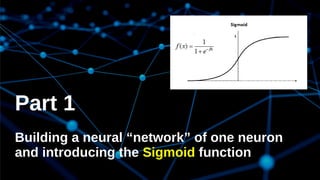
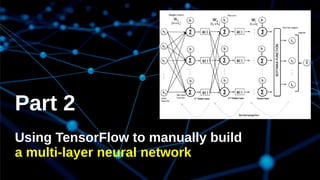
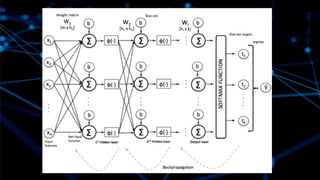
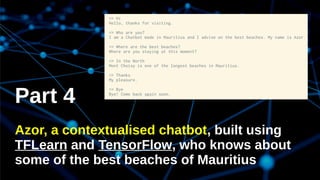
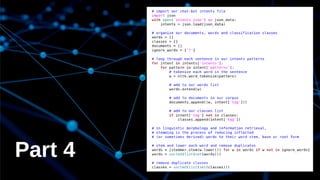
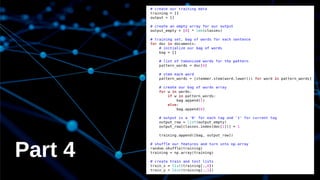
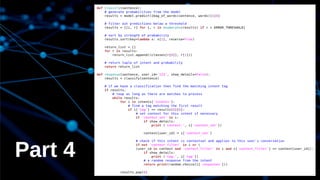
The document discusses deep learning and its application in building a chatbot using frameworks like TensorFlow and TFLearn. It provides a step-by-step guide on creating a neural network and highlights the development of a contextual chatbot named Azor, which showcases recommendations for local beaches in Mauritius. The speaker, Avinash Meetoo, is a senior adviser in the field of technology and innovation.