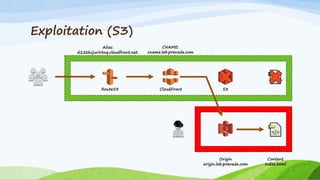
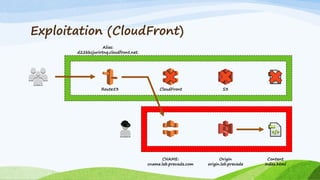
The document discusses 'cloud jacking', focusing on exploiting AWS services like Route 53, CloudFront, and S3 through subdomain hijacking techniques. It provides examples and explanations on how attackers can manipulate DNS records to gain control over e-commerce sites and content delivery networks. The presentation also highlights the associated risks, potential exploitation methods, and necessary mitigations for securing these AWS services.