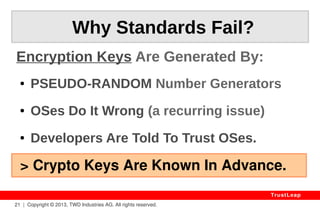
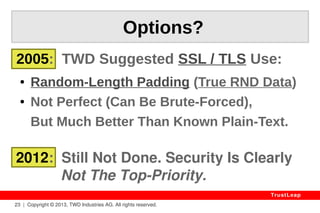
The document outlines TrustLeap's cryptographic technology designed to provide mathematically-proven, unbreakable security for digital assets against potential breaches, including threats from quantum computers. It highlights the failures of existing encryption standards and asserts that TrustLeap's approach can eliminate key leaks, offering substantial advantages in protecting sensitive information. Additionally, it discusses the importance of proven security measures across various applications, including corporate and public asset protection, while emphasizing ease of use and low overhead.




![Promotion
“no one ever lost money to an
attack on a properly designed
[standard] cryptosystem”
– Peter Gutmann
5 | Copyright © 2013, TWD Industries AG. All rights reserved.
TrustLeap](https://image.slidesharecdn.com/trustleap-130525030358-phpapp02/85/Trustleap-Mathematically-Proven-Unbreakable-Security-5-320.jpg)