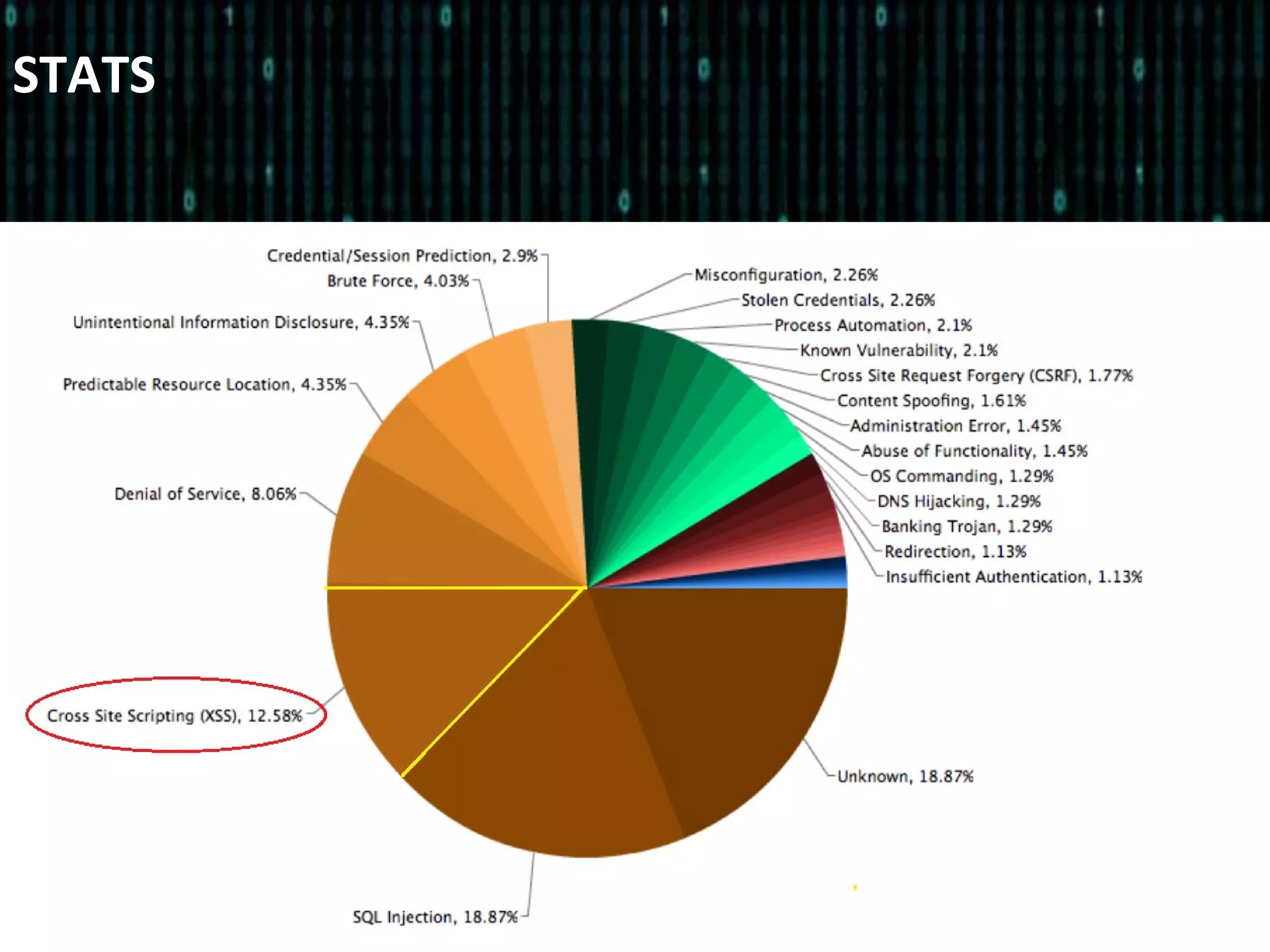
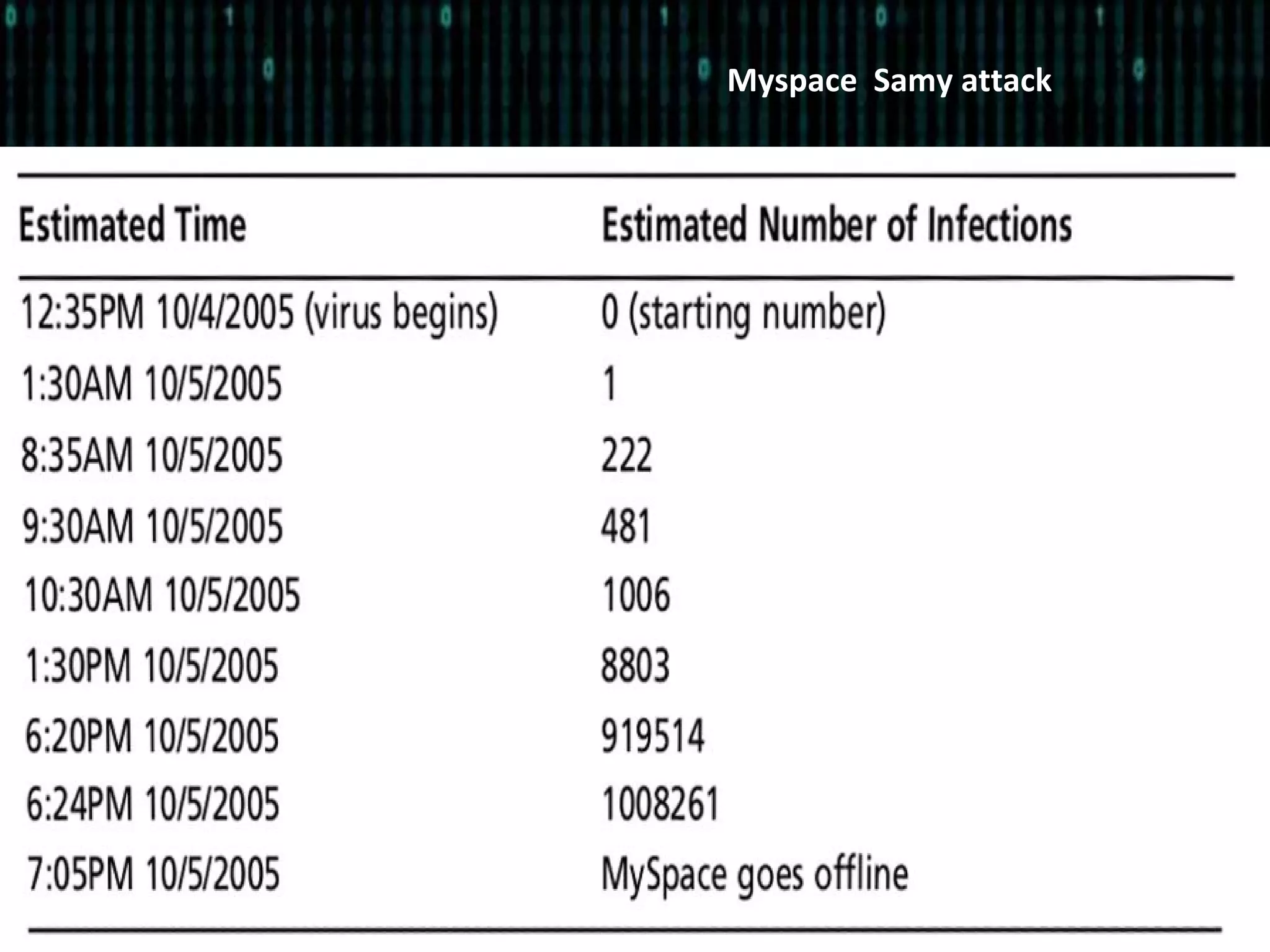
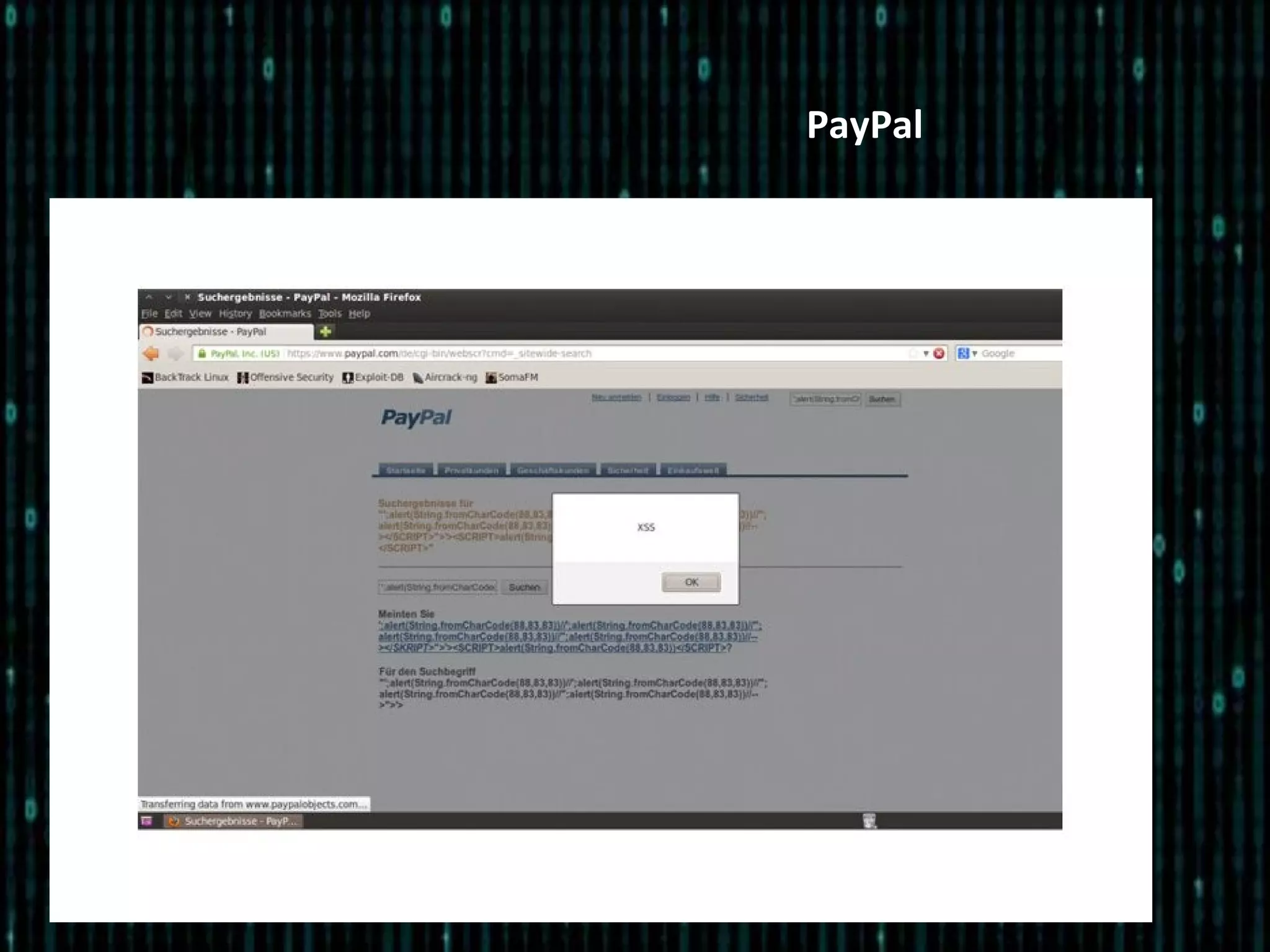
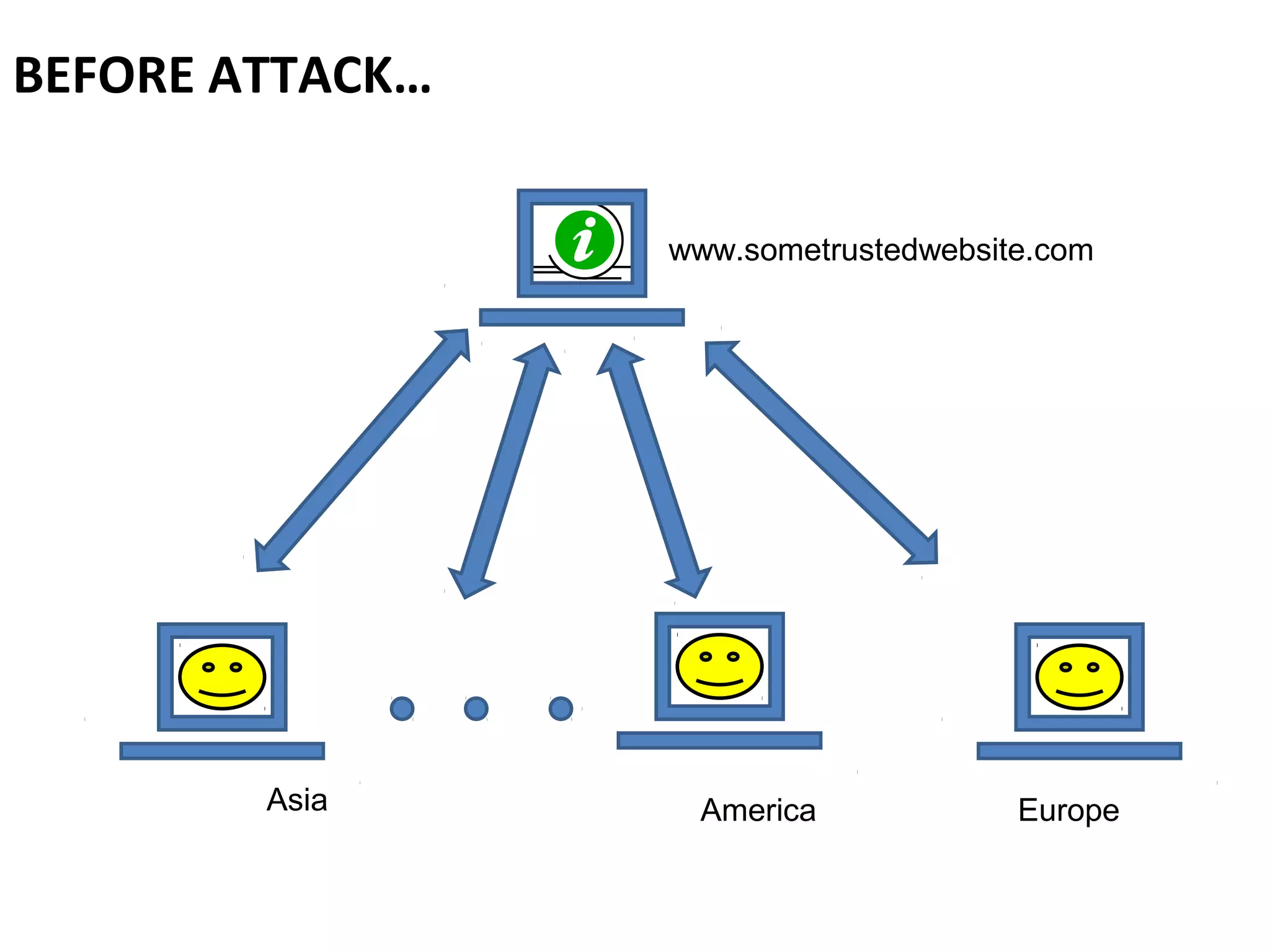
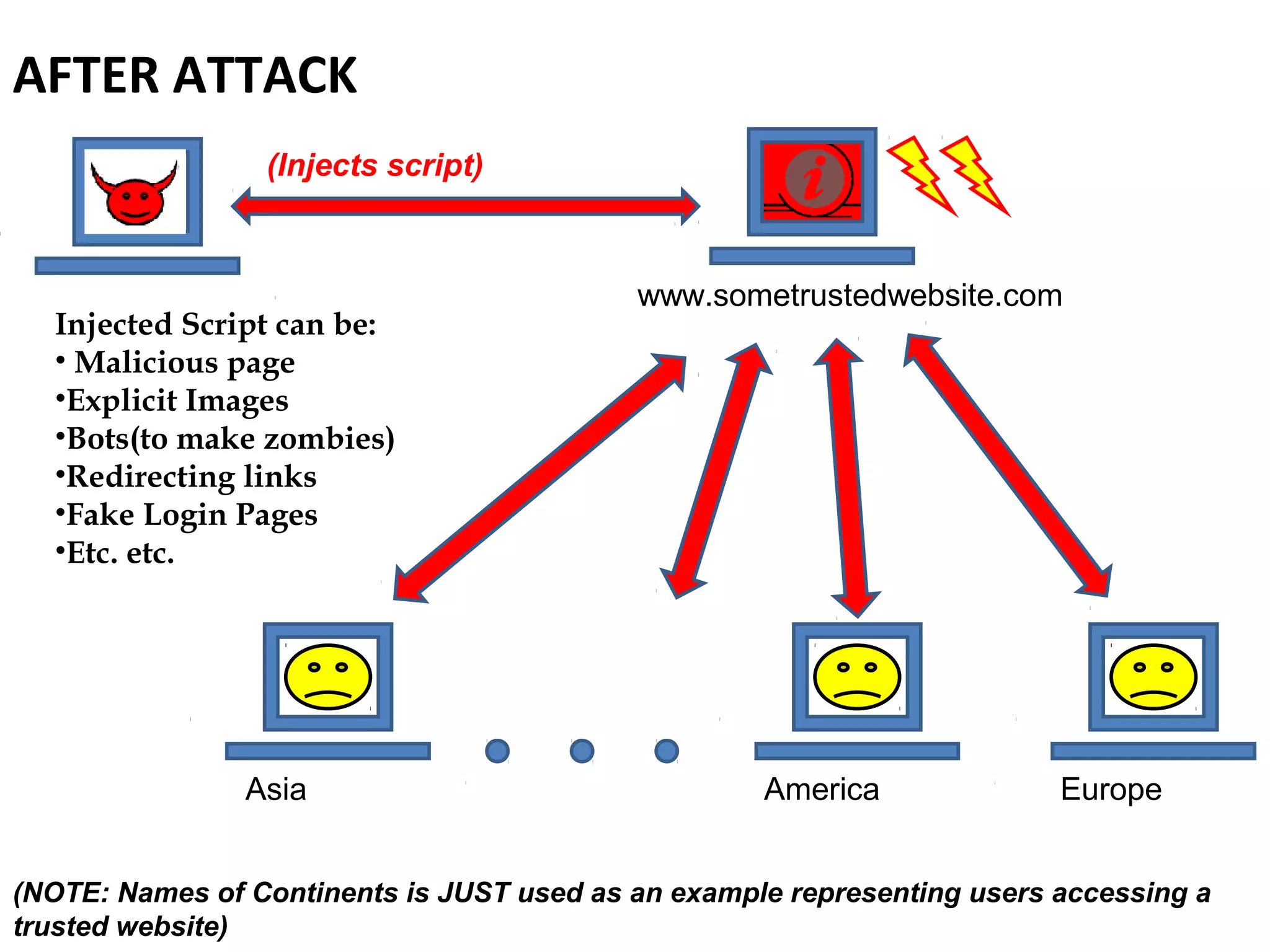
The document outlines a session organized by a hacking and information security group, focusing on Cross-Site Scripting (XSS) vulnerabilities. It discusses the birth of XSS, its types, and prevention mechanisms, emphasizing the risks associated with unsanitized code. Additionally, it includes hands-on activities for participants to experience XSS challenges and encourages engagement through Q&A and future meeting topics.














![UNSANITIZED CODE: STORED XSS
<?php
?>
if(isset($_POST['btnSign']))
{
$message = trim($_POST['mtxMessage']);
$name = trim($_POST['txtName']);
// Sanitize message input
$message = stripslashes($message);
$message = mysql_real_escape_string($message);
// Sanitize name input
$name = mysql_real_escape_string($name);
$query = "INSERT INTO guestbook (comment,name) VALUES ('$messa
ge','$name');";
$result = mysql_query($query) or die('<pre>' . mysql_error() . '</pre>' );
}](https://image.slidesharecdn.com/xsstalkattackanddefense-130624231110-phpapp01/75/Xss-talk-attack-and-defense-22-2048.jpg)
![UNSANITIZED CODE: REFLECTED XSS
<?php
{
Else // else generates HTML page on user input
{
echo '<pre>';
echo 'Hello ' . $_GET['name'];
echo '</pre>';
}
?>
$isempty = true;
}
if(!
array_key_exists ("name", $_GET) || $_GET['name'] == NULL || $_GET
['name'] == '') //checks for empty text...](https://image.slidesharecdn.com/xsstalkattackanddefense-130624231110-phpapp01/75/Xss-talk-attack-and-defense-23-2048.jpg)
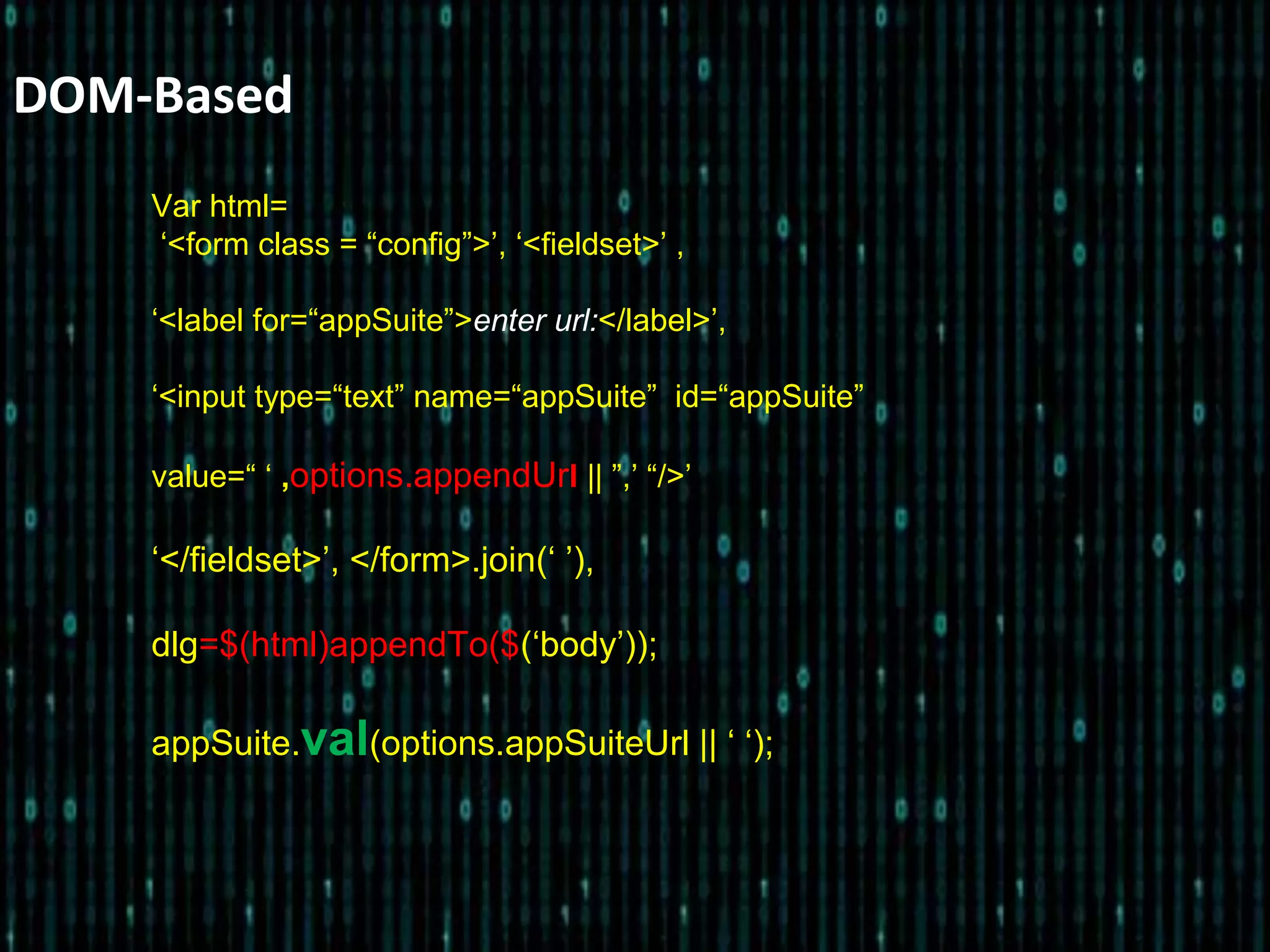
![DOM-Based XSS
Var html=
[ ‘<form class = “config”>’, ‘<fieldset>’ ,
‘<label for=“appSuite”>enter url:</label>’,
‘<input type=“text” name=“appSuite”
id=“appSuite”
value=“ ‘ ,options.appendUrl || ”,’ “/>’
‘</fieldset>’, </form>].join(‘ ’),
dlg=$((html)appendTo($body));](https://image.slidesharecdn.com/xsstalkattackanddefense-130624231110-phpapp01/75/Xss-talk-attack-and-defense-24-2048.jpg)

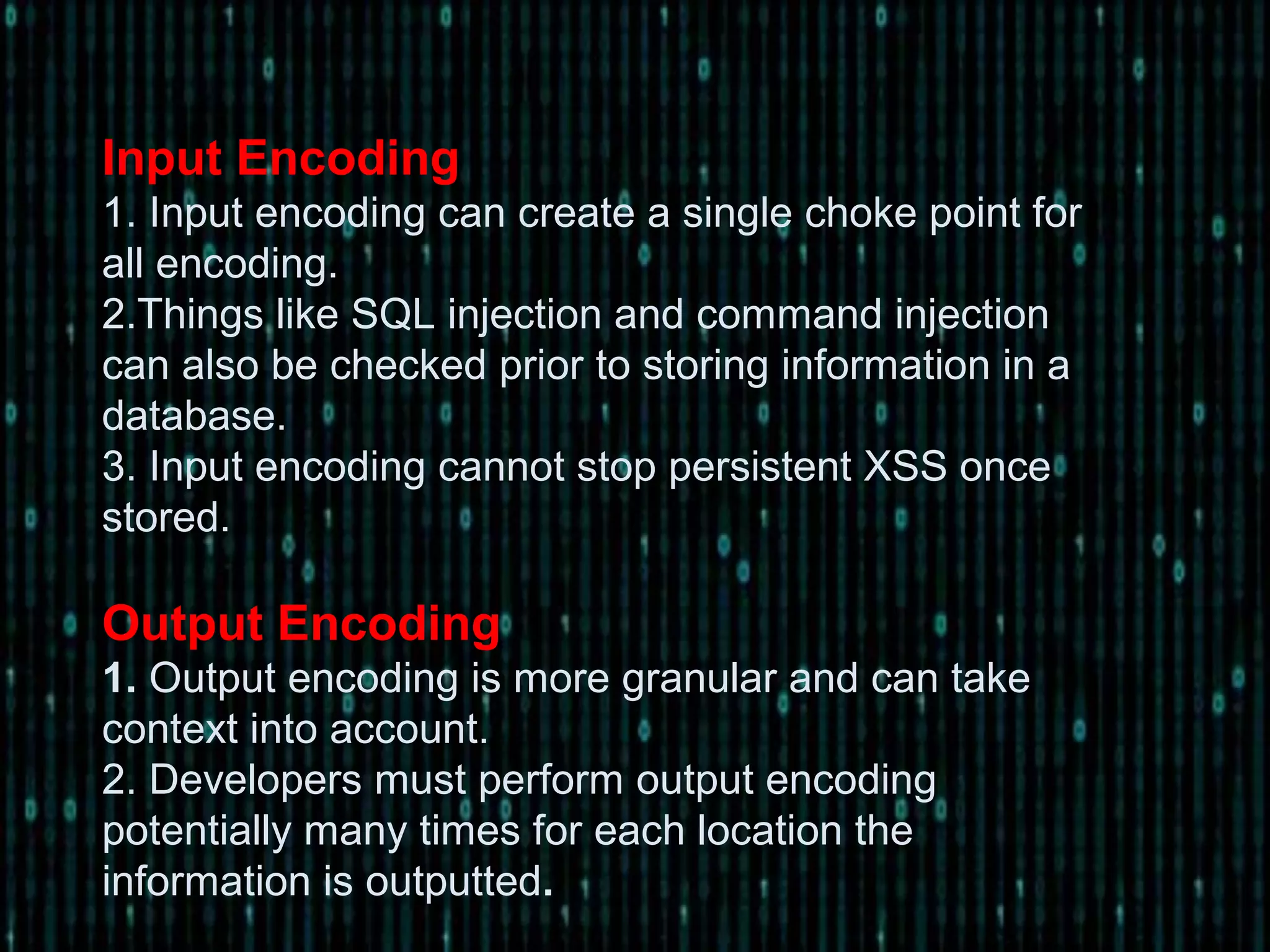

![CODE SOLUTION: Stored xss
<?php
if(isset($_POST['btnSign']))
{
$message = trim($_POST['mtxMessage']);
$name = trim($_POST['txtName']);
// Sanitize message input
$message = stripslashes($message);
$message = mysql_real_escape_string($message);
$message = htmlspecialchars($message);
// Sanitize name input
$name = stripslashes($name);
$name = mysql_real_escape_string($name);
$name = htmlspecialchars($name);
$query = "INSERT INTO guestbook (comment,name) VALUES ('$message','$name');";
$result = mysql_query($query) or die('<pre>' . mysql_error() . '</pre>' );
}](https://image.slidesharecdn.com/xsstalkattackanddefense-130624231110-phpapp01/75/Xss-talk-attack-and-defense-28-2048.jpg)
![SOLUTION:Reflected XSS
<?php
if(!array_key_exists ("name", $_GET) || $_GET['name'] == NULL ||
$_GET['name'] == '')
{
$isempty = true;
}
Else
{
echo '<pre>';
echo 'Hello ' . htmlspecialchars($_GET['name']);
echo '</pre>';
}
?>](https://image.slidesharecdn.com/xsstalkattackanddefense-130624231110-phpapp01/75/Xss-talk-attack-and-defense-29-2048.jpg)