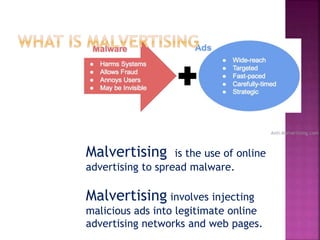
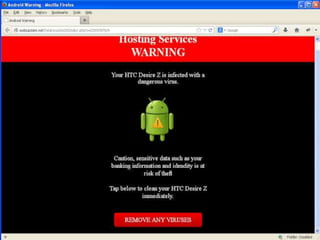
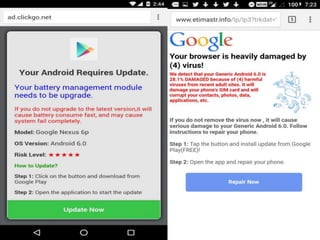
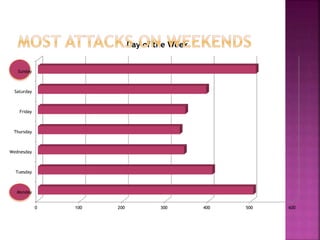
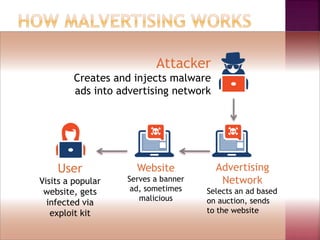
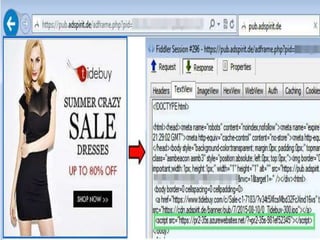
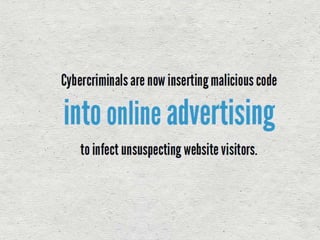
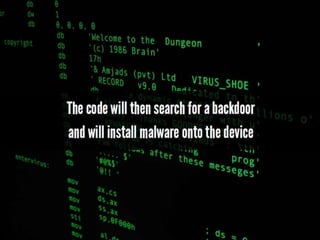
Malvertising refers to the use of online advertising to distribute malware by injecting malicious ads into legitimate advertising networks. In 2016, malvertising drove over 10 billion ad impressions, with varying activity throughout the week. Examples highlight specific exploit kits and ransomware associated with notable malvertising incidents.