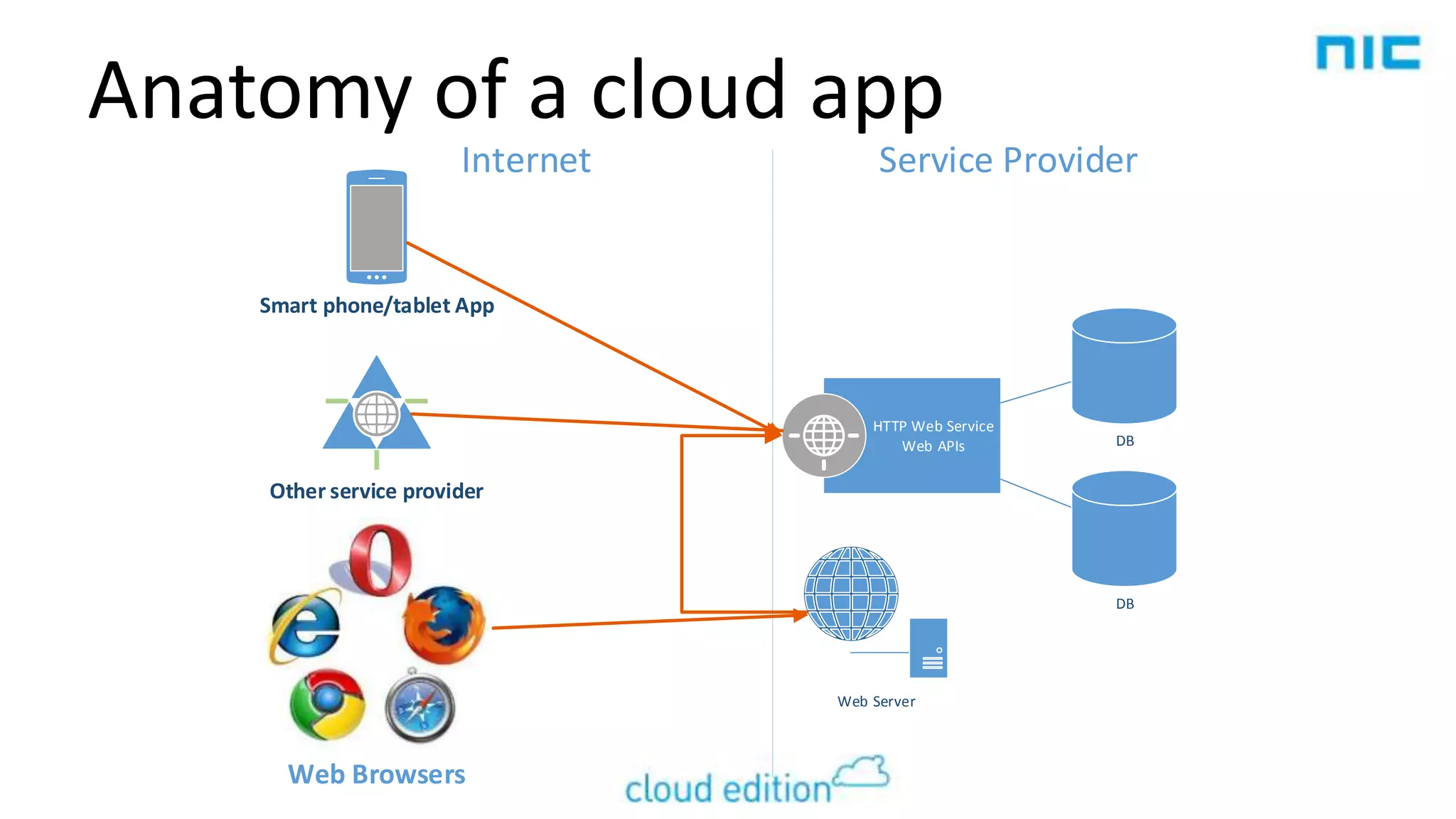
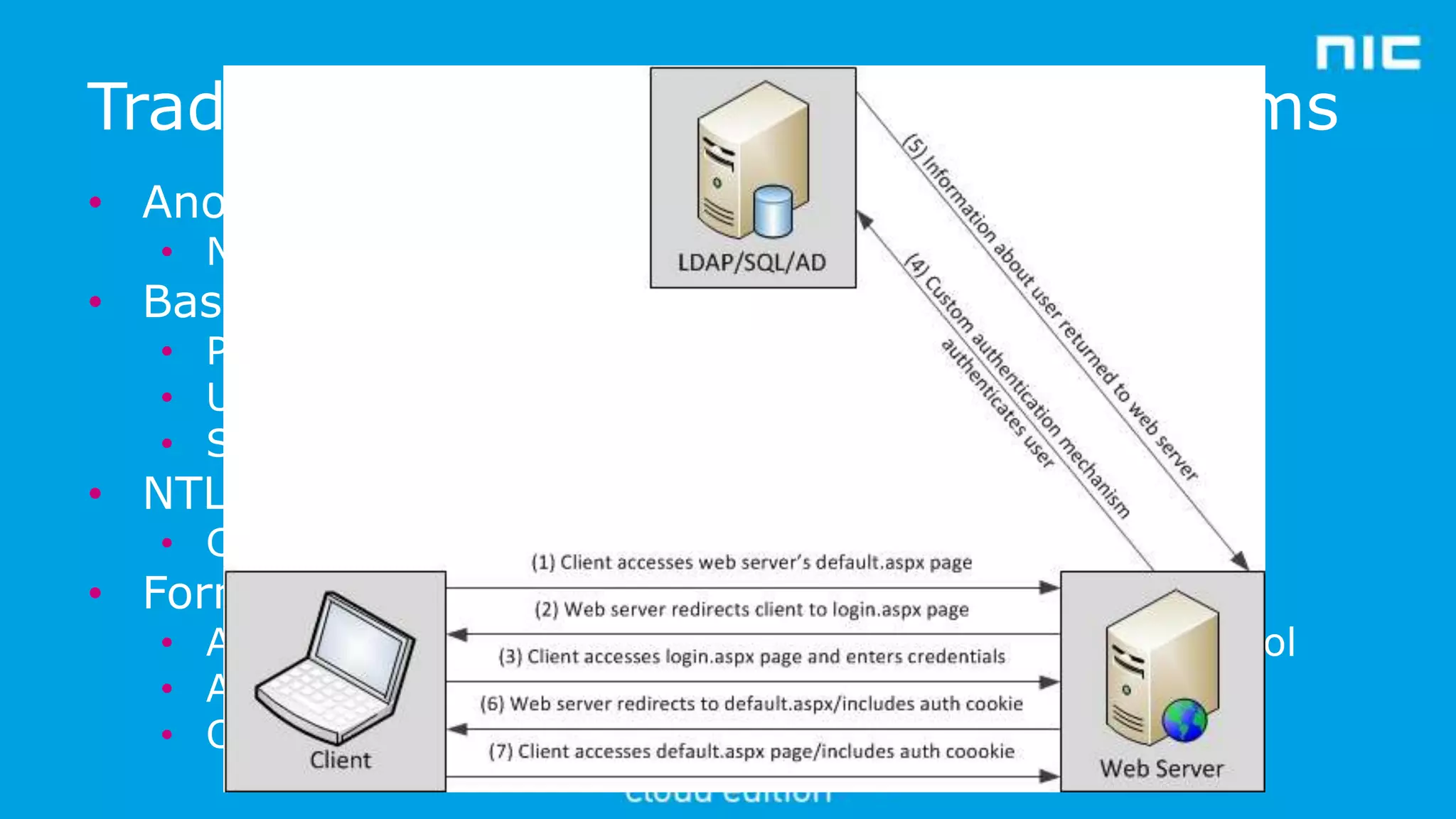
1. The document provides an introduction to modern authentication methods for cloud applications, focusing on claims-based identity.
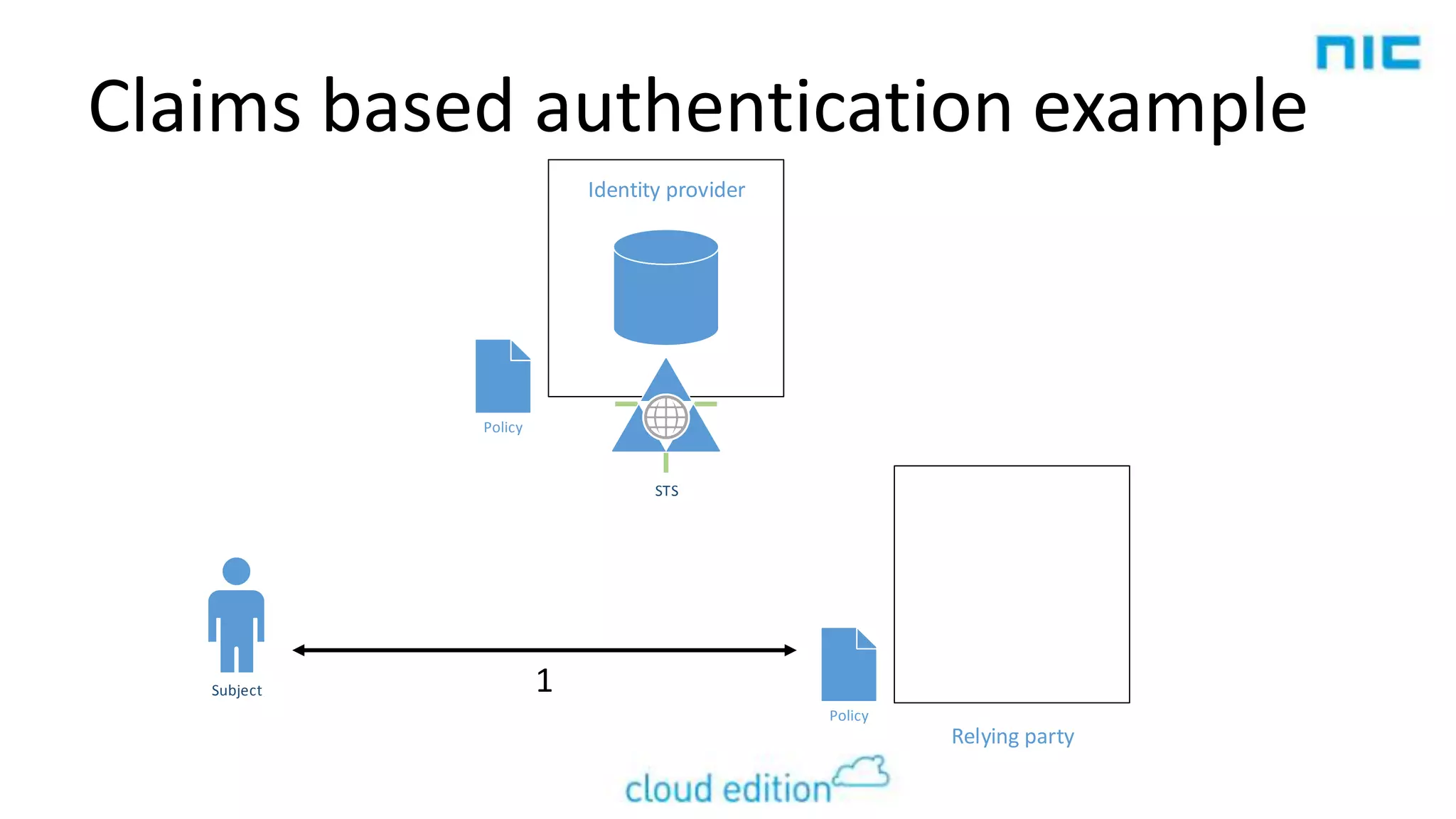
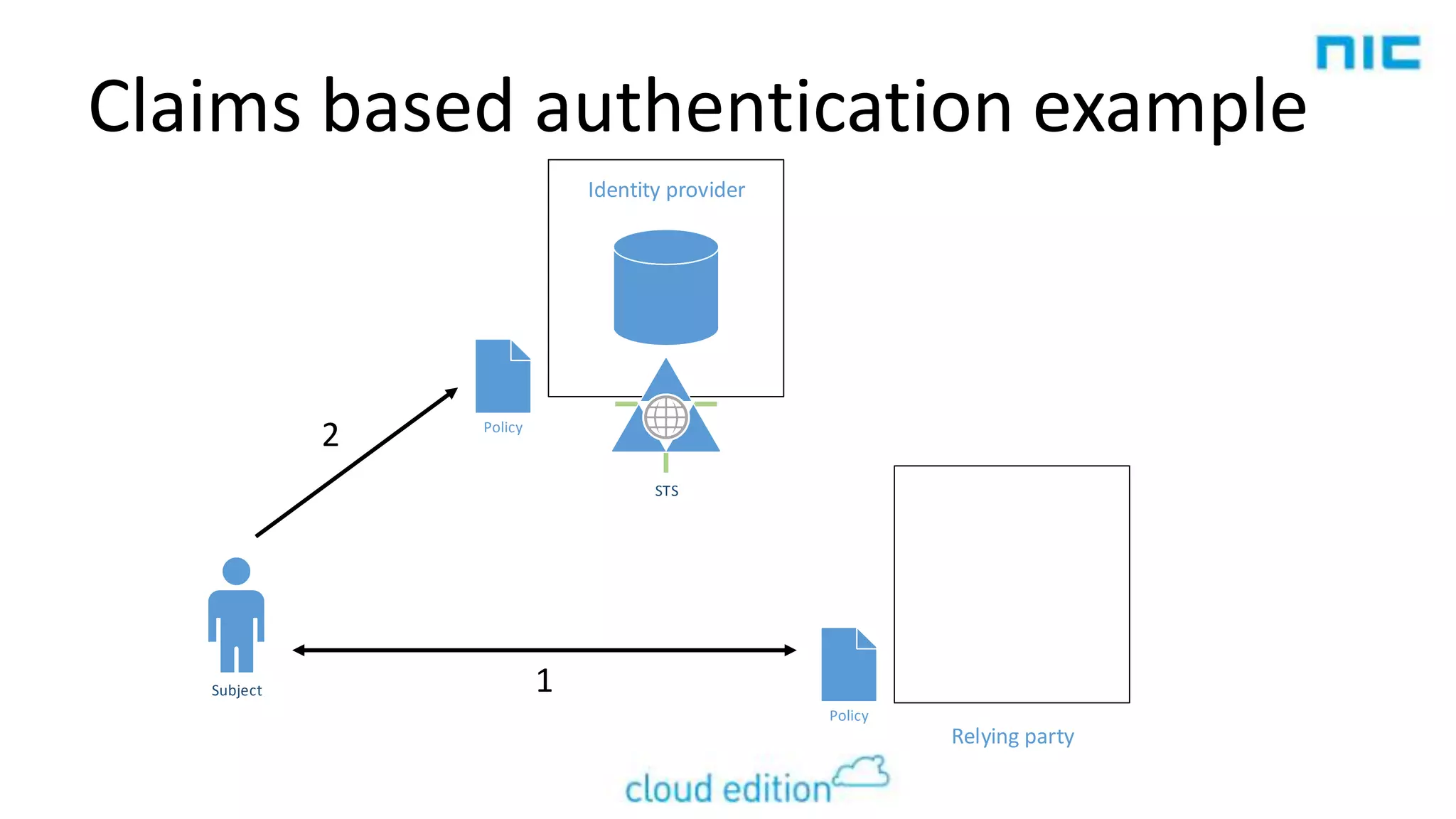
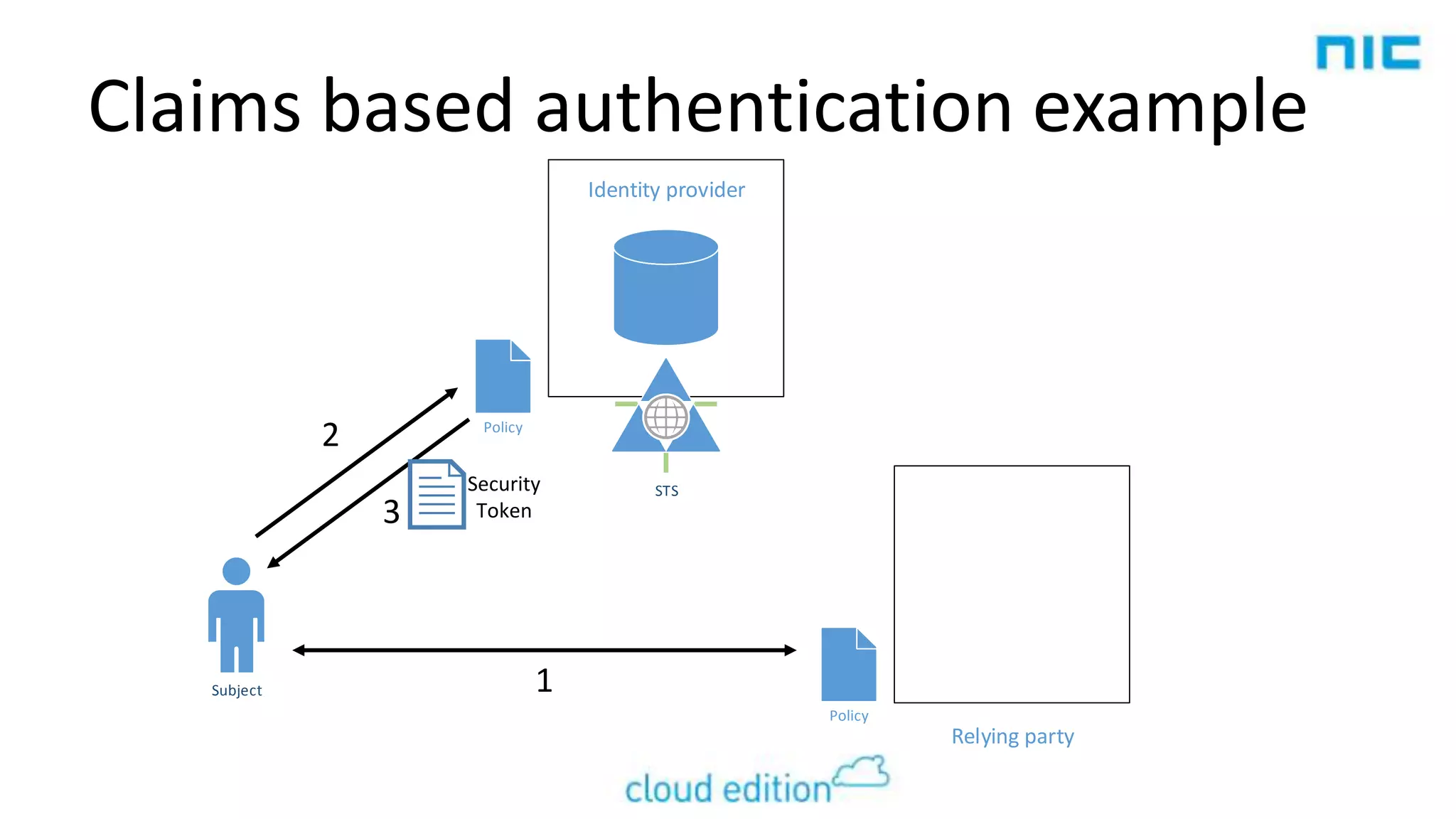
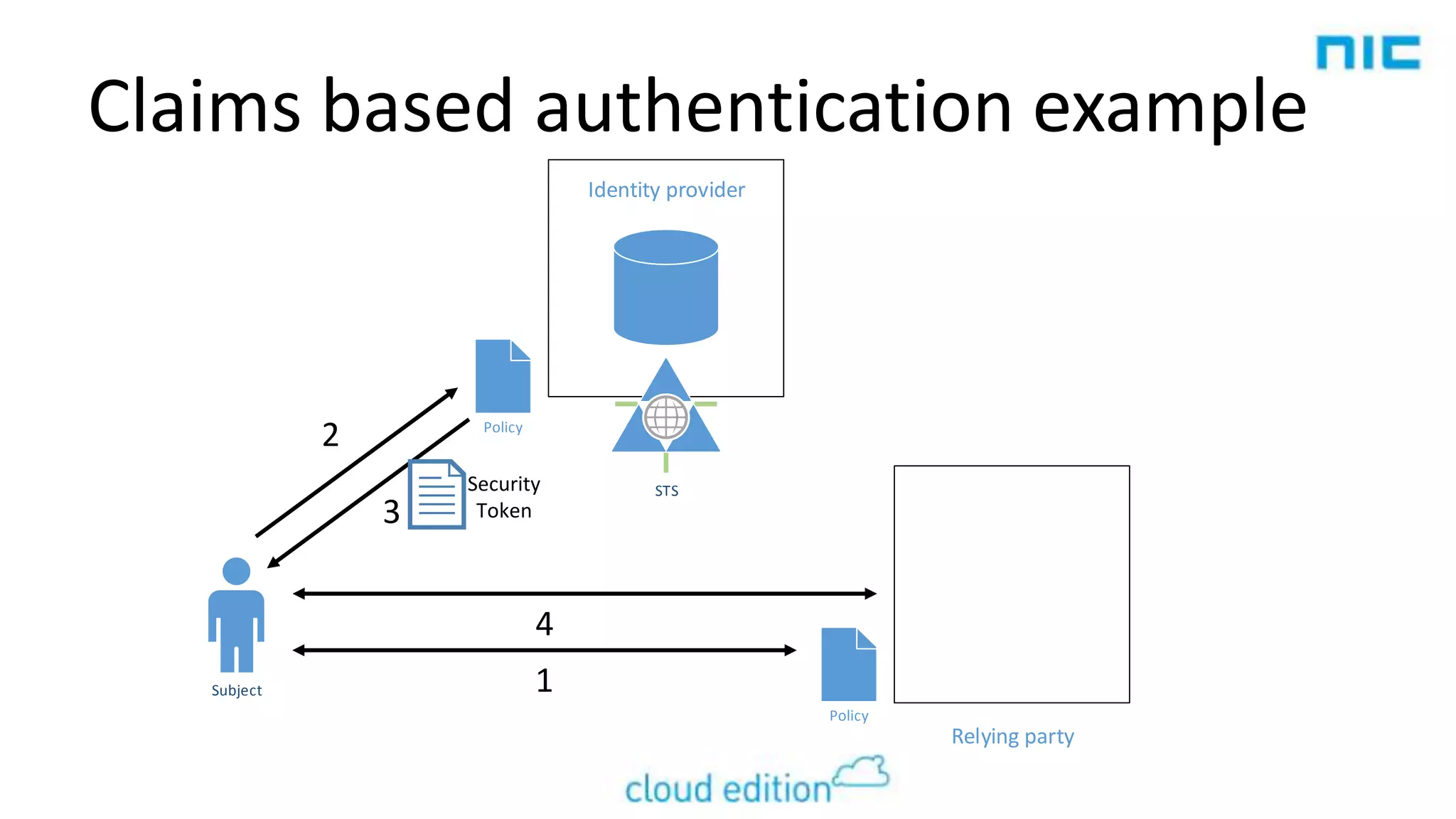
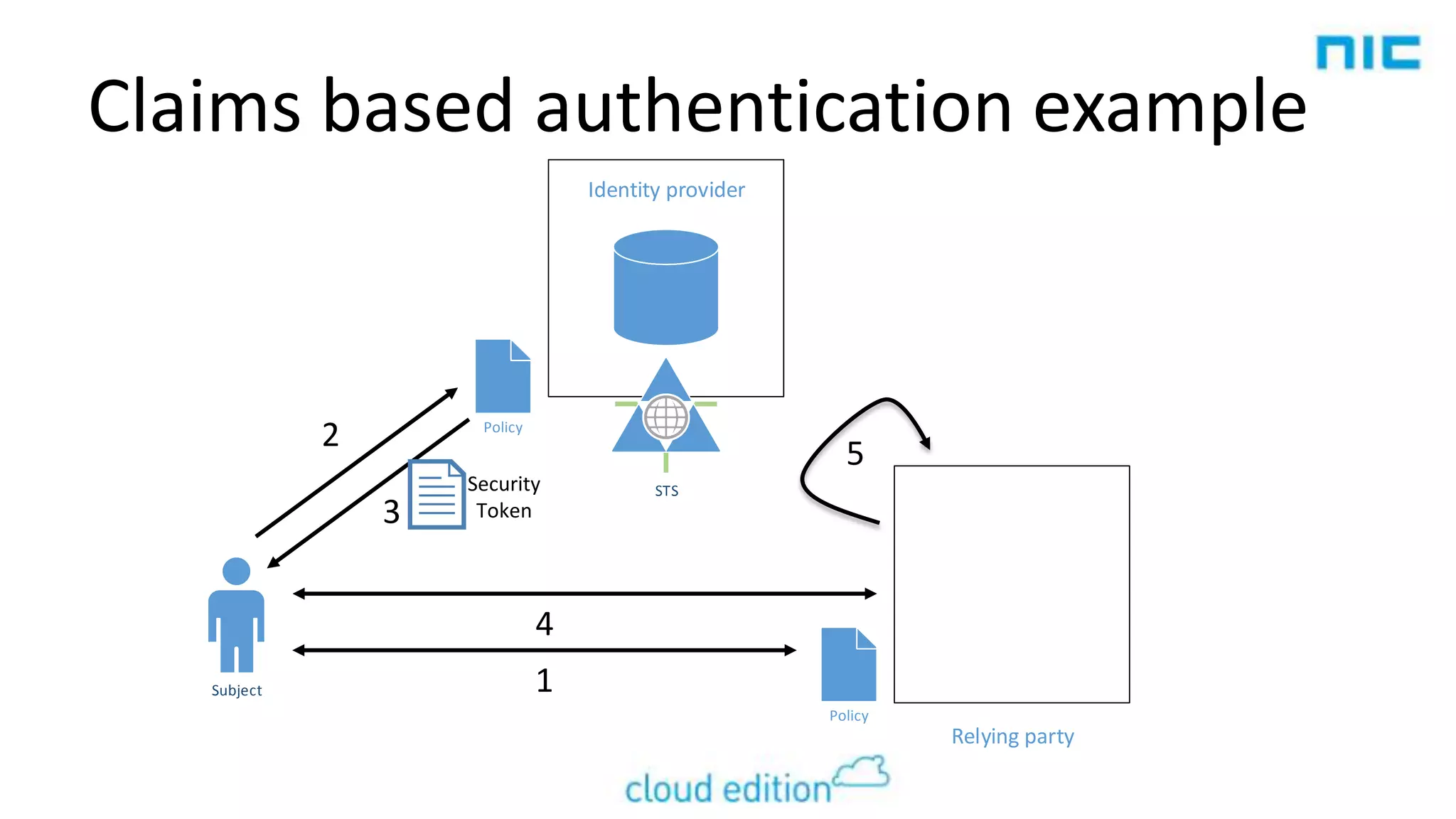
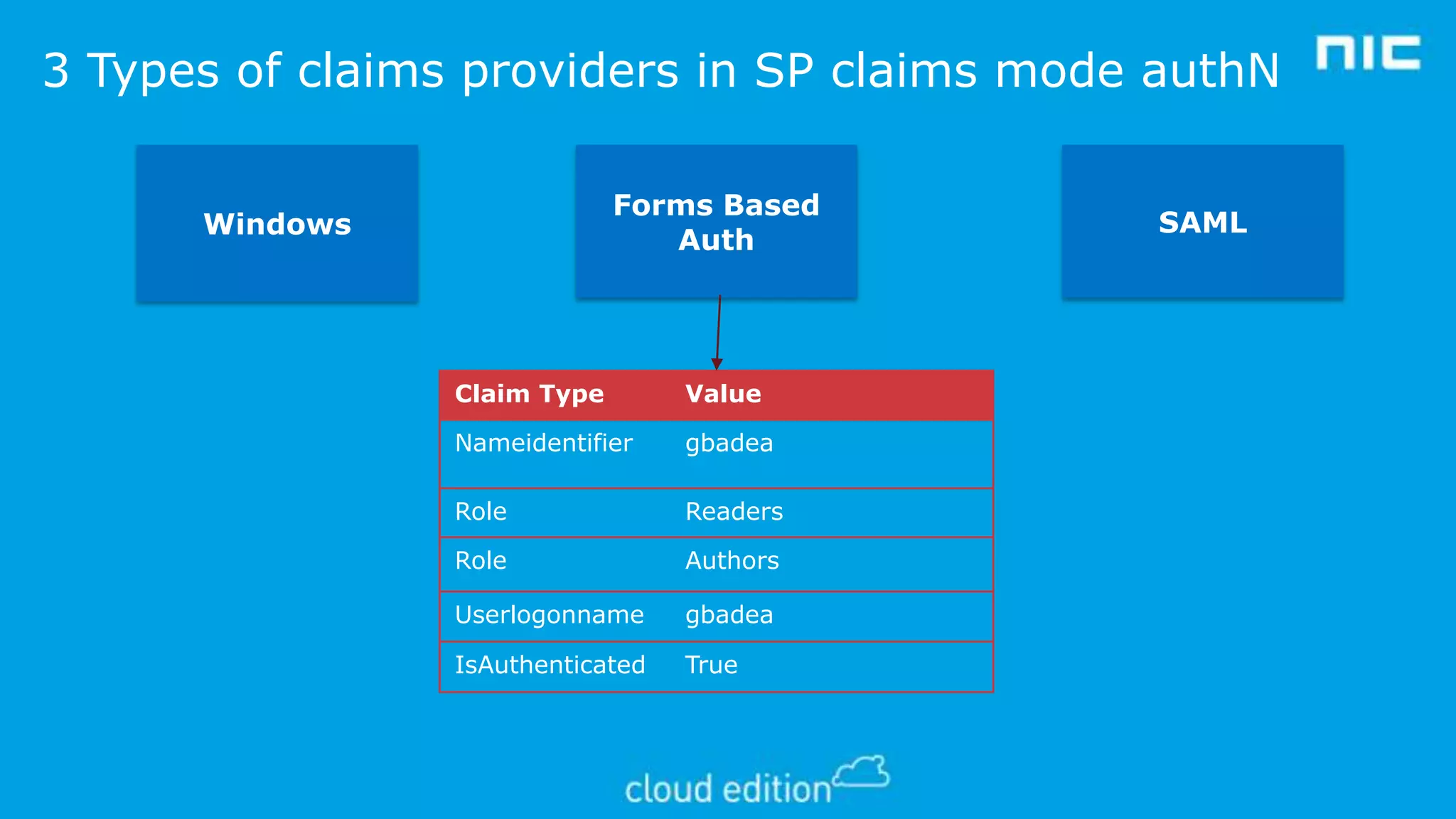
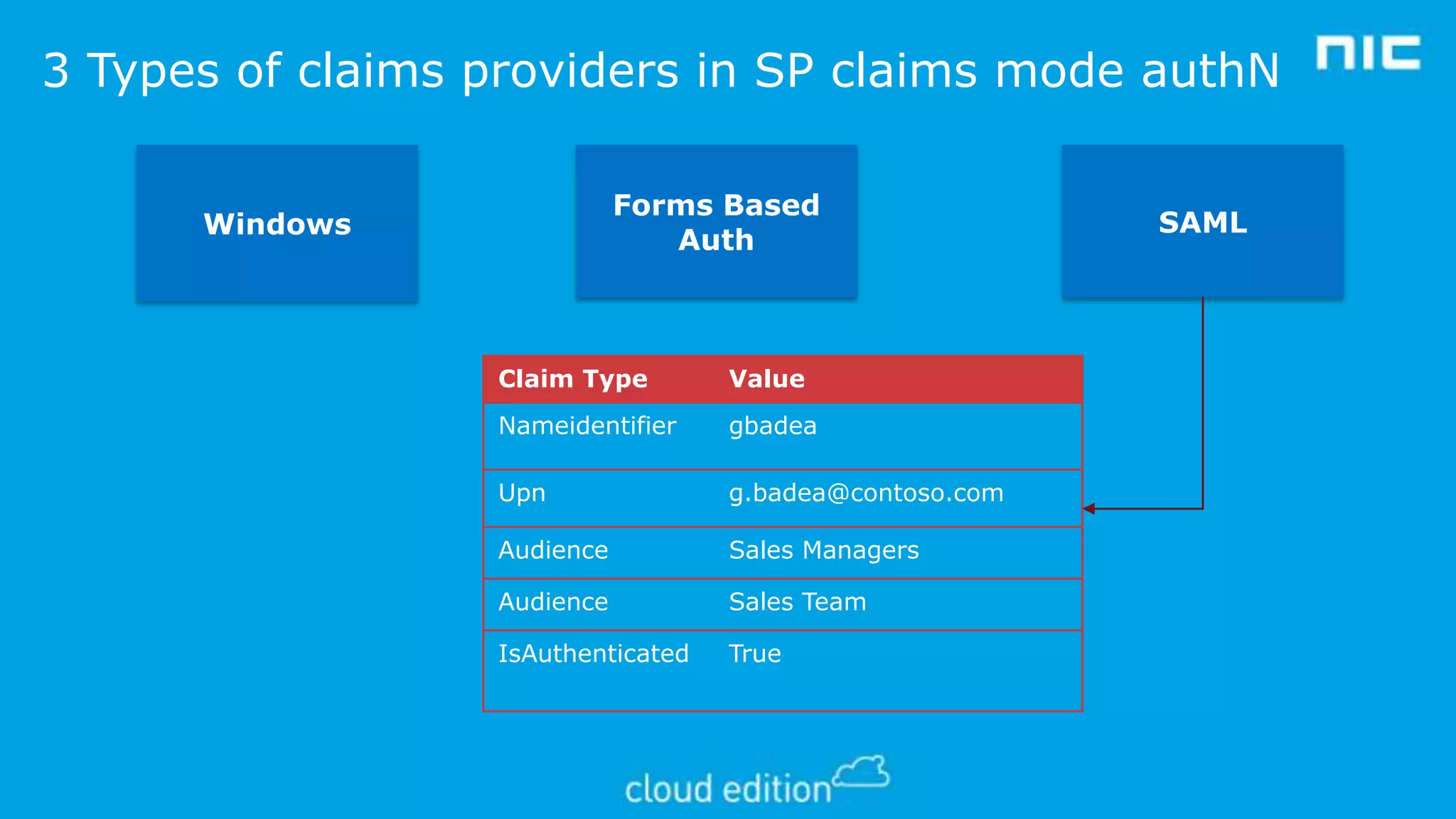
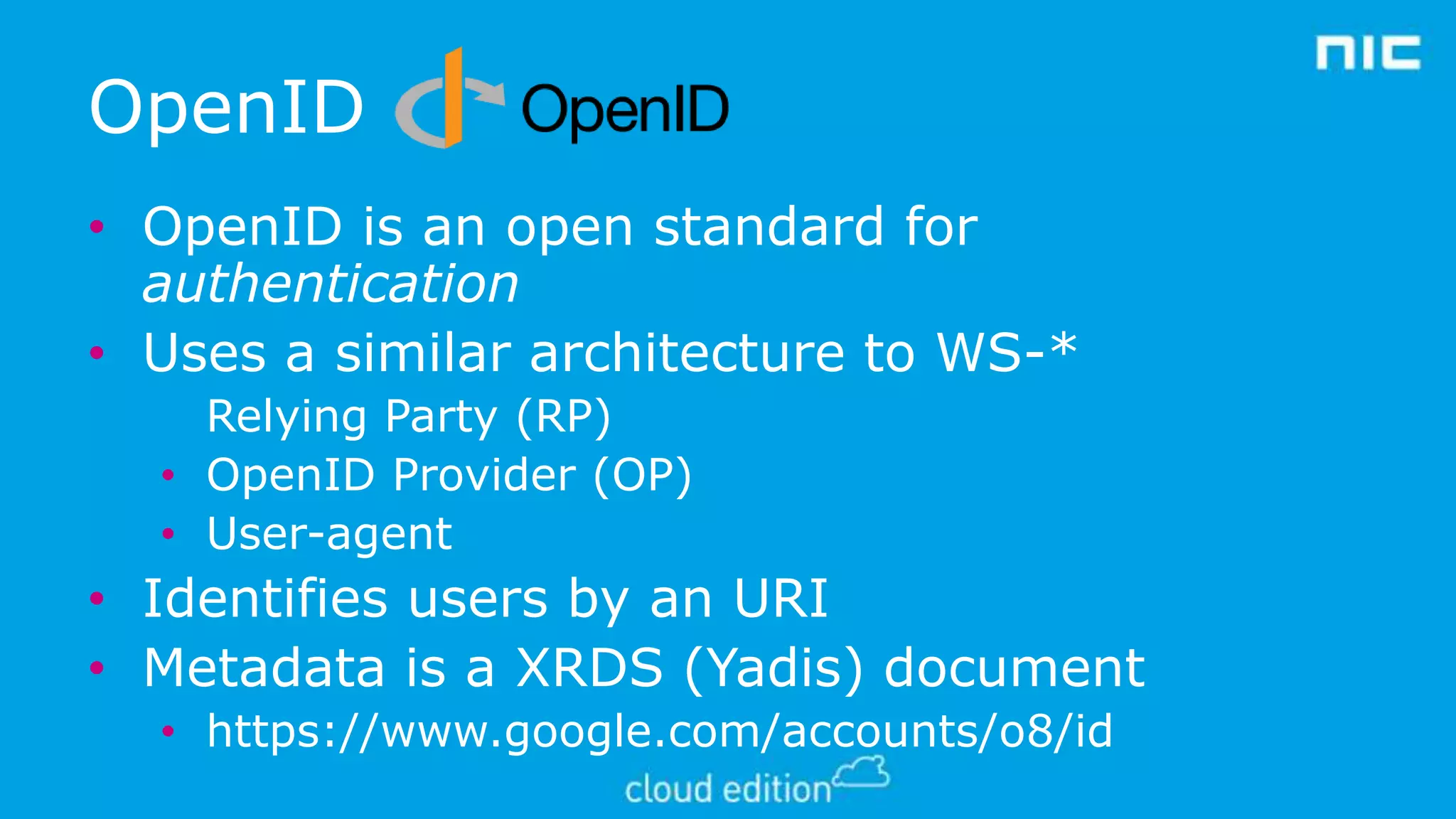
2. Claims-based identity uses an abstraction layer where claims about a subject are issued in security tokens by an identity provider and can be verified by a relying party.
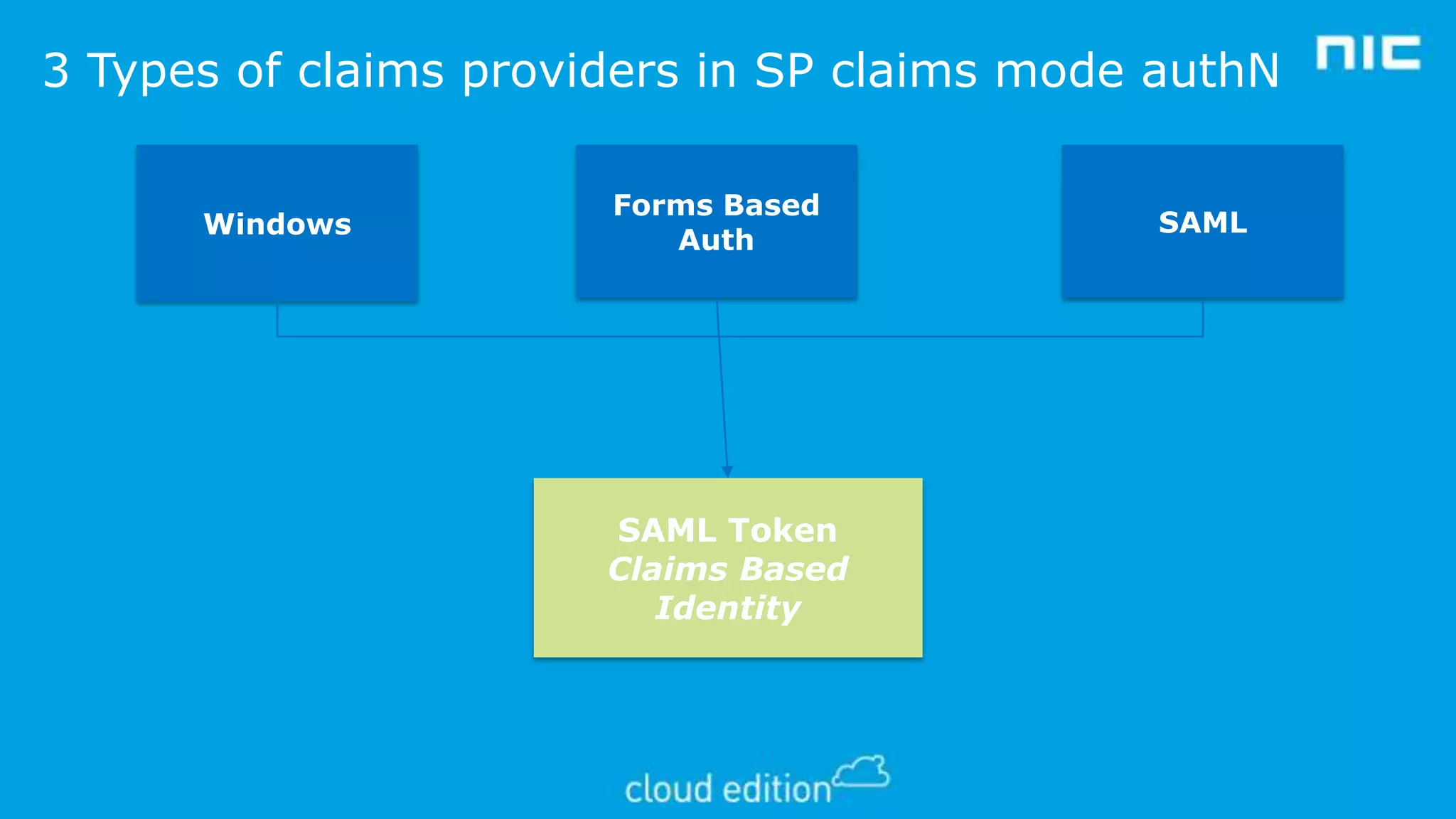
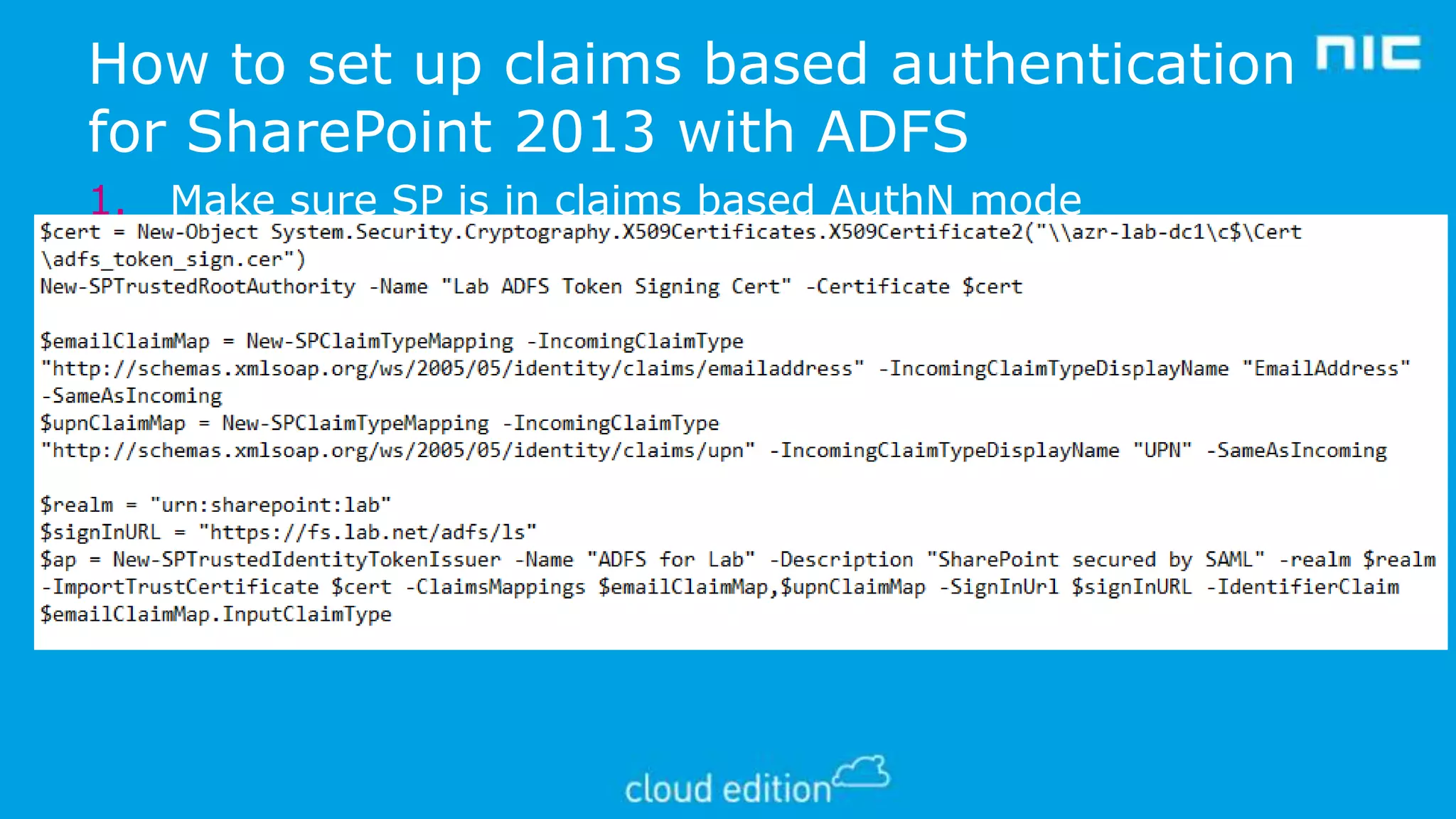
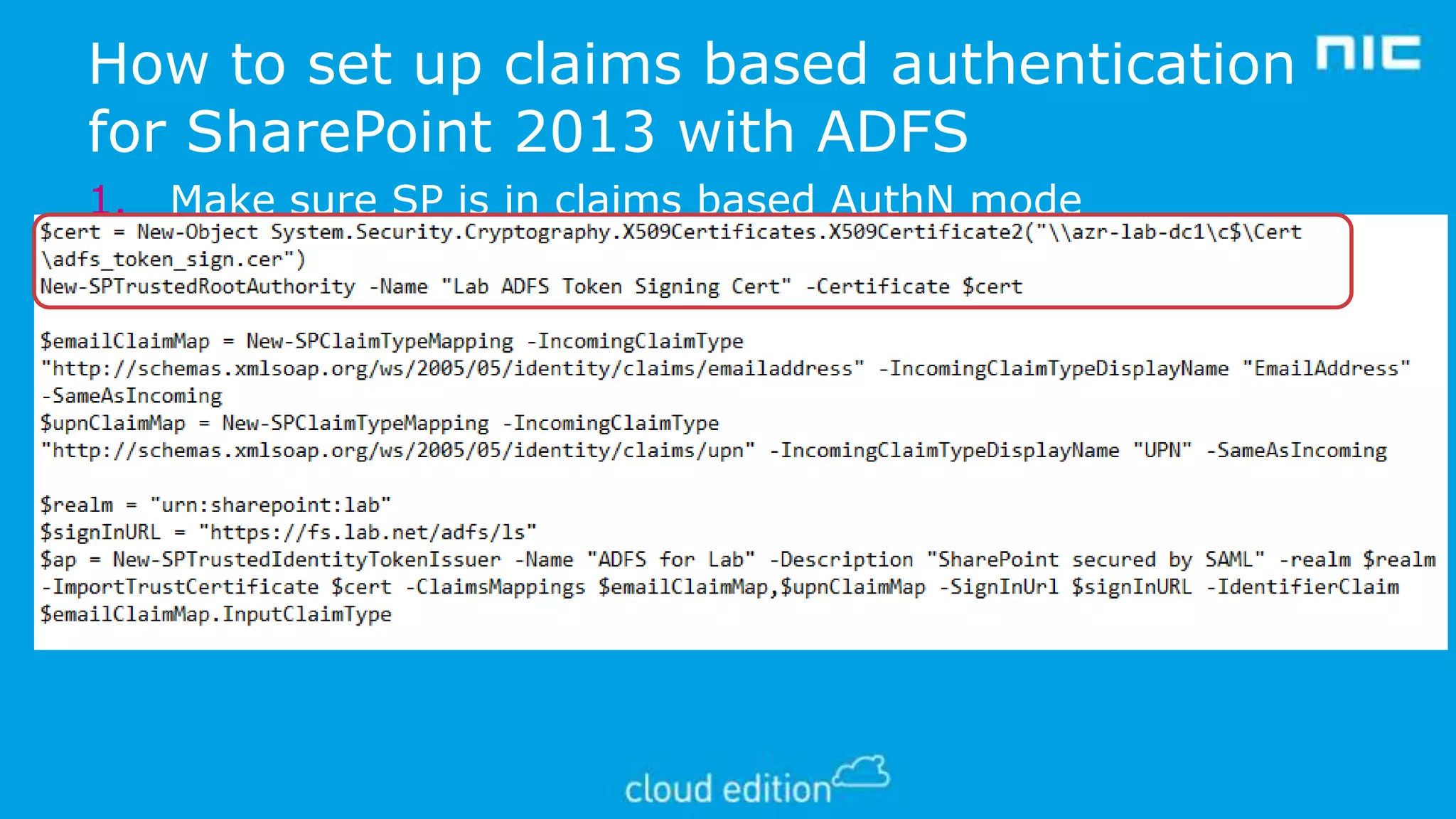
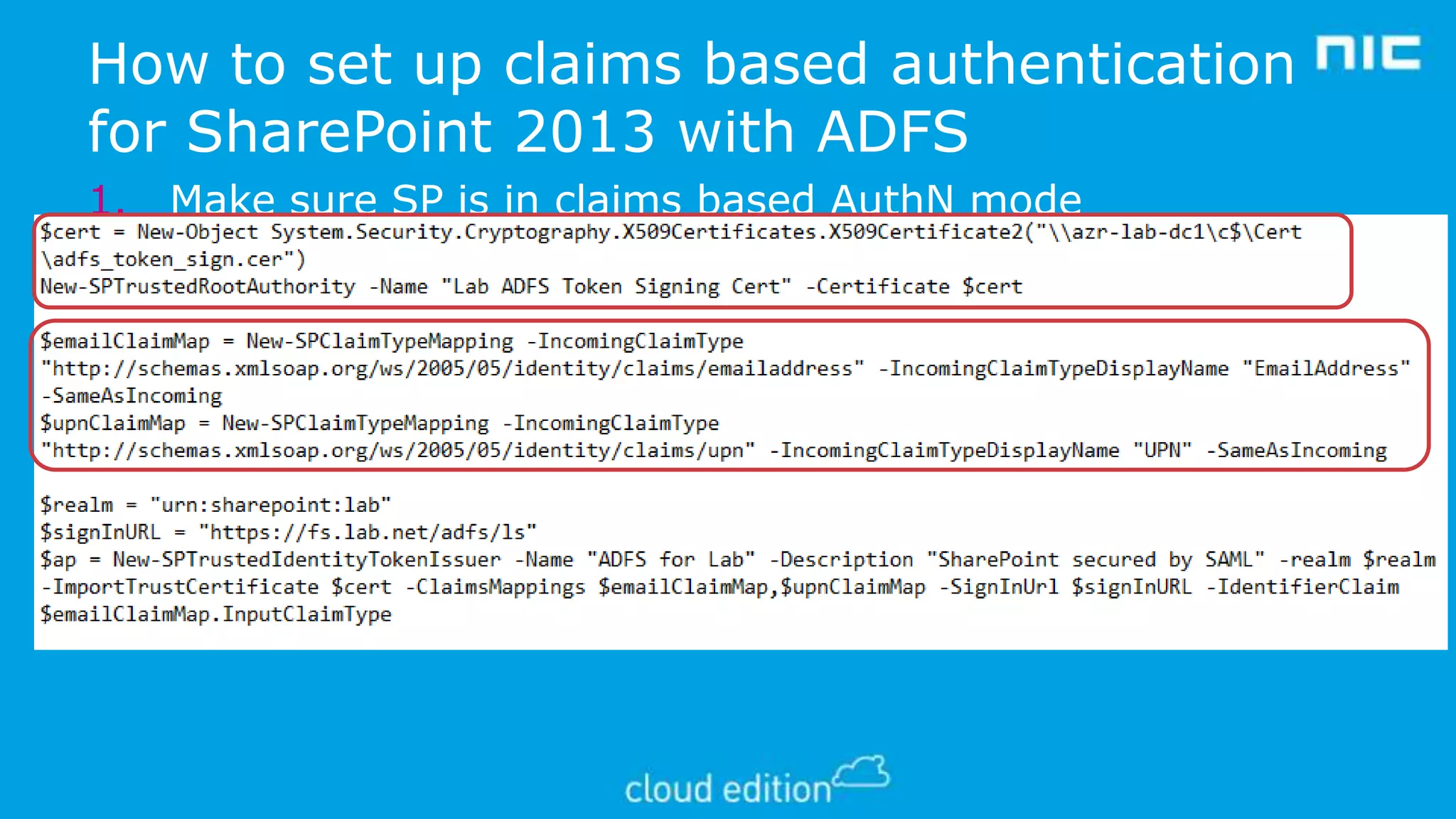
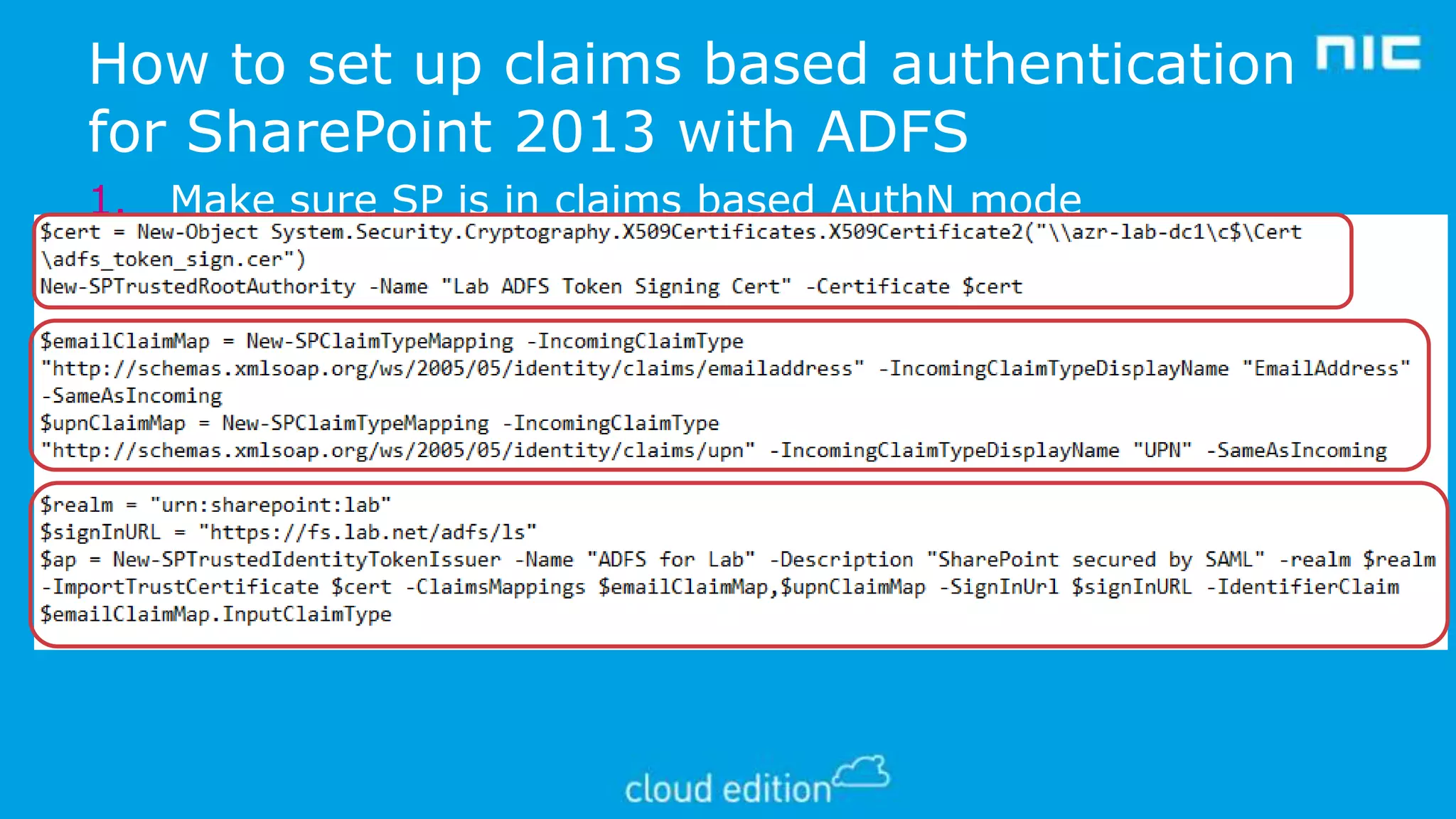
3. The document discusses examples of implementing claims-based identity on-premises using Active Directory Federation Services (ADFS) and in the cloud using Azure Active Directory (WAAD) as identity providers.