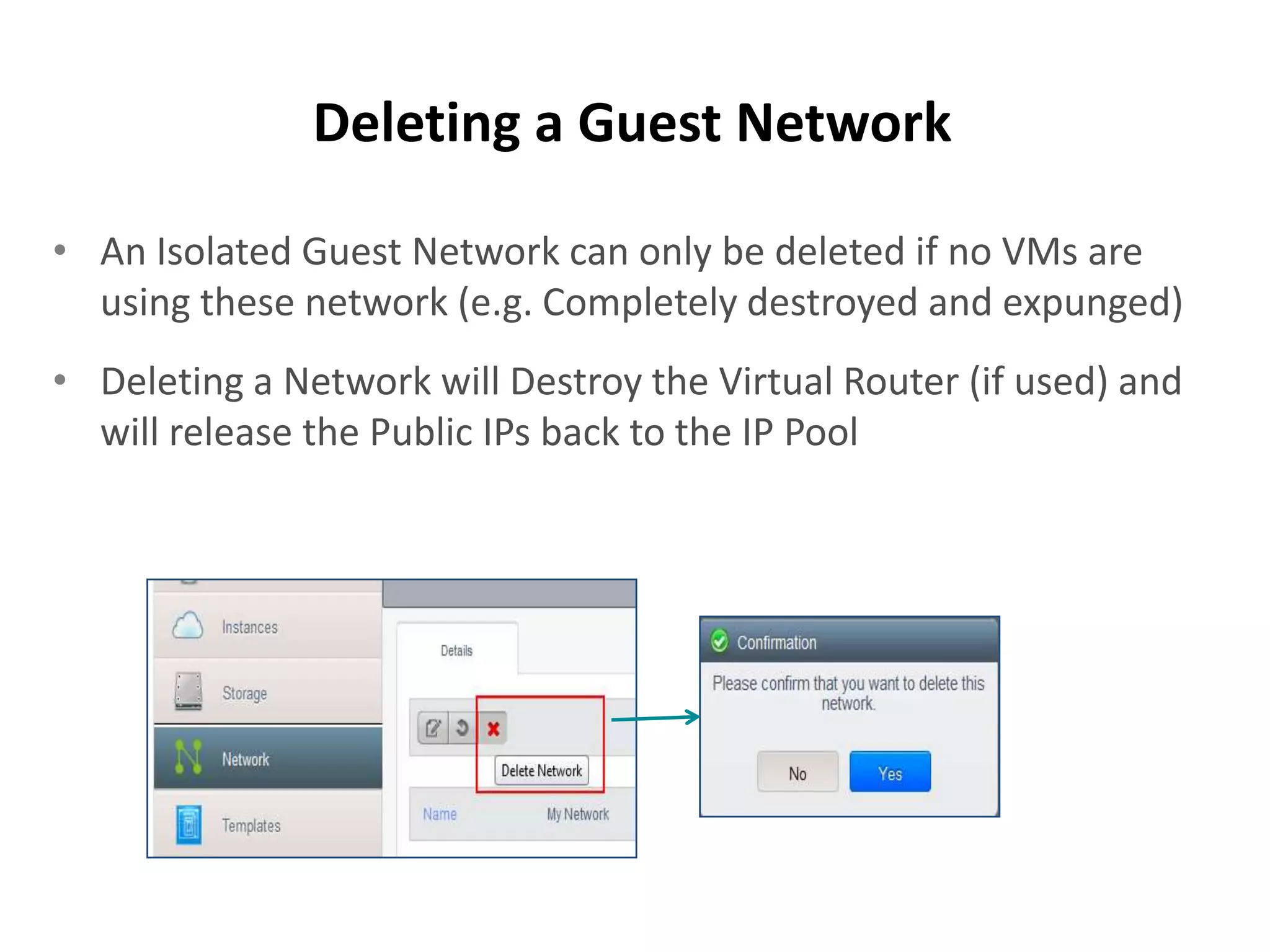
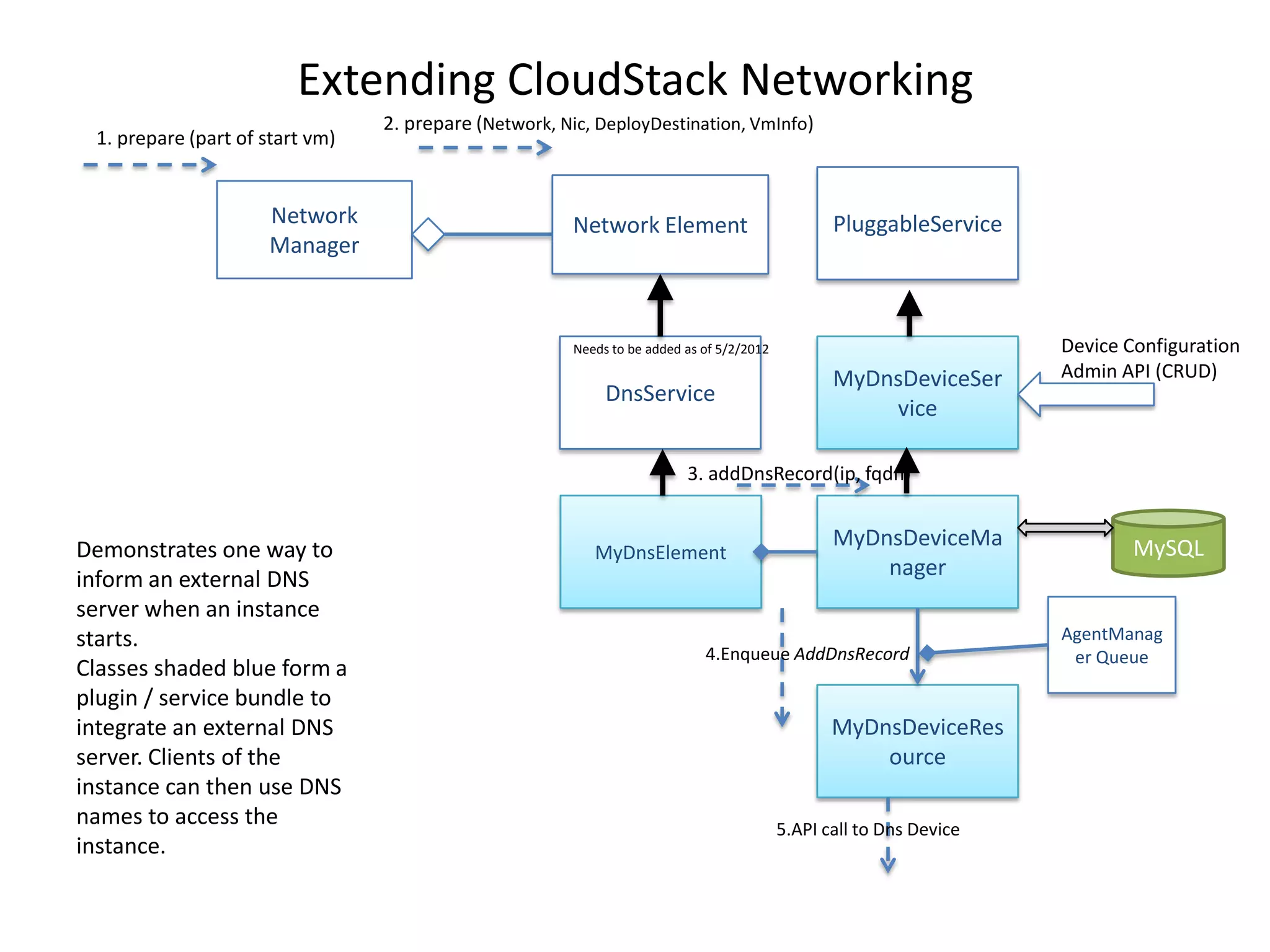
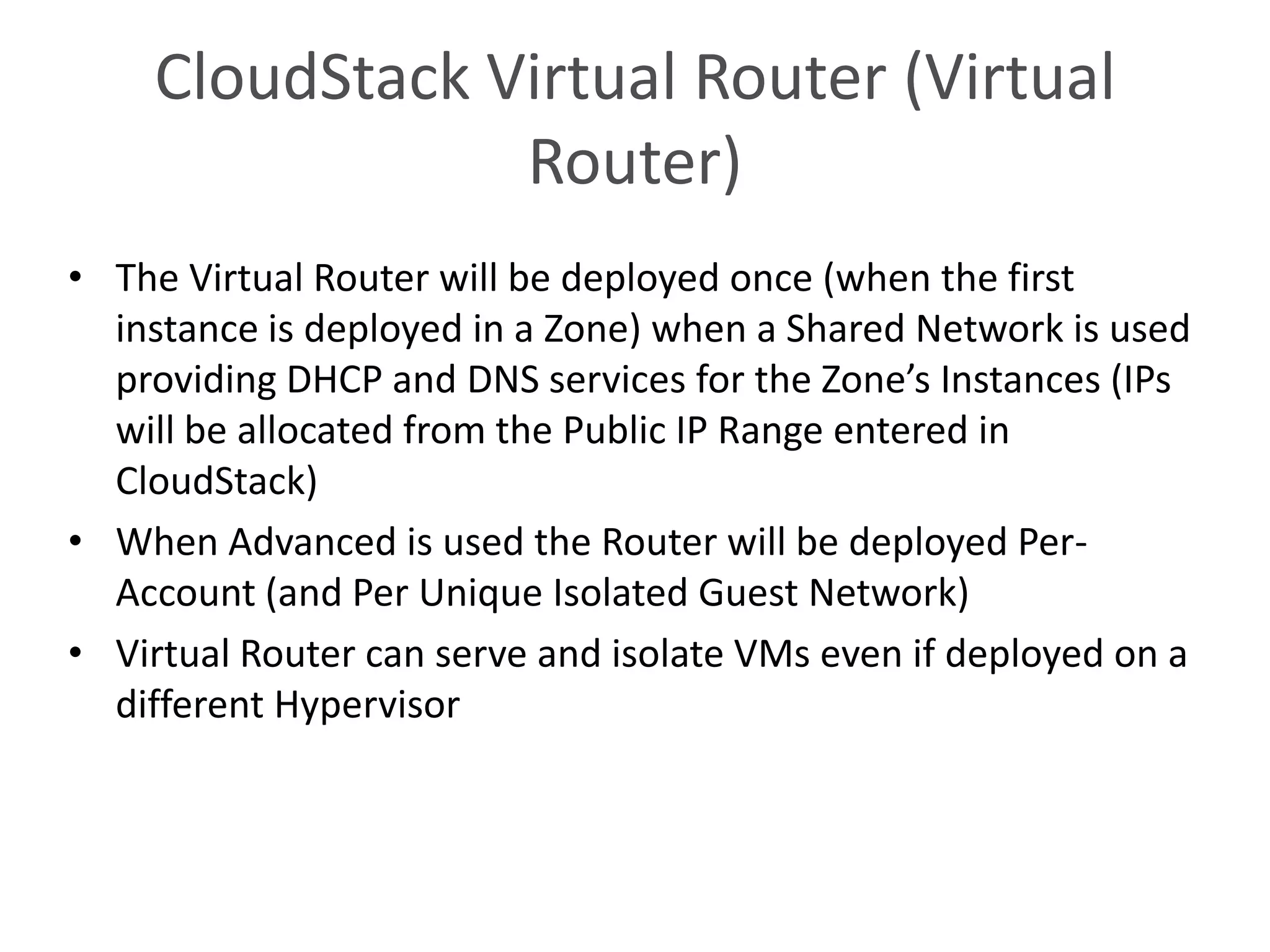
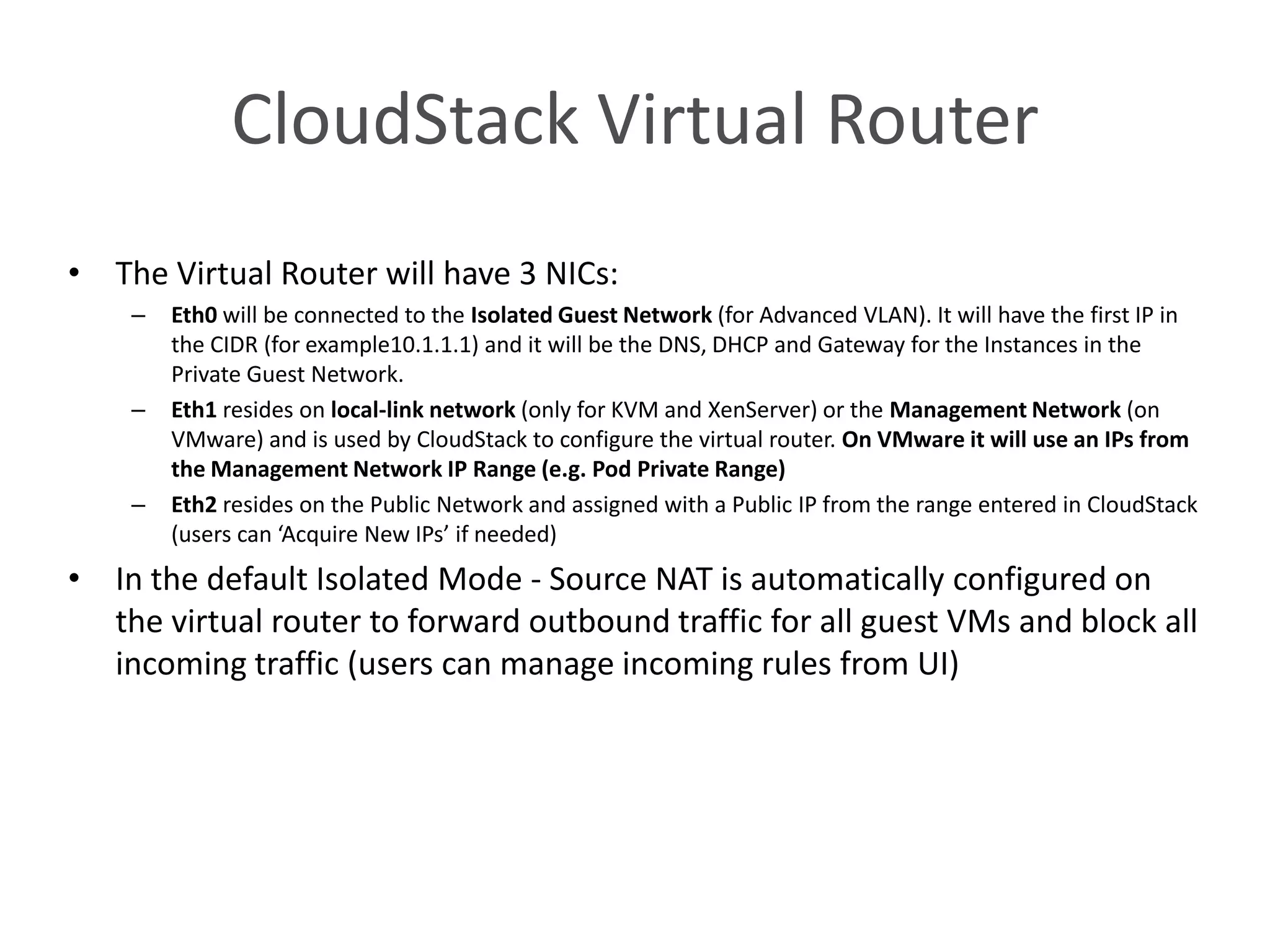
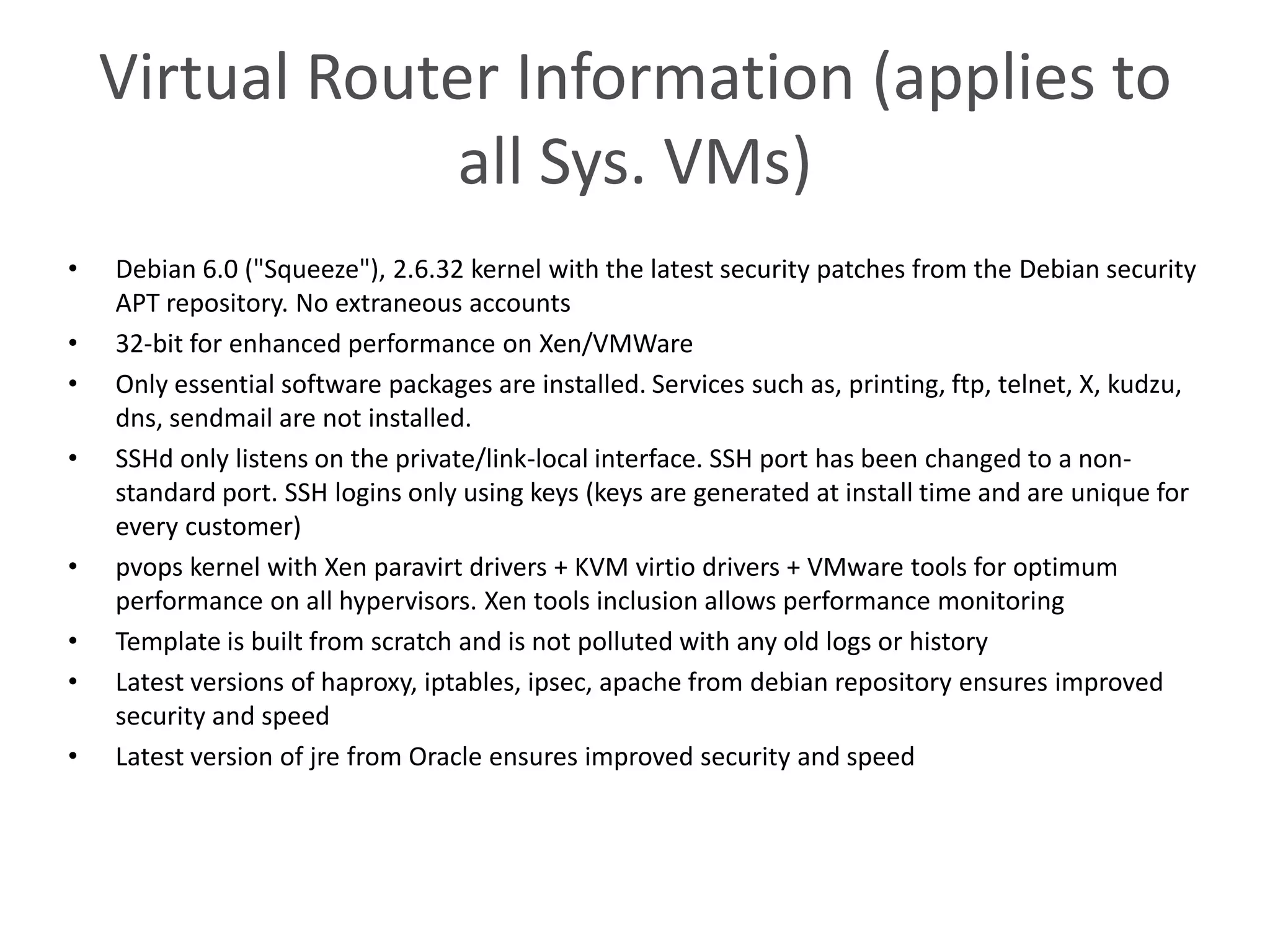
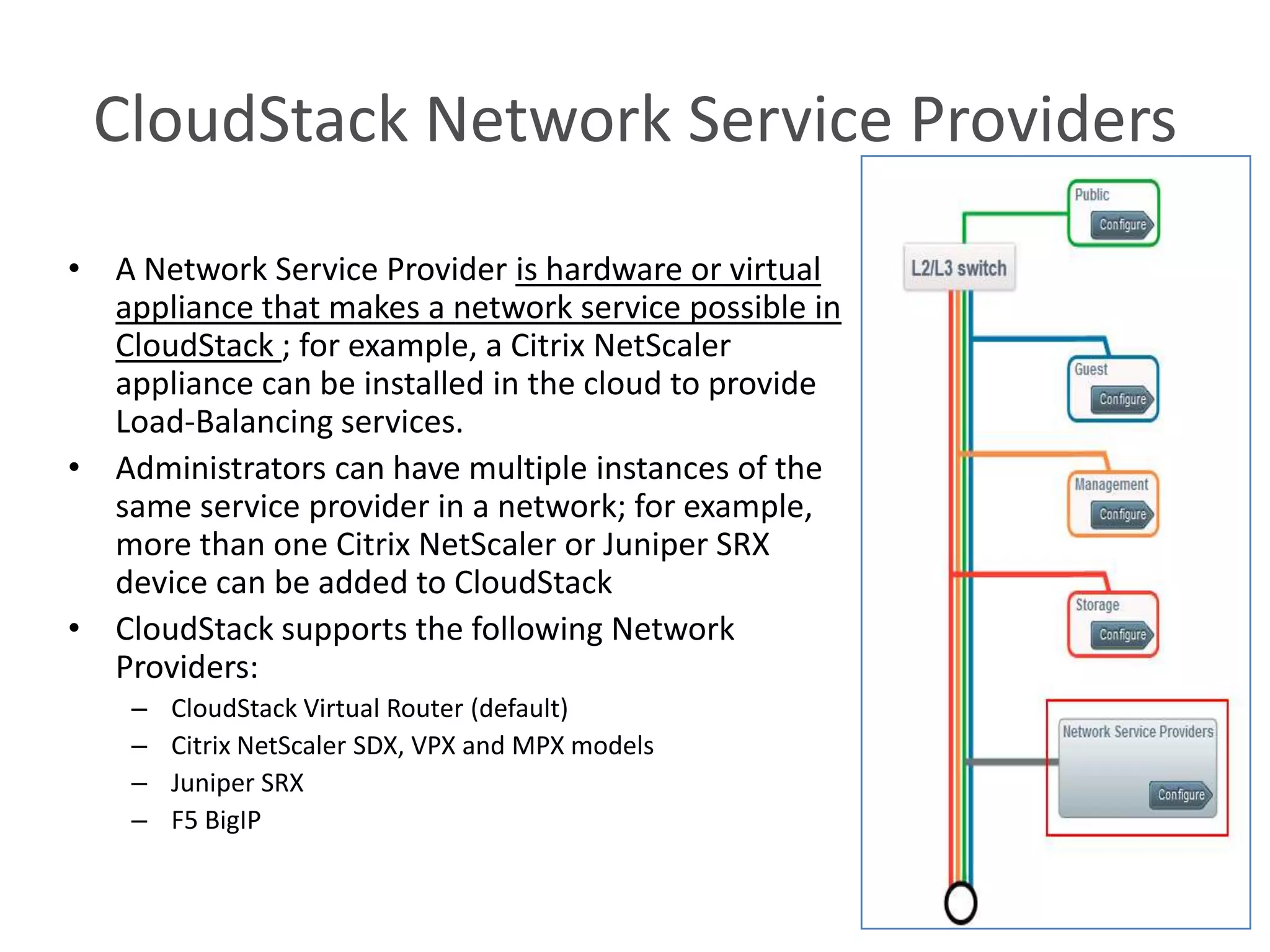
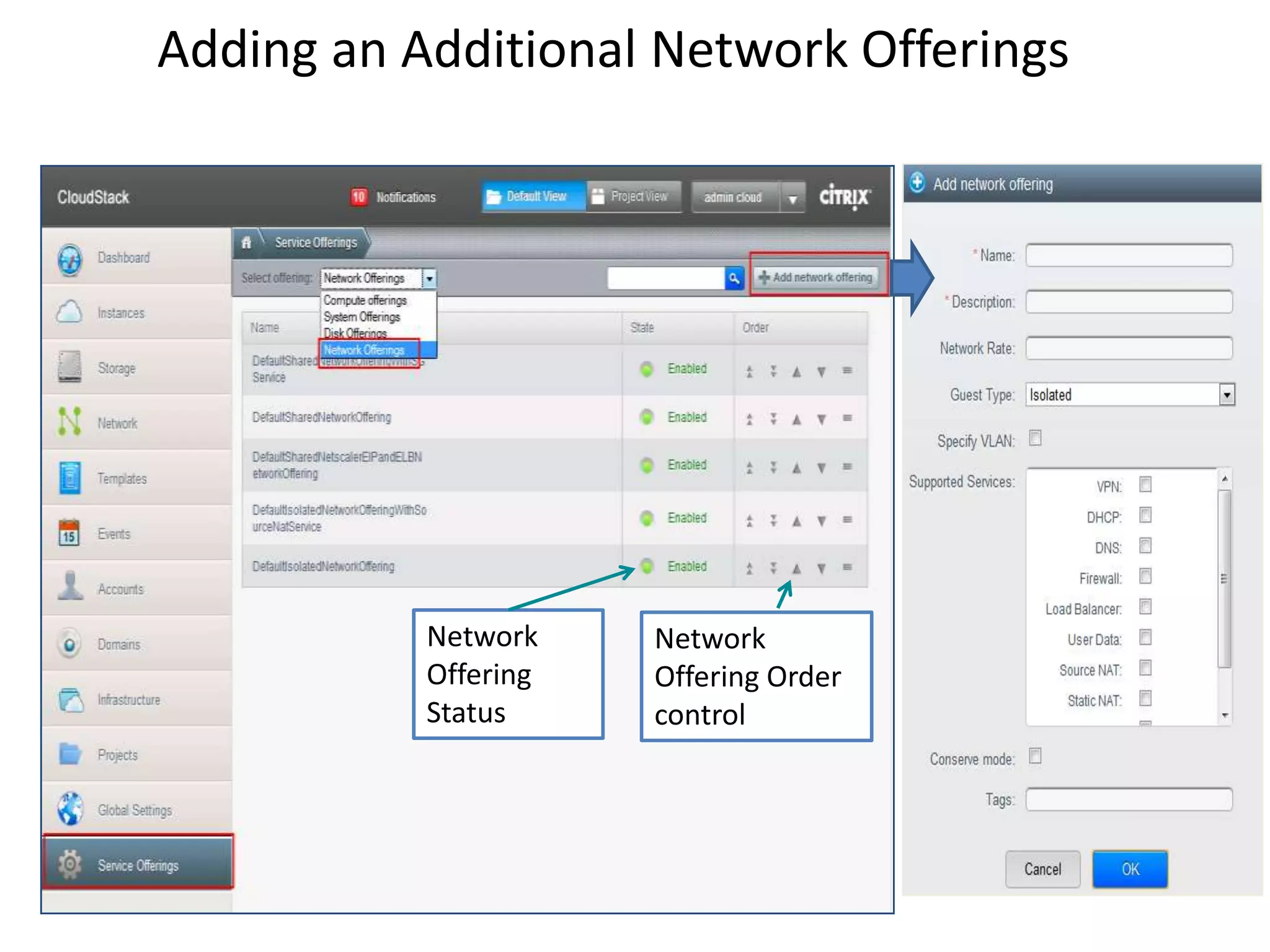
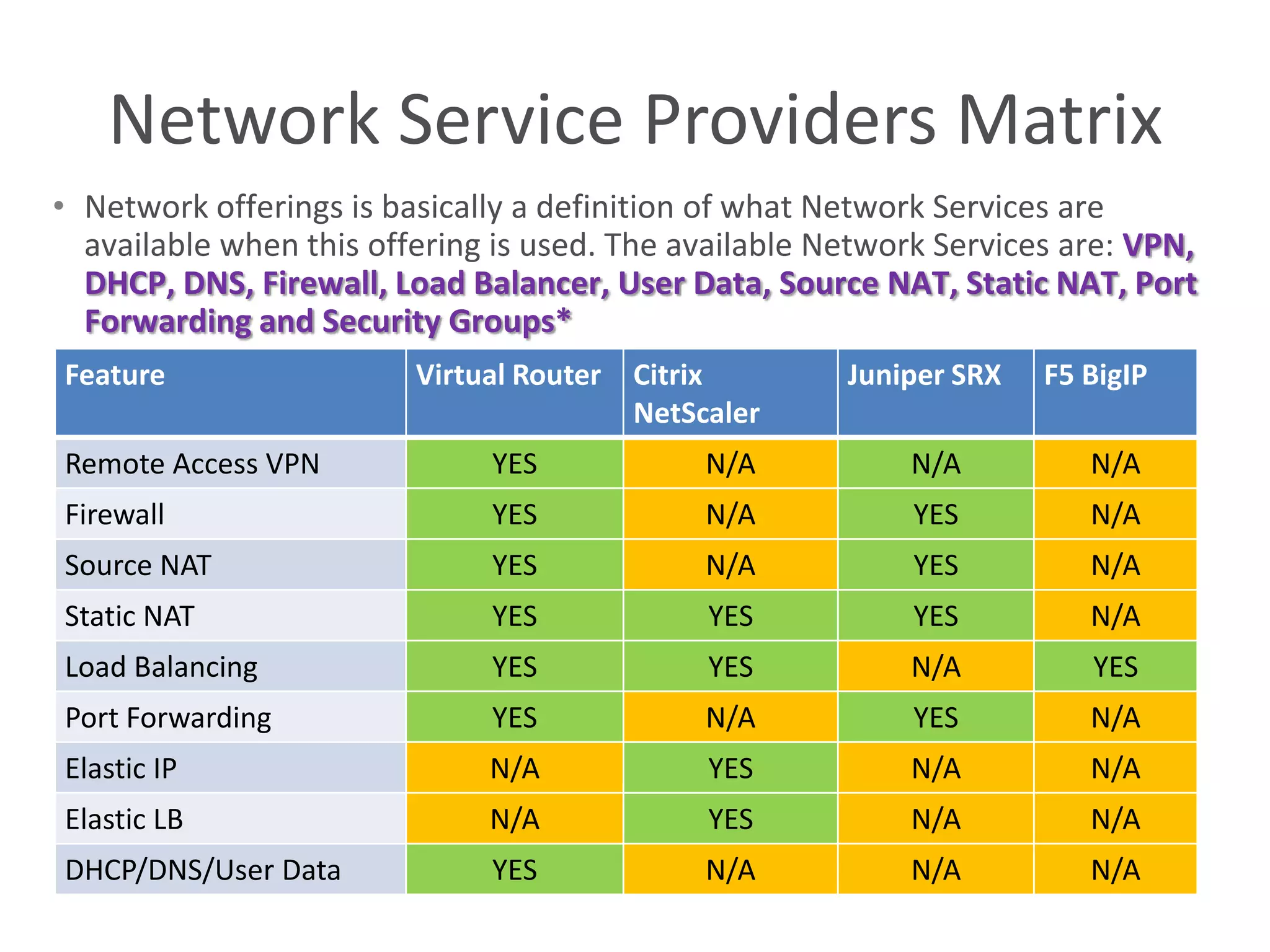
This document summarizes CloudStack networking features and architecture. CloudStack provides orchestration of network services like IPAM, DNS, firewalls, load balancing, and VPN. It supports various network isolation techniques including VLANs, L3 isolation, and overlay networks. The CloudStack virtual router provides default network services, and external devices can also be integrated. CloudStack networking supports advanced configurations including multi-tier networks, bring your own services, and software defined networking.

![Feature overview
• Orchestration of L2 – L7 network services
– IPAM, DNS, Gateway, Firewall, NAT, LB, VPN, etc
• Mix-and-match services and providers
• Out-of-the-box integration with automated deployment of virtual routers
– Highly available network services using CloudStack HA and VRRP
• Orchestrate external providers such as hardware firewalls and load
balancers
– Devices can provide multiple services
– Admin API to configure external devices
– Plugin-based extensions for network behavior and admin API extensions
• Multiple multi-tenancy [network isolation] options
• Integrated traffic accounting
• Access control
• Software Defined Networking too](https://image.slidesharecdn.com/cloudstacknetworkingmay22012-120503001801-phpapp02/75/CloudStack-Networking-3-2048.jpg)
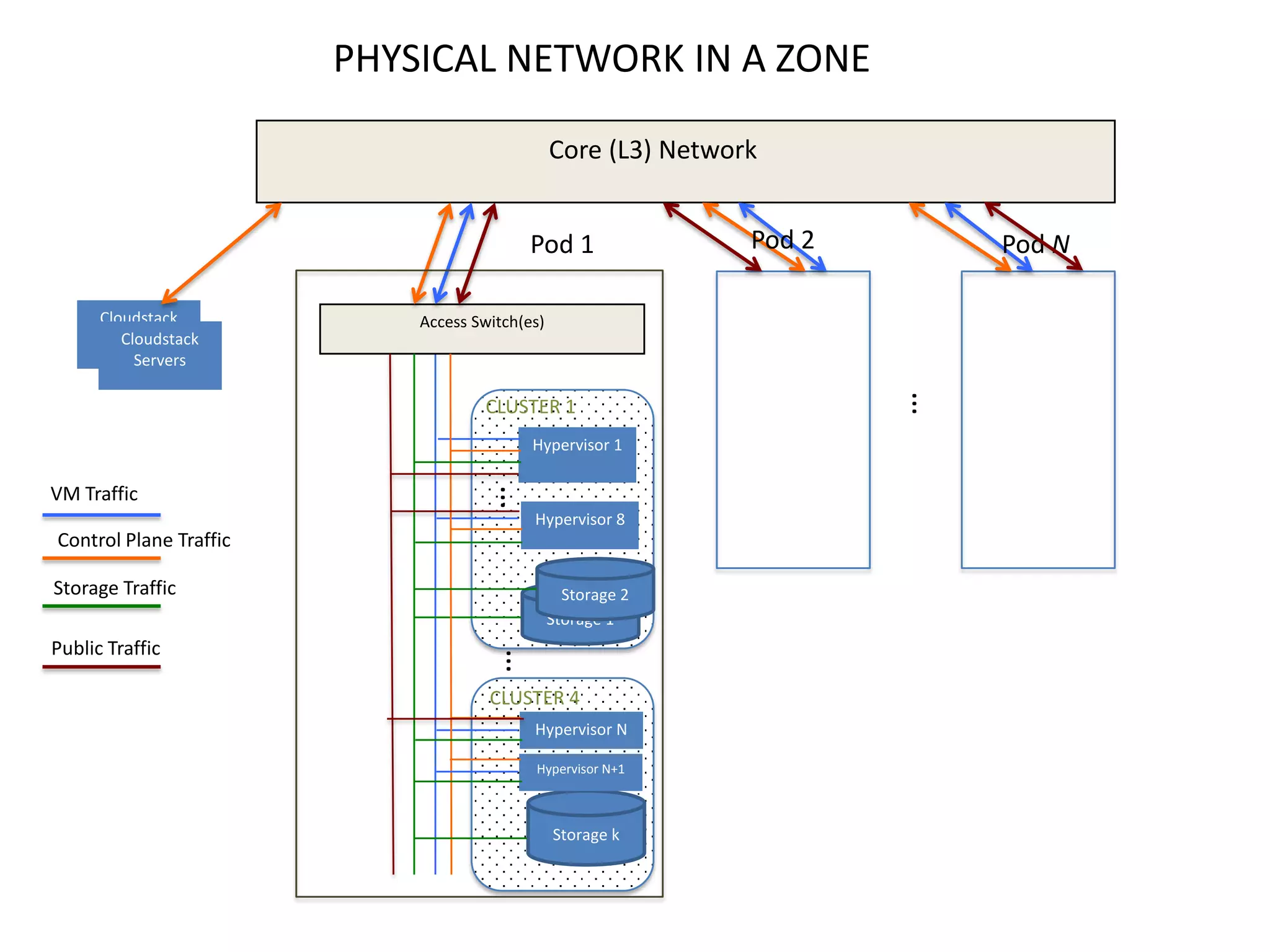
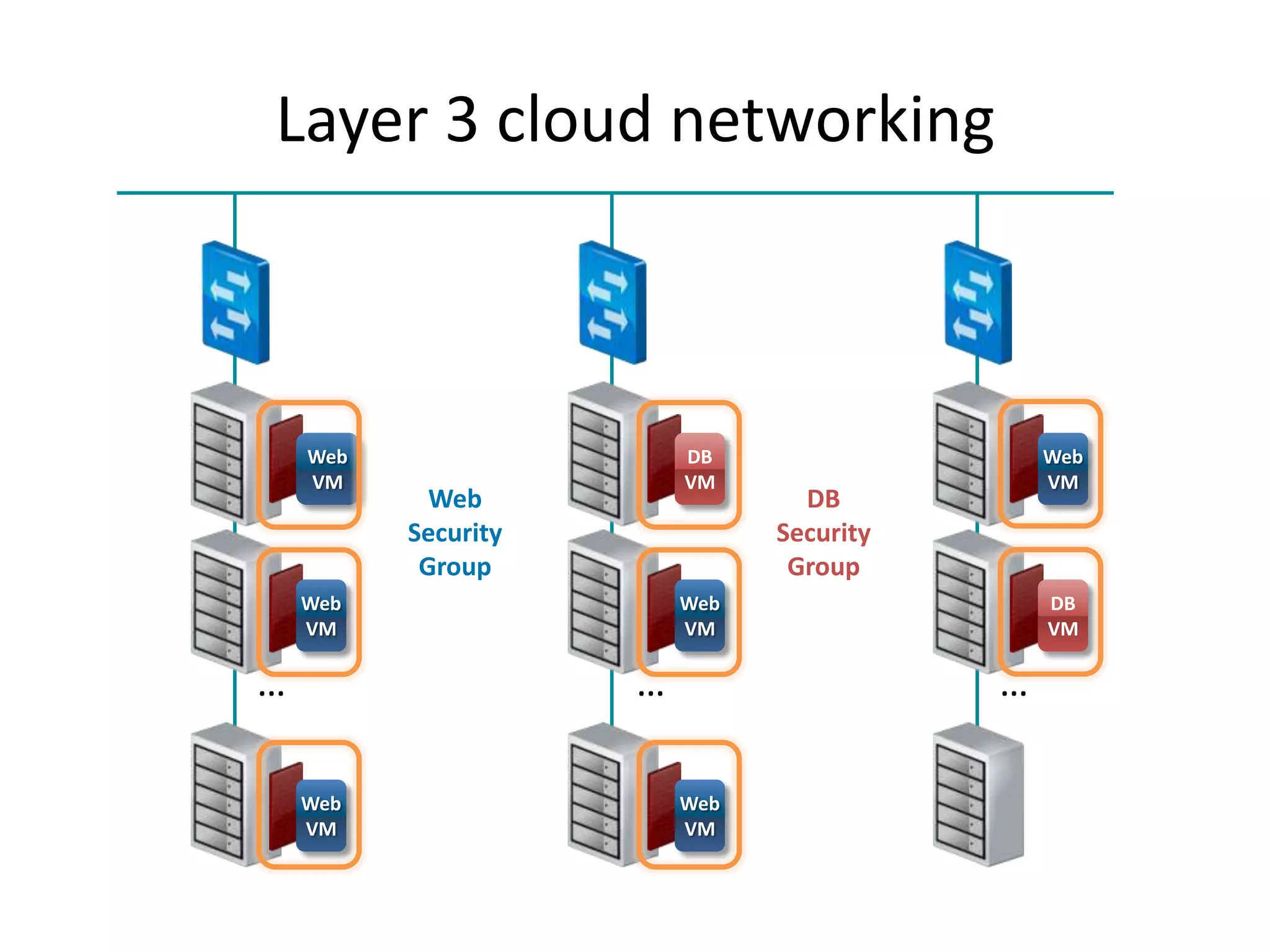
![L2 Features
• Choice of network isolation
– Physical, VLAN, L3 (anti-spoof), Overlay[GRE]
– Physical isolation through network labels [limited to # of nics or bonds]
• Multi-nic
– Deploy instance in multiple networks
– Control default route
• Access control
– Shared networks, project networks
– Dedicated VLANs offer MPLS integration
• Anti-spoofing for L3-isolated networks
• QoS [max rate]
• Traffic monitoring
• Broadcast & multicast suppression in L3-isolated networks
• Hot-plug / detach of nics [upcoming]](https://image.slidesharecdn.com/cloudstacknetworkingmay22012-120503001801-phpapp02/75/CloudStack-Networking-7-2048.jpg)
![L3 Features
• IPAM [DHCP], Public IP address management
– VR acts as DHCP server
– Can request multiple public IPs per tenant
• Gateway (default gateway)
– Redundant VR (using VRRP)
– Inter-subnet routing [upcoming]
– Static routing control [upcoming]
• Remote Access VPN
– L2TP over IPSec using PSK
– Virtual Router only
• Firewall based on source cidr
• Static NAT [1:1]
– Including “Elastic IP” in Basic Zone
• Source NAT
– Per-network, or interface NAT
• Public Traffic usage
– Monitoring on the Virtual Router / External network device
– Integration with sFlow collectors
• Site-to-Site VPN [upcoming]
– IPSec VPN based on VR
• L3 ACLs [upcoming]](https://image.slidesharecdn.com/cloudstacknetworkingmay22012-120503001801-phpapp02/75/CloudStack-Networking-8-2048.jpg)

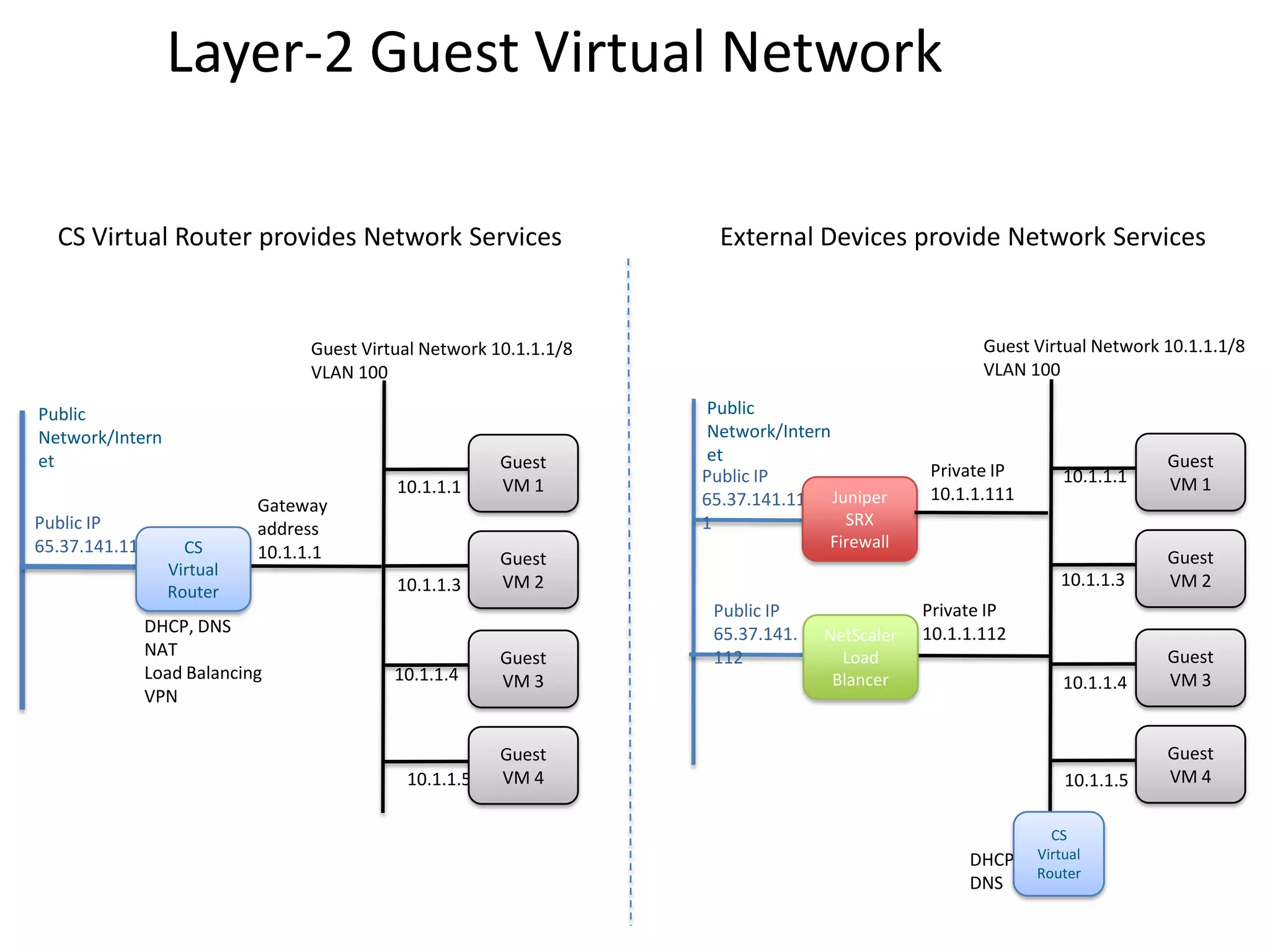
![L7 features
• Loadbalancer
– VR has HAProxy built in
– External Loadbalancer support
• Netscaler (MPX/SDX/VPX)
• F5 BigIP
• Can dedicate an LB appliance to an account or share it among tenants
– Loadbalancer supported with L3-isolation as well
– Stickiness support
– SSL support [future]
– Health Checks [future]
• User-data & meta-data
– Fetched from virtual router
• Password change server](https://image.slidesharecdn.com/cloudstacknetworkingmay22012-120503001801-phpapp02/75/CloudStack-Networking-10-2048.jpg)
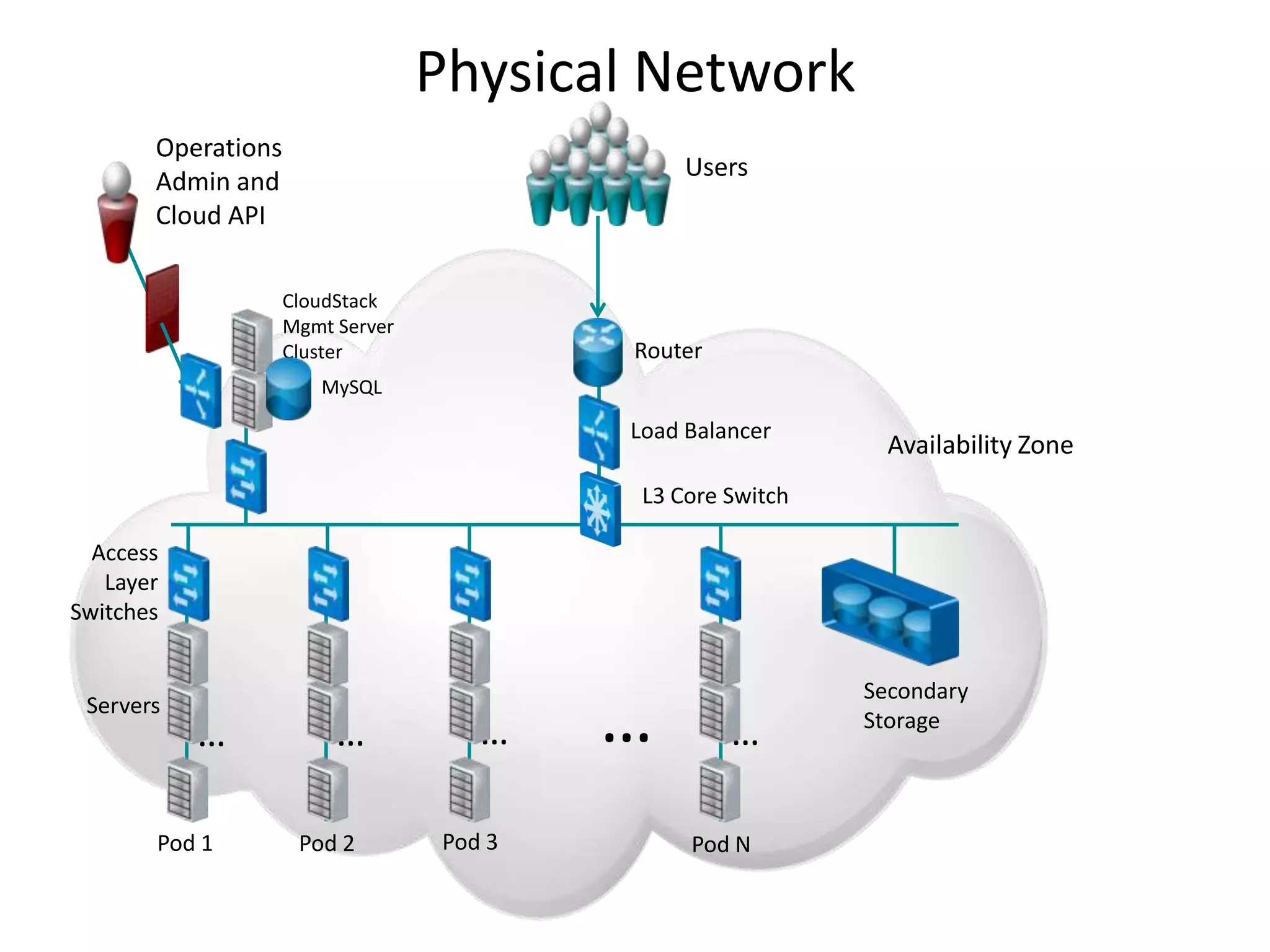
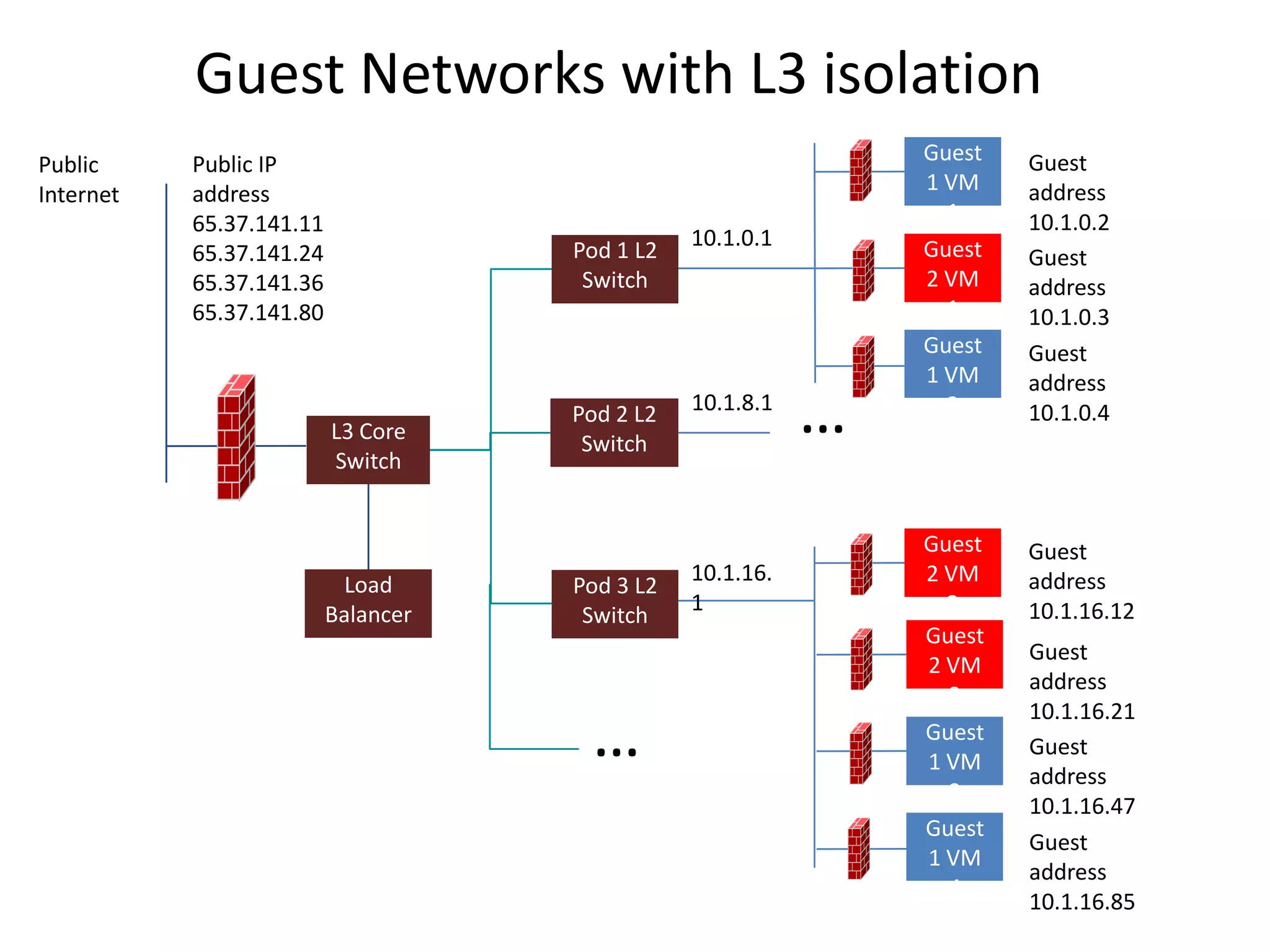
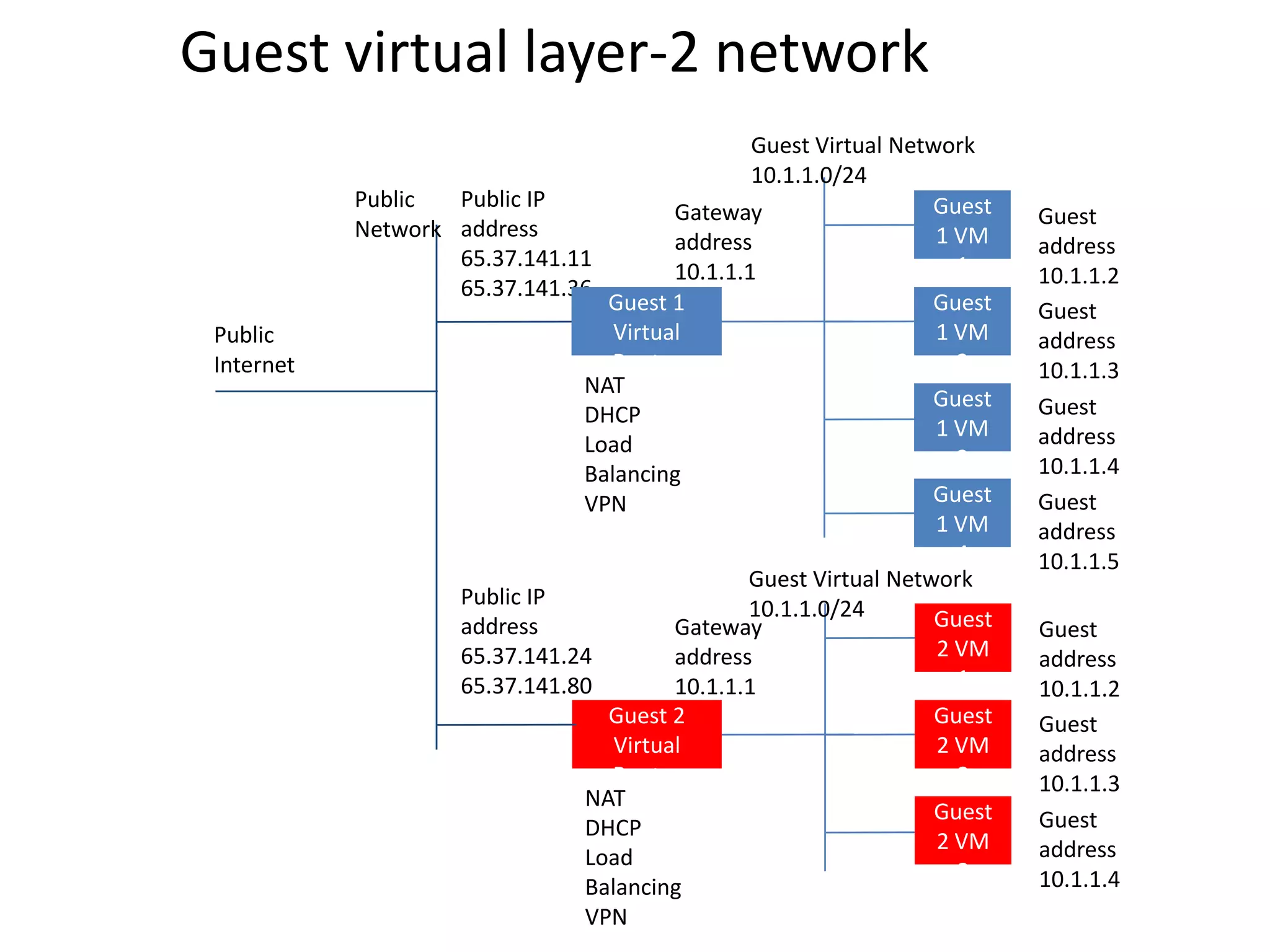
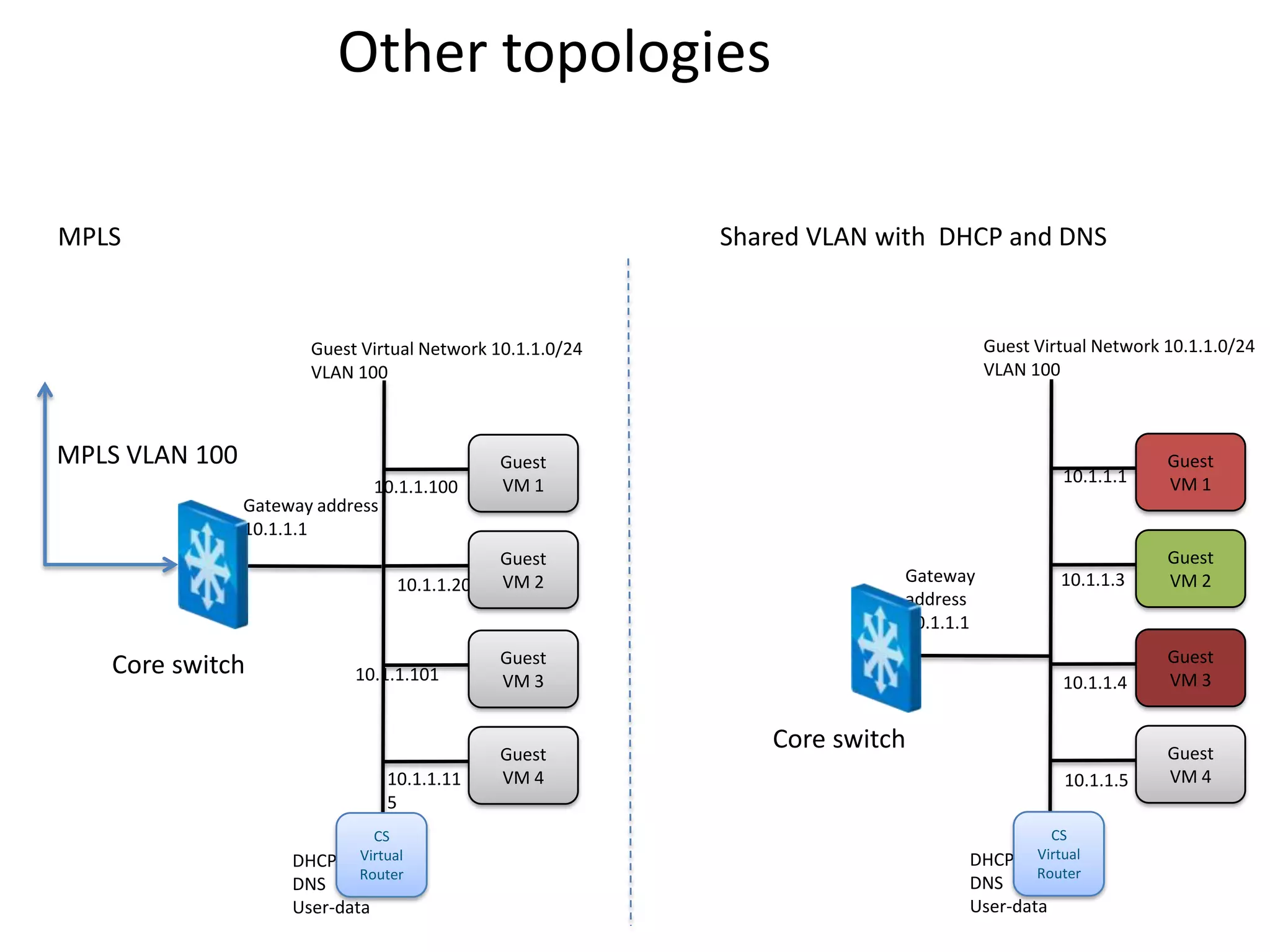
![Other Topologies
No services [Static Ips] Dedicated VLAN with DHCP and DNS
User can request specific IP[s] for NIC
Guest Virtual Network 10.1.1.0/24 Guest Virtual Network 10.1.1.0/24
VLAN 100 VLAN 100
Guest Guest
VM 1 10.1.1.1 VM 1
10.1.1.1
Gateway address
10.1.1.1
Guest Guest
10.1.1.3 VM 2 Gateway 10.1.1.3 VM 2
address
10.1.1.1
Guest Guest
Core switch 10.1.1.4 VM 3 VM 3
10.1.1.4
Guest
Core switch Guest
10.1.1.5 VM 4 10.1.1.5 VM 4
CS
DHCP, Virtual
Router
DNS
User-data](https://image.slidesharecdn.com/cloudstacknetworkingmay22012-120503001801-phpapp02/75/CloudStack-Networking-17-2048.jpg)
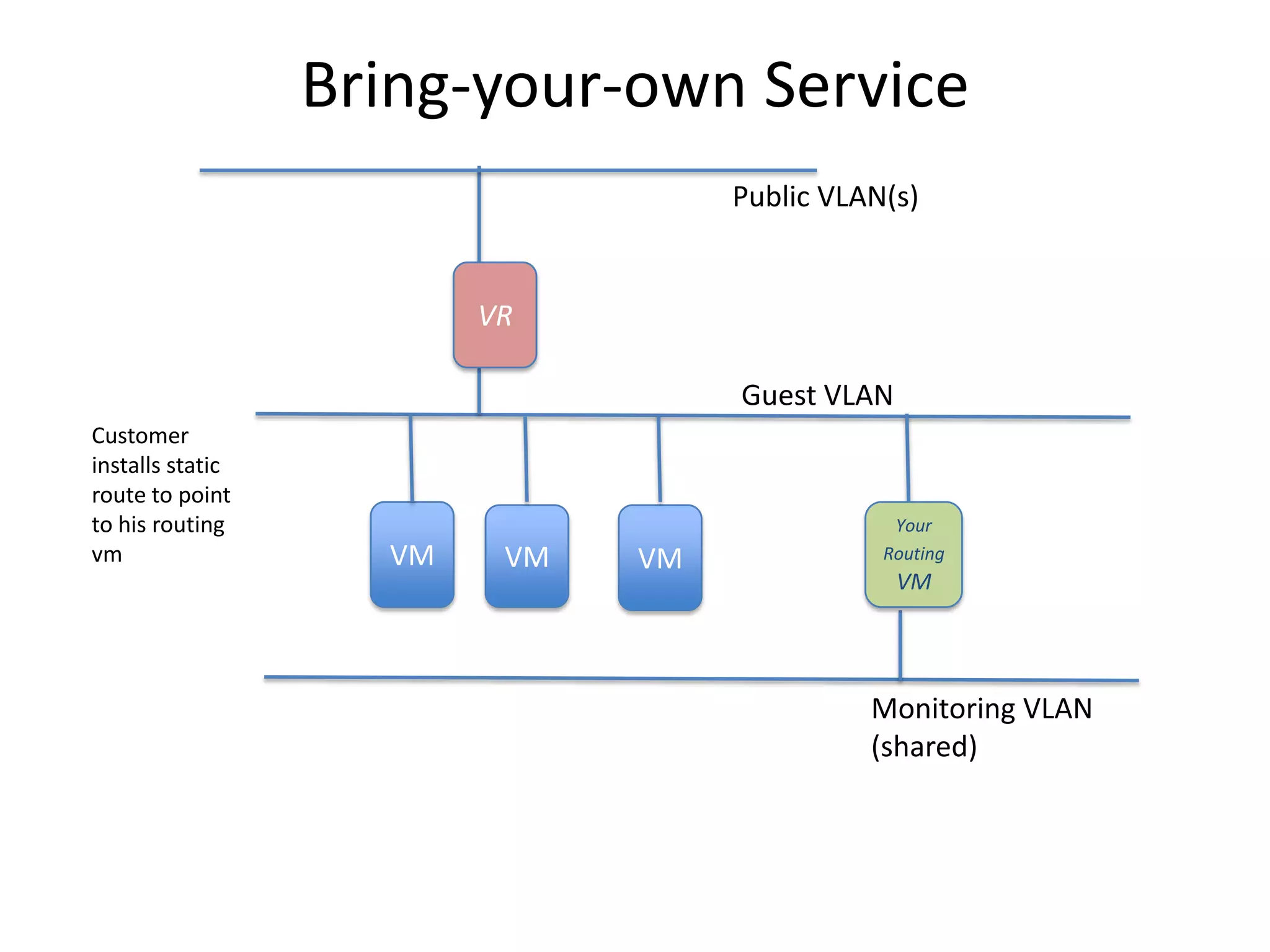
![Bring-your-own Service[site-to-site-vpn]
Public VLAN(s)
VR
Guest VLAN
Customer
installs static
route
(manually/au Your
tomated VM VM VM Routing
config) to VM
point to his
routing vm.
Routing VM
provides Site- Shared Public VLAN
to-site VPN
(configured
directly on
routing VM,
not by
CloudStack)](https://image.slidesharecdn.com/cloudstacknetworkingmay22012-120503001801-phpapp02/75/CloudStack-Networking-21-2048.jpg)
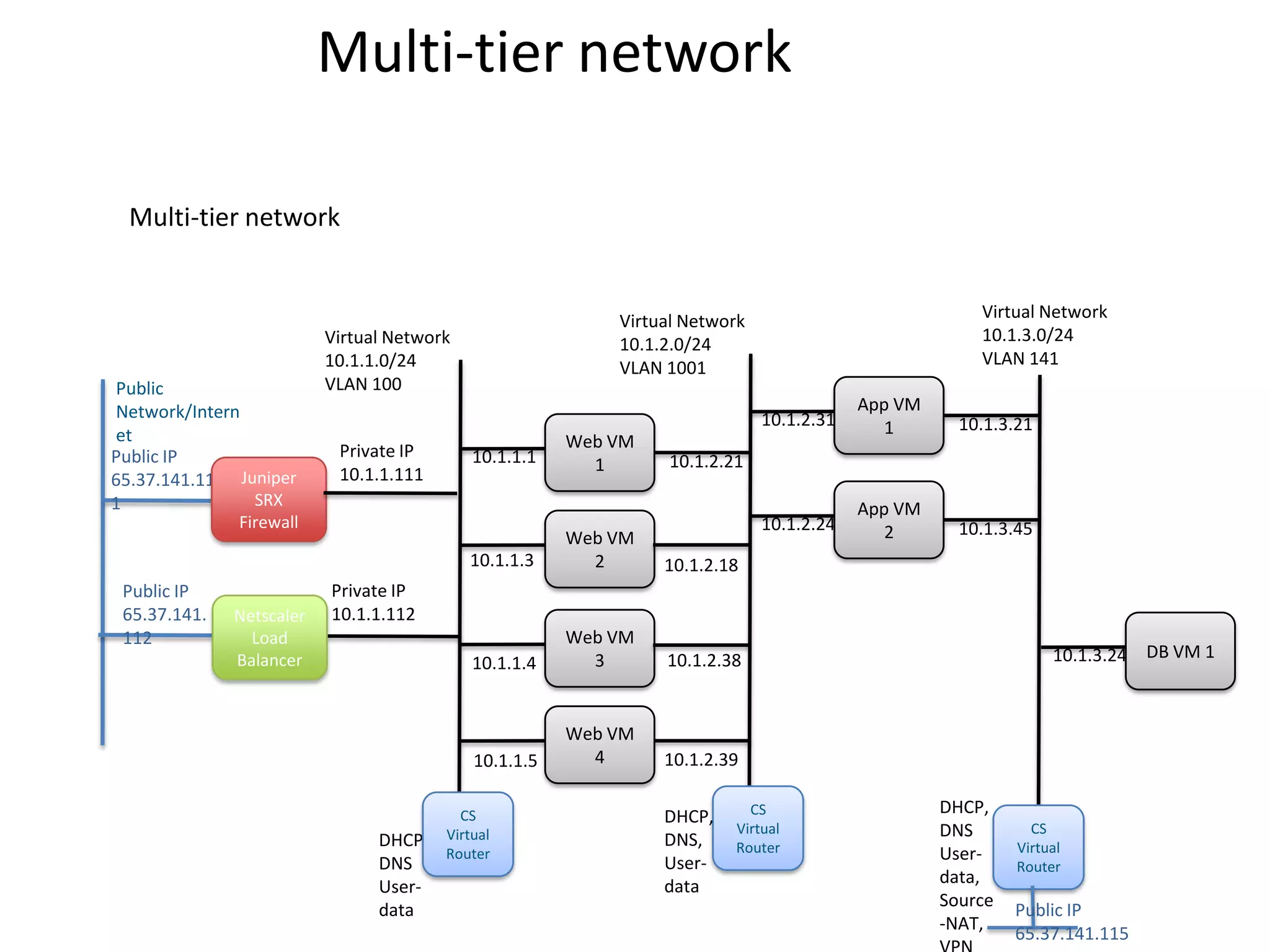
![Multi-tier unified [vision]
Internet
IPSec or SSL site-to-site VPN
CS
Virtual Router / Customer
Loadbalancer Other Premises
Monitoring VLAN
Virtual Router Services
App VM
• IPAM 10.1.2.31 1
• DNS 10.1.1.1
Web VM
1
• LB [intra]
• S-2-S VPN App VM
10.1.2.24
• Static Routes Web VM 2
• ACLs 10.1.1.3 2
• NAT, PF
• FW [ingress & egress]
Web VM
• BGP 10.1.1.4 3 10.1.3.24 DB VM 1
Web VM
10.1.1.5 4
Virtual Network Virtual Network Virtual Network
10.1.1.0/24 10.1.2.0/24 10.1.3.0/24
VLAN 100 VLAN 1001 VLAN 141](https://image.slidesharecdn.com/cloudstacknetworkingmay22012-120503001801-phpapp02/75/CloudStack-Networking-22-2048.jpg)
![Multi-tier unified with SDN[vision]
Internet
IPSec or SSL site-to-site VPN
CS
Loadbalancer Virtual Router / Customer
Other Premises
Virtual Appliance
Monitoring VLAN
Virtual Router Services
App VM
• IPAM 10.1.2.31 1
• DNS 10.1.1.1
Web VM
1
• LB [intra]
• S-2-S VPN App VM
10.1.2.24
• Static Routes Web VM 2
• ACLs 10.1.1.3 2
• NAT, PF
• FW [ingress & egress]
Web VM
• BGP 10.1.1.4 3 10.1.3.24 DB VM 1
Web VM
10.1.1.5 4
Overlay Overlay Overlay
Network Network Network
10.1.1.0/24 10.1.2.0/24 10.1.3.0/24](https://image.slidesharecdn.com/cloudstacknetworkingmay22012-120503001801-phpapp02/75/CloudStack-Networking-23-2048.jpg)
![CloudStack User APIs [sample]
• Networks (L2)
– createNetwork [requires network offering id],
– deleteNetwork (A), listNetworks,
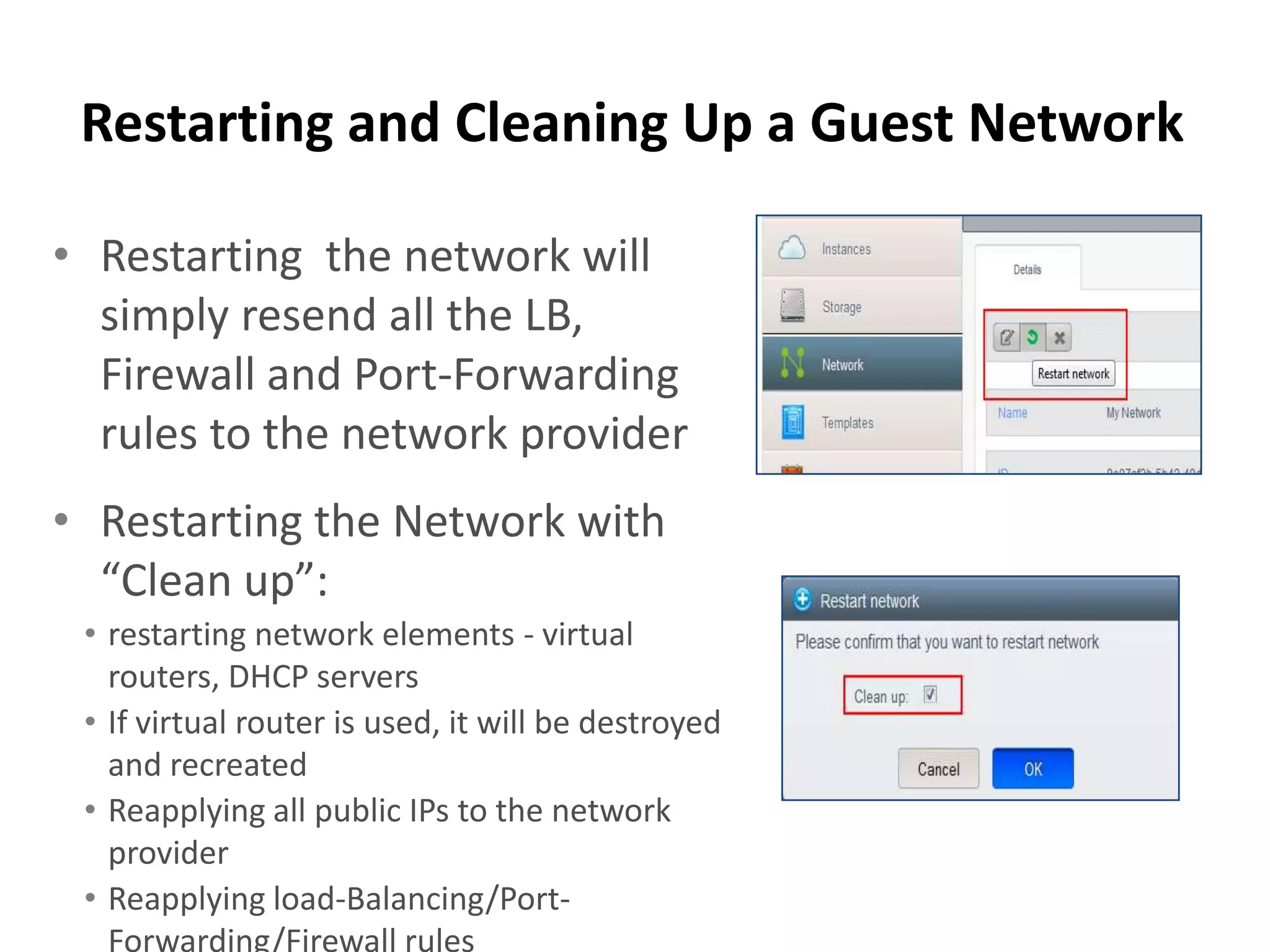
– restartNetwork (A): restarts all devices (if allowed)
supporting the network and re-applies
configuration
– updateNetwork: update network offering and
restart network](https://image.slidesharecdn.com/cloudstacknetworkingmay22012-120503001801-phpapp02/75/CloudStack-Networking-29-2048.jpg)