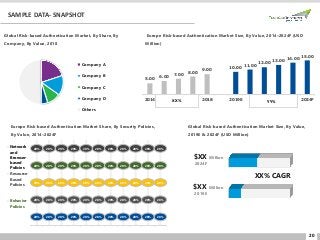
Global risk-based authentication market stood at $ 2.3 bn & is projected to grow at a CAGR of more than 18.8% by 2024 due to increasing adoption of risk-based authentication solutions in various industries. Read: https://www.techsciresearch.com/report/risk-based-authentication-market/3919.html