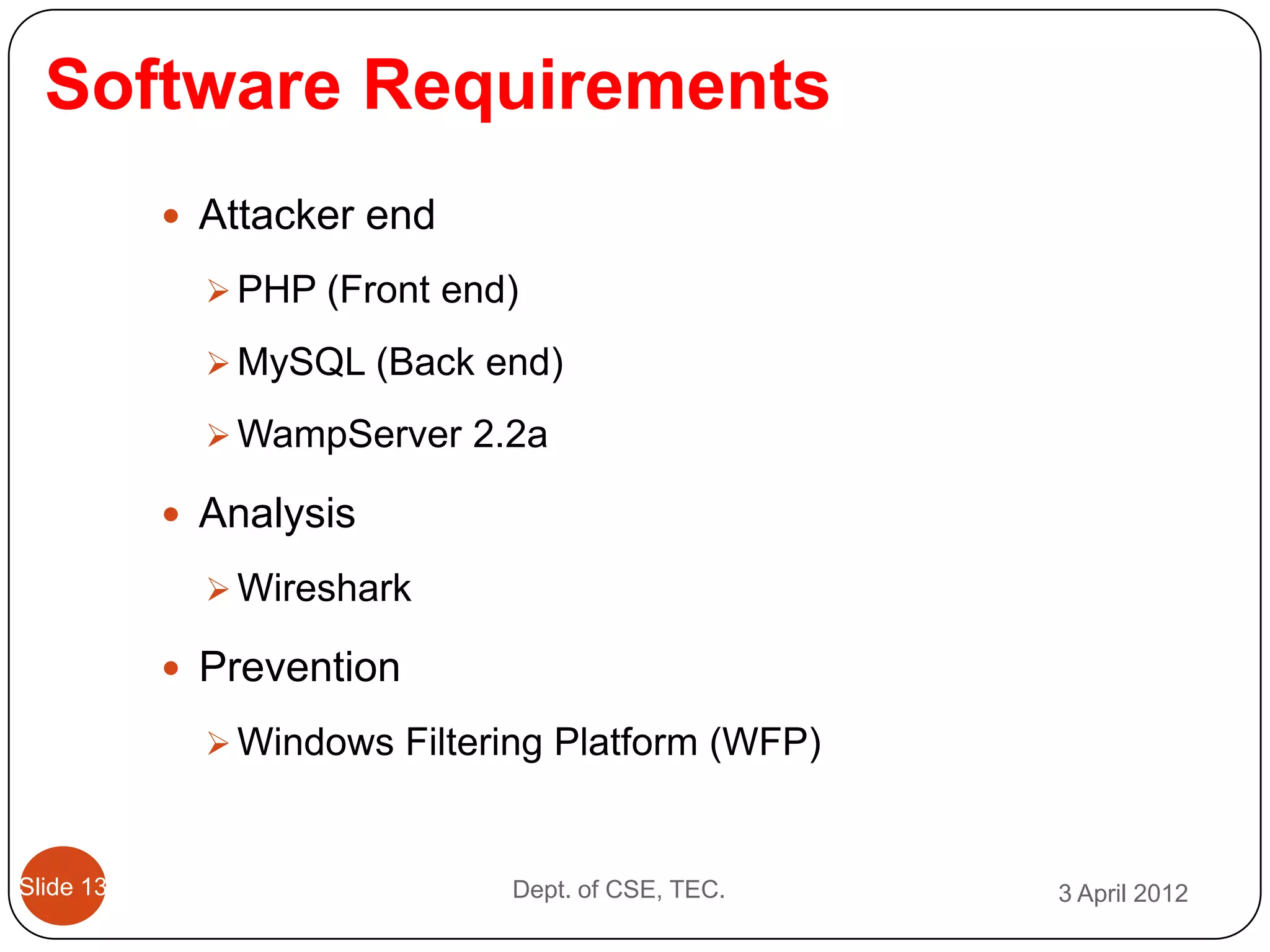
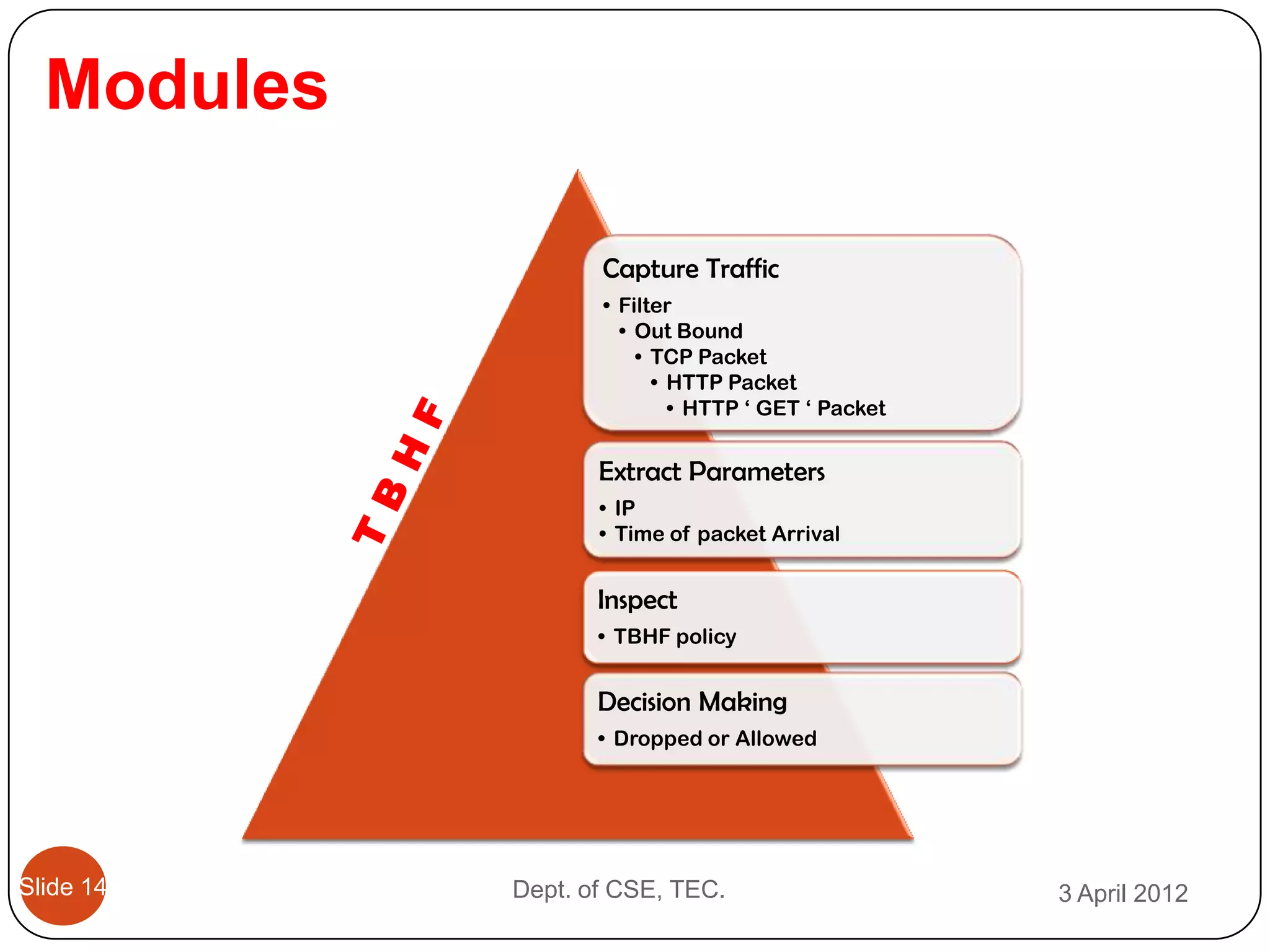
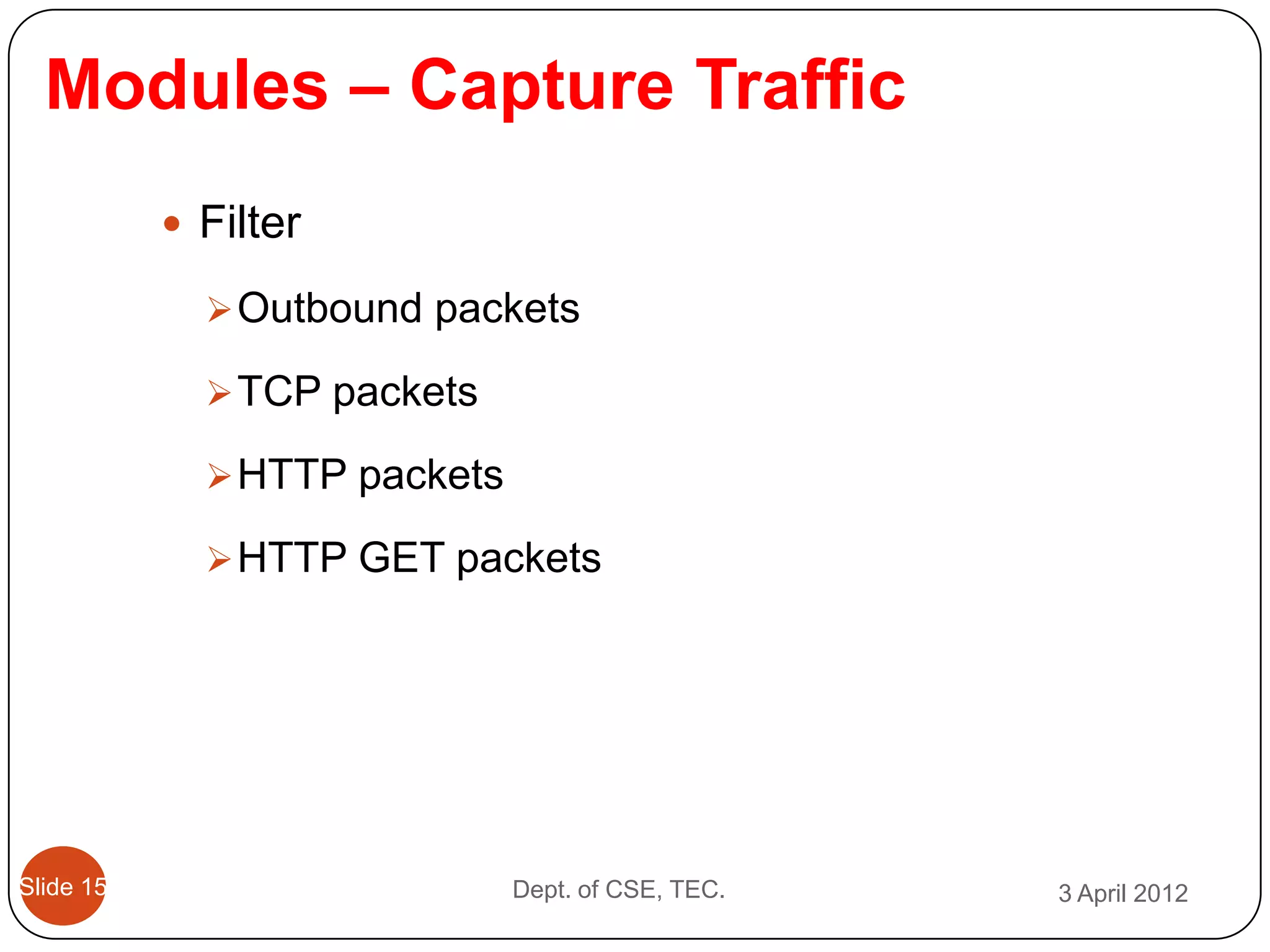
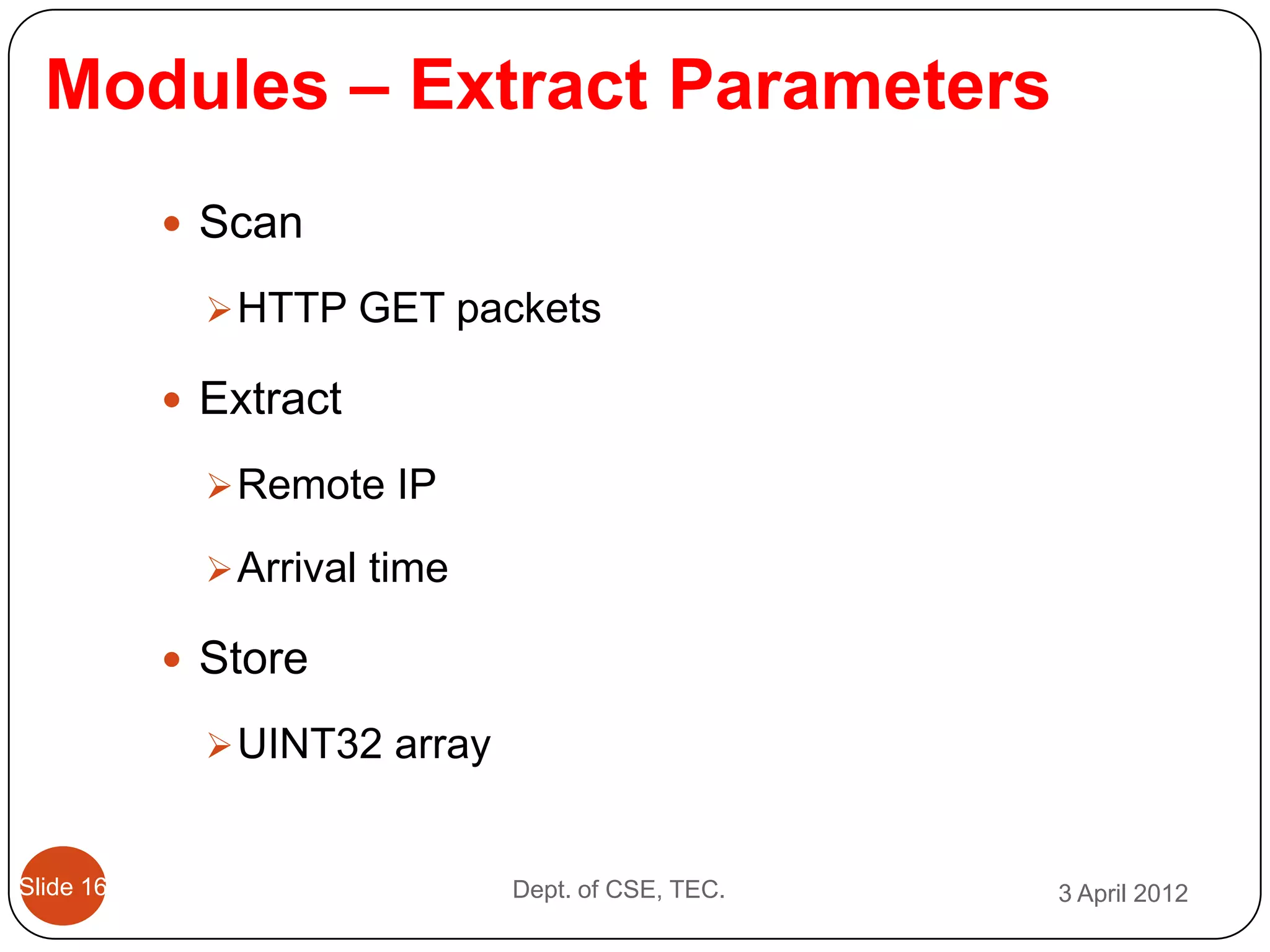
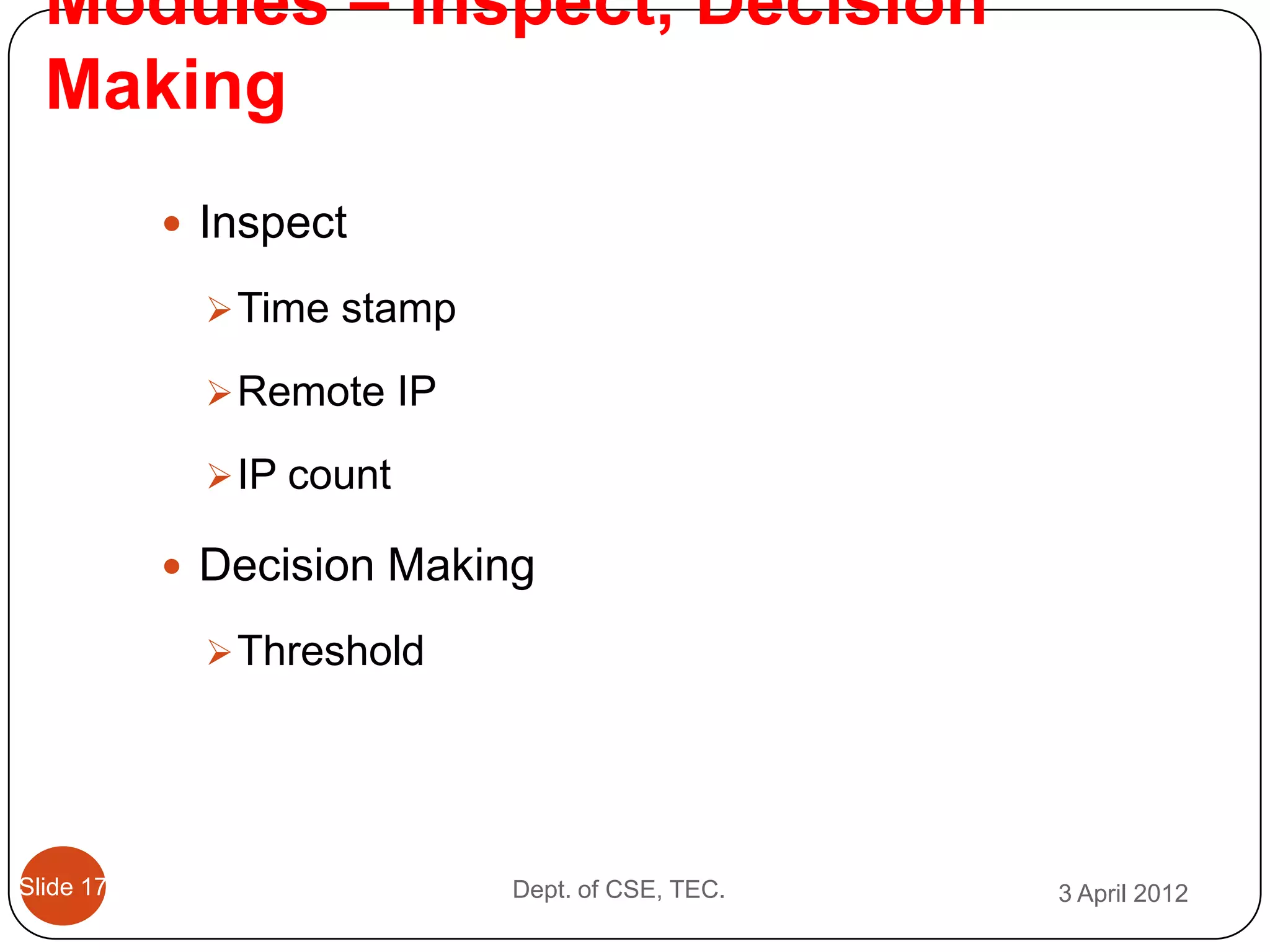
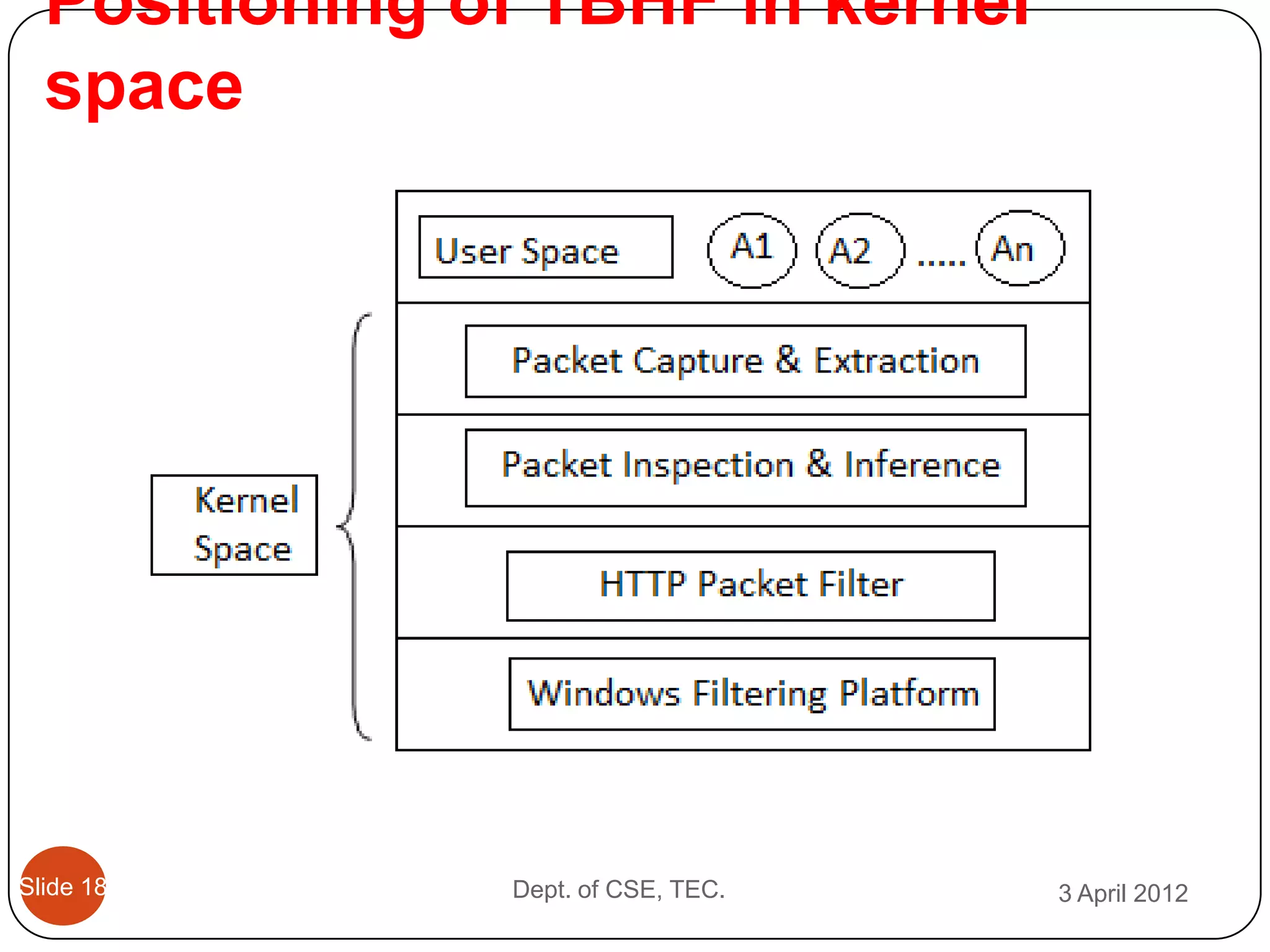
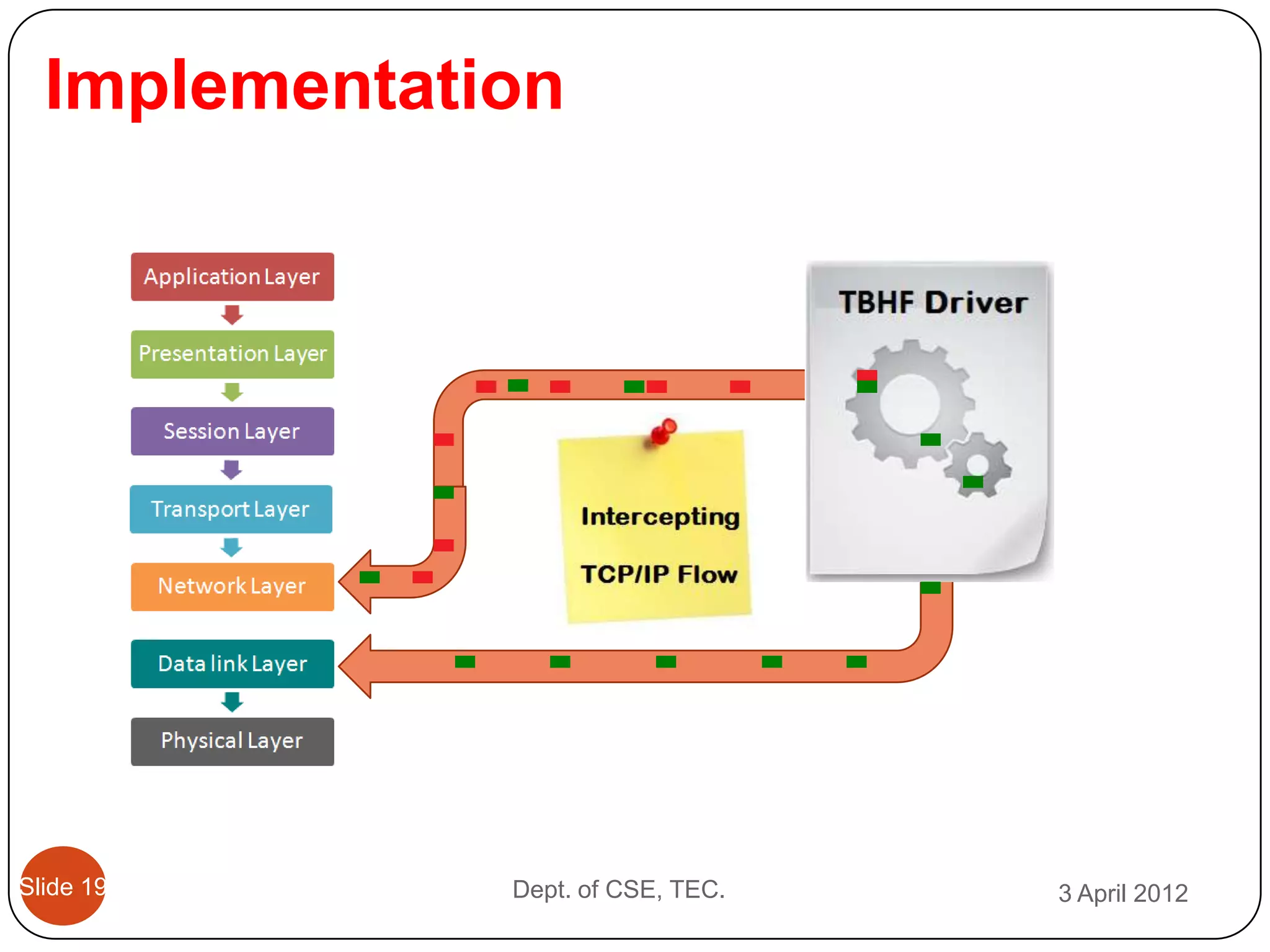
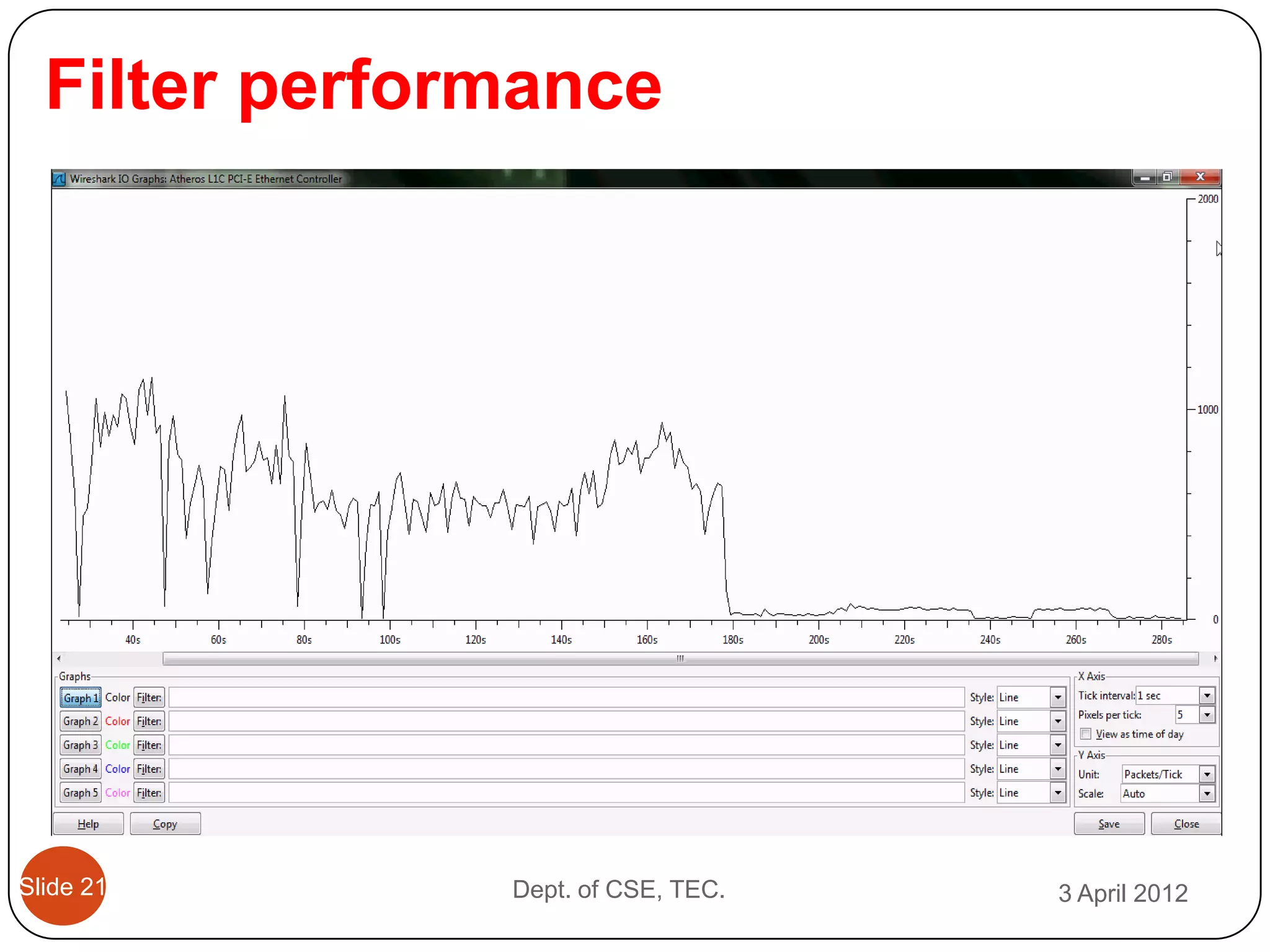
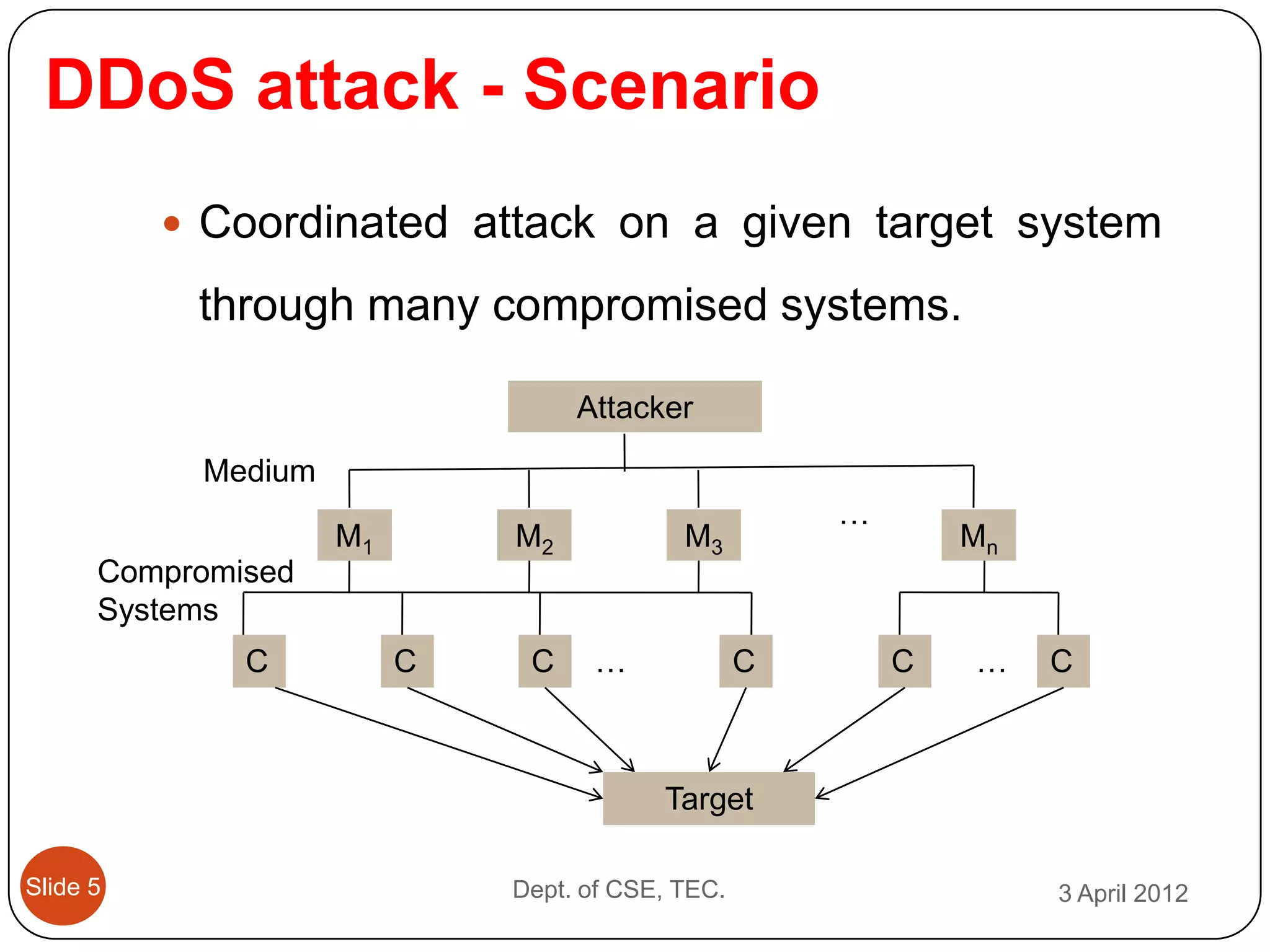
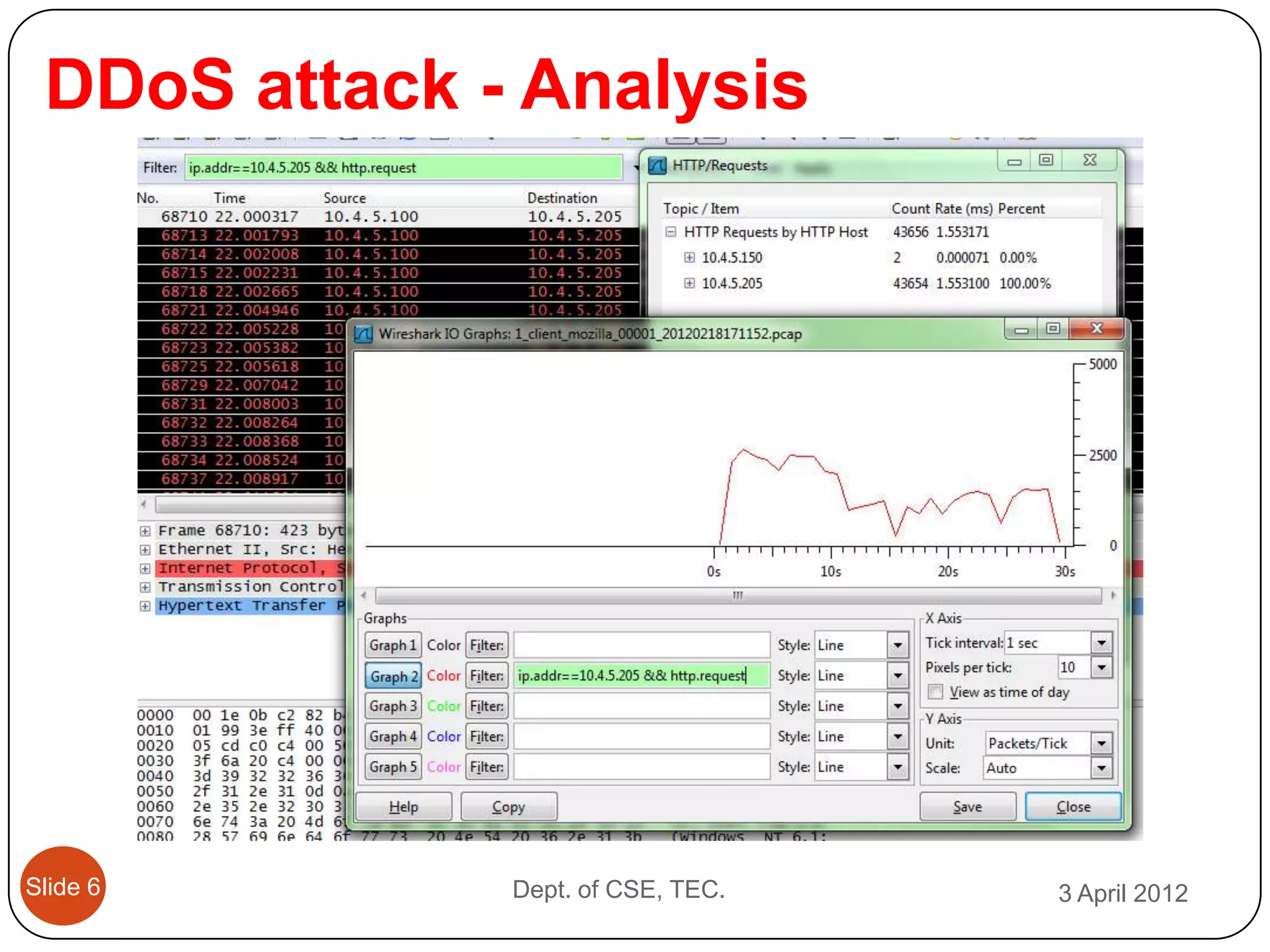
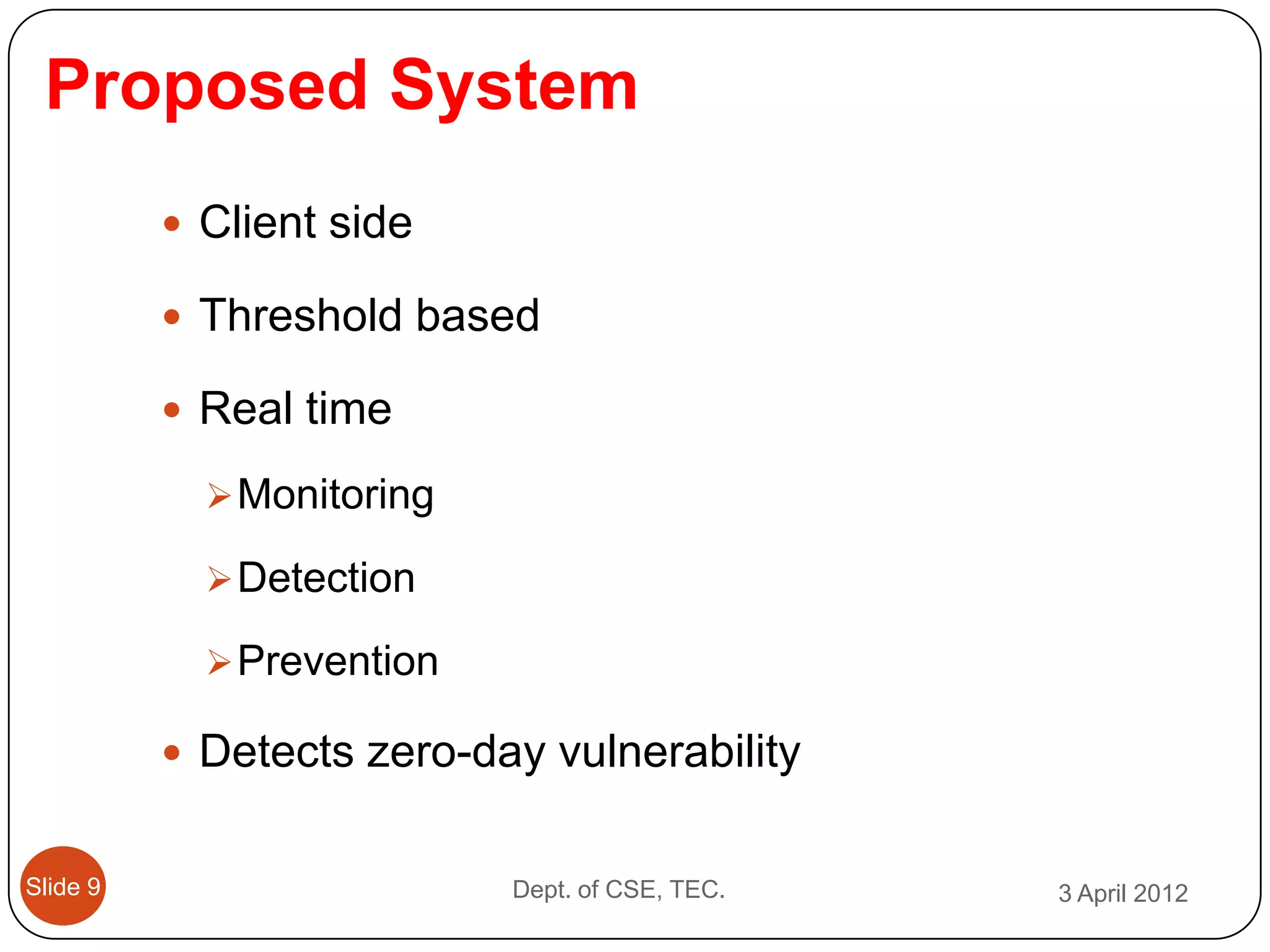
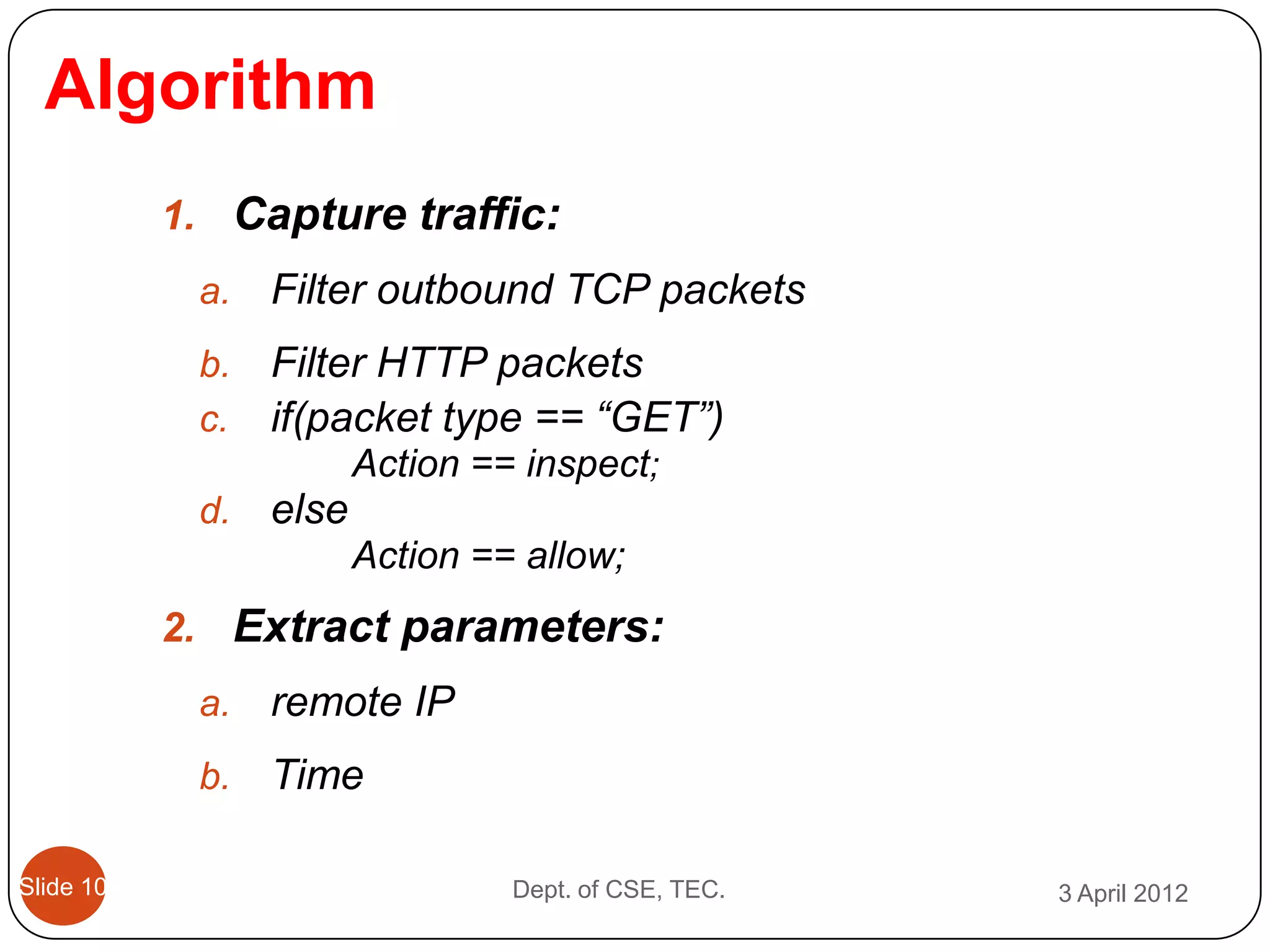
This document describes a threshold based kernel level HTTP filter (TBHF) for mitigating distributed denial of service (DDoS) attacks. It proposes a client-side real-time solution that monitors traffic, detects anomalies based on a threshold, and prevents attacks by dropping suspicious packets. The TBHF is implemented as a driver in the Windows kernel to filter outbound TCP and HTTP GET packets. It extracts IP addresses and timing data to make decisions according to a threshold-based policy.





![Algorithm Contd…
//r.addr1, r.addr2, …, r.addri -> remote IP
//T1, T2, …, Ti -> packet time
// ∆t -> Time stamp
3. Inspect:
a. If(r. addri not in array)
addr[i] = r.addri;
t[i] = Ti;
b. else if (r. addri in array && (T(i+1) – Ti)<=∆t)
r.count[i]++;
c. Else
Reset r.count[];
Slide 11 Dept. of CSE, TEC. 3 April 2012](https://image.slidesharecdn.com/tbhf-13398513794974-phpapp01-120616075913-phpapp01/75/Tbhf-14-2048.jpg)
![Algorithm Contd…
//N -> Threshold value
4. Decision Making:
a. If(r.count[i] >= N)
Action = allow packet;
b. else
Action = drop packet;
Slide 12 Dept. of CSE, TEC. 3 April 2012](https://image.slidesharecdn.com/tbhf-13398513794974-phpapp01-120616075913-phpapp01/75/Tbhf-15-2048.jpg)