Every Workplace Needs to Reduce Risk of Data Breaches – Including Government Institutions
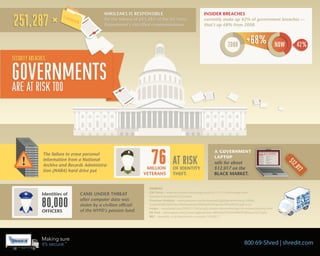
- 1. 251,287 ³ WIKILEAKS IS RESPONSIBLE INSIDER BREACHES for the release of 251,287 of the US State currently make up 42% of government breaches — Department’s classified communications. that’s up 68% from 2008. 2008 +68% NOW 42% SECURITY BREACHES GOVERNMENTS ARE AT RISK TOO 76 A GOVERNMENT The failure to erase personal information from a National AT RISK LAPTOP sells for about $12 Archive and Records Administra- MILLION OF IDENTITY $12,017 on the ,01 tion (NARA) hard drive put 7 VETERANS THEFT. BLACK MARKET. SOURCES CBC News – www.cbc.ca/news/technology/story/2011/11/15/technology-data- Identities of CAME UNDER THREAT 80,000 breaches-it-security.html (Canada) after computer data was Ponemon Institute – www.ponemon.org/local/upload/fckjail/generalcontent/18/file/ stolen by a civilian official Cost%20of%20a%20Lost%20Laptop%20White%20Paper%20Final%203.pdf (U.S.) Forbes – www.forbes.com/2009/11/24/security-hackers-data-technology-cio-network-breaches.html OFFICERS of the NYPD’s pension fund. NY Post – www.nypost.com/p/news/regional/item_8BX3Qmj7PnfxPOdMPZTr8K#ixzz1jFv7eqYy BBC – www.bbc.co.uk/news/world-us-canada-14765837 800 69-Shred | shredit.com
