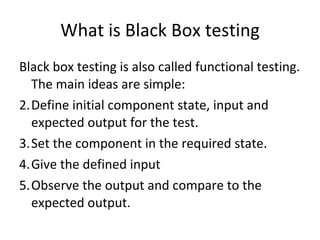
- White box testing uses information from the code to generate tests that achieve high coverage, like path coverage. Black box testing treats the system as a "black box" and defines inputs and expected outputs without viewing the code.
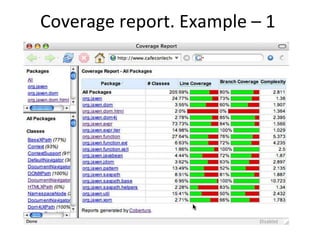
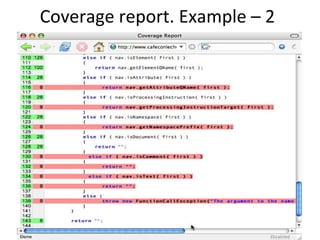
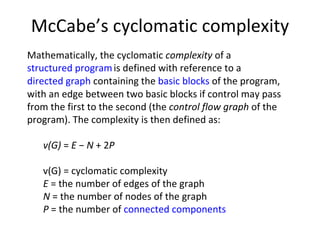
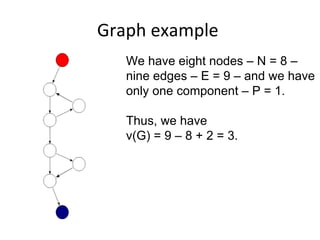
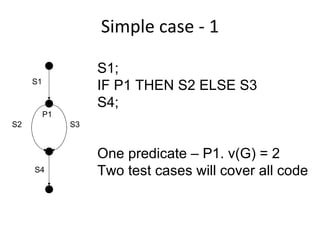
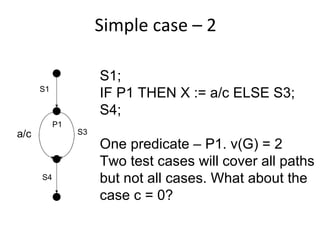
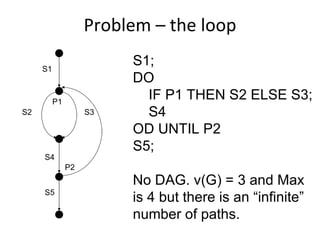
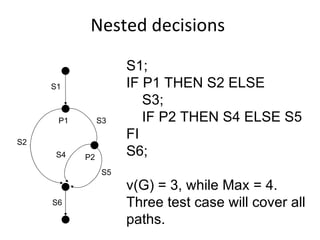
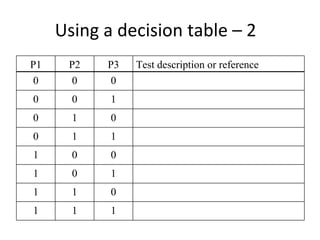
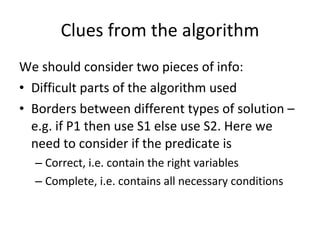
- Coverage metrics like McCabe's cyclomatic complexity and decision tables can be used to guide white box testing and ensure all paths are tested. Loops require special handling like testing with 0, 1, 5, and 20 iterations.
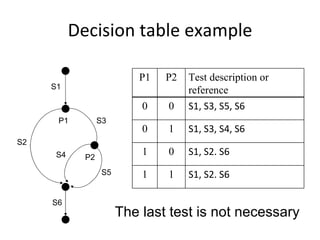
- Patterns like basic scenario, key-event service, and timed key-event service patterns effectively test real-time systems by defining preconditions, inputs, postconditions, and timeouts.










![Basic scenario pattern - BSP Check for precondition Check post-condition PreCondition == true / {Set activation time } IsTimeout == true / [report fail] PostCondition == true / [report success]](https://image.slidesharecdn.com/whiteboxvsblackbox-120130193510-phpapp02/85/White-boxvsblackbox-23-320.jpg)

![Key-event service pattern - KSP Check for key event Check post-condition Check precondition PreCondition == true PostCondition == true / [report success] KeyEventOccurred / [SetActivationTime] IsTimeout == true / [report fail]](https://image.slidesharecdn.com/whiteboxvsblackbox-120130193510-phpapp02/85/White-boxvsblackbox-25-320.jpg)

![Timed key-event service pattern - TKSP Check for key event Check post-condition Check precondition PreCondition == true IsTimeout == true / [report fail] PostCondition == true / [report success] KeyEventOccurred / [SetActivationTime] DurationExpired / [report not exercised]](https://image.slidesharecdn.com/whiteboxvsblackbox-120130193510-phpapp02/85/White-boxvsblackbox-27-320.jpg)

