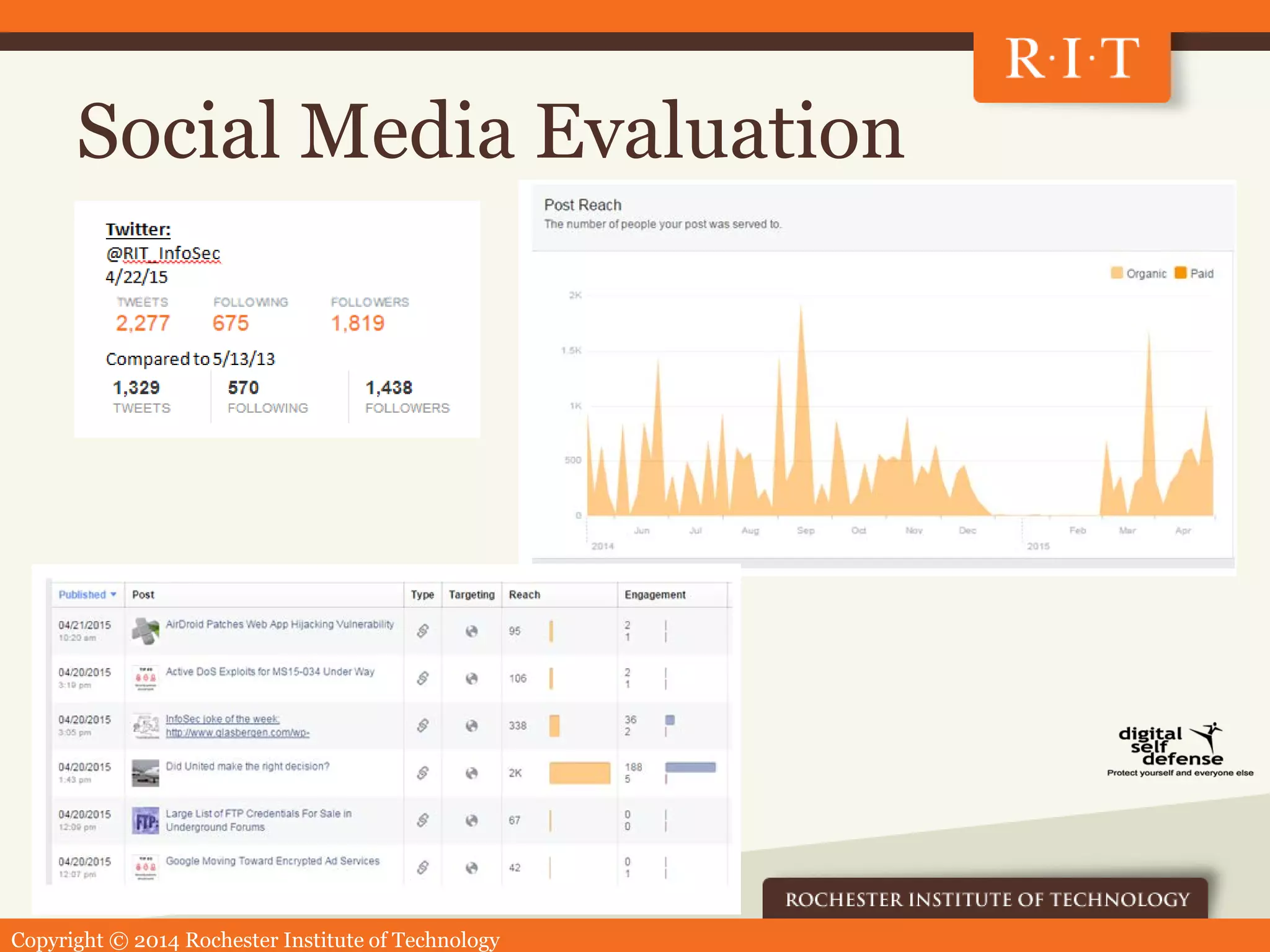
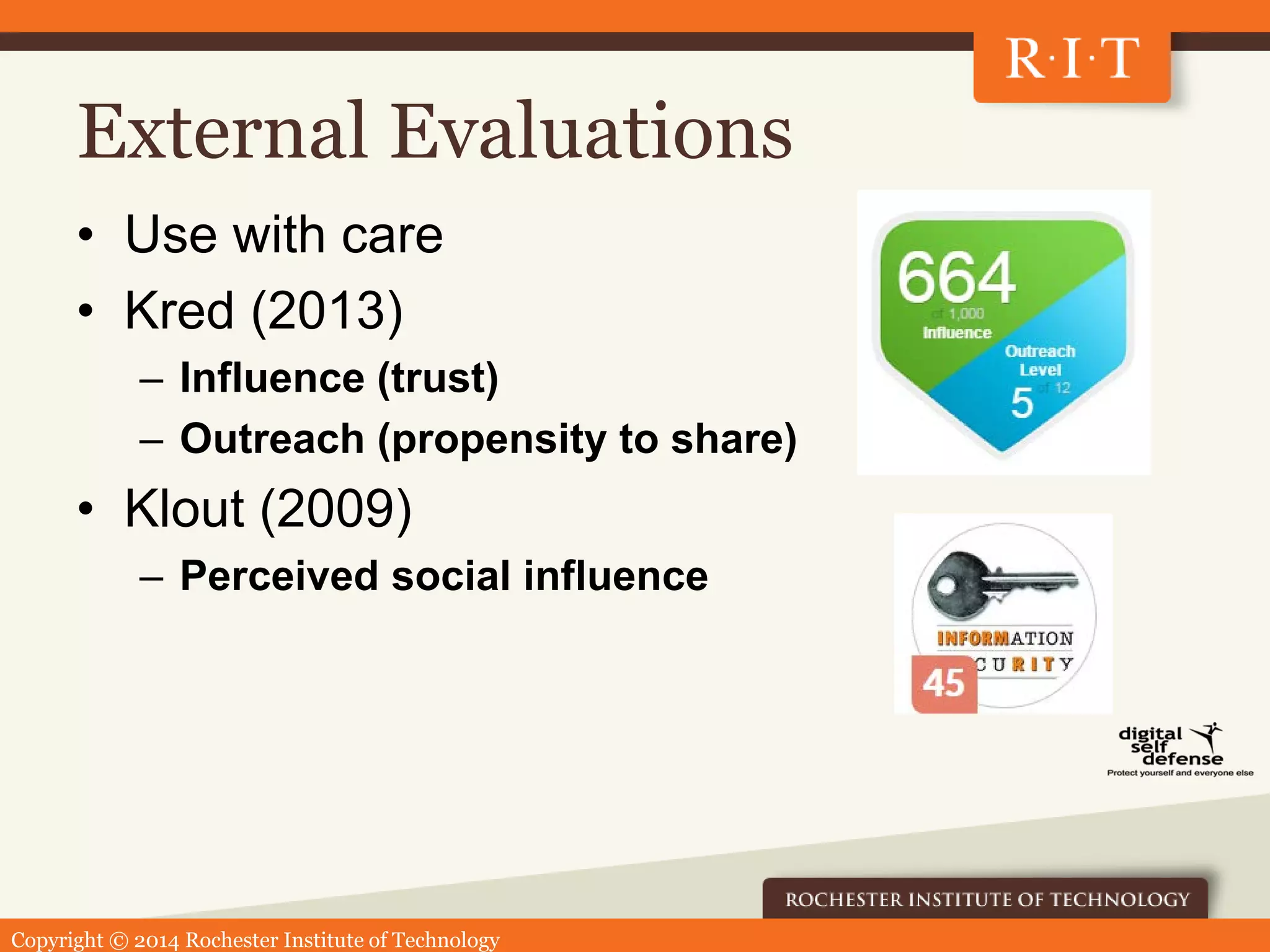
The document outlines a presentation by Ben Woelk regarding a communications strategy for cybersecurity awareness at the Rochester Institute of Technology. It discusses the implementation of a systematic approach to educate and inform the community about information security threats while addressing challenges like messaging overload. Key components include audience analysis, multi-channel communications, and an evaluation plan to measure success and make adjustments.