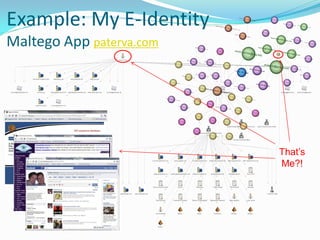
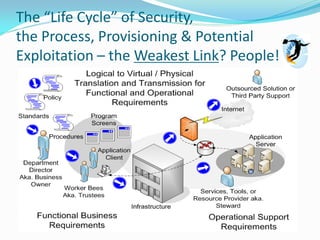
The document discusses protecting one's electronic identity and the risks of identity theft. It begins with an introduction by Erwin Carrow on his background and role conducting IT evaluations. It then outlines some key points on understanding the risk to personal information, how identities can be stolen both online and offline, and the various ways data can be lost or leaked. It provides examples of commercial and personal threats, describing how identities are exploited using social engineering and technical attacks. It notes the legal implications are still developing and that individuals bear responsibility for initiating action. Overall, the document aims to increase awareness of identity theft risks and provide resources on protecting personal information and responding to potential issues.







![Threats and the Facts
(Commercial - part 1)
October 19, Help Net Security - (International) Kaspersky download site hacked, redirecting users to fake AV. October 17, the Kaspersky’s
USA download site provided download links that redirected users to a malicious Web page where windows telling them their computer was
infected were popping up and they were encouraged to buy a fake AV solution. Source: www.net-security.org
October 19, V3.co.uk - (International) RealPlayer receives critical security update. Real Networks has issued a security update for RealPlayer,
addressing flaws in versions …. vulnerabilities ranging from buffer overflow and injection flaws to issues that could allow an attacker to
remotely execute code on a targeted system. Source: www.v3.co.uk/v3/news
October 18, Computerworld - (International) ‘Unprecedented wave’ of Java exploits hits users, says Microsoft. Microsoft said October 18 that
an “unprecedented wave” of attacks are exploiting vulnerabilities …. attempts to exploit Java bugs …. “IDS/IPS vendors ... have challenges with
parsing Java code,” … the performance impact on a network IPS could be crippling. [So] the people that we expect to notice increases in
exploitation might have a hard time seeing this. Call it Java-blindness.” Source: www.computerworld.com
July 19, SCADA System’s Hard-Coded Password Circulated Online for Years - malware that targets command-and-control software installed
in critical infrastructures uses a known default password that the software maker hard-coded into its system.…. SCADA, short for “supervisory
control and data acquisition,” systems are programs installed in utilities and manufacturing facilities to manage the operations. SCADA
…potentially vulnerable to remote attack by malicious outsiders who might want to seize control of utilities for purposes of sabotage,
espionage or extortion. “Default passwords are and have been a major vulnerability for many years,” said Steve Bellovin, …“It’s irresponsible to
put them in, in the first place…. If that’s the way the Siemens systems works, they were negligent.” Siemens did not respond to a request for
comment. Source: www.wired.com
October 20, Softpedia - (International) Fake Firefox and Chrome warning pages distribute malware. Security researchers warn a new
malware distribution campaign uses fake versions of the malicious site warnings commonly displayed by Firefox and Google Chrome. Security
researchers from F-Secure now warn malware pushers are increasingly abusing the trust users associate with these warnings to infect them.
Malicious Web sites that mimic both Firefox’s “Reported Attack Page” alert, as well as Chrome’s “this site may harm your computer” warning,
have been spotted. The pages look exactly the same as the real thing, except for a button that reads “Download Updates,” suggesting that
security patches are available for the browsers. The executable files served when these buttons are pressed install rogue antivirus programs …
the users who land on these latest sites discovered by F-Secure are also exposed to drive-by downloads via a hidden IFrame, which loads the
Phoenix exploit kit. Source: news.softpedia.com
October 20, Trusteer - (International) Trusteer reports hackers improve Zeus Trojan to retain leadership in crimeware race. Trusteer reported October
20 it has captured and analyzed a new version (2.1) of the Zeus financial malware. New capabilities include: URL matching based on a full
implementation of the Perl Compatible Regular Expressions (PCRE) library. This allows much more flexibility for Zeus’s configuration to define targets.
Source: www.trusteer.com](https://image.slidesharecdn.com/whymyeidentityneedsprotection-12899094925272-phpapp01/85/Why-My-E-Identity-Needs-Protection-9-320.jpg)

![More of the Same “Threats and the
Facts” – But, What are the Results?
Privacy Right Clearinghouse
Chronology of Data Record Breaches 13,678,437 (460 events,
2010) and 510,619,382 since January 2005 that have been
reported [www.privacyrights.org/ar/ChronDataBreaches.htm]
Ponemon –HRH 2008 Privacy Breach Index Survey (Sept 2008)
Self evaluation of overall performance of organization: -- 9%
gave an “A” -- 31% gave a “B” -- 26% gave a ”C” -- 29% gave a “D”
– 5% gave a “F” [www.HRH.com/privacy]
80 % believed their organizations experienced information
system data breaches and loss of customer and personal
information
50% Negligence, -- 29% Third-Party, 3% Hacker, --1% other
criminal activity;
36% 1 to 4 breaches involving 100 or records; 32% 5 to 8; 31% 9
or more](https://image.slidesharecdn.com/whymyeidentityneedsprotection-12899094925272-phpapp01/85/Why-My-E-Identity-Needs-Protection-11-320.jpg)

![The Basic Method to Exploit ...
YOUR E-Identity
Identify Social / Cultural “Normalcy” and associated “Common Denominators” where
potential gain or benefit may exist on the Internet or in the real world
Voice / Chat / Email / Tweet has become the primary “Means of Communication”
Browser Based Culture and Community, e.g., On-line Gaming (Entertainment), Banking
(financial), Social Networks (Socialization), pornography sites (22% of all Internet based
revenue), etc.
Marketing from Data Warehouses – Services (medical Google, Microsoft, Government
Entities (regardless of intentions, you are a customer, beneficiary, or potential threat)
Non-electronic communication or storage methods, e.g., stealing stuff with your name and
other information on it
Exploit “Common Denominators” by …
Identify and Predict potential Outcomes from Your INFORMATION [ANY FRINGE
FANS?]
Making it look like normal expected activity
Browser based exploits – Social networks, social engineer, harvest information, or capitalize on browser
technology vulnerabilities
Email based exploits – Phishing
Browser, Email, and Web Site exploitation are all used in conjunction
Obscure and confuse the real with the Counterfeit!
Their Objective …, is to recreate a Counterfeit “Normalcy” that attracts and is utilized
by YOU!!!!
FOR ORGANIZATIONAL (Terrorist) or PERSONAL (Theft, Malice, or Vendetta) GAIN](https://image.slidesharecdn.com/whymyeidentityneedsprotection-12899094925272-phpapp01/85/Why-My-E-Identity-Needs-Protection-13-320.jpg)