Global tech project list
•Download as DOC, PDF•
0 likes•606 views
GlobaTech Solutions Call 09423222949 // 09823467071
Report
Share
Report
Share
Recommended
Recommended
Greencornertech,Ieee 2015-16 Projects,Nellore,AndhraPradeshCSE Java ieee titles 2015-16,Live Projects,Green Corner Tech,Nellore,Andhra ...

CSE Java ieee titles 2015-16,Live Projects,Green Corner Tech,Nellore,Andhra ...Green Corner Tech,Nellore
More Related Content
What's hot
What's hot (13)
Cloud computing titles list dream web techno solutions

Cloud computing titles list dream web techno solutions
cse projects,Dot net ieee projects 2015,green corner tech,nellore

cse projects,Dot net ieee projects 2015,green corner tech,nellore
Similar to Global tech project list
Greencornertech,Ieee 2015-16 Projects,Nellore,AndhraPradeshCSE Java ieee titles 2015-16,Live Projects,Green Corner Tech,Nellore,Andhra ...

CSE Java ieee titles 2015-16,Live Projects,Green Corner Tech,Nellore,Andhra ...Green Corner Tech,Nellore
DOTNET/JAVA/MATLAB/VLSI/NS2/EMBEDDED IEEE 2014 PROJECTS FOR ME/BE/B.TECH STUDENTS. FINAL YEAR 2014 PROJECTS FOR CSE/IT/ECE/EEE/ STUDENTS IN CHENNAI (S3 INFOTECH : 09884848198).
Final year IEEE 2014 projects for BE, BTech, ME, MTech &PHD Students (09884848198 : S3 Infotech)
Dear Students,
Greetings from S3 INFOTECH (0988 48 48 198). We are doing Final year (IEEE & APPLICATION) projects in DOTNET, JAVA, MATLAB, ANDROID, VLSI, NS2, EMBEDDED SYSTEMS and POWER ELECTRONICS.
For B.E, M.E, B.Tech, M.Tech, MCA, M.Sc, & PHD Students.
We implement your own IEEE concepts also in ALL Technologies. We are giving support for Journal Arrangement & Publication also.
Send your IEEE base paper to yes3info@gmail.com (or) info@s3computers.com.
To Register your project: www.s3computers.com
We are providing Projects in
• DOT NET
• JAVA / J2EE / J2ME
• EMBEDDED & POWER ELECTRONICS
• MATLAB
• NS2
• VLSI
• NETWORKING
• HADOOP / Bigdata
• Android
• PHP
JAVA IEEE 2014 PROJECTS FOR ME/BE/B.TECH STUDENTS. FINAL YEAR 2014 PROJECTS F...

JAVA IEEE 2014 PROJECTS FOR ME/BE/B.TECH STUDENTS. FINAL YEAR 2014 PROJECTS F...S3 Infotech IEEE Projects
Similar to Global tech project list (20)
IEEE projects java and dotnet for BE BTECH ME MTECH MCA MCS Diploma

IEEE projects java and dotnet for BE BTECH ME MTECH MCA MCS Diploma
CSE Java ieee titles 2015-16,Live Projects,Green Corner Tech,Nellore,Andhra ...

CSE Java ieee titles 2015-16,Live Projects,Green Corner Tech,Nellore,Andhra ...
Ieee projects-in-pondicherry | 2015 ieee projects in pondicherry

Ieee projects-in-pondicherry | 2015 ieee projects in pondicherry
Bulk ieee projects | bulk ieee projects in pondicherry

Bulk ieee projects | bulk ieee projects in pondicherry
JAVA IEEE 2014 PROJECTS FOR ME/BE/B.TECH STUDENTS. FINAL YEAR 2014 PROJECTS F...

JAVA IEEE 2014 PROJECTS FOR ME/BE/B.TECH STUDENTS. FINAL YEAR 2014 PROJECTS F...
IEEE JAVA DOTNET ANDROID PROJECT TITLES 2014 - 2015 

IEEE JAVA DOTNET ANDROID PROJECT TITLES 2014 - 2015
Ieee 2020 21 java dotnet in pondicherry,final year projects in pondicherry,pr...

Ieee 2020 21 java dotnet in pondicherry,final year projects in pondicherry,pr...
Recently uploaded
Recently uploaded (20)
Automating Google Workspace (GWS) & more with Apps Script

Automating Google Workspace (GWS) & more with Apps Script
ICT role in 21st century education and its challenges

ICT role in 21st century education and its challenges
Boost Fertility New Invention Ups Success Rates.pdf

Boost Fertility New Invention Ups Success Rates.pdf
Apidays New York 2024 - The value of a flexible API Management solution for O...

Apidays New York 2024 - The value of a flexible API Management solution for O...
Emergent Methods: Multi-lingual narrative tracking in the news - real-time ex...

Emergent Methods: Multi-lingual narrative tracking in the news - real-time ex...
TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery

TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
2024: Domino Containers - The Next Step. News from the Domino Container commu...

2024: Domino Containers - The Next Step. News from the Domino Container commu...
"I see eyes in my soup": How Delivery Hero implemented the safety system for ...

"I see eyes in my soup": How Delivery Hero implemented the safety system for ...
Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...

Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...
Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood

Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood
Apidays Singapore 2024 - Scalable LLM APIs for AI and Generative AI Applicati...

Apidays Singapore 2024 - Scalable LLM APIs for AI and Generative AI Applicati...
TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments

TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments
EMPOWERMENT TECHNOLOGY GRADE 11 QUARTER 2 REVIEWER

EMPOWERMENT TECHNOLOGY GRADE 11 QUARTER 2 REVIEWER
Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe

Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe
Why Teams call analytics are critical to your entire business

Why Teams call analytics are critical to your entire business
Global tech project list
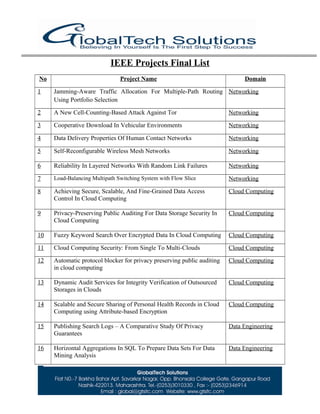
- 1. IEEE Projects Final List No Project Name Domain 1 Jamming-Aware Traffic Allocation For Multiple-Path Routing Using Portfolio Selection Networking 2 A New Cell-Counting-Based Attack Against Tor Networking 3 Cooperative Download In Vehicular Environments Networking 4 Data Delivery Properties Of Human Contact Networks Networking 5 Self-Reconfigurable Wireless Mesh Networks Networking 6 Reliability In Layered Networks With Random Link Failures Networking 7 Load-Balancing Multipath Switching System with Flow Slice Networking 8 Achieving Secure, Scalable, And Fine-Grained Data Access Control In Cloud Computing Cloud Computing 9 Privacy-Preserving Public Auditing For Data Storage Security In Cloud Computing Cloud Computing 10 Fuzzy Keyword Search Over Encrypted Data In Cloud Computing Cloud Computing 11 Cloud Computing Security: From Single To Multi-Clouds Cloud Computing 12 Automatic protocol blocker for privacy preserving public auditing in cloud computing Cloud Computing 13 Dynamic Audit Services for Integrity Verification of Outsourced Storages in Clouds Cloud Computing 14 Scalable and Secure Sharing of Personal Health Records in Cloud Computing using Attribute-based Encryption Cloud Computing 15 Publishing Search Logs – A Comparative Study Of Privacy Guarantees Data Engineering 16 Horizontal Aggregations In SQL To Prepare Data Sets For Data Mining Analysis Data Engineering
- 2. 17 Closing The Loop In Webpage Understanding Data Engineering 18 Automatic Discovery Of Personal Name Aliases From The Web Data Engineering 19 A Personalized Ontology Model For Web Information Gathering Data Engineering 20 Scalable And Secure Sharing Of Personal Health Records In Cloud Computing Using Attribute-Based Encryption Data Engineering 21 Efficient Computation of Range Aggregates against Uncertain Location Based Queries Data Engineering 22 Hiding Sensitive Association Rule For Privacy Preservation Security 23 Authentication Schemes For Session Passwords Using Color And Images Security 24 Separable Reversible Data Hiding In Encrypted Image Security 25 Implicit Password Authentication System Security 26 Data Hiding In Motion Vectors Of Compressed Video Based On Their Associated Prediction Error Security 27 Defenses Against Large Scale Online Password Guessing Attacks By Using Persuasive Click Points Security 28 A Probabilistic Model Of (T, N) Visual Cryptography Scheme With Dynamic Group Security
- 5. 29 Robust Correlation Of Encrypted Attack Traffic Through Stepping Stones By Flow Watermarking Image Processing 30 On the Selection of Optimal Feature Region Set for Robust Digital Image Watermarking Image Processing 31 Semi supervised Biased Maximum Margin Analysis For Interactive Image Retrieval Image Processing 32 Three-Dimensional Password For More Secure Authentication Image Processing 33 Optimal Stochastic Location Updates In Mobile Ad Hoc Networks Mobile Computing 34 Mabs: Multicast Authentication Based On Batch Signature Mobile Computing 35 Random Cast: An Energy Efficient Communication Scheme For Mobile Ad Hoc Networks Mobile Computing 36 Monitoring Service Systems From A Language-Action Perspective Service Computing 37 Online Intrusion Alert Aggregation With Generative Data Stream Modeling Service Computing 38 Dynamic Authentication For Cross-Realm SOA-Based Business Processes Service Computing 39 Identifying Content For Planned Events Across Social Media Sites Service Computing 40 Bridging Socially-Enhanced Virtual Communities Service Computing 41 Automated Certification For Compliant Cloud-Based Business Processes Data Mining 42 Slow Adaptive OFDMA Systems Through Chance Constrained Programming Signal Processing 43 Exploiting Dynamic Resource Allocation For Efficient Parallel Data Processing In The Cloud Parallel & Distributed 44 Anonymous Query Processing In Road Network Parallel & Distributed 45 Throughput Optimization In High Speed Downlink Packet Access (HSDPA) Wireless Communications 46 Analysis of P2P File Sharing Network Wireless Communications 47 Digital Image Watermarking Image Processing 48 Load-Balancing Multipath Switching System with Flow Slice Data Mining 49 Vulnerability Analysis in SOA-based Business Processes Data Mining 50 A Fast Clustering-Based Feature Subset 51 A Load Balancing Model Based on Cloud Partitioningfor the Public Cloud
