NormShield Cyber Risk Rating October 18
•
0 likes•42 views
NormShield Cyber Risk Rating - Infographic 2018 October
Report
Share
Report
Share
Recommended
Recommended
More Related Content
Similar to NormShield Cyber Risk Rating October 18
Similar to NormShield Cyber Risk Rating October 18 (20)
Procurement Risk Management PowerPoint Presentation Slides

Procurement Risk Management PowerPoint Presentation Slides
Risk Management Tools And Techniques PowerPoint Presentation Slides

Risk Management Tools And Techniques PowerPoint Presentation Slides
How AGCO implemented an Supply Chain Risk management solution to save millions

How AGCO implemented an Supply Chain Risk management solution to save millions
Risk Management Module Powerpoint Presentation Slides

Risk Management Module Powerpoint Presentation Slides
Choosing the Right Trading Desk for Your Display Programmatic Buying

Choosing the Right Trading Desk for Your Display Programmatic Buying
Failure Modes FMEA-&-Measurement_Systems_Analysis.ppt

Failure Modes FMEA-&-Measurement_Systems_Analysis.ppt
Risk Management module PowerPoint Presentation Slides

Risk Management module PowerPoint Presentation Slides
More from NormShield
More from NormShield (9)
Are There Any Domains Impersonating Your Company For Phishing?

Are There Any Domains Impersonating Your Company For Phishing?
Review on 3rd-party Cyber Risk Assessment and Scoring Tools

Review on 3rd-party Cyber Risk Assessment and Scoring Tools
Recently uploaded
Recently uploaded (20)
Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...

Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
Axa Assurance Maroc - Insurer Innovation Award 2024

Axa Assurance Maroc - Insurer Innovation Award 2024
Scaling API-first – The story of a global engineering organization

Scaling API-first – The story of a global engineering organization
The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf

The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf
Injustice - Developers Among Us (SciFiDevCon 2024)

Injustice - Developers Among Us (SciFiDevCon 2024)
The Codex of Business Writing Software for Real-World Solutions 2.pptx

The Codex of Business Writing Software for Real-World Solutions 2.pptx
08448380779 Call Girls In Greater Kailash - I Women Seeking Men

08448380779 Call Girls In Greater Kailash - I Women Seeking Men
Tata AIG General Insurance Company - Insurer Innovation Award 2024

Tata AIG General Insurance Company - Insurer Innovation Award 2024
Exploring the Future Potential of AI-Enabled Smartphone Processors

Exploring the Future Potential of AI-Enabled Smartphone Processors
From Event to Action: Accelerate Your Decision Making with Real-Time Automation

From Event to Action: Accelerate Your Decision Making with Real-Time Automation
Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...

Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...
Boost PC performance: How more available memory can improve productivity

Boost PC performance: How more available memory can improve productivity
Breaking the Kubernetes Kill Chain: Host Path Mount

Breaking the Kubernetes Kill Chain: Host Path Mount
NormShield Cyber Risk Rating October 18
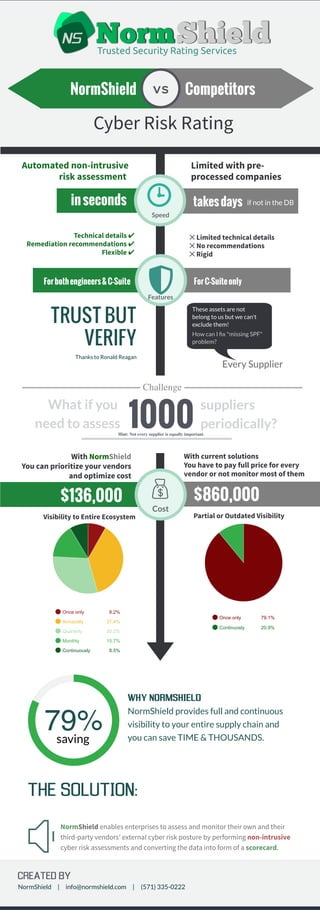
- 1. Cyber Risk Rating CompetitorsNormShield vs Trusted Security Rating Services Automated non-intrusive risk assessment Limited with pre- processed companies ✕ Limited technical details ✕ No recommendations ✕ Rigid Technical details ✔ Remediation recommendations ✔ Flexible ✔ takesdays inseconds ForC-SuiteonlyForbothengineers&C-Suite Features Speed if not in the DB Every Supplier These assets are not belong to us but we can't exclude them! How can I fix "missing SPF" problem? What if you need to assess Challenge 1000Hint: Not every supplier is equally important. suppliers periodically? TRUST BUT VERIFY Thanks to Ronald Reagan Once only 8.2% Annaually 37.4% Quarterly 30.2% Monthly 15.7% Continuously 8.5% Once only 79.1% Continuosly 20.9% With current solutions You have to pay full price for every vendor or not monitor most of them With NormShield You can prioritize your vendors and optimize cost $860,000 Partial or Outdated Visibility $136,000 Visibility to Entire Ecosystem 79% WHY NORMSHIELD NormShield provides full and continuous visibility to your entire supply chain and you can save TIME & THOUSANDS.saving THE SOLUTION: Cost NormShield enables enterprises to assess and monitor their own and their third-party vendors’ external cyber risk posture by performing non-intrusive cyber risk assessments and converting the data into form of a scorecard. CREATED BY NormShield | info@normshield.com | (571) 335-0222
