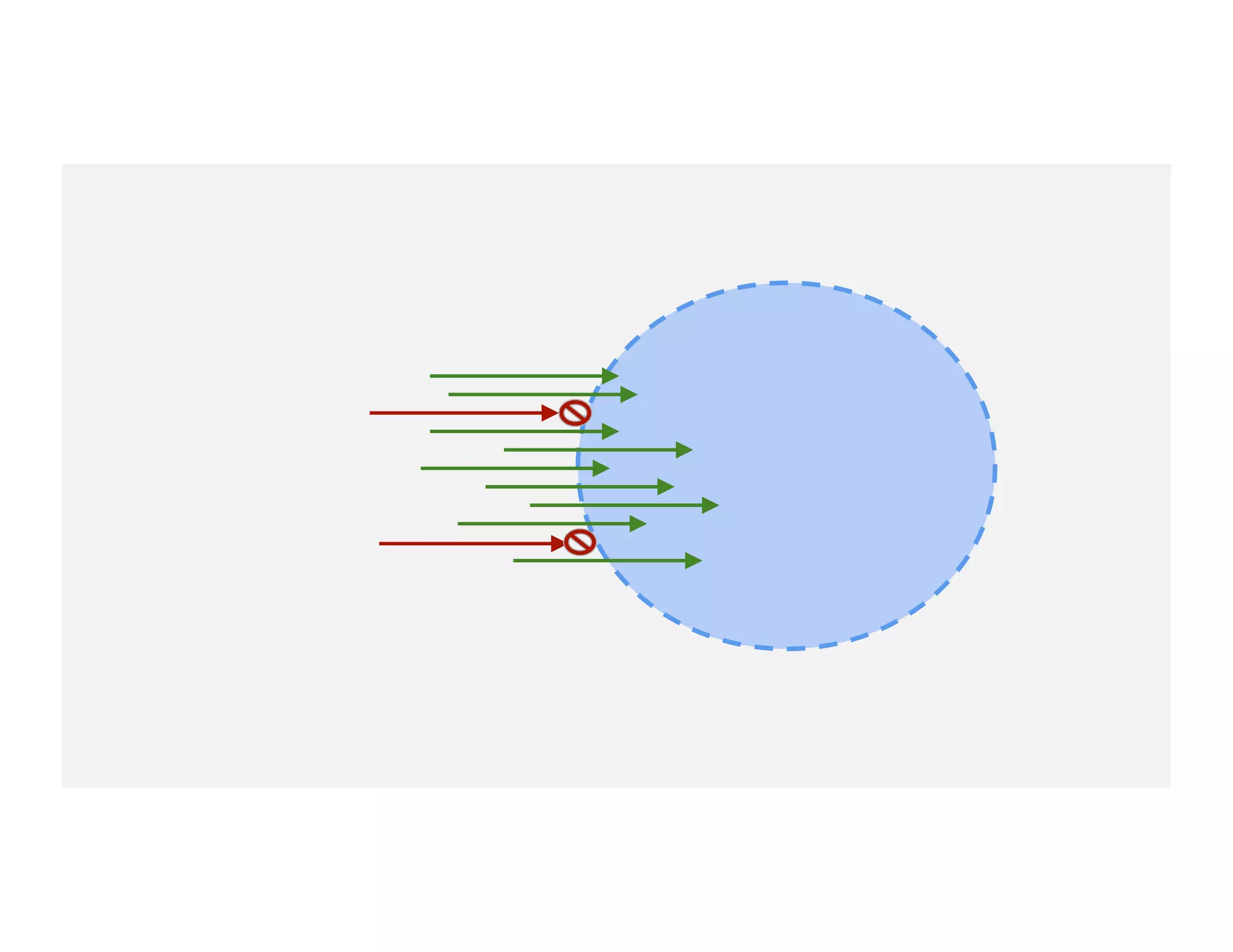
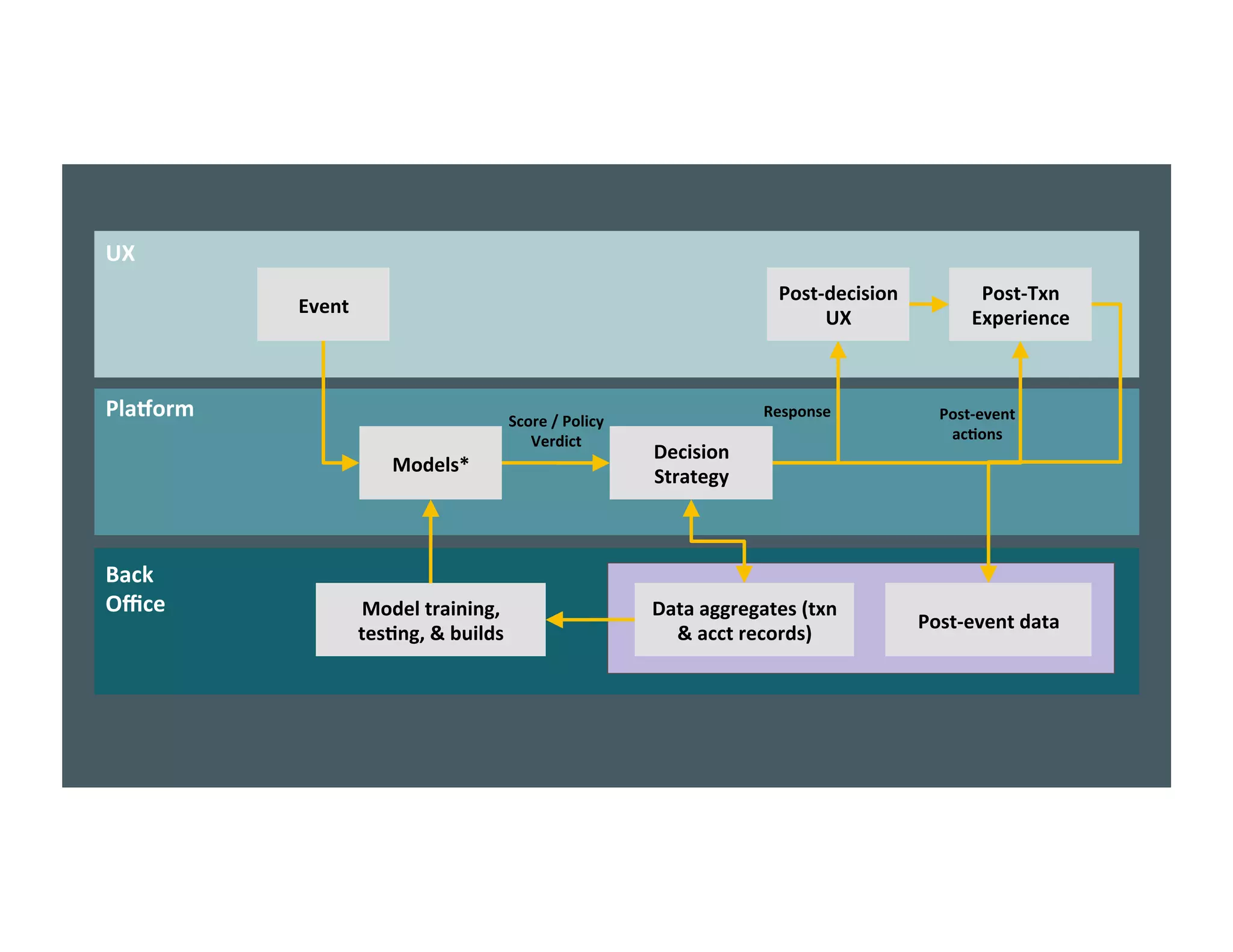
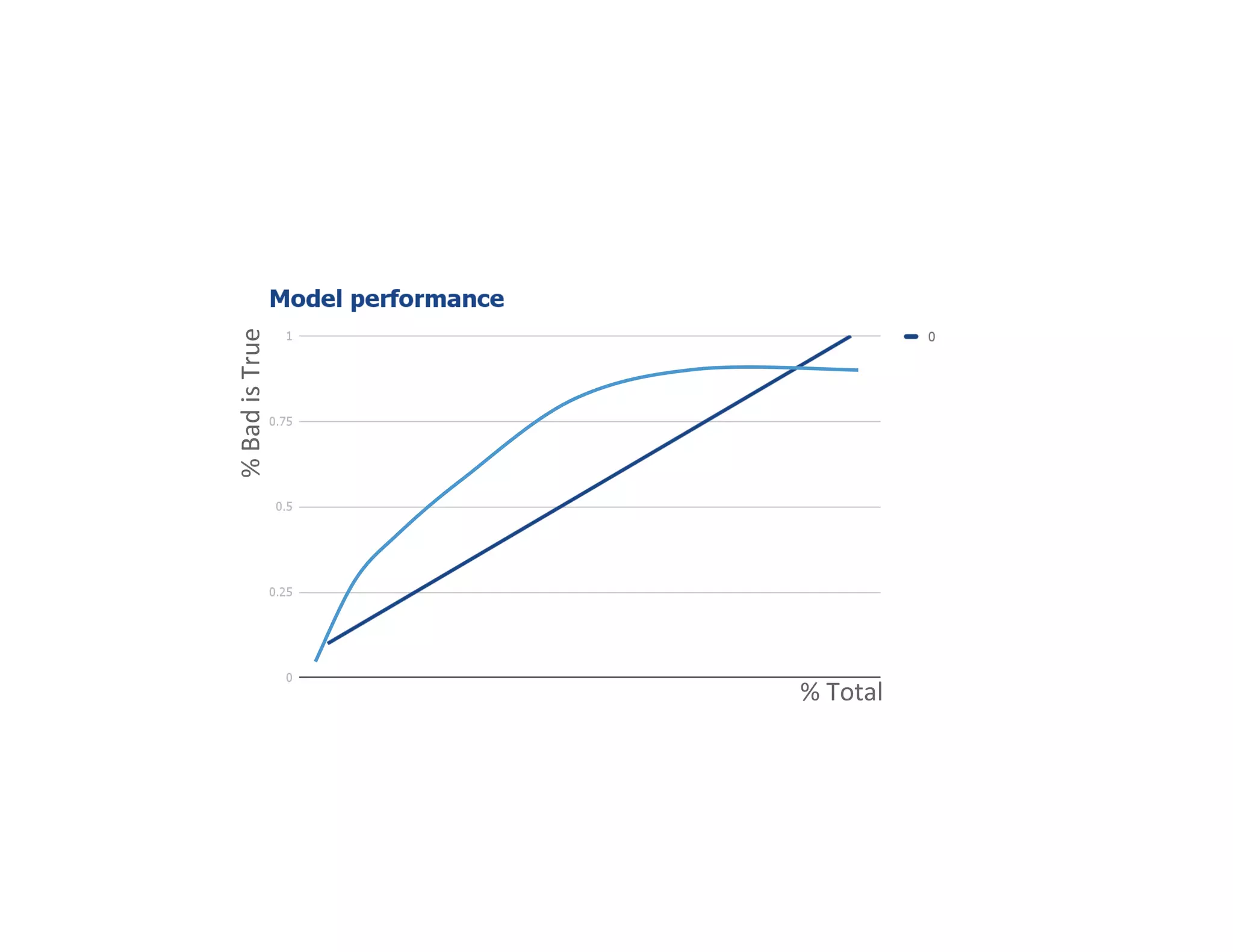
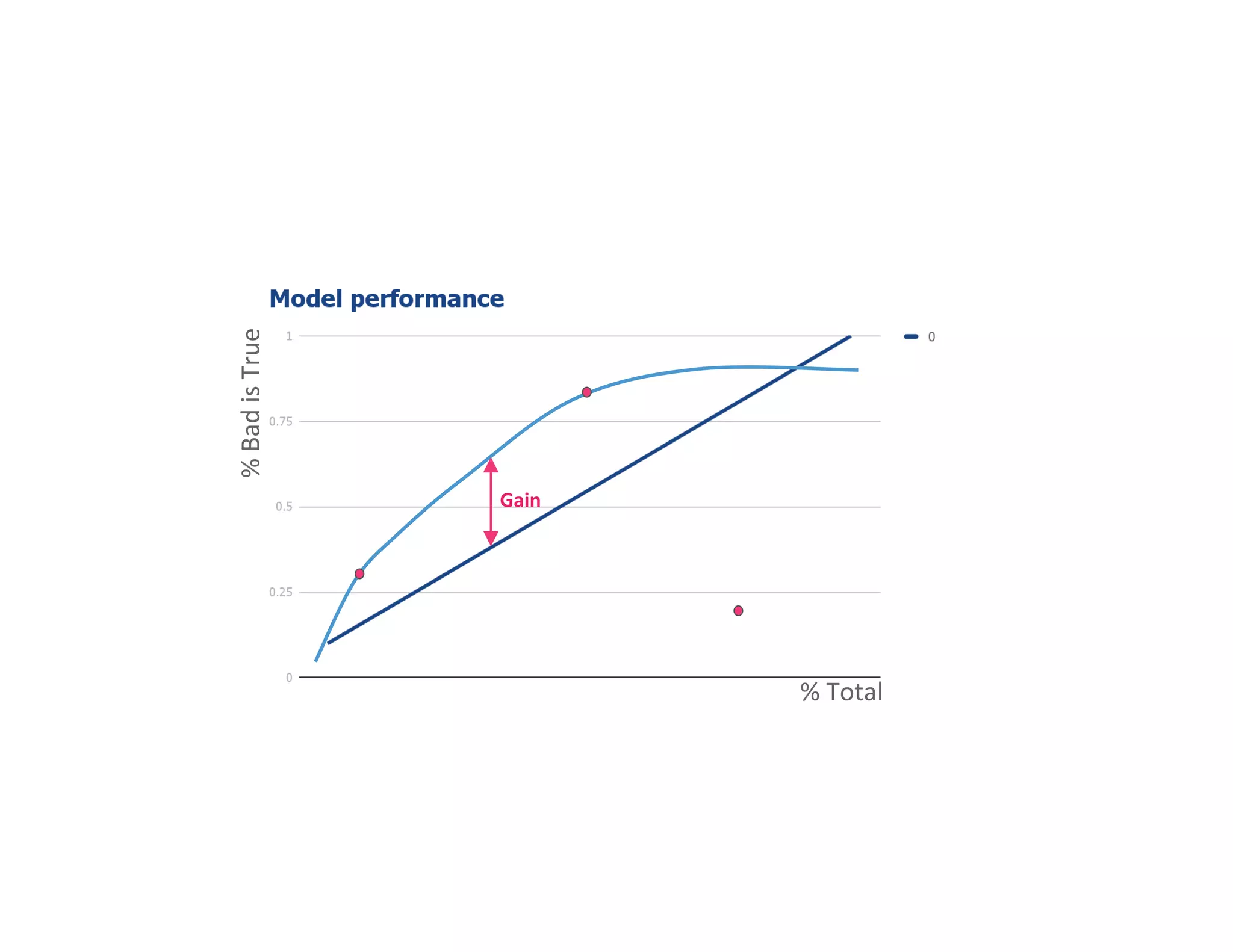
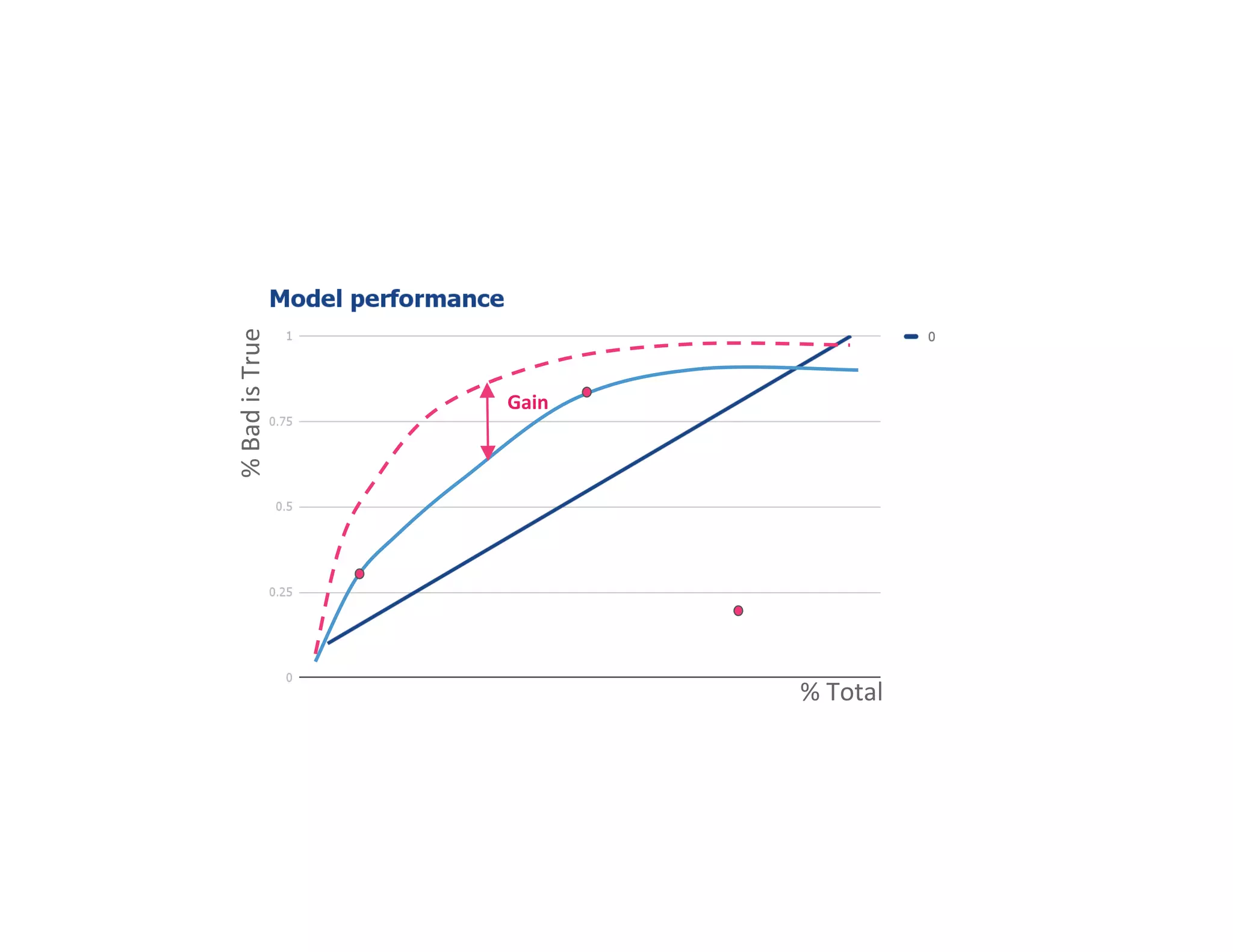
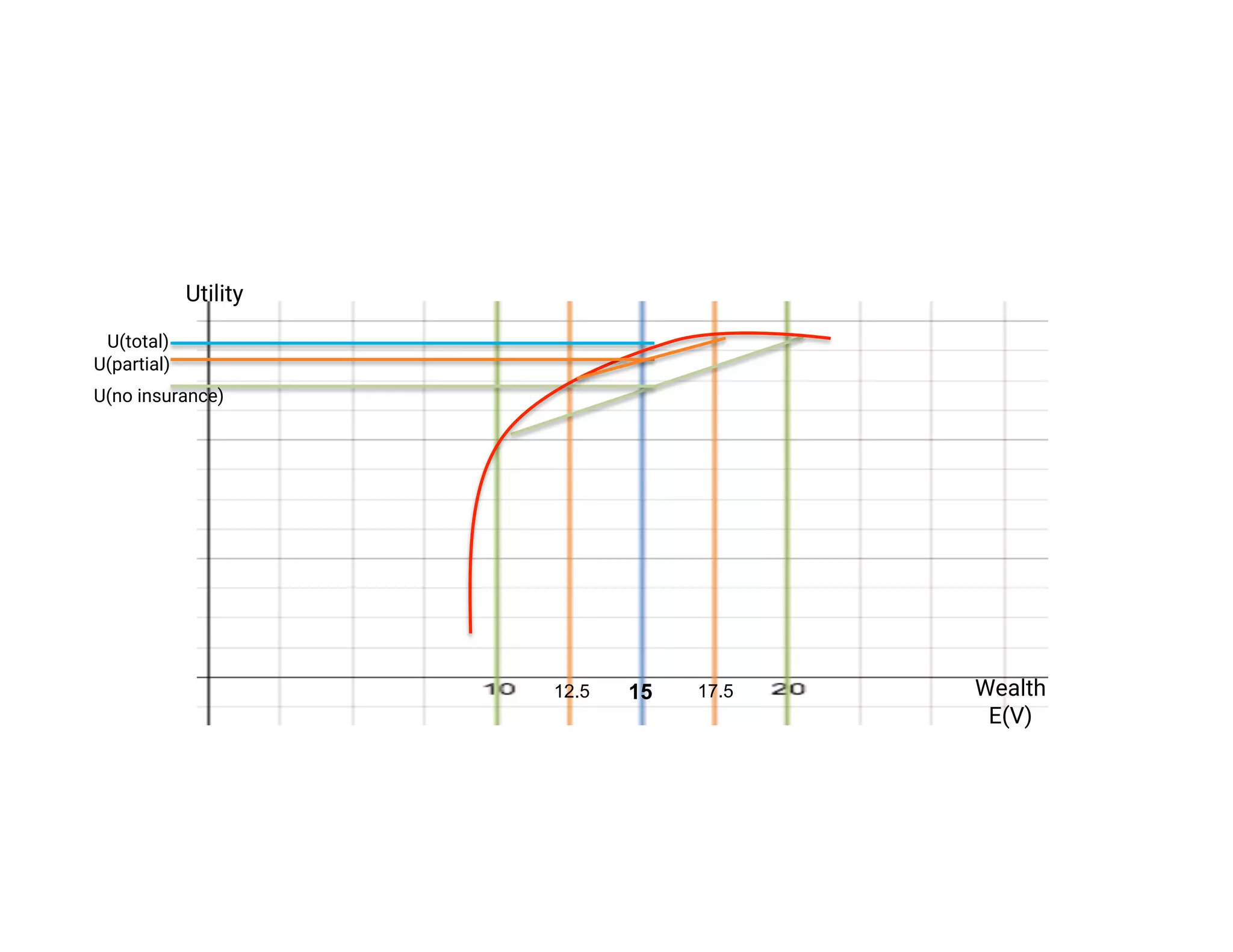
The document discusses the intersection of big data, behavioral economics, and security through the lens of decision-making, risk management, and game theory. It emphasizes the importance of modeling and feedback in understanding decisions and post-event actions while addressing the challenges posed by adversaries and bad actors. Additionally, it offers a framework for evaluating security investments and trade-offs while highlighting the complexity of human behavior in uncertain environments.










































![.
Some references (mostly about behavior)
• Improving SSL Warnings: Comprehension and Adherence. A. Felt, A. Ainslie, R. Reeder, S.
Consolvo, S. Thyagaraja, A. Bettes, H. Harris, and J. Grimes. CHI, page 2893-2902. ACM,
(2015) https://static.googleusercontent.com/media/research.google.com/en//pubs/archive/43265.pdf
• D. Akhawe and A. P. Felt. Alice in warningland: A large-scale field study of browser security warning
effectiveness. In Proc. of USENIX Security, pages 257–272, 2013.
• Ariely, Dan. Predictably Irrational: The Hidden Forces That Shape Our Decisions. New York, NY:
HarperCollins, 2008.
• Arthur, W Brian. All Systems will be Gamed: Exploitive Behavior in Economic and Social
Systems. Santa Fe Institute: SFI WORKING PAPER: 2014-06-
016. http://tuvalu.santafe.edu/~wbarthur/Papers/All%20Systems%20Gamed.pdf To appear in
Complexity and the Economy, W. B Arthur, Oxford University Press, 2014
• Kahneman, Daniel. Thinking, Fast and Slow. New York: Farrar, Straus and Giroux, 2011.
• Leyton-Brown, Kevin, and Yoav Shoham. Essentials of Game Theory: A Concise, Multidisciplinary
Introduction. [San Rafael, Calif.]: Morgan & Claypool, 2008.
• Meadows, Donella. Thinking in Systems: A Primer. London: Chelsea Green Publishing, 2008.](https://image.slidesharecdn.com/2017-170802214946/75/Something-Wicked-55-2048.jpg)

