Paper nctsn
•
0 likes•59 views
The document discusses an open redirect vulnerability found on the website nctsnet.org. An open redirect occurs when a website redirects a user's browser to a different URL, allowing an attacker to perform phishing attacks or distribute malware. The vulnerability on nctsnet.org was found in the pubdlcnt.php script, which did not validate or verify the redirect URL. An attacker could exploit this by crafting a malicious URL with the vulnerability and tricking users into clicking on the link. Open redirects abuse a site's trust and can be used to steal user information or credentials from a trusted domain.
Report
Share
Report
Share
Download to read offline
Recommended
NTXISSACSC3 - How I hacked the Government and Got Away with It by Seven Hatfield

NTXISSACSC3 - How I hacked the Government and Got Away with It by Seven HatfieldNorth Texas Chapter of the ISSA
More Related Content
What's hot
NTXISSACSC3 - How I hacked the Government and Got Away with It by Seven Hatfield

NTXISSACSC3 - How I hacked the Government and Got Away with It by Seven HatfieldNorth Texas Chapter of the ISSA
What's hot (11)
NTXISSACSC3 - How I hacked the Government and Got Away with It by Seven Hatfield

NTXISSACSC3 - How I hacked the Government and Got Away with It by Seven Hatfield
Sucuri Webinar: Simple Steps To Secure Your Online Store

Sucuri Webinar: Simple Steps To Secure Your Online Store
Webinar: CWAF for Mid Market/Enterprise Organizations

Webinar: CWAF for Mid Market/Enterprise Organizations
CROSS-SITE REQUEST FORGERY - IN-DEPTH ANALYSIS 2011

CROSS-SITE REQUEST FORGERY - IN-DEPTH ANALYSIS 2011
AtlasCamp 2010: Securing your Plugin - Penny Wyatt

AtlasCamp 2010: Securing your Plugin - Penny Wyatt
CSRF Attack and Its Prevention technique in ASP.NET MVC

CSRF Attack and Its Prevention technique in ASP.NET MVC
Similar to Paper nctsn
Similar to Paper nctsn (20)
State of the Art Analysis Approach for Identification of the Malignant URLs

State of the Art Analysis Approach for Identification of the Malignant URLs
Web Application Penetration Tests - Vulnerability Identification and Details ...

Web Application Penetration Tests - Vulnerability Identification and Details ...
A8 cross site request forgery (csrf) it 6873 presentation

A8 cross site request forgery (csrf) it 6873 presentation
OWASP Top 10 and Securing Rails - Sean Todd - PayNearMe.com

OWASP Top 10 and Securing Rails - Sean Todd - PayNearMe.com
Secure Form Processing and Protection - Devspace 2015 

Secure Form Processing and Protection - Devspace 2015
Recently uploaded
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...Enterprise Knowledge
Recently uploaded (20)
Axa Assurance Maroc - Insurer Innovation Award 2024

Axa Assurance Maroc - Insurer Innovation Award 2024
From Event to Action: Accelerate Your Decision Making with Real-Time Automation

From Event to Action: Accelerate Your Decision Making with Real-Time Automation
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
Neo4j - How KGs are shaping the future of Generative AI at AWS Summit London ...

Neo4j - How KGs are shaping the future of Generative AI at AWS Summit London ...
Exploring the Future Potential of AI-Enabled Smartphone Processors

Exploring the Future Potential of AI-Enabled Smartphone Processors
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...
Handwritten Text Recognition for manuscripts and early printed texts

Handwritten Text Recognition for manuscripts and early printed texts
Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...

Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...
Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...

Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...
Injustice - Developers Among Us (SciFiDevCon 2024)

Injustice - Developers Among Us (SciFiDevCon 2024)
08448380779 Call Girls In Civil Lines Women Seeking Men

08448380779 Call Girls In Civil Lines Women Seeking Men
Scaling API-first – The story of a global engineering organization

Scaling API-first – The story of a global engineering organization
Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...

Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...
Paper nctsn
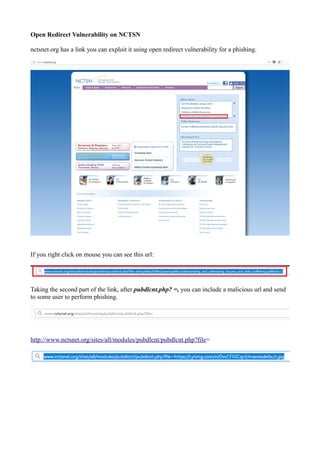
- 1. Open Redirect Vulnerability on NCTSN nctsnet.org has a link you can exploit it using open redirect vulnerability for a phishing. If you right click on mouse you can see this url: Taking the second part of the link, after pubdlcnt.php? =, you can include a malicious url and send to some user to perform phishing. http://www.nctsnet.org/sites/all/modules/pubdlcnt/pubdlcnt.php?file=
- 2. Analyzing the source code, we can observe that there is no validation or verification of the link to where the user will be redirected. But what are Open Redirect Vulnerabilities? An open redirect vulnerability occurs when a victim visits a particular URL for a given website and that website instructs the victim’s browser to visit a completely different URL, on a separate domain. When you visit the URL, the main page would receive a GET HTTP request and use the variable to parameter's value to determine where the visitor's browser should be redirected. After doing só, another page would return a 302 HTTP response, instructing the user's broswer to make a GET request to another page, the variable parameter's value. The Open Web Application Security Project (OWASP), which is a community dedicated to application security that curates a list of the most critical security flaws in web applications, has listed this vulnerability in ther 2014 Top Ten vulnerabilities list. Open redirects exploit the trust of a given domain, www.nctsnet.org, to lure victims to a malicious website. This can be used in phishing attack to trick users into believing theu are submitting information to the trusted site, when their valuable information is actually going to a malicious site. This also enables attackers to distribute malware from the malicious site or steal Oauth tokens.
- 3. Not all vulnerabilities are complex. This open redirect simply required changing the domain_name parameter to an external site, which would have resulted in a user being redirected off-site from NCTSNET. This type of vulnerability relies on an abuse of trust, where victims are tricked into visiting an attacker's site thinking they will be visiting a site they recognize. When you spot likely vulnerable parameters, be sure to test them out thoroughly and add special characters, like a period, if some part of the URL is hard-coded.