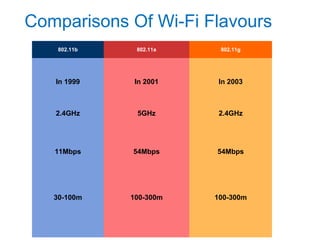
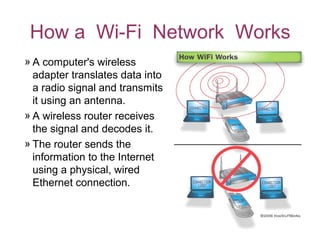
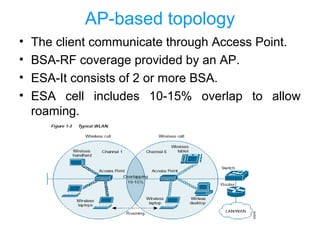
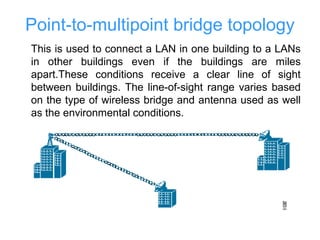
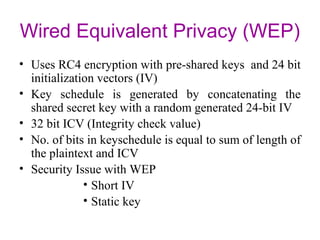
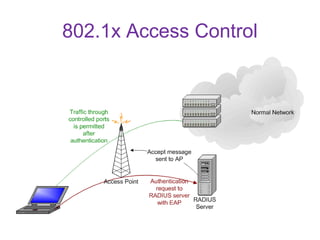
This document discusses Wi-Fi technology, including its history and standards, how Wi-Fi networks work, common network topologies, applications, security techniques and advantages/disadvantages. It introduces Wi-Fi as a wireless alternative to wired networks that uses radio technologies like 802.11b, 802.11a and 802.11g to transmit data at high speeds. Key components of a Wi-Fi network include access points and Wi-Fi cards. [/SUMMARY]