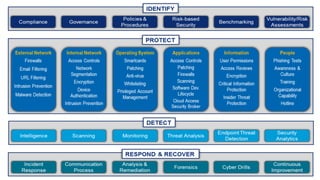
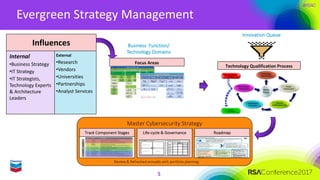
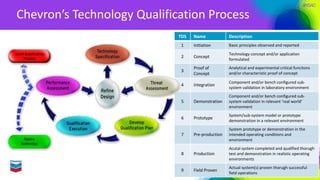
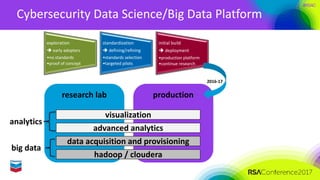
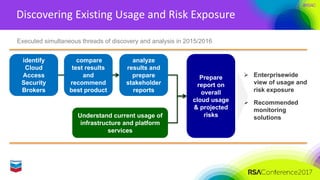
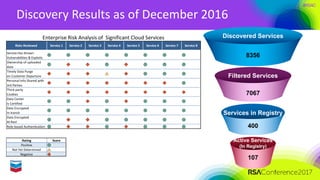
The document outlines Chevron's approach to delivering emerging cybersecurity technologies, with a focus on innovation and strategic research in data science and analytics. It describes the company's technology qualification process and the challenges faced in integrating cloud security while managing risks associated with cloud services. Additionally, it highlights the importance of collaboration, engagement with skeptics, and lessons learned for fostering innovation within organizations.