Digital certificates
•Download as PPTX, PDF•
0 likes•3,222 views
PKI, Digital Certificate
Report
Share
Report
Share
Recommended
Recommended
More Related Content
What's hot
What's hot (20)
Viewers also liked
Viewers also liked (12)
Understanding Digital Certificates & Secure Sockets Layer

Understanding Digital Certificates & Secure Sockets Layer
Similar to Digital certificates
Similar to Digital certificates (20)
computer-security-and-cryptography-a-simple-presentation

computer-security-and-cryptography-a-simple-presentation
Slide Deck – Session 6 – FRSecure CISSP Mentor Program 2017

Slide Deck – Session 6 – FRSecure CISSP Mentor Program 2017
Dr Petar Radanliev, PhD Thesis Department of Computer Sciences, University of...

Dr Petar Radanliev, PhD Thesis Department of Computer Sciences, University of...
Recently uploaded
💉💊+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHABI}}+971581248768
+971581248768 Mtp-Kit (500MG) Prices » Dubai [(+971581248768**)] Abortion Pills For Sale In Dubai, UAE, Mifepristone and Misoprostol Tablets Available In Dubai, UAE CONTACT DR.Maya Whatsapp +971581248768 We Have Abortion Pills / Cytotec Tablets /Mifegest Kit Available in Dubai, Sharjah, Abudhabi, Ajman, Alain, Fujairah, Ras Al Khaimah, Umm Al Quwain, UAE, Buy cytotec in Dubai +971581248768''''Abortion Pills near me DUBAI | ABU DHABI|UAE. Price of Misoprostol, Cytotec” +971581248768' Dr.DEEM ''BUY ABORTION PILLS MIFEGEST KIT, MISOPROTONE, CYTOTEC PILLS IN DUBAI, ABU DHABI,UAE'' Contact me now via What's App…… abortion Pills Cytotec also available Oman Qatar Doha Saudi Arabia Bahrain Above all, Cytotec Abortion Pills are Available In Dubai / UAE, you will be very happy to do abortion in Dubai we are providing cytotec 200mg abortion pill in Dubai, UAE. Medication abortion offers an alternative to Surgical Abortion for women in the early weeks of pregnancy. We only offer abortion pills from 1 week-6 Months. We then advise you to use surgery if its beyond 6 months. Our Abu Dhabi, Ajman, Al Ain, Dubai, Fujairah, Ras Al Khaimah (RAK), Sharjah, Umm Al Quwain (UAQ) United Arab Emirates Abortion Clinic provides the safest and most advanced techniques for providing non-surgical, medical and surgical abortion methods for early through late second trimester, including the Abortion By Pill Procedure (RU 486, Mifeprex, Mifepristone, early options French Abortion Pill), Tamoxifen, Methotrexate and Cytotec (Misoprostol). The Abu Dhabi, United Arab Emirates Abortion Clinic performs Same Day Abortion Procedure using medications that are taken on the first day of the office visit and will cause the abortion to occur generally within 4 to 6 hours (as early as 30 minutes) for patients who are 3 to 12 weeks pregnant. When Mifepristone and Misoprostol are used, 50% of patients complete in 4 to 6 hours; 75% to 80% in 12 hours; and 90% in 24 hours. We use a regimen that allows for completion without the need for surgery 99% of the time. All advanced second trimester and late term pregnancies at our Tampa clinic (17 to 24 weeks or greater) can be completed within 24 hours or less 99% of the time without the need surgery. The procedure is completed with minimal to no complications. Our Women's Health Center located in Abu Dhabi, United Arab Emirates, uses the latest medications for medical abortions (RU-486, Mifeprex, Mifegyne, Mifepristone, early options French abortion pill), Methotrexate and Cytotec (Misoprostol). The safety standards of our Abu Dhabi, United Arab Emirates Abortion Doctors remain unparalleled. They consistently maintain the lowest complication rates throughout the nation. Our Physicians and staff are always available to answer questions and care for women in one of the most difficult times in their lives. The decision to have an abortion at the Abortion Cl+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...?#DUbAI#??##{{(☎️+971_581248768%)**%*]'#abortion pills for sale in dubai@
A Principled Technologies deployment guide
Conclusion
Deploying VMware Cloud Foundation 5.1 on next gen Dell PowerEdge servers brings together critical virtualization capabilities and high-performing hardware infrastructure. Relying on our hands-on experience, this deployment guide offers a comprehensive roadmap that can guide your organization through the seamless integration of advanced VMware cloud solutions with the performance and reliability of Dell PowerEdge servers. In addition to the deployment efficiency, the Cloud Foundation 5.1 and PowerEdge solution delivered strong performance while running a MySQL database workload. By leveraging VMware Cloud Foundation 5.1 and PowerEdge servers, you could help your organization embrace cloud computing with confidence, potentially unlocking a new level of agility, scalability, and efficiency in your data center operations.Deploy with confidence: VMware Cloud Foundation 5.1 on next gen Dell PowerEdg...

Deploy with confidence: VMware Cloud Foundation 5.1 on next gen Dell PowerEdg...Principled Technologies
Recently uploaded (20)
Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe

Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe
Repurposing LNG terminals for Hydrogen Ammonia: Feasibility and Cost Saving

Repurposing LNG terminals for Hydrogen Ammonia: Feasibility and Cost Saving
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...
Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...

Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...
Top 5 Benefits OF Using Muvi Live Paywall For Live Streams

Top 5 Benefits OF Using Muvi Live Paywall For Live Streams
Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024

Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024
Strategies for Landing an Oracle DBA Job as a Fresher

Strategies for Landing an Oracle DBA Job as a Fresher
TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments

TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments
Exploring the Future Potential of AI-Enabled Smartphone Processors

Exploring the Future Potential of AI-Enabled Smartphone Processors
Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...

Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...
Top 10 Most Downloaded Games on Play Store in 2024

Top 10 Most Downloaded Games on Play Store in 2024
Deploy with confidence: VMware Cloud Foundation 5.1 on next gen Dell PowerEdg...

Deploy with confidence: VMware Cloud Foundation 5.1 on next gen Dell PowerEdg...
Apidays New York 2024 - The Good, the Bad and the Governed by David O'Neill, ...

Apidays New York 2024 - The Good, the Bad and the Governed by David O'Neill, ...
Tata AIG General Insurance Company - Insurer Innovation Award 2024

Tata AIG General Insurance Company - Insurer Innovation Award 2024
From Event to Action: Accelerate Your Decision Making with Real-Time Automation

From Event to Action: Accelerate Your Decision Making with Real-Time Automation
Automating Google Workspace (GWS) & more with Apps Script

Automating Google Workspace (GWS) & more with Apps Script
Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...

Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...
Digital certificates
- 2. Cryptography History • Cryptography is the art of encrypting and decrypting information • The earliest known use of cryptography was the Egyptians in 1900BC • Julius Ceaser use a simple substituion cipher to secure his communications • Thomas Jefferson, in 1790, invented a cipher wheel that the US Navy used in WWII • In the late 20s and early 30s, the FBI established an office to combat the increasing use of cryptography by criminals (rum runners) • Dr. Hosrt Feistel invented the precusor to DES while at IBM • In 1976, the Federal Govt introduced DES based on using Feistel ciphers • In 1977, Scientific American magazine introduced us to Rivest, Shamir and • Aldeman or RSA encryption. They offered it for free with a self addressed • envelope and the NSA promptly freaked out • 1990 brought us the 128 bit cipher called “IDEA” • X.500 was the orginal protocol in 1988 • X.509 V3 was released in 1996 2
- 3. (X.509 digital certificates)what for ● 802.1x port authentication ● Digital Signatures ● File Encryption ● Web Authorization (SSL) ● IP Security (end-point to end-point) ● Secure Email ● VPNs 3
- 4. Digital Certificate Electronic Certificate it contains information about an individual or entity. It Is issued from a trusted 3rd party. Contains information that can prove its authenticity. Has an expiration date.It Is presented to someone (or some thing) for validation. (Ex. driver’s license or passport) 4
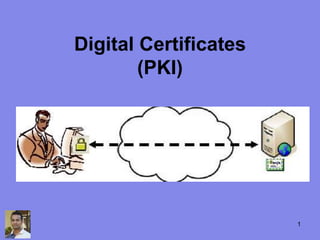
- 5. Introduction to Public Key Infrastructure (PKI) PKI is a security architecture that has been introduced to provide an increased level of confidence for exchanging information over an increasingly insecure Internet. Public |<>| Private 5
- 6. The Public Key used for Encryption Another person uses your public encryption key when they want to send you confidential information. The information to be sent is encrypted using your public key*. You can provide your public key to the sender, or it can be retrieved from the directory in which it is published. 6
- 7. The Private Key used for Decryption A private key is used to decrypt information that has been encrypted using its corresponding public key. The person using the private key can be certain that the information it is able to decrypt must have been intended for them, but they cannot be certain who the information is from. 7
- 8. Plain text Encrypt with B’s public key Plain text Decrypt with B’s private key Sender (A) Netwo rk Receiver (B) Cipher text Cipher text 8
- 9. Customer A Customer B Customer C Bank’s public key Bank’s public key Bank’s public key Bank’s private key Bank 9
- 10. C1(S1) C4(S4) C2(S2) C3(S3) S1 S2 S3 S4 Certificate Servers Certificate Generator 10
- 11. Certification Authority (CA) It Is a combination of hardware and software which is responsible for creating digital certificates It can issue certificates to individuals, organizations, network devices, servers, or other CAs 11
- 12. Support for Windows / Linux • Outlook • Lotus Notes • Netscape / Mozilla • Thunderbird 12
- 13. PKI (Public Key Infrastructure) -Infrastructure using pairs of public and private keys to ensure privacy and security of data. Private Key -One half of the PKI key pair and which is never given out to anyone. This key can be protected by a password. Public Key -The second half of the PKI key pair that can be given out to the public or placed on a key server. CA (Certificate Authority) (Ex. DNS) -A trusted authority that signs your certificates and validates the certificate. Terminology 13
- 14. Self Signed Certificate – A digital certificate that you signed and validated using a private CA and is not trusted by default in the real world. SSL (Secure Socket Layer) – A protocol developed by Netscape to provide a secure method of exchanging data using a browser over a public network such as the internet. Hash -Hashing is taking a file and applying a hashing algorithm to it and generating a mathematical checksum. RSA (Rivest, Shamir and Aldeman) – A public key cipher that can be used to encrypt and to digitally sign. DSA (Digital Signing Algorithm) – Like RSA, it is a public key cipher but it can only be used to digitally sign. PKCS#12 (Personal Information Exchange Syntax) – A portable container file format that can be used to transfer certificates and private keys. Terminology 14
- 15. algorithm MD5 – Message Digest 5. Hash algorithm that was released in 1991. SHA1 – Secure Hash Algorithm version 1 ciper was released in 1995. There are improved versions of SHA collectively called “SHA2” 15
