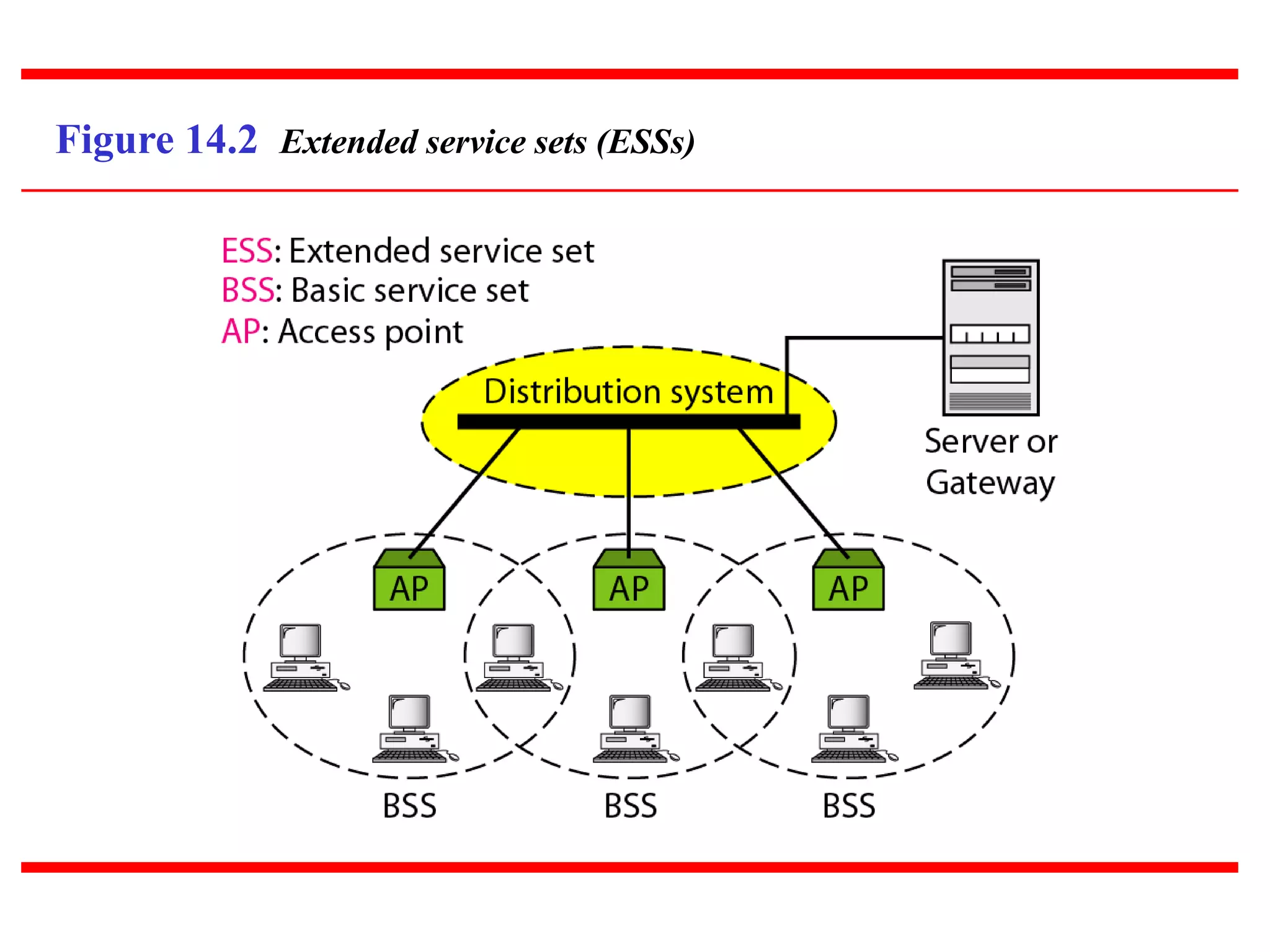
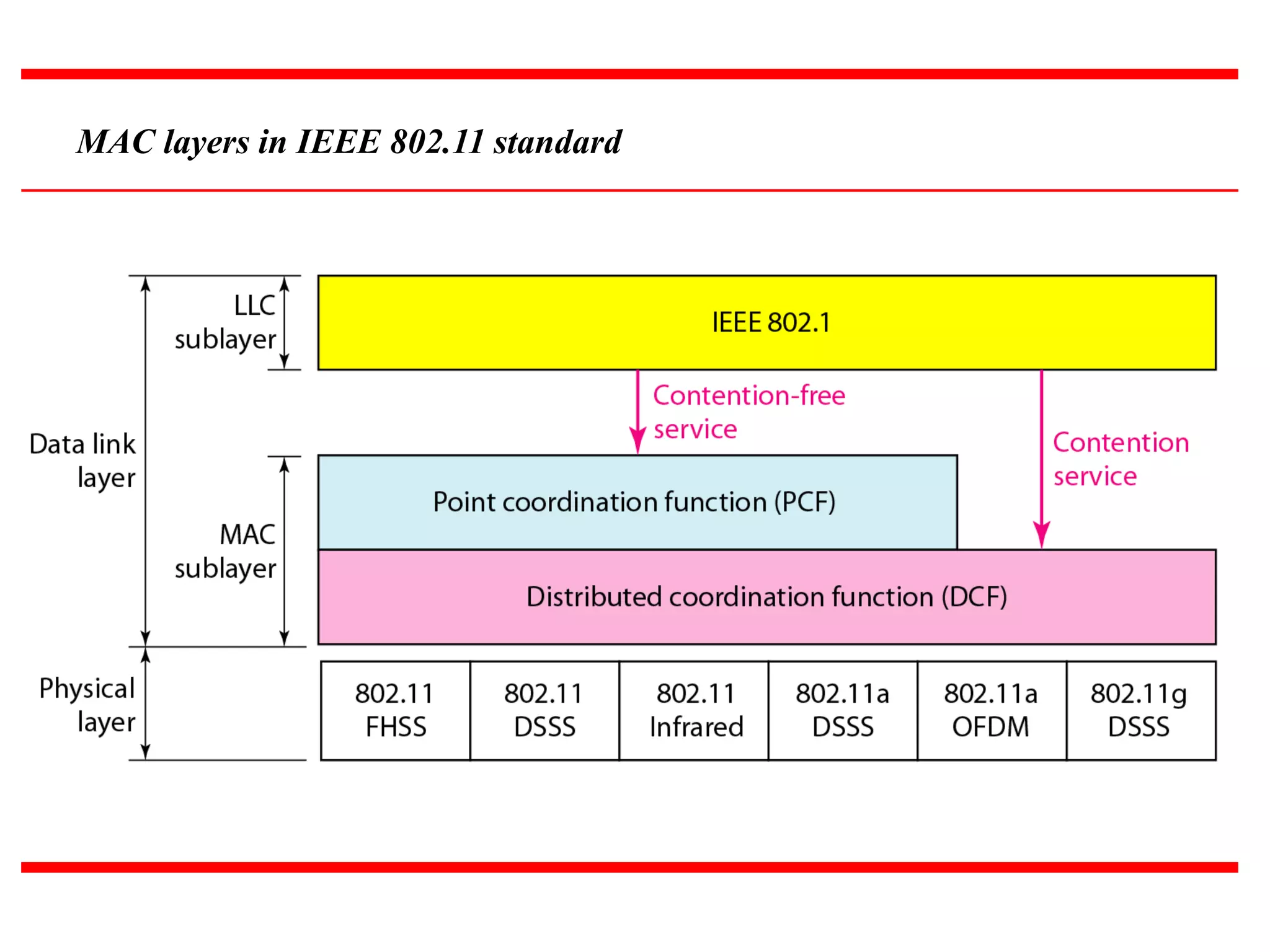
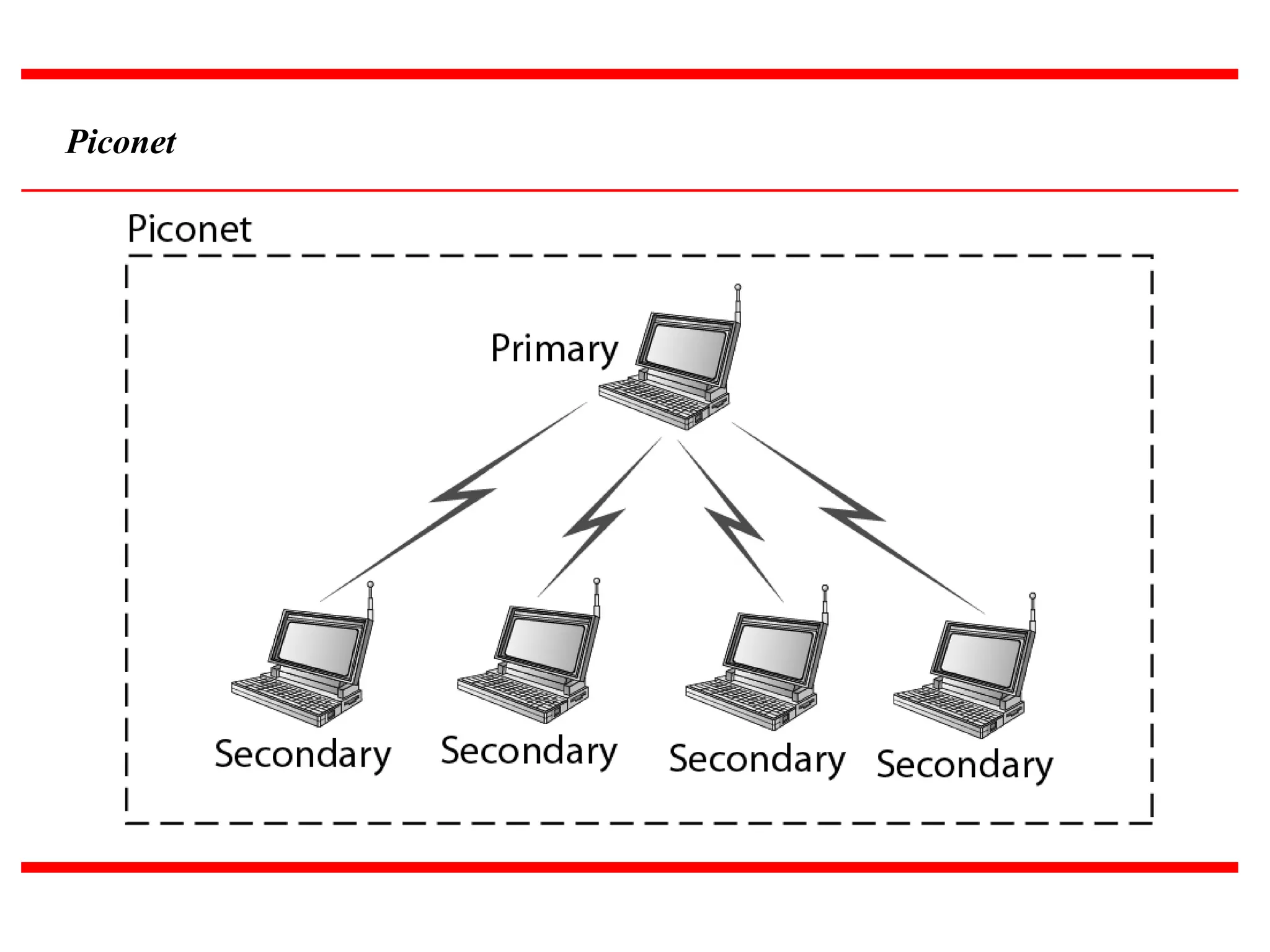
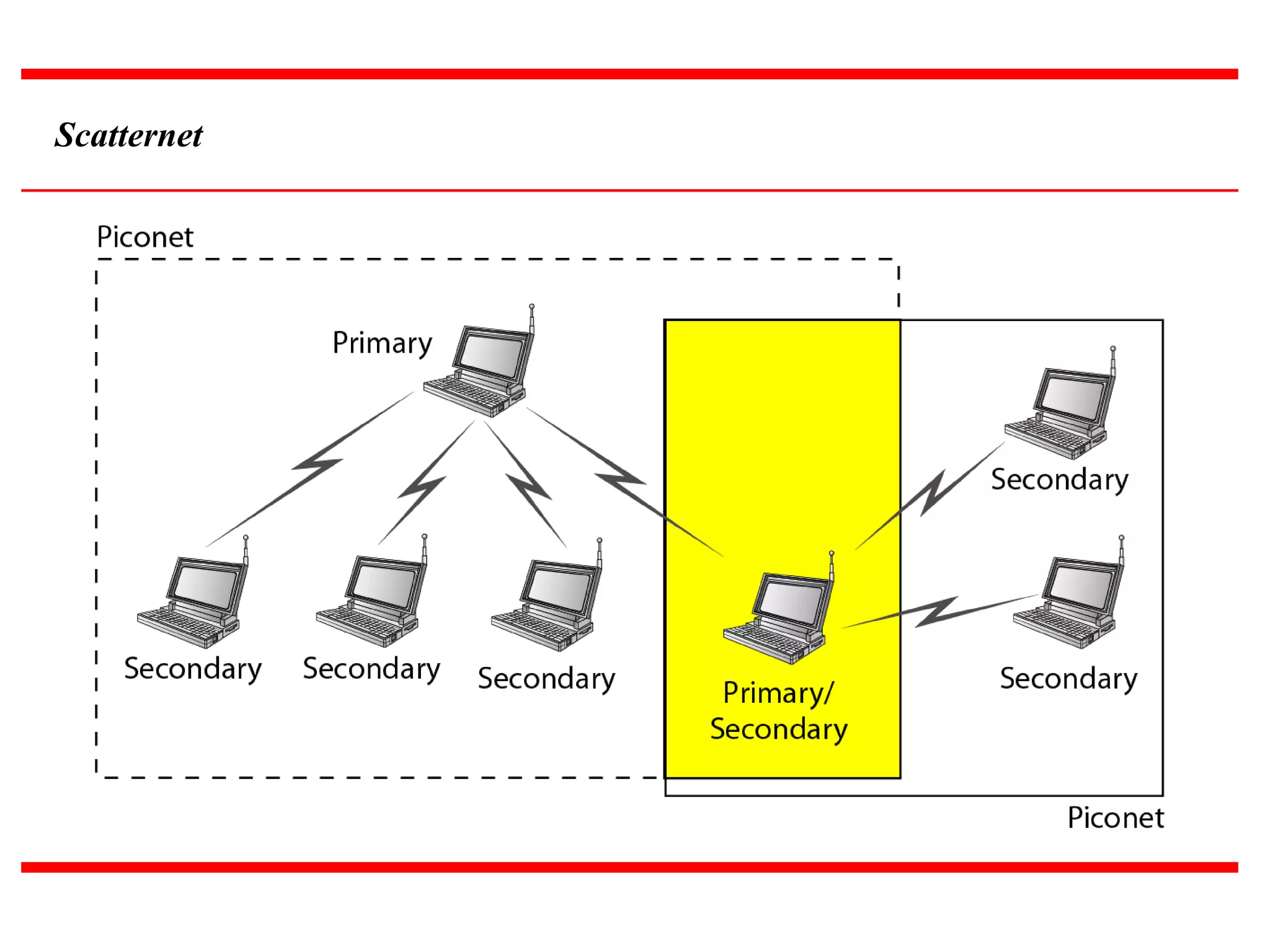
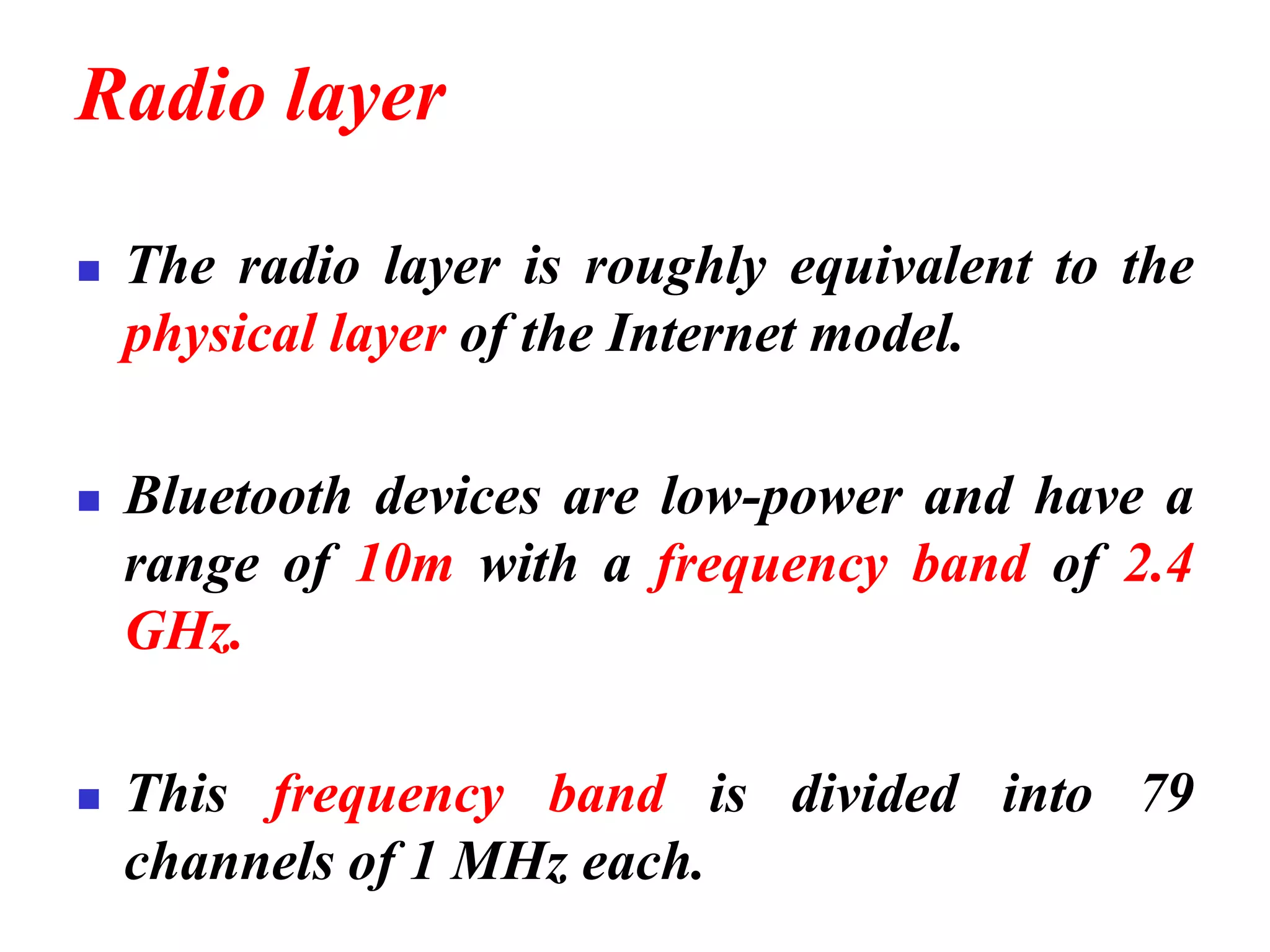
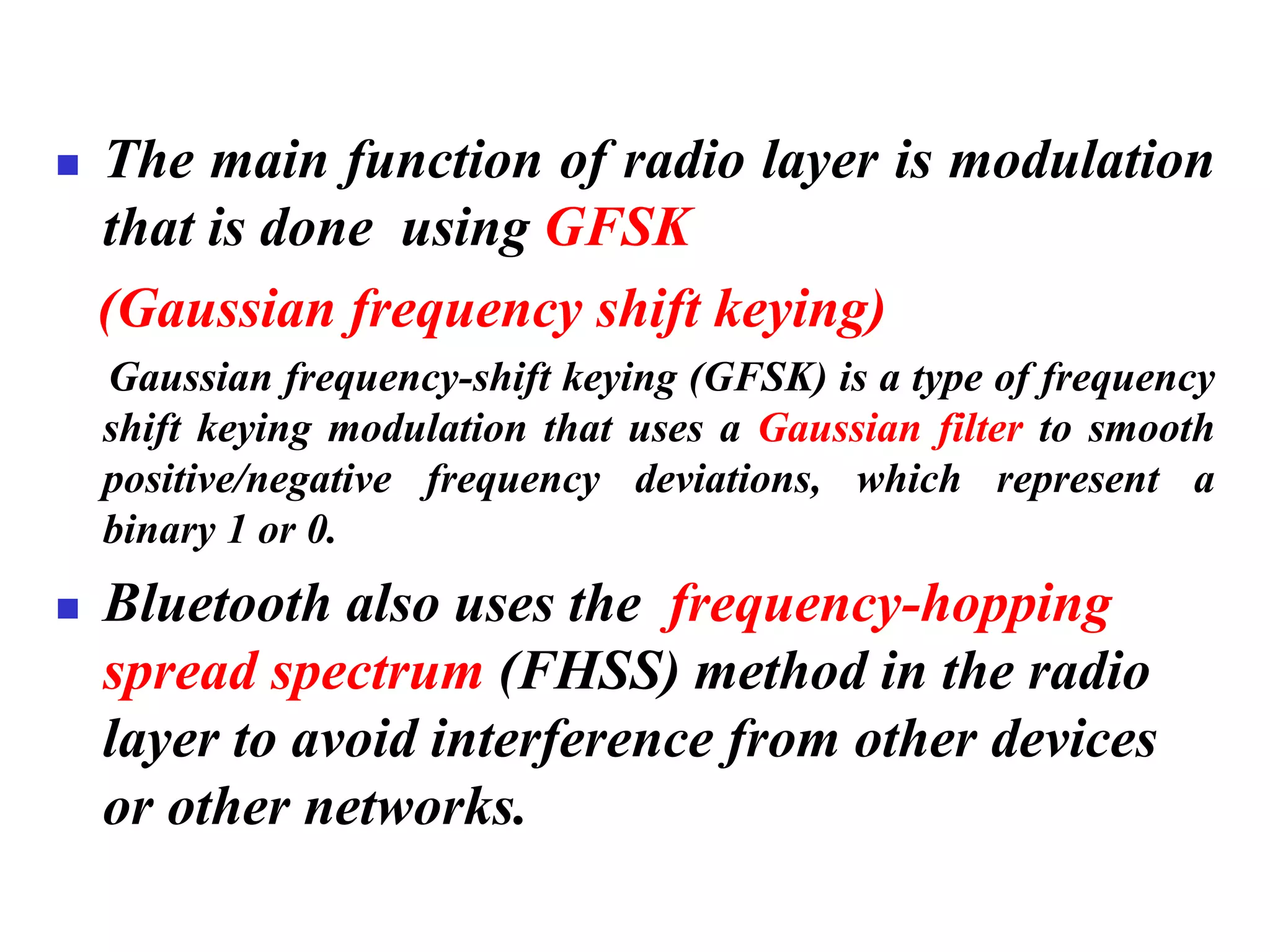
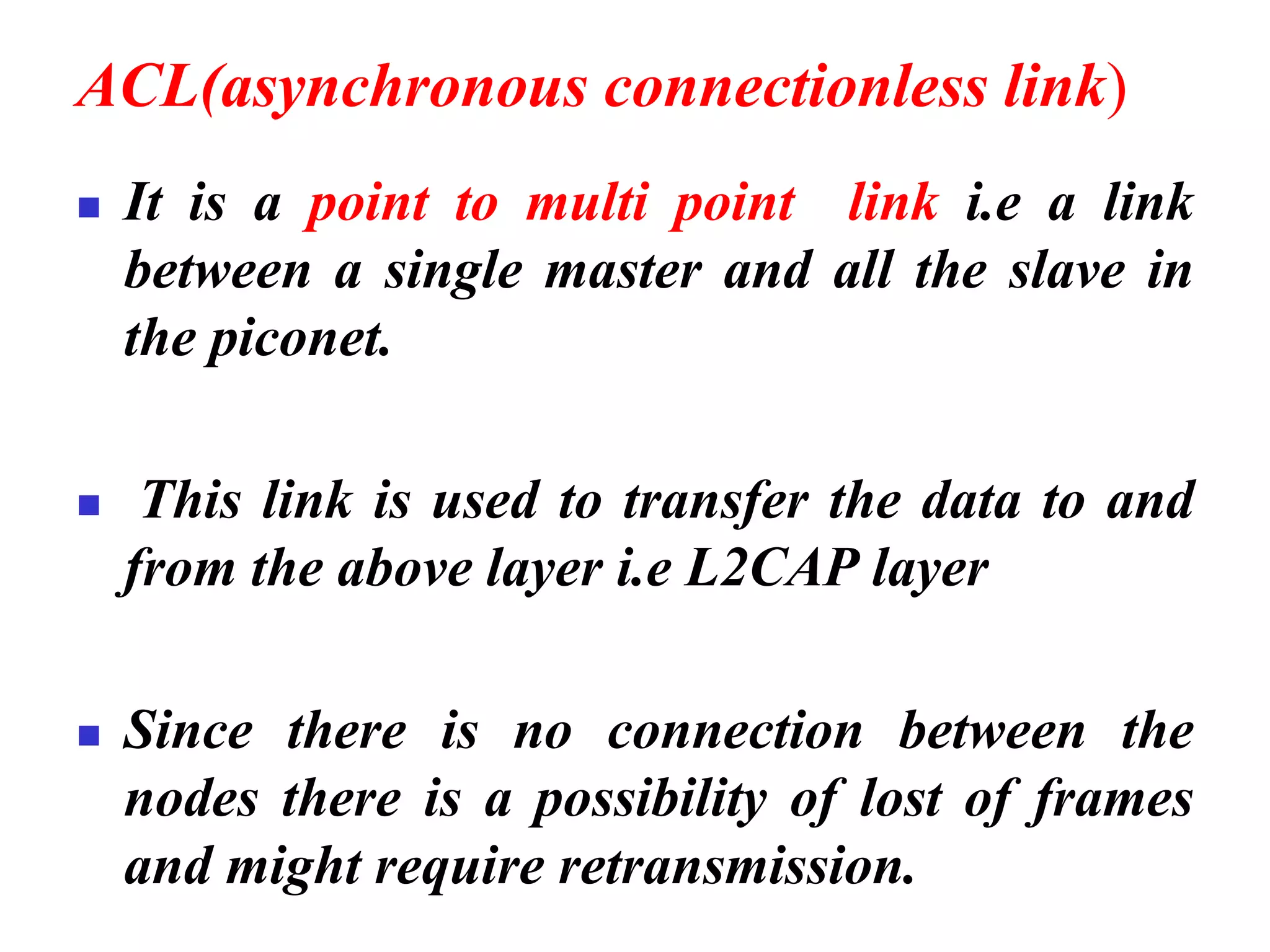
The document discusses wireless LAN technologies, focusing on IEEE 802.11 and Bluetooth. It explains the architecture of wireless LANs, including basic and extended service sets, as well as the MAC sublayers and frame formats. Additionally, it details Bluetooth networking, including piconets and scatternets, and describes various layers and protocols within Bluetooth technology.