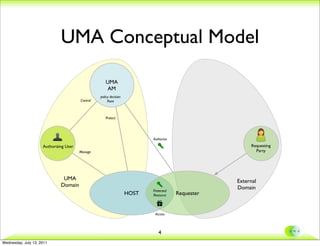
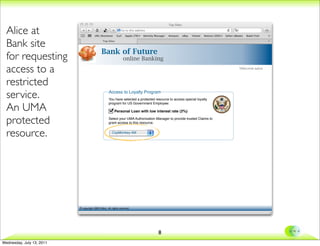
This document discusses extending the UMA protocol to support trusted claims (tClaims). It begins with an overview of the UMA conceptual model and requirements for trusted claims. It then discusses how OpenID Connect can be used to provide authentication, authorization, and attribute transmission. The document proposes an integration approach where the UMA authorization manager interacts with an OpenID Connect identity provider and claims provider. It provides examples of user interactions and considers the trust model implications.