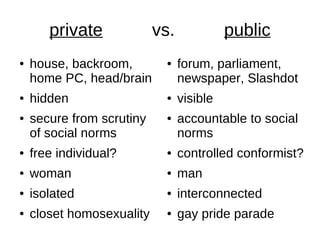












The document discusses optimism towards a future with less privacy. It argues that privacy is doomed as information that is shared online can never be fully removed. However, it posits that in a world with less privacy and more transparency, there are potential benefits like increased freedom, trust, and diversity. Some ideas discussed include identity fluidity, participation in a collective "hive mind", and increasing normality through greater differences between people. Recommended reading on related topics is also provided.




















