What is the minimum security due diligence that a company needs to do before putting it's data in the cloud?
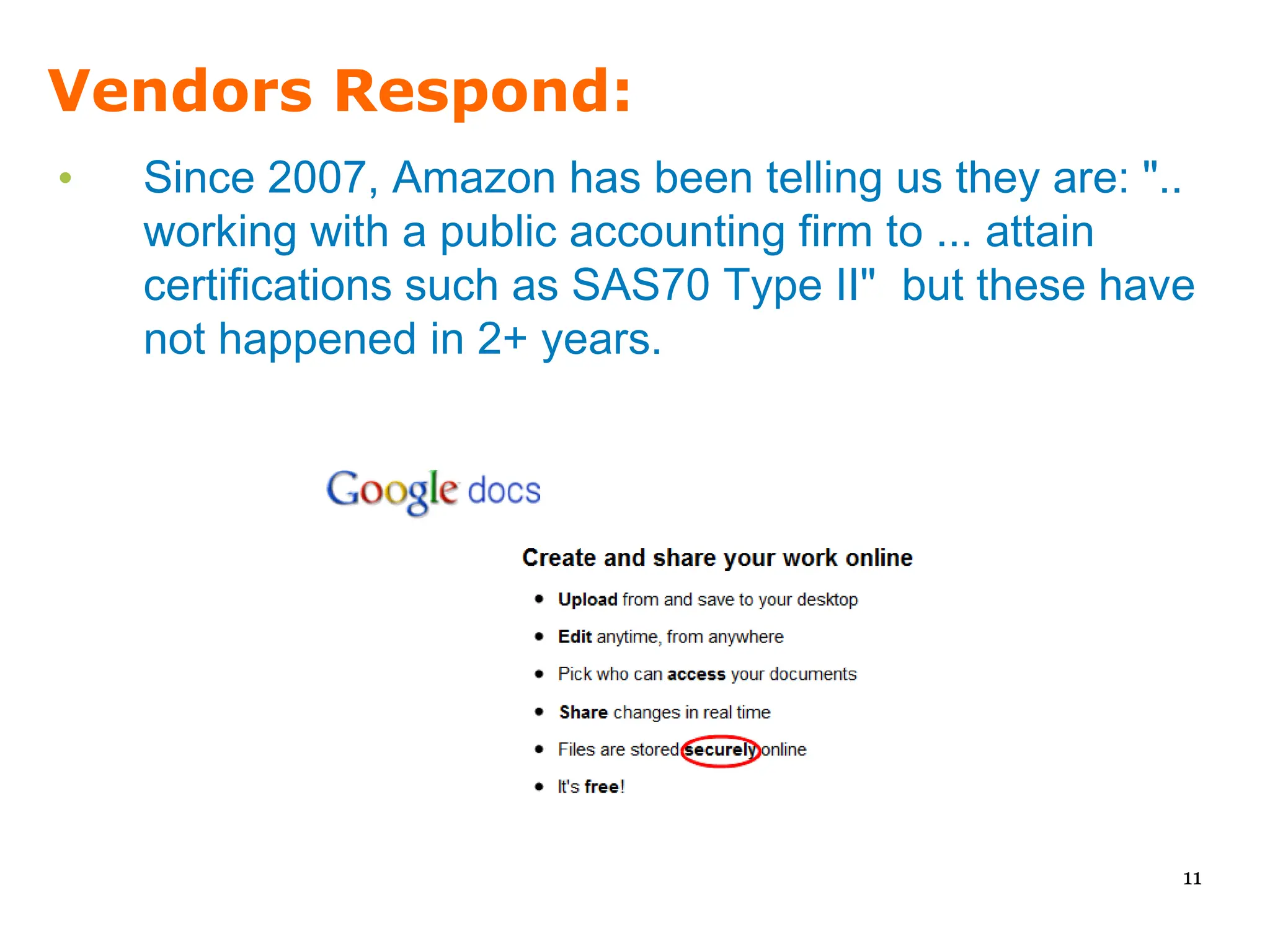
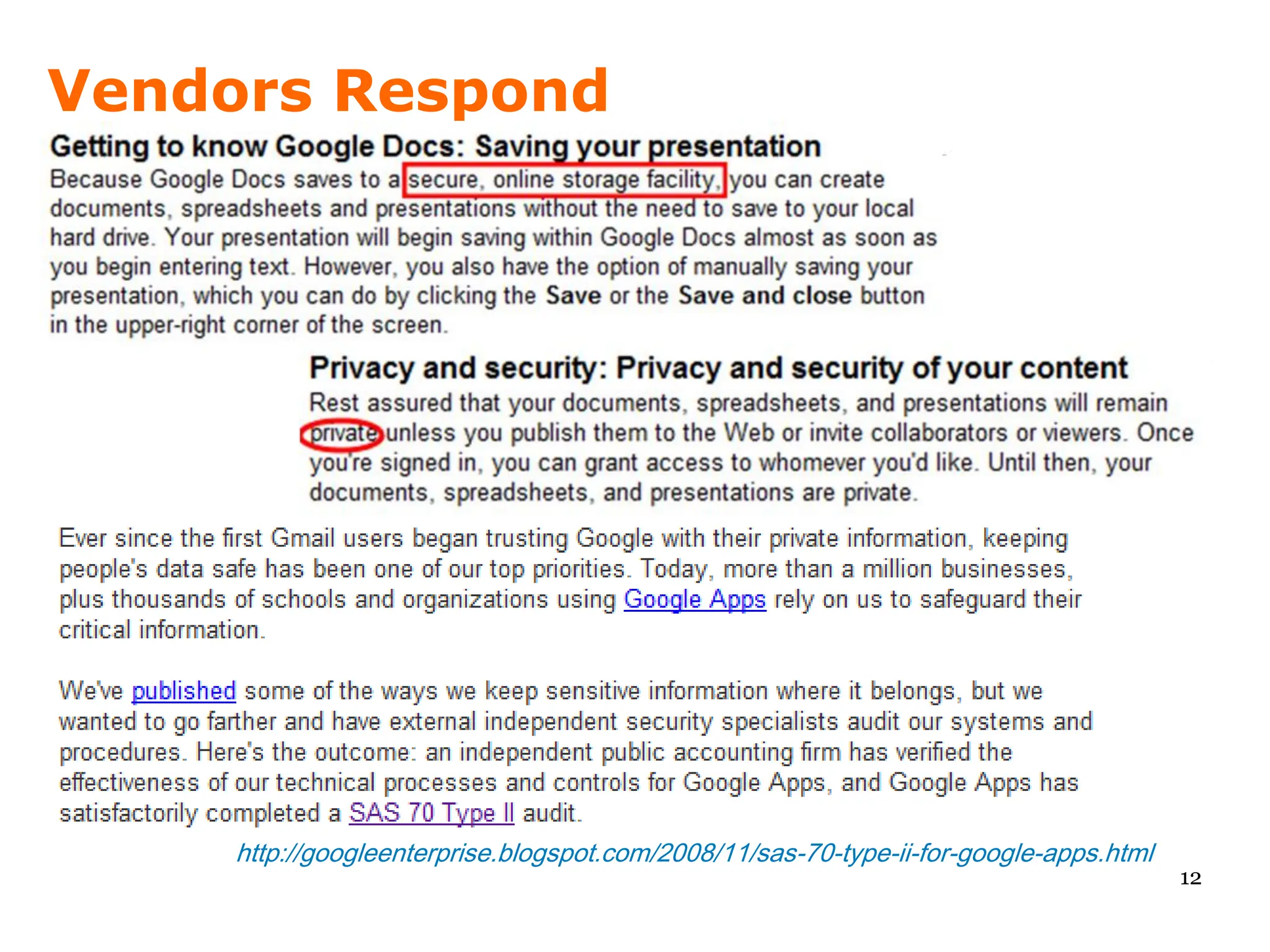
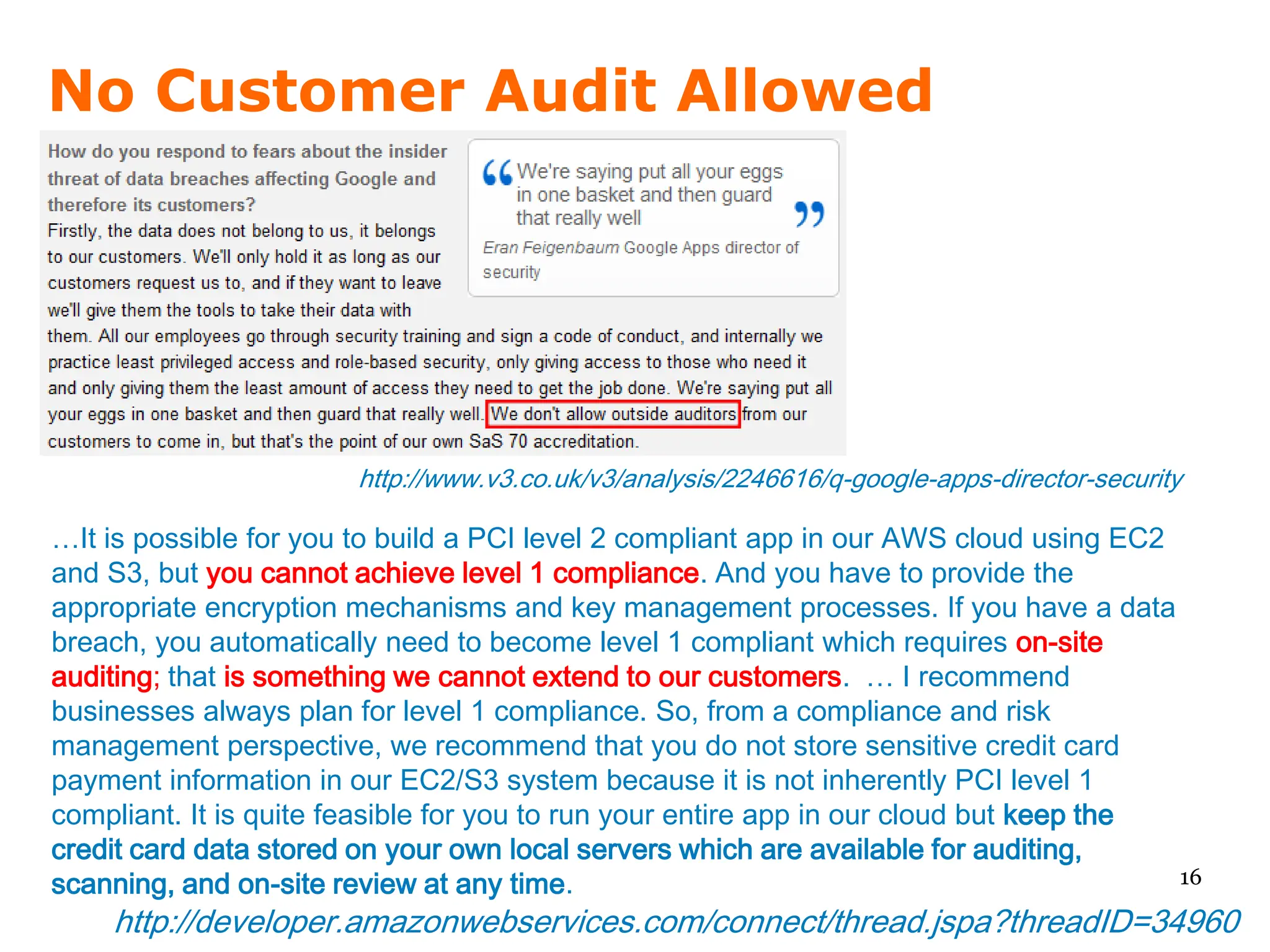
Since 2007, Amazon has been telling us they are ".. working with a public accounting firm to ... attain certifications such as SAS70 Type II" but these have not happened in 2+ years.
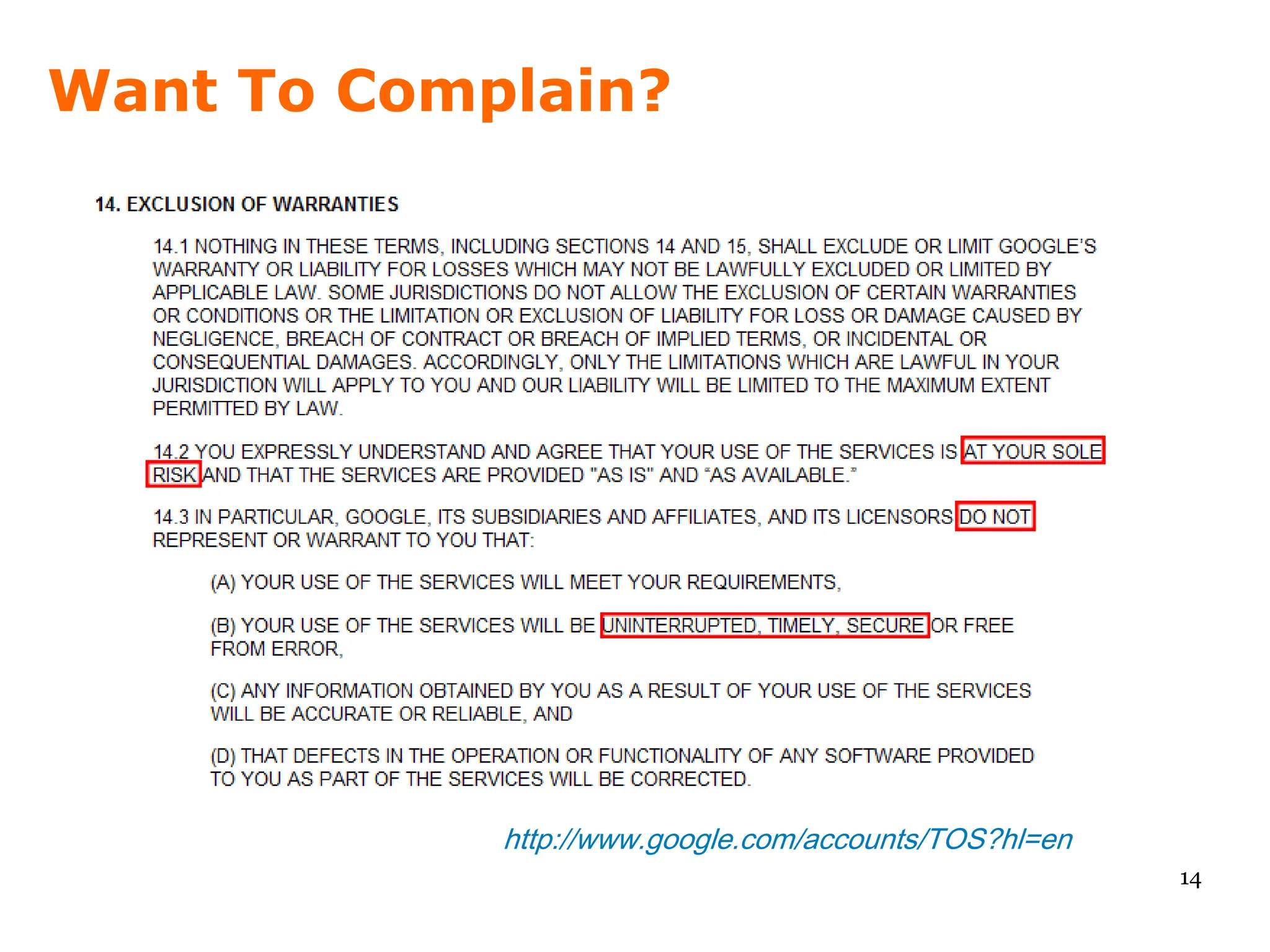
On one side of the cloud security issue we have the marketing people, who hype up the existing security and gloss over the non-existing. On the other side we have security services vendors, who hawk their wares by hyping up the lack of security. The truth is, there is a class of data for every cloud out there, and there is also someone who will suffer a data breach because they did not secure it properly.
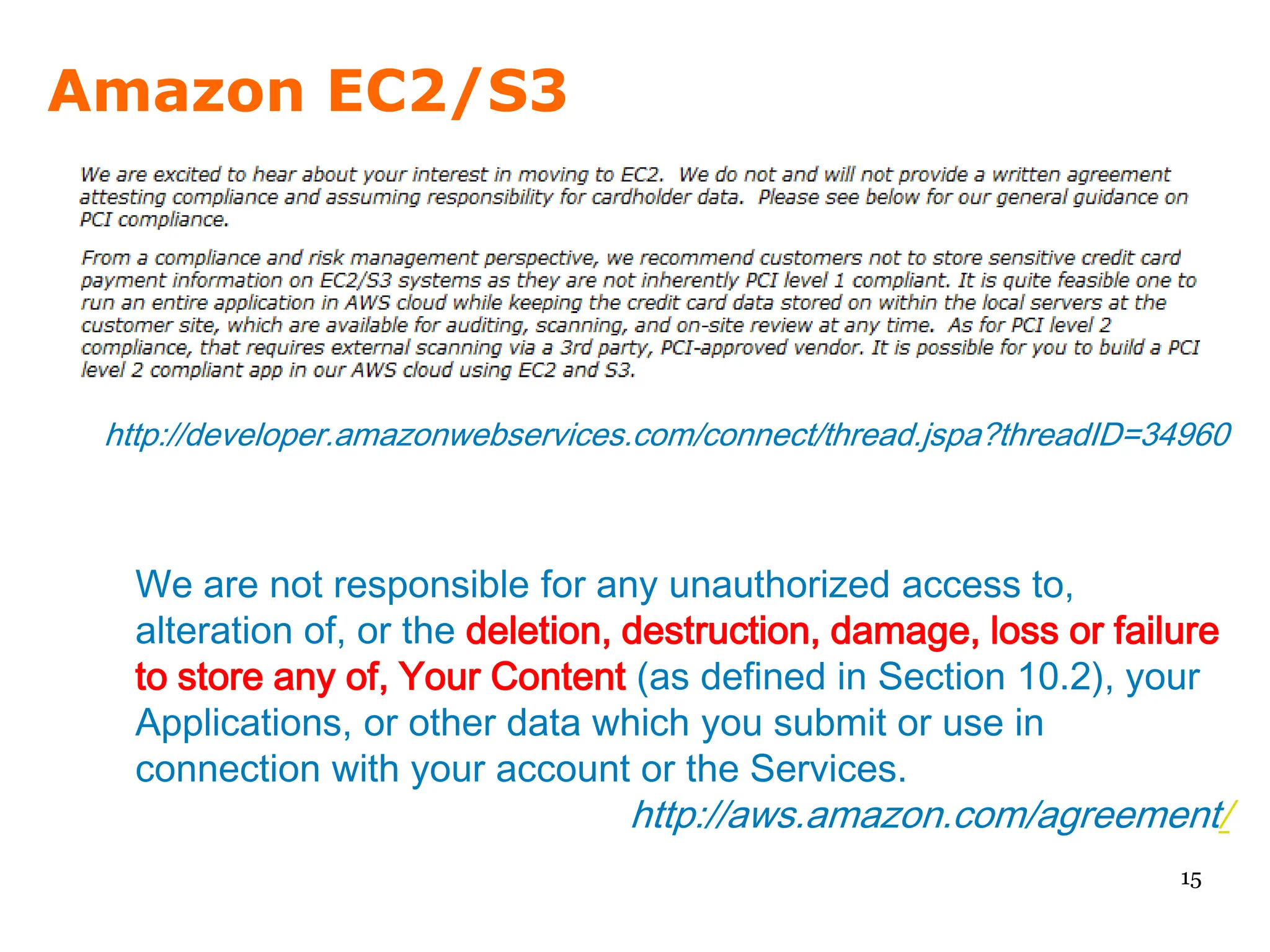
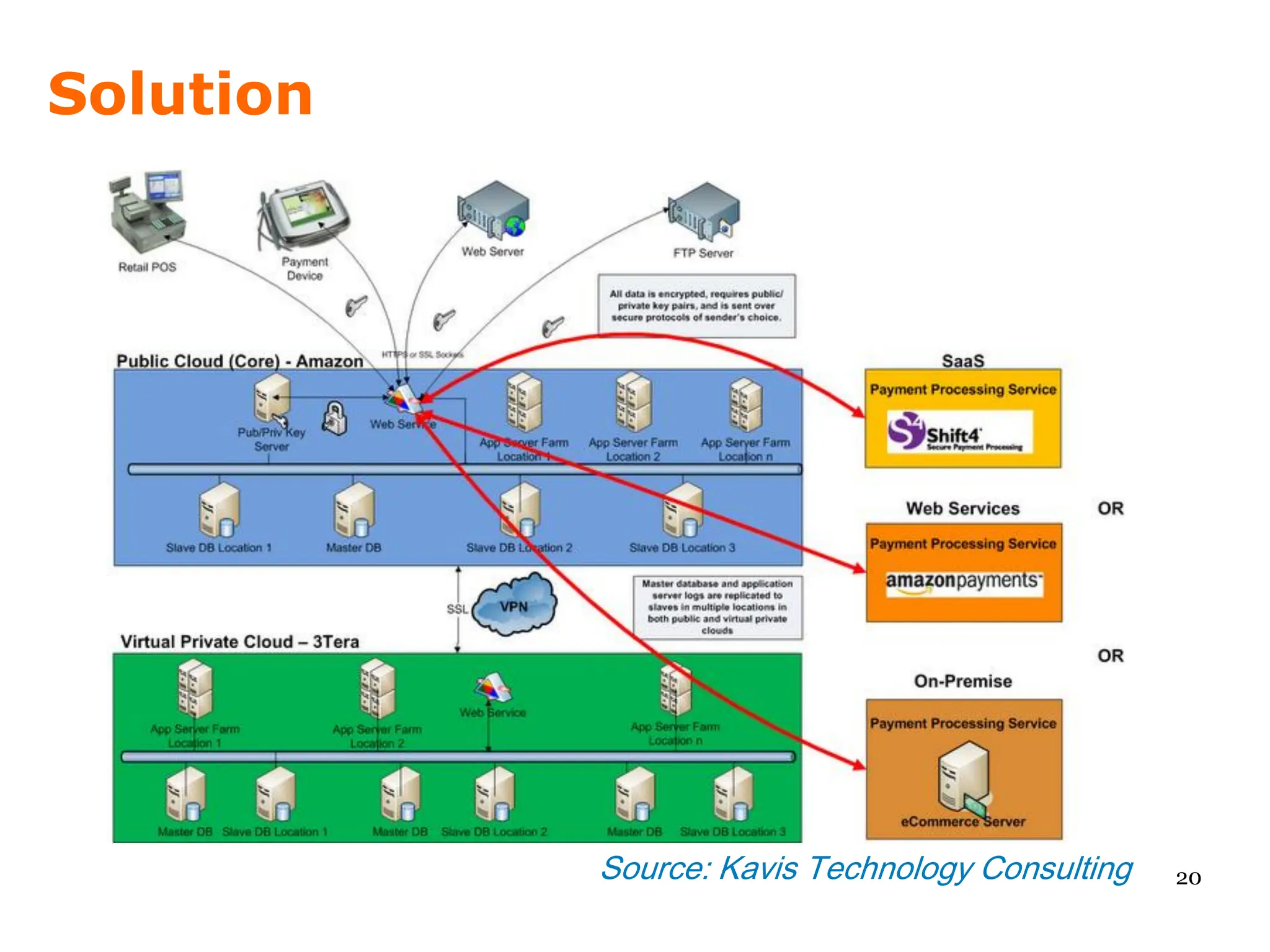
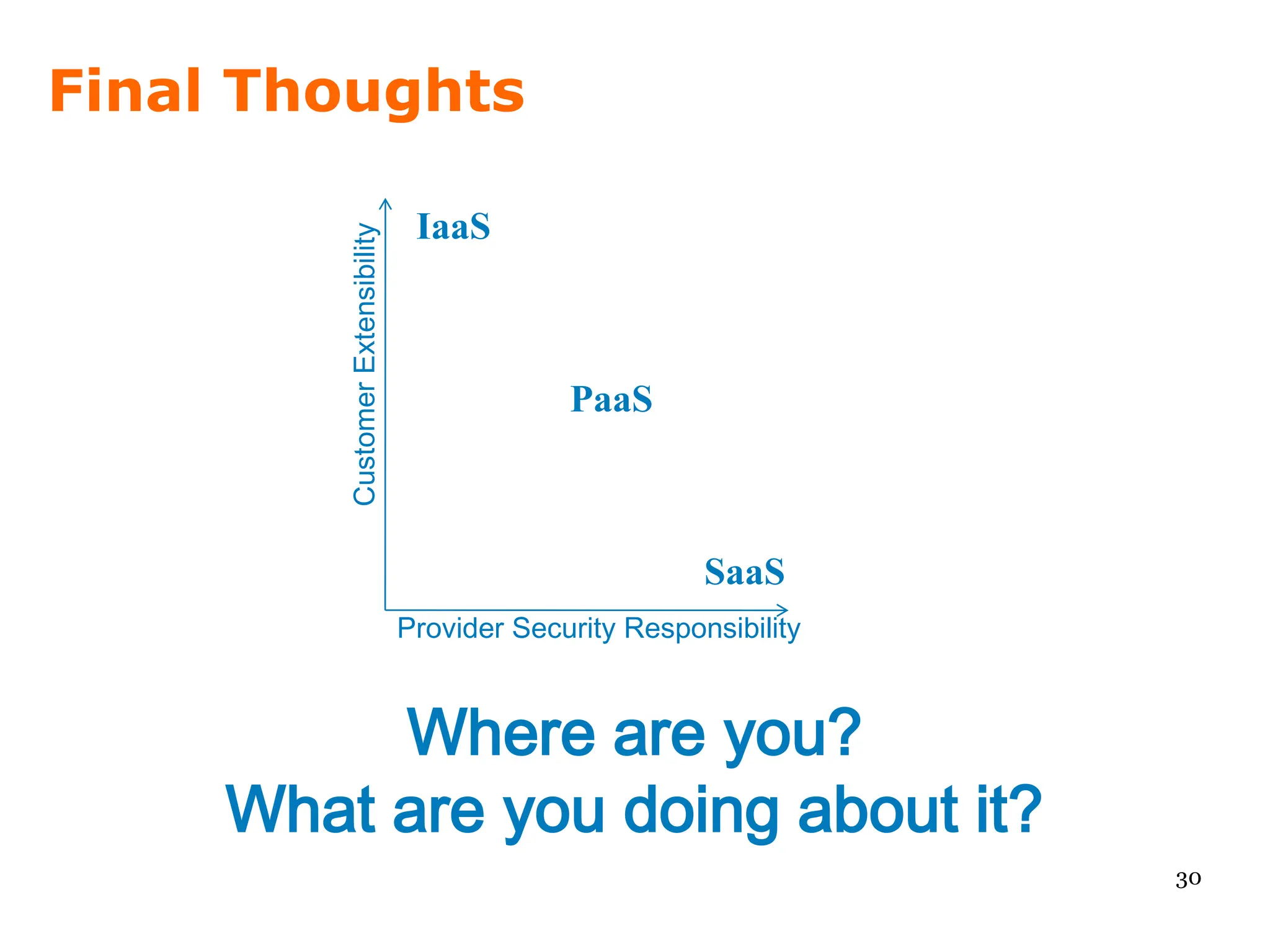
We look at Amazon's EC2, risk tolerance, and how to secure the data in the cloud.