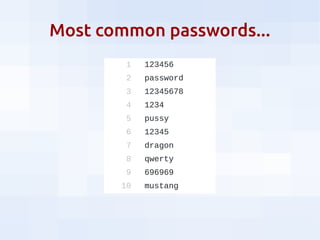
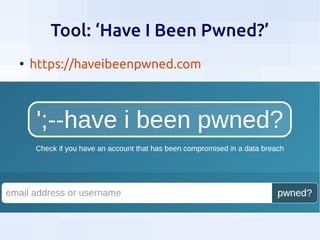
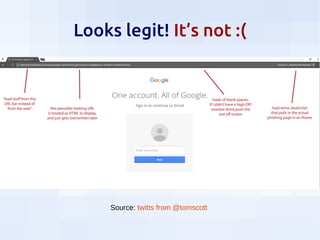
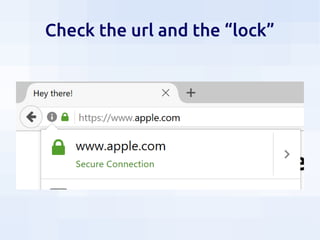
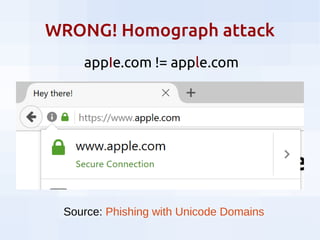
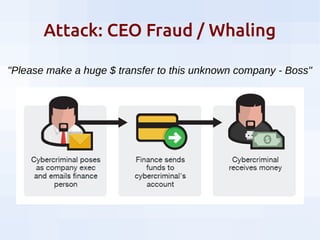
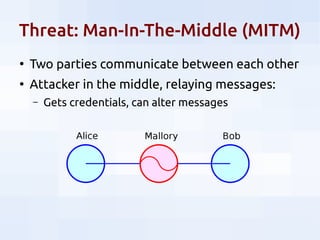
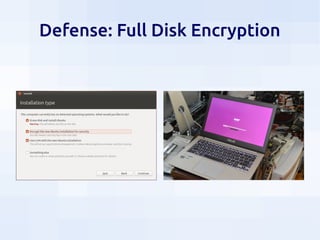
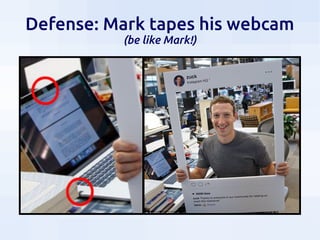
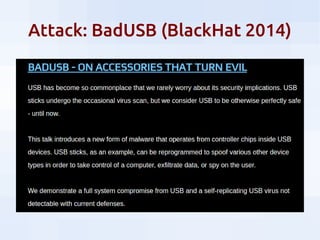
This document summarizes security threats and defenses for data scientists. It discusses common attacks like brute forcing passwords, phishing, and spear phishing. It also covers threats from password reuse due to data breaches, man-in-the-middle attacks, internet tracking, physical access to hardware, and USB devices. Defenses include using strong unique passwords, two-factor authentication, encryption, blocking tracking, and avoiding unknown USB devices. The document recommends resources for further learning about data security.