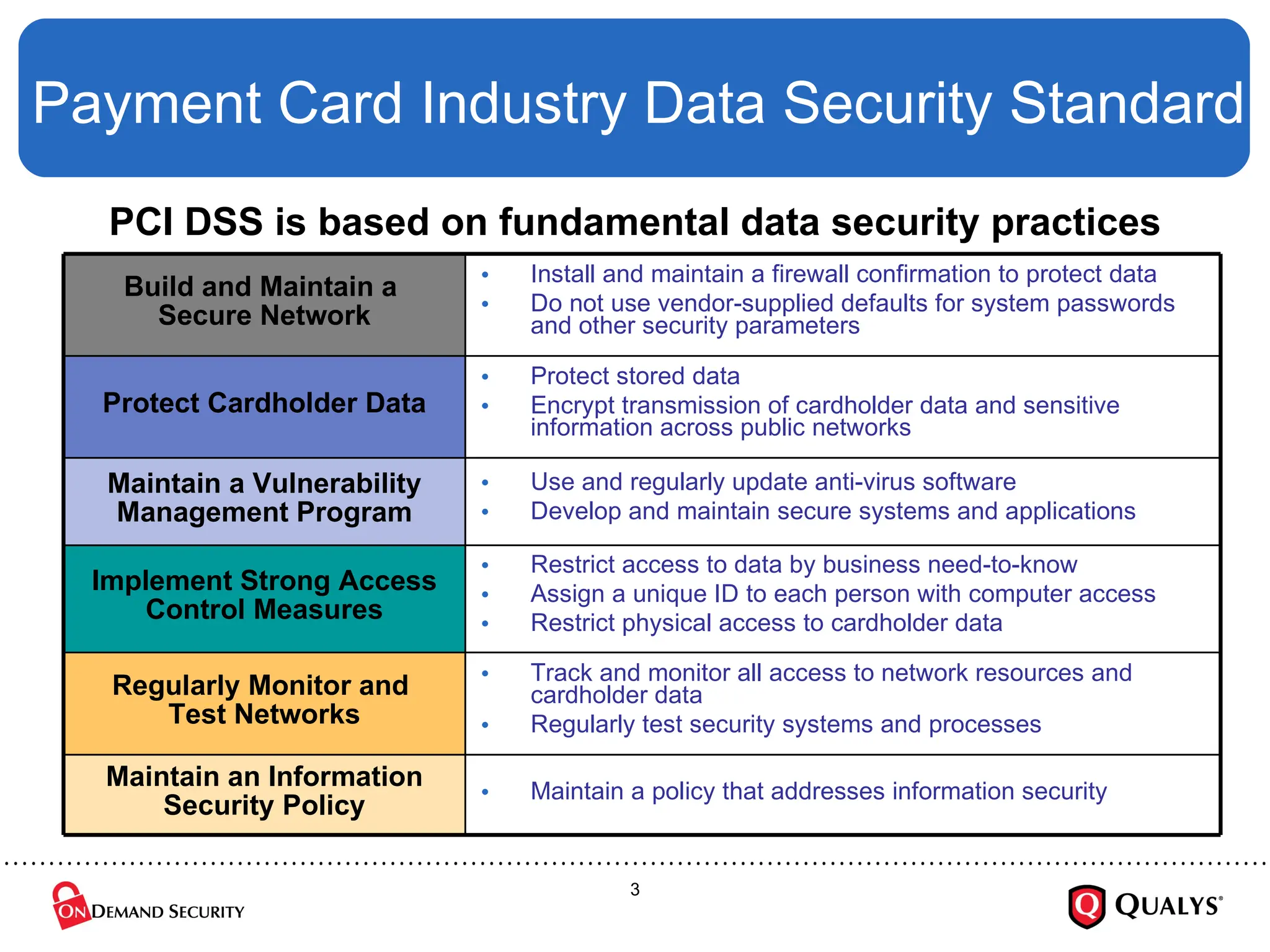
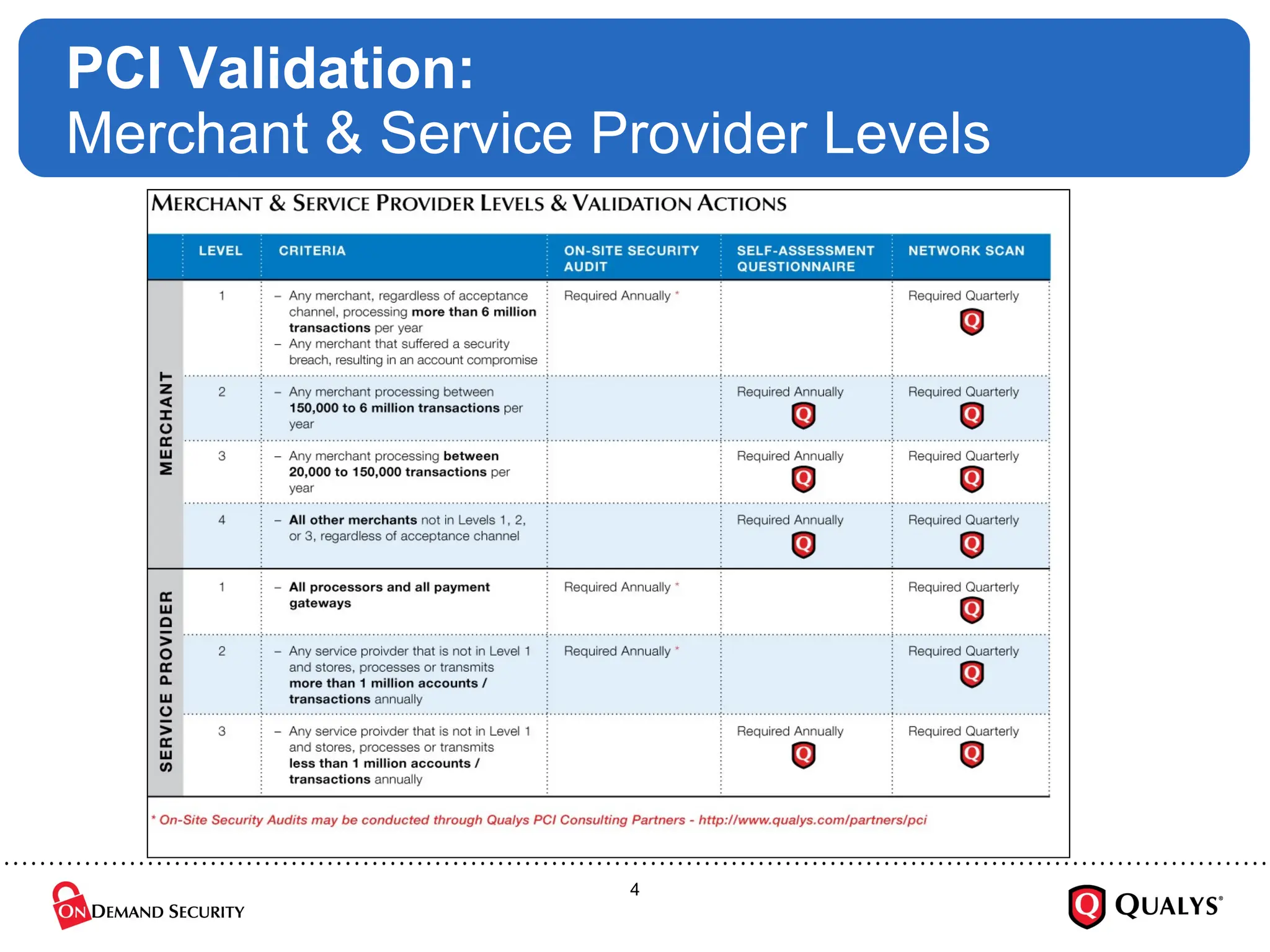
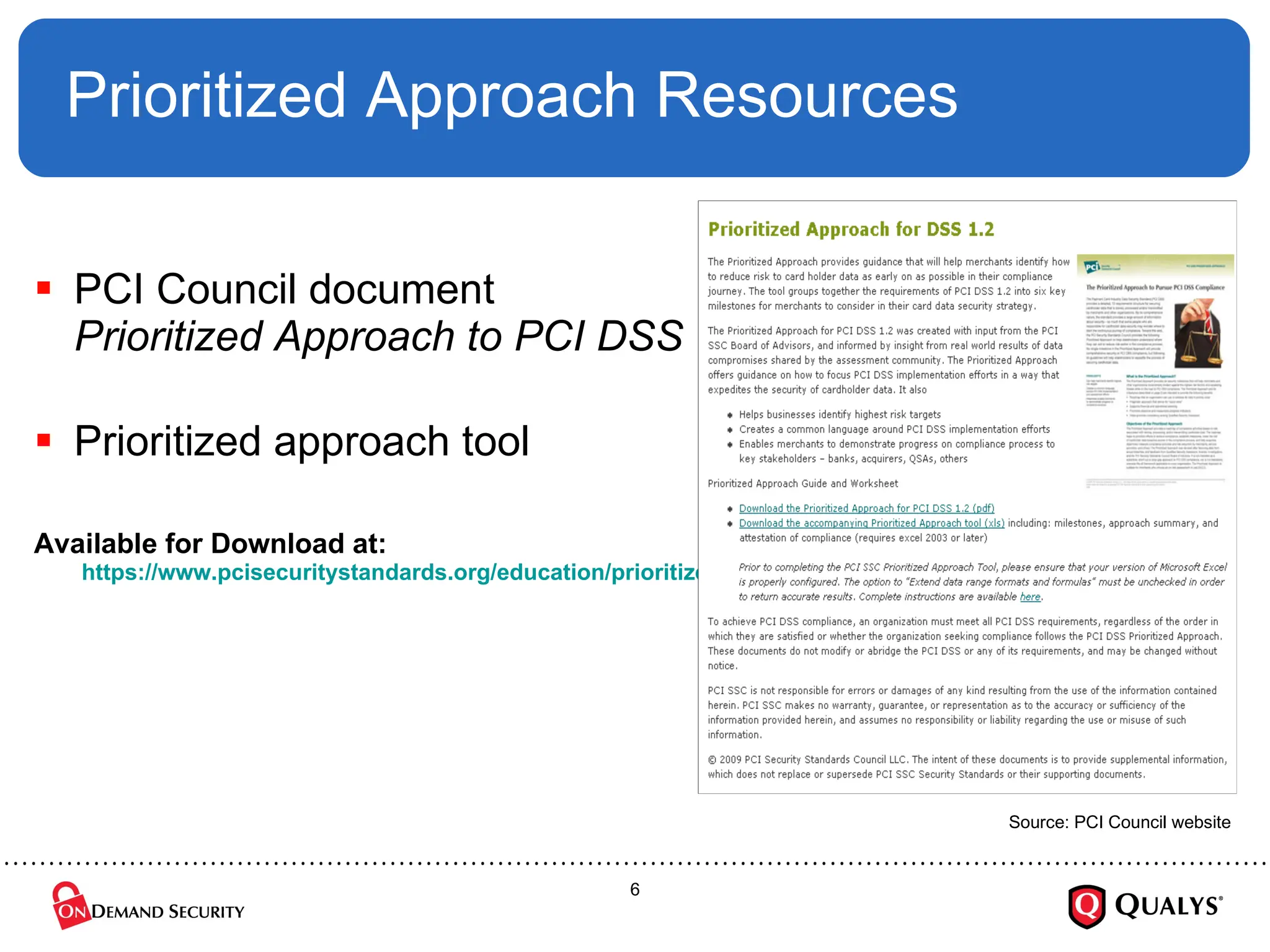
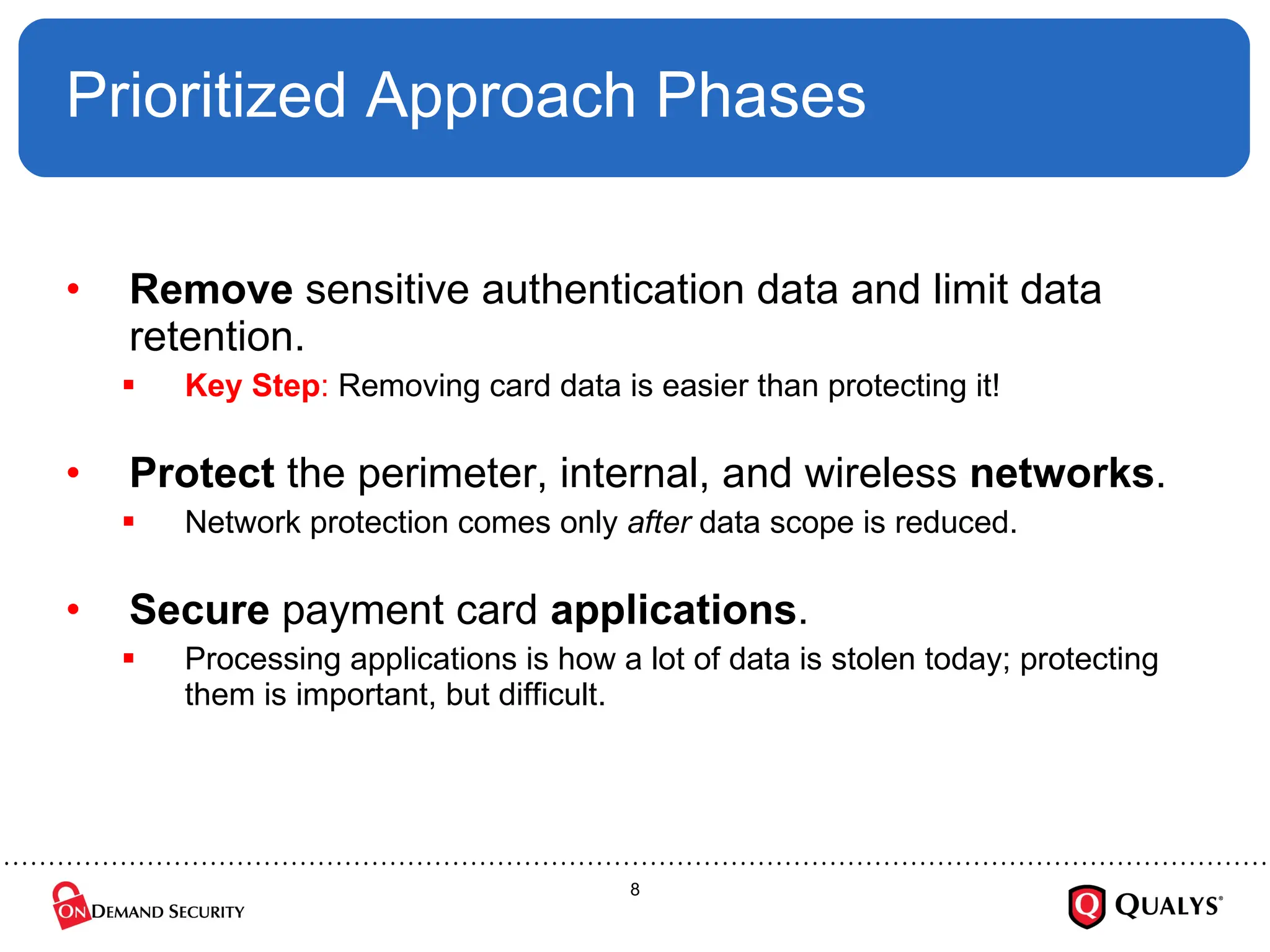
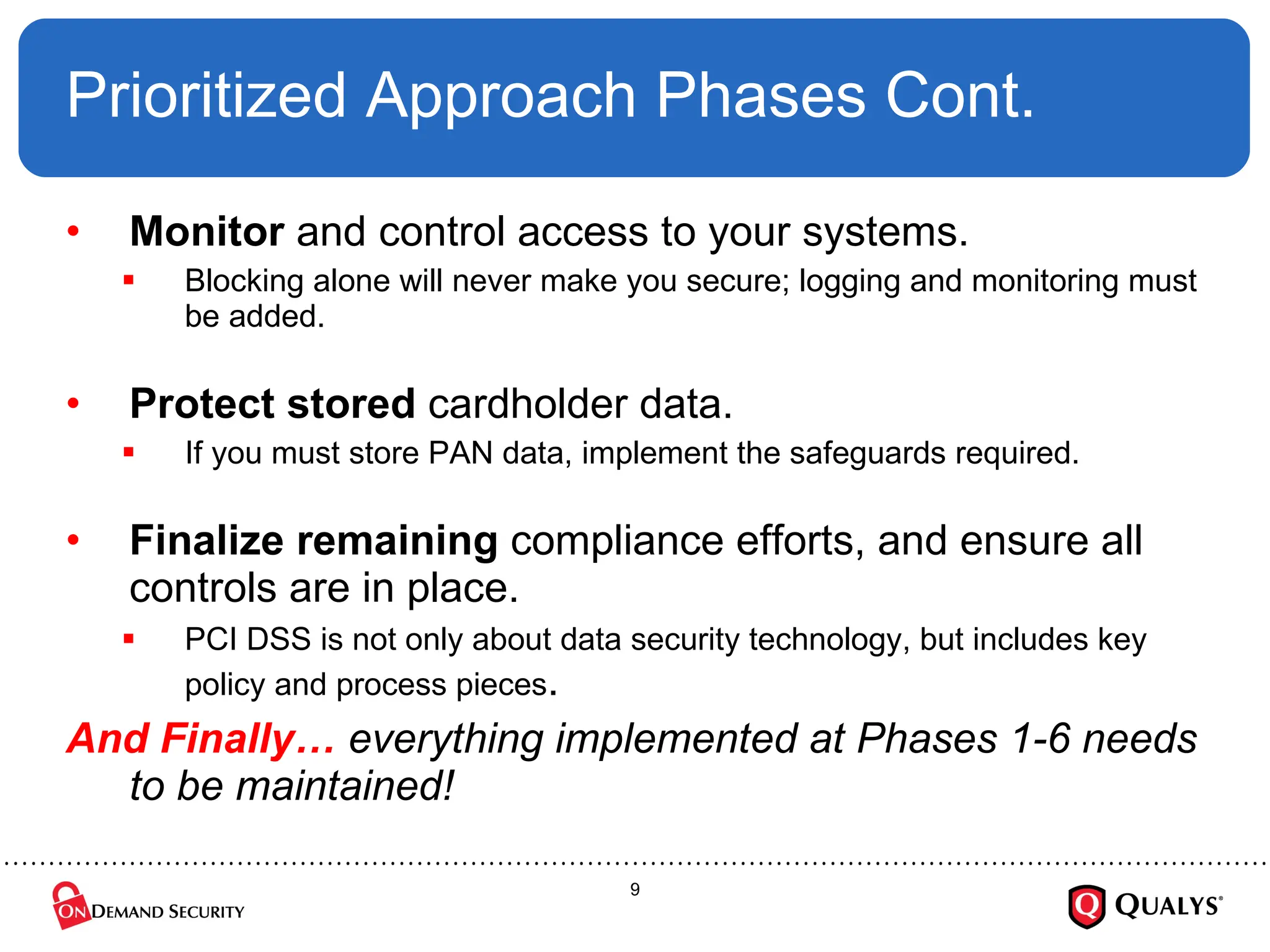
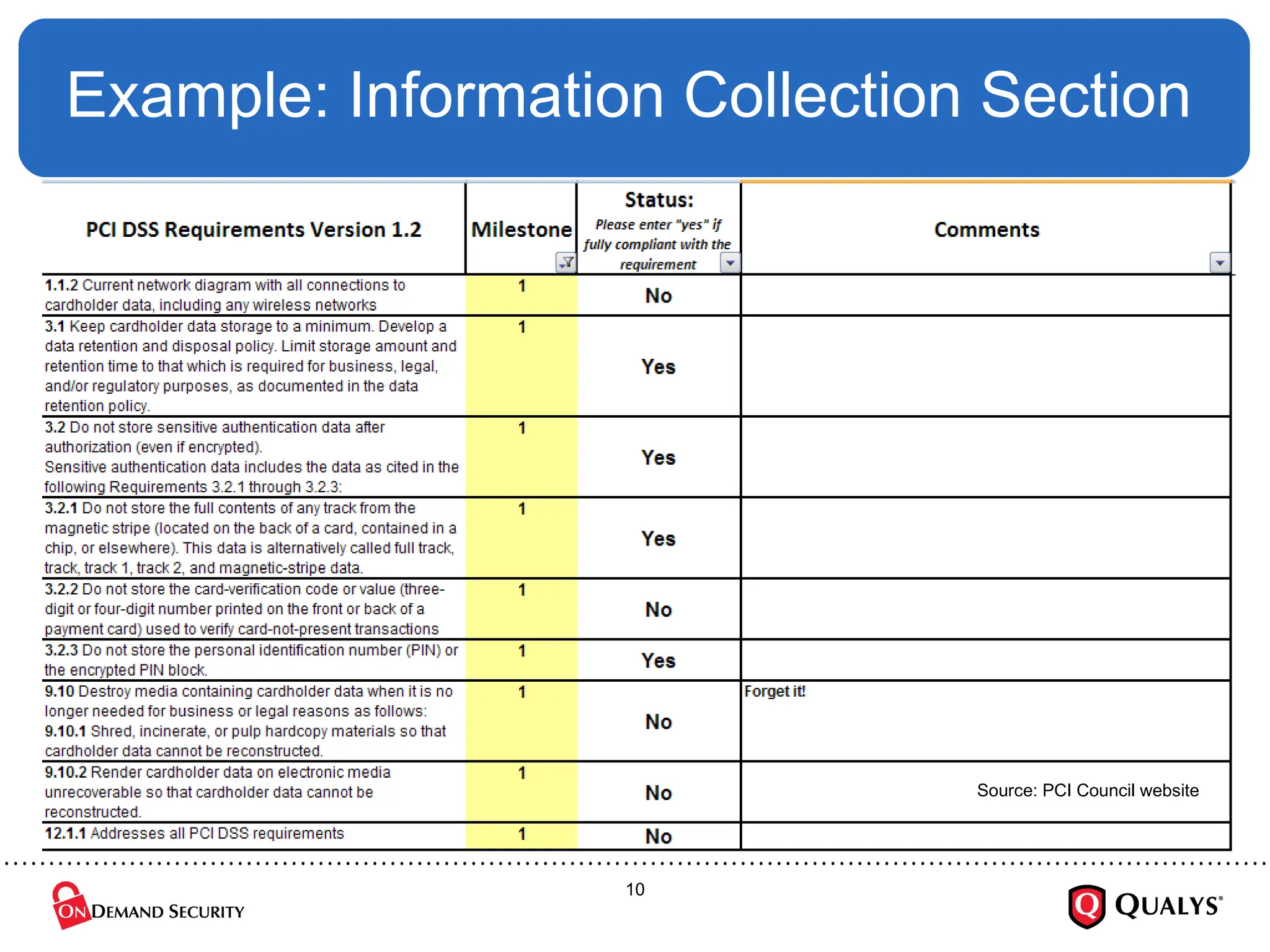
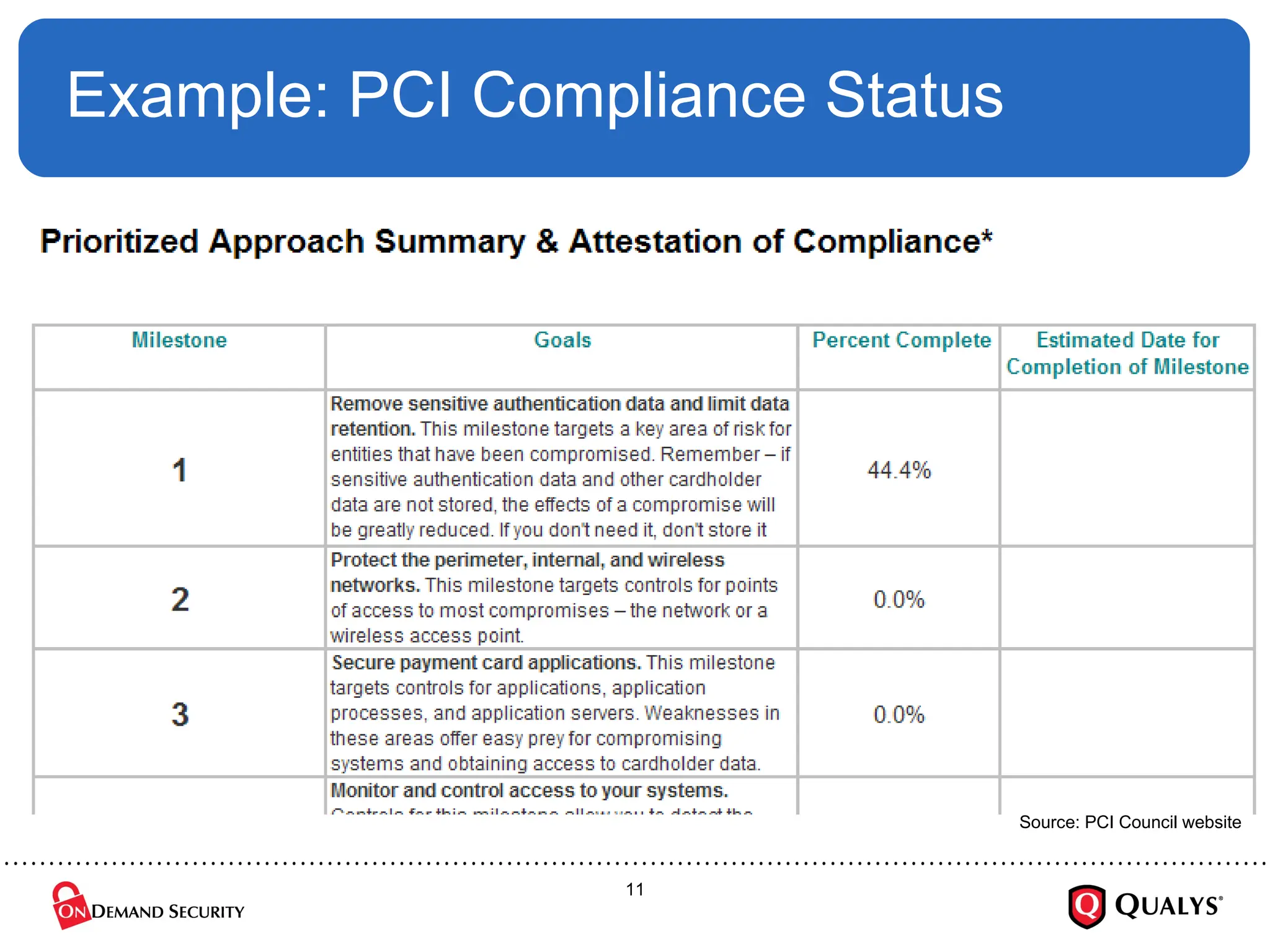
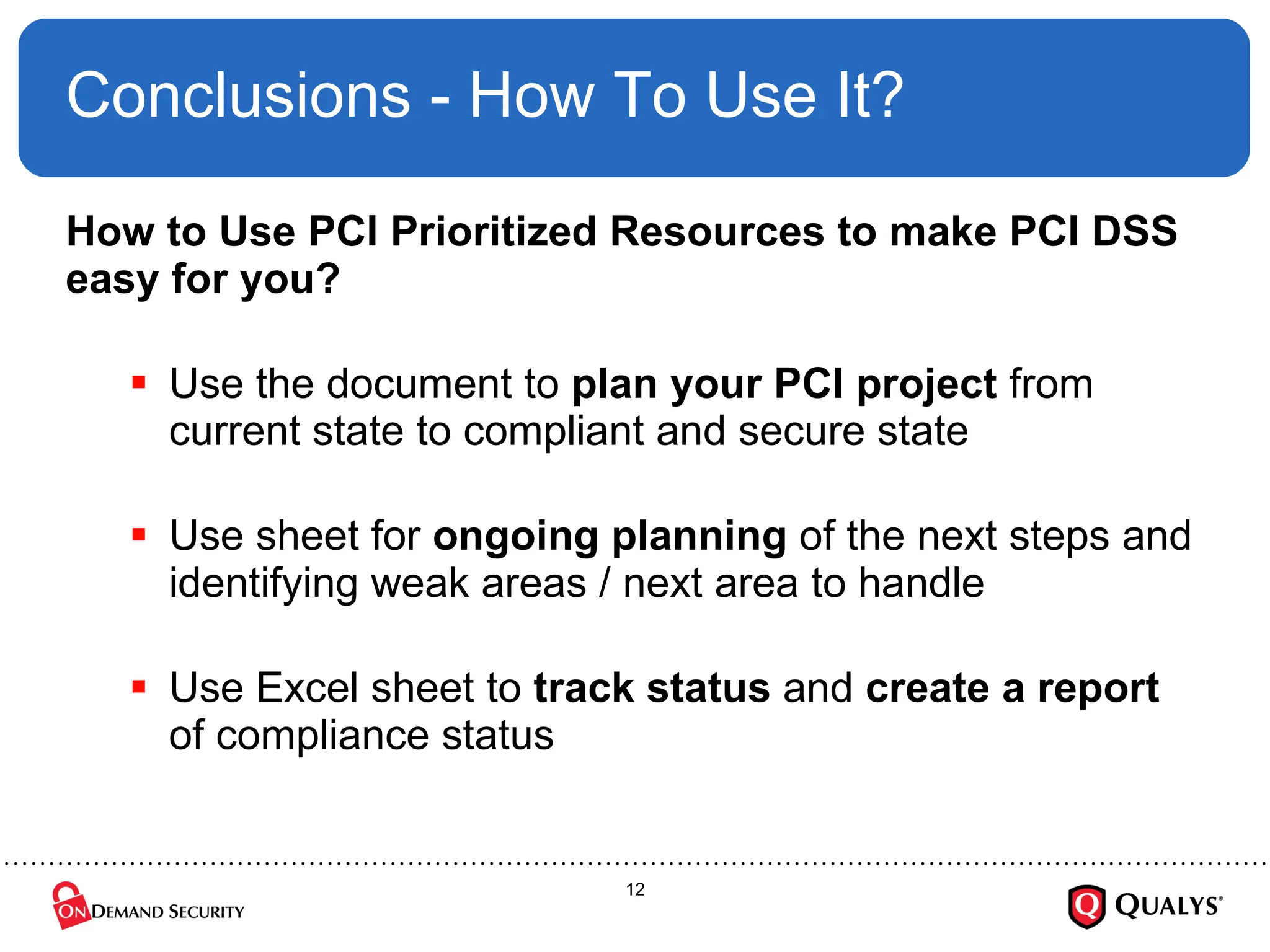
Using the recently released PCI Council “Prioritized Approach” guidance, this briefing will discuss how organizations can effectively focus their PCI DSS implementation efforts in order to ensure the security of cardholder data, reduce information risk and protect the organization --- all while on the shortest path towards PCI DSS validation. The session will also cover how to use the new guidance to save time and money on compliance projects as well as how decide where to start with PCI DSS.
There will be a Q&A session at the end of the briefing - which will then be posted on http://chuvakin.blogspot.com