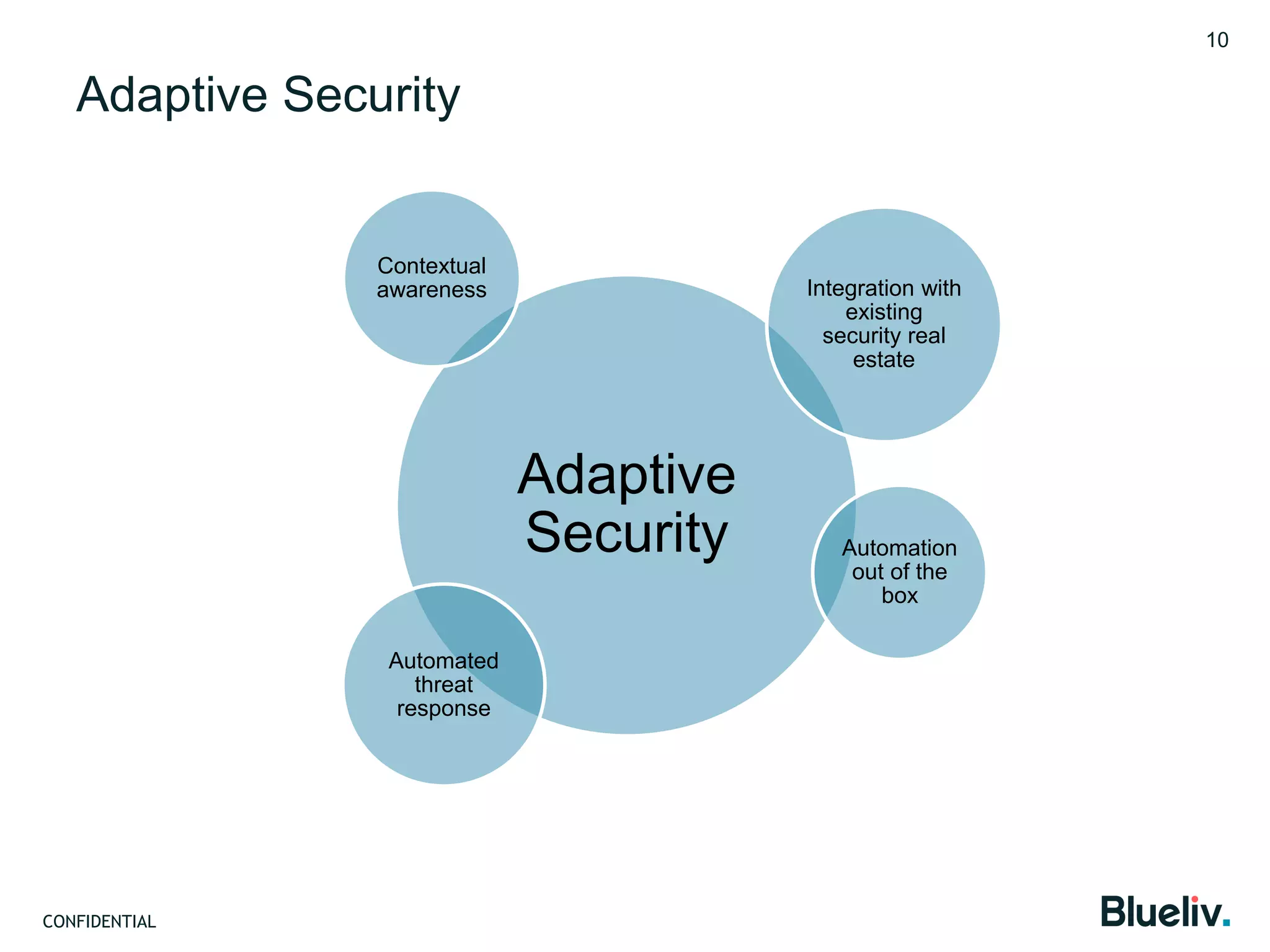
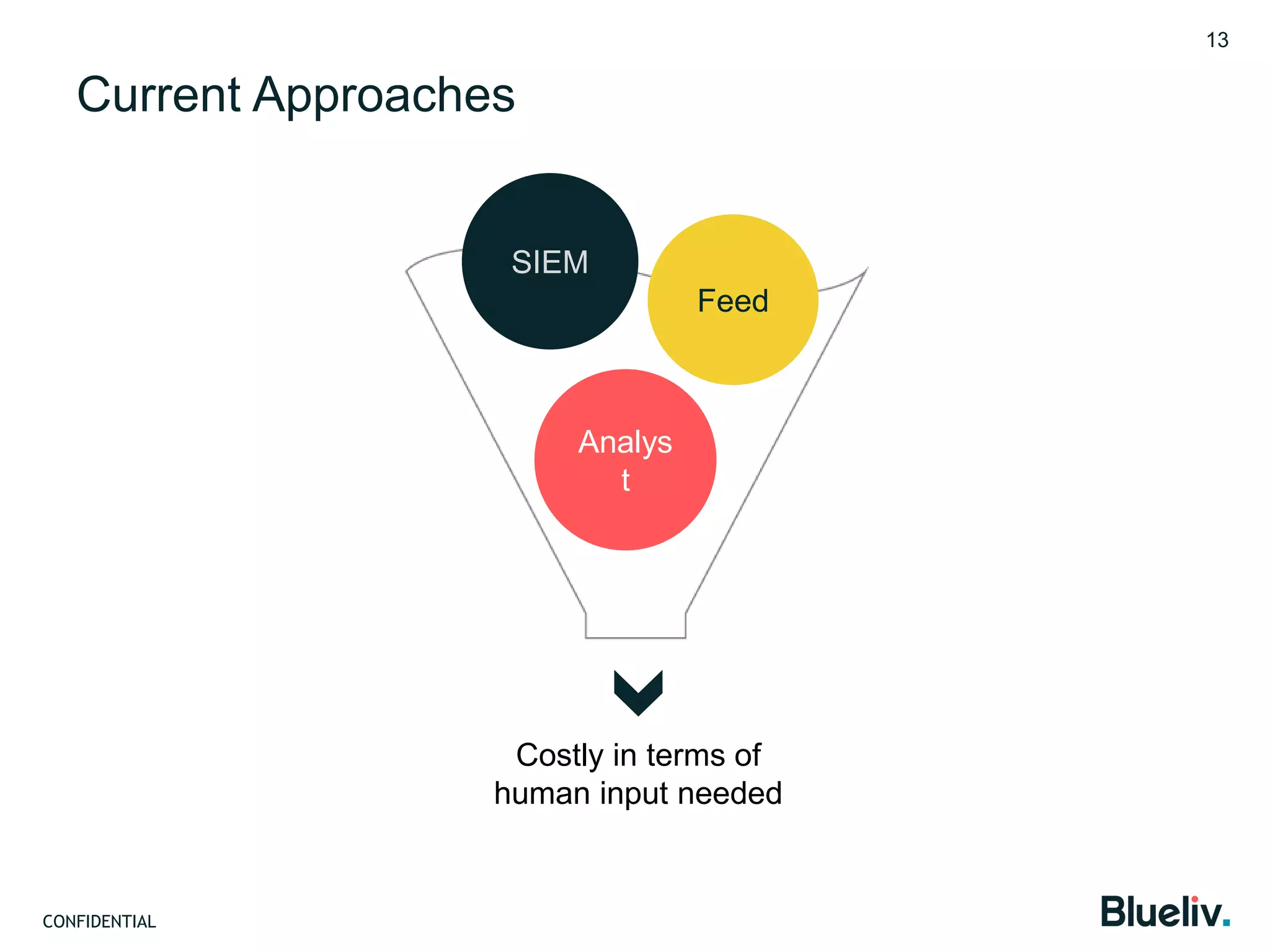
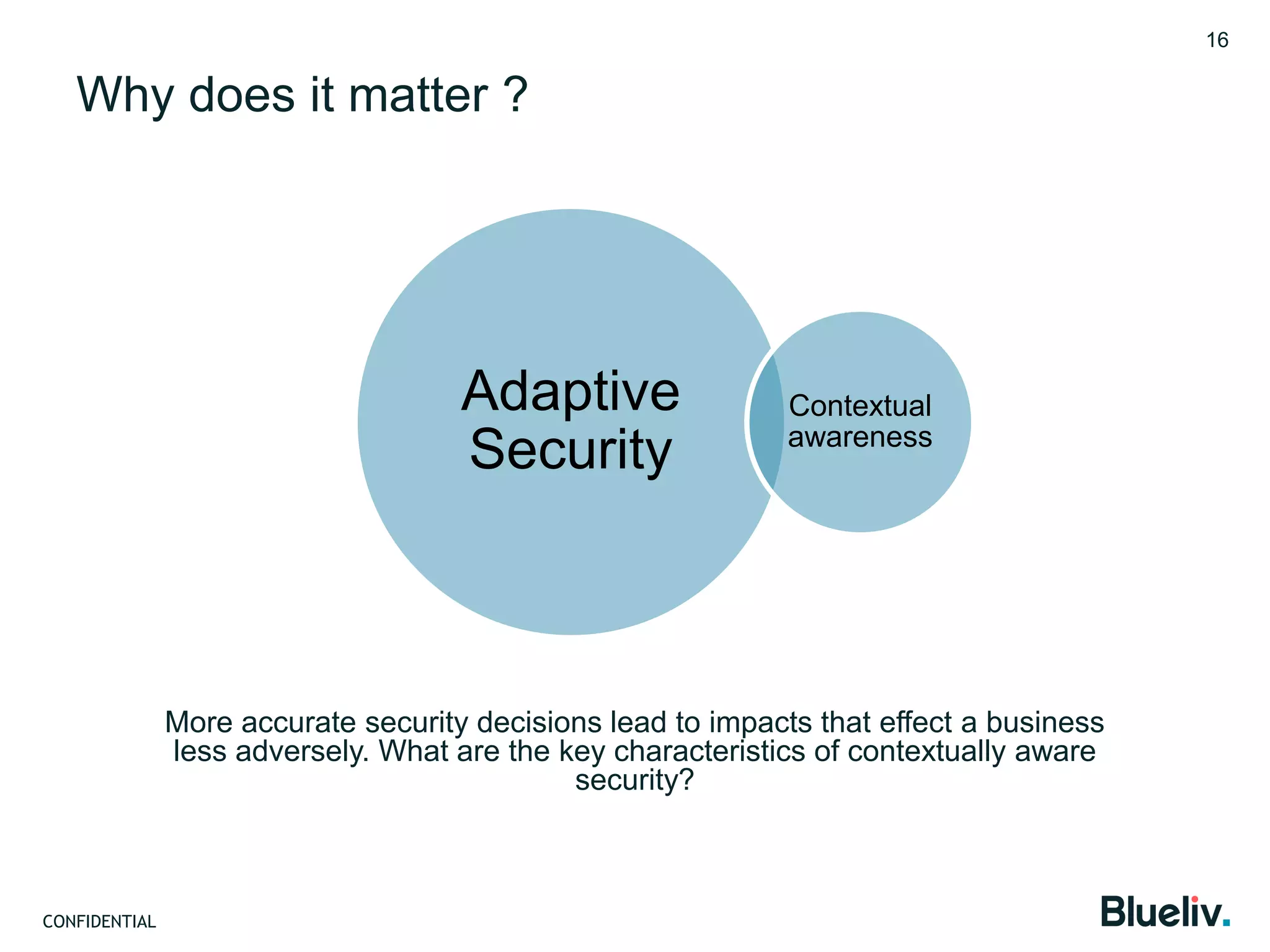
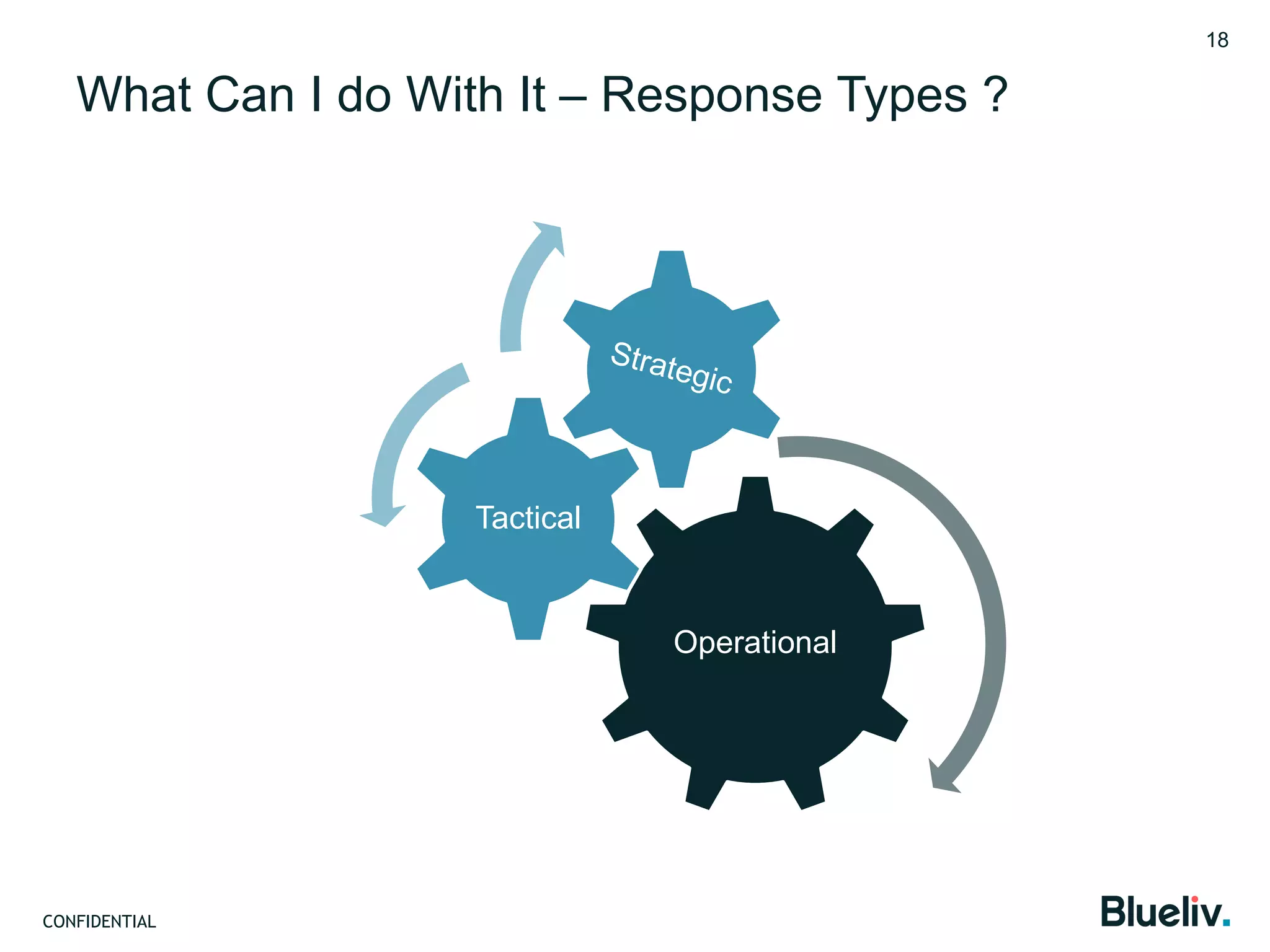
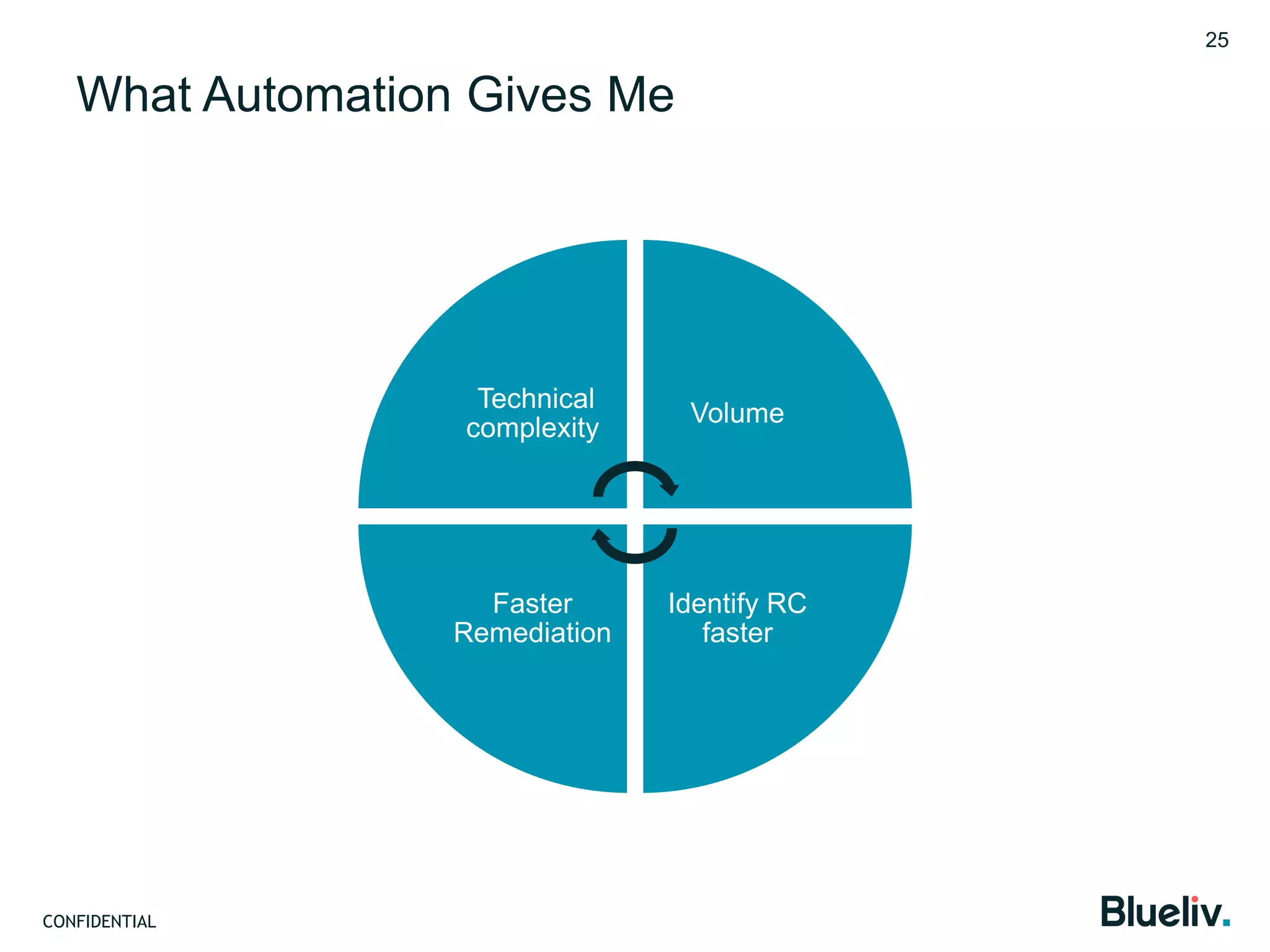
Blueliv is a leading provider of targeted cyber threat intelligence aimed at large enterprises and security vendors, focusing on converting global threat data into actionable intelligence. The document discusses the importance of adaptive security, contextual awareness, and automation in modern cybersecurity, highlighting the complexity and costs associated with traditional security measures. It emphasizes the need for organizations to evolve their security posture to combat the continuously changing landscape of cyber threats.